Computer Science: CUET Mock Test - 3 - CUET MCQ
30 Questions MCQ Test CUET UG Mock Test Series 2026 - Computer Science: CUET Mock Test - 3
Choose correct SQL query to
Display the details of all male customers having membership more than 10 months.
Choose correct SQL query to display total customers under each trainer in the Gym.
Choose correct SQL query to display the names of all trainees with their date of appointment in descending order, who are taking core activity.
Choose correct SQL query to update the membership of all the customers, under Trainer with code G101 and G102, to 12 months.
Choose the correct SQL query to display a report showing Trainer name, Salary, Customer name and Fee for all Trainers having salary between 20000 to 25000.
A. Select TName, Salary, Cust Name, Fee
From Customer C, Trainer T
Where T.TId = C.TId and Salary>=20000 and Salary<=25000;
B. Select TName, Salary, Cust_Name, Fee
From Customer, Trainer
Where Customer.TId = Trainer. TId and Salary between 20000 and 25000;
C. Select TName, Salary, C_Name, Fee
From Customer C, Trainer T
Where C.TId = T.TId and Salary between 20000 and 25000;
D. Select TName, Salary, C_Name, Fee
From Customer, Trainer
Where C.TI d = T.TId and 20000<=Salary<=25000;
E. Select TName, Salary, Cust_Name, Fee
From Customer C, Trainer T
Where T.TId = C.TId and Salary between 20000 and 25000;
Choose the most appropriate answer from the options given below:
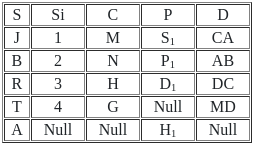
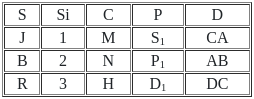
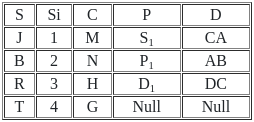
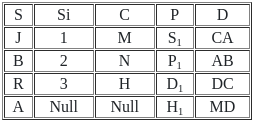
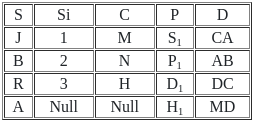
Which of the following join is used to get all the tuples of relation X and Y with Null values of corresponding missing values ?
Number of tuples obtained by applying cartesian product over X and Y are :
Find the number of tuples by applying the operation X⟕X.s = y.sY
Number of tuples by applying right outer join on relation X and Y is/are :
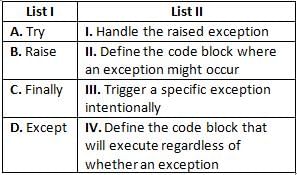
When will the bad_alloc exception be thrown by a program?
A file management system can typically access records from:
Which constraint does not allow NULL values?
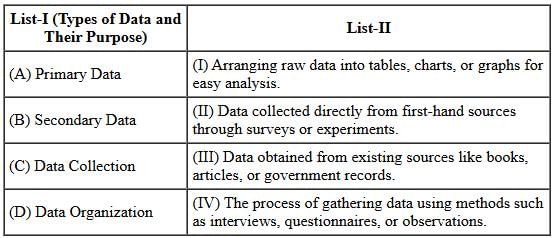
Directions: Match the contents under List I with those under List II.
Two statements are given below:
Statement I: The 'x' file access mode allows you to create a new file but will raise an error if the file already exists.
Statement II: The 'a' file access mode allows you to write to the file but not overwrite any existing content.
Testing stack for overflow is performed by comparing the values of the top with value ______.
What is the similarity between the operations on stacks and those on queues, although they are entirely different?
Which of the following is not a limitation of the binary search algorithm?
