RRB JE IT CBT 2 Full Test 1 - Railways MCQ
30 Questions MCQ Test RRB JE (Railways Junior Engineer) CBT Mock Test Series 2025 - RRB JE IT CBT 2 Full Test 1
Which of the following is not a primary component of a Linux system?
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
Which of the following is not a valid category of “System bus” in a computer system?
Which of the following categories of viruses normally infect executable code, such as as.com and .exe files?
A ________ is the term used when a search engine return a Web page that matches the search.
Criteria.
In January 2019, Krishna Sobti passed away. She was a famous ________.
Which of the following is not an application layer protocol?
Which of following datatype can be returned by a function?
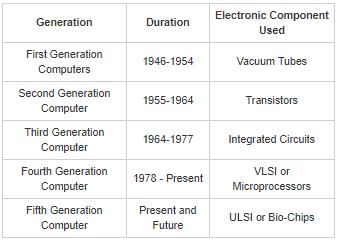
Which electronic components were used in Fifth Generation Computers?
________ command is used to circulate between two different file directories.
Which of the following decisive battles had established the dominion of the British in India?
Which of the following examines the specification to ensure that all system requirements are error free?
Binary search algorithm cannot be applied to which of following?
A set of programs which enables computer hardware and software to work together is called
Which of the following operator can be used to decrease the value of variable “x” by “1”?
Which force is required to maintain a body in Uniform circular Motion?
What is the correct HTML code for inserting an image?
Which of the following is the main constituent of Biogas after Methane?
Which of the following chemical compounds is used for causing acid rain?
In which of the following during the emission of radioactive rays, no changes occur in the mass or charge?