RRB JE IT (CBT II) Mock Test- 3 - Computer Science Engineering (CSE) MCQ
30 Questions MCQ Test RRB JE Mock Test Series for Computer Science Engineering 2025 - RRB JE IT (CBT II) Mock Test- 3
What is the frequency of alternating current which is used in the house?
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
Which of the following standard library functions returns the length of the string?
The command line arguments are handled using main() function arguments where ______ refers to the number of arguments passed.
In MS Excel, ctrl + ; is used to insert _________ in the workbook.
Which of the following is not a multitasking operating system
Which of the following features is independent of CPU and allows certain hardware subsystems to access random access memory?
The signed magnitude representation of 0 in 4-bit representation is:
In MS Excel, ‘highlighting cells rule’ comes under which of the following panes?
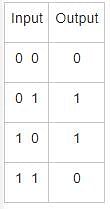
Which of the following is also called a 1 – operand machine?
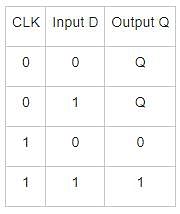
Which of the following is also called as transparent flip flop:
Which task region in the spiral model is used to build one or more representations of the application?
__________ refers to the set of activities that ensure that software correctly implements a specific function.
Data and Time are available on the desktop at _______.
The most acceptable range of LEO (Low Earth Orbit) is________.
The least distance of distinct vision for a young adult with normal vision is about
The network database model can be organized as _________.
__________ uses a series of phases, called the systems development life cycle (SDLC), to plan, analyze, design, implement, and support an information system.
In Microsoft Word, File, edit, view etc. are provided in _______________.
__________ is any combination of columns that uniquely identifies a row in a table.
Which among the following cannot be considered as a measure of improvement or national development?
Which of the following components of Microsoft Windows provides the ability to view and change system settings?
Which one of the following is not an example of a hardware device?
The stability of a pond or ecosystem depends on which of the following?
Which of the following can be used to create a new data type name in the C programming language?