Ankita is writing a program to perform some operations in Queue. She has created three Insert_in_Queue(Student), Delete_from_Queue(Student) and Print_Queue(Student) methods/functions in Python to add a new student name, delete a student name and print the list of student from a queue, considering them to act as insert, delete and print operations of the Queue data structure. She is not getting the desired result. Help her to get the desired result from the given Python code.
def Insert_in_Queue(queue):
a=input("enter student name: ")
queue.____________ # Statement-1
def Delete_from_Queue (queue):
if (____________): # Statement-2
print("Queue empty")
else:
print("Deleted element is: ",queue[0])
del queue[___] #Statement-3
def Print_Queue(queue):
if not ________: #Statement-4
print(queue[__:___ ]) # Statement-5
Q. What should Ankita write to complete the Statement-1 to store the student name?
Ankita is writing a program to perform some operations in Queue. She has created three Insert_in_Queue(Student), Delete_from_Queue(Student) and Print_Queue(Student) methods/functions in Python to add a new student name, delete a student name and print the list of student from a queue, considering them to act as insert, delete and print operations of the Queue data structure. She is not getting the desired result. Help her to get the desired result from the given Python code.
def Insert_in_Queue(queue):
a=input("enter student name: ")
queue.____________ # Statement-1
def Delete_from_Queue (queue):
if (____________): # Statement-2
print("Queue empty")
else:
print("Deleted element is: ",queue[0])
del queue[___] #Statement-3
def Print_Queue(queue):
if not ________: #Statement-4
print(queue[__:___ ]) # Statement-5
Q. Fill in the blank in Statement-3 with index number.
Ankita is writing a program to perform some operations in Queue. She has created three Insert_in_Queue(Student), Delete_from_Queue(Student) and Print_Queue(Student) methods/functions in Python to add a new student name, delete a student name and print the list of student from a queue, considering them to act as insert, delete and print operations of the Queue data structure. She is not getting the desired result. Help her to get the desired result from the given Python code.
def Insert_in_Queue(queue):
a=input("enter student name: ")
queue.____________ # Statement-1
def Delete_from_Queue (queue):
if (____________): # Statement-2
print("Queue empty")
else:
print("Deleted element is: ",queue[0])
del queue[___] #Statement-3
def Print_Queue(queue):
if not ________: #Statement-4
print(queue[__:___ ]) # Statement-5
Q. Specify the range to print all queue elements in Statement-5.
Ankita is writing a program to perform some operations in Queue. She has created three Insert_in_Queue(Student), Delete_from_Queue(Student) and Print_Queue(Student) methods/functions in Python to add a new student name, delete a student name and print the list of student from a queue, considering them to act as insert, delete and print operations of the Queue data structure. She is not getting the desired result. Help her to get the desired result from the given Python code.
def Insert_in_Queue(queue):
a=input("enter student name: ")
queue.____________ # Statement-1
def Delete_from_Queue (queue):
if (____________): # Statement-2
print("Queue empty")
else:
print("Deleted element is: ",queue[0])
del queue[___] #Statement-3
def Print_Queue(queue):
if not ________: #Statement-4
print(queue[__:___ ]) # Statement-5
Q. Fill in the blank in Statement-2 to check whether the queue is empty or not.
Ankita is writing a program to perform some operations in Queue. She has created three Insert_in_Queue(Student), Delete_from_Queue(Student) and Print_Queue(Student) methods/functions in Python to add a new student name, delete a student name and print the list of student from a queue, considering them to act as insert, delete and print operations of the Queue data structure. She is not getting the desired result. Help her to get the desired result from the given Python code.
def Insert_in_Queue(queue):
a=input("enter student name: ")
queue.____________ # Statement-1
def Delete_from_Queue (queue):
if (____________): # Statement-2
print("Queue empty")
else:
print("Deleted element is: ",queue[0])
del queue[___] #Statement-3
def Print_Queue(queue):
if not ________: #Statement-4
print(queue[__:___ ]) # Statement-5
Q. Select the correct option to complete Statement-4.
File Transfer Protocol (FTP) use port number ____ and _____ to transfer communication and data signals respectively.
Which virus attack serves unwanted and aggressive advertising (e.g., pop-up ads) to the end-user?
Which of the following allows communication by allowing various computer networks around the world to interconnect?
Computer networks constituting the internet are connected by telephones, underwater cables and _____________
|
39 docs|145 tests
|