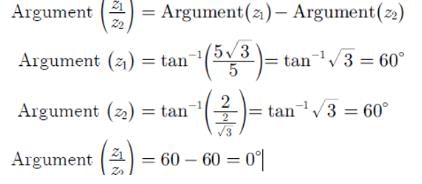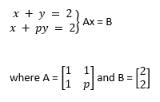Computer Science And IT (CS/IT) Mock Test For Gate - Computer Science Engineering (CSE) MCQ
30 Questions MCQ Test - Computer Science And IT (CS/IT) Mock Test For Gate
In the following question, some part of the sentence may have errors. Find out which part of the sentence has an error and select the appropriate option. If the sentence is free from error, select 'No error'.The fox thought to him
The fox thought to him (A)/ that he should wait for the (B)/ lady to leave the place.(C)/ No error
A book shelf has 27 books – 9 books each written by 3 eminent authors. If Raj selects any 2 books without looking at their author’s name, what is the probability that he picks up books written by the different authors.
The ratio material cost and labor cost in a small construction project is 3:1. If the labor cost went up by 20% and material cost witnessed an avenge increase of 15%, what will be the new ratio of labor cost and material cost?
A monkey is trying to reach the top of a tree. He climbs 3 feet in a minute but slides down by 1.5 feet after each climb. If he reaches the top of the tree in 58 minutes, then the maximum possible height of the tree is ____ feets.
Direction: Read the sentence to find out whether there is any error in it. The error, will be in one part of the sentence. Ignore the errors of punctuation, if any.The misuse of drugs and alcohol were seen as very damaging/ to the society, chiefly because it often promoted/ violent crimes and anti-social behavior; while also/ causing ill-health, poverty and family breakdown.
An event A is considered to be rolling a fair dice .If 10 dice are rolled each of which are independent, find the probability that the sum obtained on the faces is between 30 and 40 both inclusive.
Given: N(1.0184) = 0.84 , which is value of normal distribution for X = 1.018
Which of the given option is most appropriate in the context of the word in bold letters in the given sentence.The reason there is no exodus towards banks in general for new project funding is their relatively less experience in project appraisal.
Improve the bracketed part of the sentence. My car (broke off) on my way to the office.
Chinnaswamy is driving to pick up his son from school on a Saturday which is a half day. On his way to school, he crossed a church which is 1/5th of the way to school at 9:50 hours and exactly 10 minutes later, he went past a temple which is 1/3rd of the way to school. The time after 10:00 hours at which he reaches his son’s school is ____ minutes.
In the following question, out of the four alternatives, select the word similar in meaning to the given word.Literal
In control flow analysis, control flow graph contain basis blocks for the code.
A basic block is a segment of the code that a program must enter at the beginning and it can exit only at the end. A basic block ends in which of the following ways?
Which of the following operators is used to search a specified pattern in a column?
The logic pumping lemma is a good example of
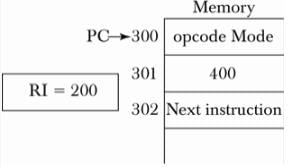
An instruction is stored at location 300 with its address field at location 301. The address field has the value 400. A processor register R1 contains the number 200. What will be the addressing mode of the effective address of the instruction is 702?
A file system is said to exhibit data dependence because;
Choose the correct option to fill the empty blanks in below statement :If variables are declared previously, then __________ is responsible for generation of symbol table but if variables are not declared then symbol table will be generated by __________.
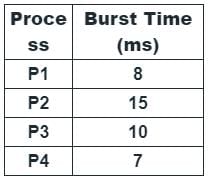
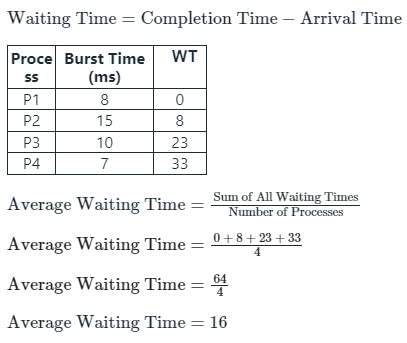
For the following set of processes scheduled using FCFS policy, determine the average waiting time. Assume that the processes arrived in the order P1, P2, P3, P4.
