Computer Science: CUET Mock Test - 5 - CUET MCQ
30 Questions MCQ Test CUET Mock Test Series - Computer Science: CUET Mock Test - 5
Which character is used in Python to make a single line comment?
_______ type is returned by the readlines() method of the file object.
The like operator makes use of two wild card characters underscore ( _ ) and %. Which of the following statement(s) is / are correct w.r.t these operators?
A. % represents zero, one or multiple characters
B. Underscore represents zero, one or multiple characters
C. Underscore represents only multiple characters
D. Underscore represents exactly a single character
E. % represents zero character
Choose the most appropriate answer from the options given below:
Given below are two statements: one is labelled as Assertion A and other is labelled as Reason R.
Assertion A : Wi - Fi gives users the flexibility to move around within the network area while being connected to the network.
Reason R : Wireless network connects communicating devices to each other without any wire.
In the light of the above statements, choose the most appropriate answer from the options given below:
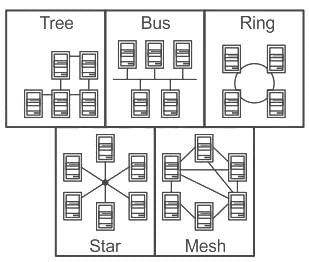
Choose the Network Topology that requires a central controller.
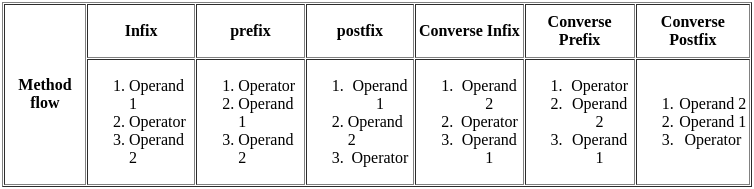
What would be the prefix notation for the given equation?
(a+(b/c) *(d^e)-f)
Which of the following features are associated with SQL?
A. SQL is a case-sensitive language.
B. Allows for the creation of views and tables.
C. It does not permit the handling of data in a relational database management system (RDBMS).
D. Facilitates the imposition of constraints to ensure the integrity of the data.
Choose the correct answer from the options given below:
Which of the following is valid order for SQL query evaluation?
Note: Options order from left to right.
Which of the following is the correct extension of the Python file?
Two statements are given below, one is Assertion (A) and the other is Reason (R). Read the statements carefully and choose the correct answer.
Assertion (A): Linear search is an efficient searching algorithm for large arrays.
Reason (R): Linear search has a time complexity of O(n).
Which language is used to access and manipulate databases?
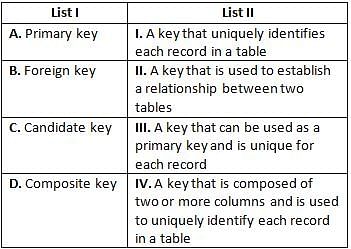
Directions: Match the contents under List I with those under List II.
A node that forwards data packets from one network to their destination in another network is called:
Which of the following options can be used to read the first line of a text file Myfile.txt?
If we want to add more contents in an existing file, file must be opened in............mode.
Two statements are given below:
Statement I: ALTER TABLE statement is used to add a new column to an existing table in SQL.
Statement II: INSERT Row statement is used to insert the Row to an existing table in SQL.
It is possible to create a loop using goto statement in python?
What will be the output of following Python code?
str1="Information"
print(str1[2:8])
The process of identifying a slot for the second and further items in the hash table in the event of collision, is called _______.
Which of the following is/are the advantage(s) of a database management system?
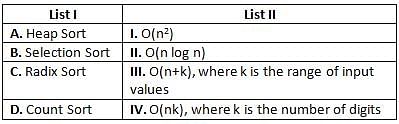
Directions: Match the contents under List I with those under List II.
What is the output of the following if statement
a, b = 12, 5
if a + b:
print('True')
else:
print('False')
Your teacher has given you a method/function FilterWords() in python which read lines from a text file NewsLetter.TXT, and display those words, which are lesser than 4 characters. Your teachers intentionally kept few blanks in between the code and asked you to fill the blanks so that the code would run to find desired result. Do the needful with the following python code:
def FilterWords():
c=0
file=open('NewsLetter.TXT', '_____') #Statement-1
line = file._____ #Statement-2
word = _____ #Statement-3
for c in word:
if _____: #Statement-4
print(c)
_________ #Statement-5
FilterWords()
Q. Write the mode of opening the file in Statement-1.
Your teacher has given you a method/function FilterWords() in python which read lines from a text file NewsLetter.TXT, and display those words, which are lesser than 4 characters. Your teachers intentionally kept few blanks in between the code and asked you to fill the blanks so that the code would run to find desired result. Do the needful with the following python code:
def FilterWords():
c=0
file=open('NewsLetter.TXT', '_____') #Statement-1
line = file._____ #Statement-2
word = _____ #Statement-3
for c in word:
if _____: #Statement-4
print(c)
_________ #Statement-5
FilterWords()
Q. Fill in the blank in Statement-3 to read data word by word.
Your teacher has given you a method/function FilterWords() in python which read lines from a text file NewsLetter.TXT, and display those words, which are lesser than 4 characters. Your teachers intentionally kept few blanks in between the code and asked you to fill the blanks so that the code would run to find desired result. Do the needful with the following python code:
def FilterWords():
c=0
file=open('NewsLetter.TXT', '_____') #Statement-1
line = file._____ #Statement-2
word = _____ #Statement-3
for c in word:
if _____: #Statement-4
print(c)
_________ #Statement-5
FilterWords()
Q. Fill in the blank in Statement-5 to close the file.
Your teacher has given you a method/function FilterWords() in python which read lines from a text file NewsLetter.TXT, and display those words, which are lesser than 4 characters. Your teachers intentionally kept few blanks in between the code and asked you to fill the blanks so that the code would run to find desired result. Do the needful with the following python code:
def FilterWords():
c=0
file=open('NewsLetter.TXT', '_____') #Statement-1
line = file._____ #Statement-2
word = _____ #Statement-3
for c in word:
if _____: #Statement-4
print(c)
_________ #Statement-5
FilterWords()
Q. Fill in the blank in Statement-2 to read the data from the file.
Your teacher has given you a method/function FilterWords() in python which read lines from a text file NewsLetter.TXT, and display those words, which are lesser than 4 characters. Your teachers intentionally kept few blanks in between the code and asked you to fill the blanks so that the code would run to find desired result. Do the needful with the following python code:
def FilterWords():
c=0
file=open('NewsLetter.TXT', '_____') #Statement-1
line = file._____ #Statement-2
word = _____ #Statement-3
for c in word:
if _____: #Statement-4
print(c)
_________ #Statement-5
FilterWords()
Q. Fill in the blank in Statement-4, which displays the word having lesser than 4 characters.
|
8 docs|148 tests
|