Computer Science: CUET Mock Test - 1 - CUET MCQ
30 Questions MCQ Test CUET Mock Test Series - Computer Science: CUET Mock Test - 1
Given below are two statements:
Statement I. When all the value are sorted in ascending or descending order, the middle value is called mode.
Statement II. Value that appears most number of times in the given data of an attribute / variable is called mode.
In the light of the above statements, choose the correct answer from the options given below:
Statement I. When all the value are sorted in ascending or descending order, the middle value is called mode.
Statement II. Value that appears most number of times in the given data of an attribute / variable is called mode.
Adjacent elements are compared and swapped in ________ sorting technique.
Which of the following statements are correct for Queue?
A. Queue is an ordered linear data structure
B. Deque can support both stack and queue operations
C. Queue is a non-linear data structure
D. Queue works on FILO principle
E. Deque is a version of Queue which does not allow insertion and deletion at both ends
Choose the correct answer from the options given below:
From a text file "myfile.txt", Kriti will read next line through file object Fl using
What will be the output of the following Python code:
a = 1
if (a = 2):
print("value of a is", a)
Match the following SQL functions to their descriptions.
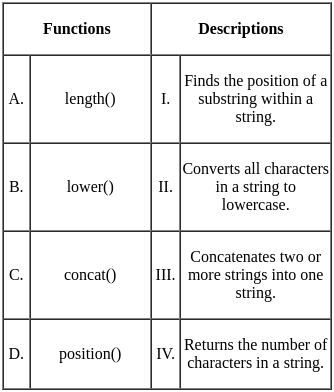
Choose the correct answer from the options given below:
What do we use to define a block of code in Python language?
Referential integrity constraint in a relational database is specified with the help of a _________.
Which among the following SQL commands does not fall under the category of data manipulation language?
Which of the following networking components is called a three-layer switch?
Which of the following operators cannot be used with string data type?
To read the next line of the file from a file object infile, we use ____________.
Which of the following is correctly evaluated for this function?
pow(x,y,z)
Which of the following is false regarding the loops in Python?
Insertions take place at the rear end of the queue and deletions take place at the 'front' end of the queues. On which principal does this work?
What is the significance of the tell() method?
Computers manipulate data in many ways, this manipulation is called _____.
What are the two advantages of database management system?
Which method is used to protect online images from hackers?
_________ switching is well suited for voice communication while _________switching is better suited for data and other non-voice communication.
Consider a declaration, L = (1, 'Python', '3.14').
Which of the following represents the data type of L?
Which of the following file modes is not valid?
Radha Shah is a programmer, who has recently been given a task to write a python code to perform the following CSV file operations with the help of two user defined functions/modules:
a. CSVOpen() : to create a CSV file called BOOKS.CSV in append mode containing information of books – Title, Author, and Price.
b. CSVRead() : to display the records from the CSV file called BOOKS.CSV where the field title starts with 'R'.
She has succeeded in writing partial code and has missed out certain statements, so she has left certain queries in comment lines.
import csv
def CSVOpen():
with open('books.csv','______',newline='') as csvf:
#Statement-1
cw=______ #Statement-2
______ #Statement-3
cw.writerow(['Rapunzel','Jack',300])
cw.writerow(['Barbie','Doll',900])
cw.writerow(['Johnny','Jane',280])
def CSVRead():
Q. Choose the appropriate mode in which the file is to be opened in append mode (Statement 1).
Radha Shah is a programmer, who has recently been given a task to write a python code to perform the following CSV file operations with the help of two user defined functions/modules:
a. CSVOpen() : to create a CSV file called BOOKS.CSV in append mode containing information of books – Title, Author, and Price.
b. CSVRead() : to display the records from the CSV file called BOOKS.CSV where the field title starts with 'R'.
She has succeeded in writing partial code and has missed out certain statements, so she has left certain queries in comment lines.
import csv
def CSVOpen():
with open('books.csv','______',newline='') as csvf:
#Statement-1
cw=______ #Statement-2
______ #Statement-3
cw.writerow(['Rapunzel','Jack',300])
cw.writerow(['Barbie','Doll',900])
cw.writerow(['Johnny','Jane',280])
def CSVRead():
Q. Choose the correct option for Statement 3 to write the names of the column headings in the CSV file, BOOKS.CSV.
|
8 docs|148 tests
|



