Initially a priority queue had 5 elements and it is being implemented as a Max-Heap. Let’s say the level order traversal of the heap is: 30, 18, 17, 12, 11. Now two more elements are inserted into the heap i.e. 10 and 19 in the same order. What is the level order traversal of the heap after the insertion?
Create a view which gives students number and name for those who enrolled in class ”Database Design” and whose age is under 25.
Consider the following C program:
int main(){
printf("what %%");
return 0;
}
What does the code print?
Consider a program which stores the frequency of marks of student in a particular subject say Mathematics. The marks is in the range [0...100] and there are around 500 students. But there is one condition we only want to record frequency if the student has passed in the exam, the passing marks being 40. What is the best way to store the frequency of marks above 40?
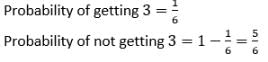
A fair die with faces {1, 2, 3, 4, 5, 6} is thrown repeatedly till ‘3’ is observed for the first time. Let X denote the number of times the die is thrown. The expected value of X is _____.
The alternate way of writing the instruction, SUB #7,R1 is______. The above addressing mode is Immediate addressing mode
Which one of the following is a closed form expression for the generating function for the sequence {Sn}, where Sn = an, for all n = 0, 1, 2, …… and ‘a’ is a constant?
Given two complex numbers, 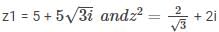 the argument of z1/z2 in degrees is
the argument of z1/z2 in degrees is
An athlete can play on several teams and each team needs atleast one player.
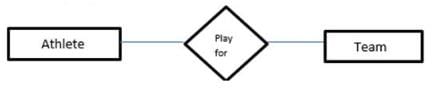
Based on the description above, what is the maximum cardnality between each instance of “Athelete” and “team”?
Find the type of given grammar:
S -> #S | @ A#
A -> @ A @ | #B!A
B -> &B% | ! | e
Non Terminal (V) = { S , A , B }
Terminal (T) = { # , ! , @ , % , & }
Here e is epsilon or null symbol.
What is the unit digit of number obtained from: 111283+171293 - 71283
Consider the following system of equations.
x+y = 2
x+py = 2
where p is constant. Find the value of ‘p’ such that the system has more than two solutions.
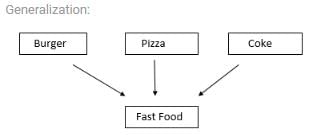
When number of entities are bought together into one entity based on their similar characteristics, what is this process called;


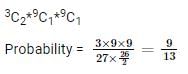

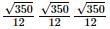
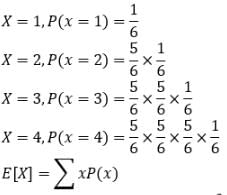
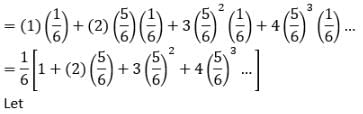
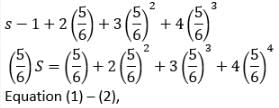
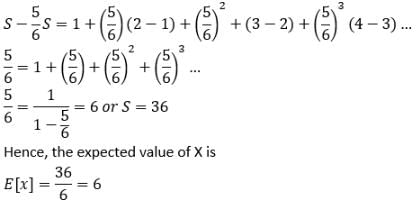
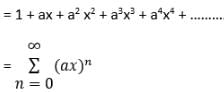
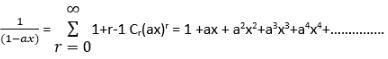
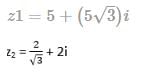
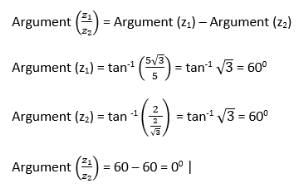 Since we know that
Since we know that