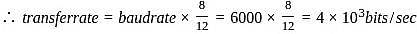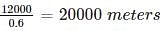UGC NET Paper 2 Computer Science Mock Test - 3 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series 2024 - UGC NET Paper 2 Computer Science Mock Test - 3
How many strings of 5 digits have the property that the sum of their digits is 7?
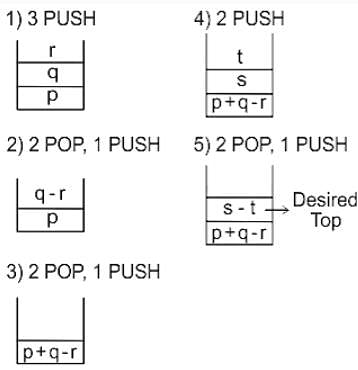
Postfix to infix operations is performed on the following expression. Using stack we need to perform the set of PUSH and POP operations depending upon the operator or operand in the expression. At a certain point, the top of the stack is " s - t"
How many push and pop operations are performed till that moment.
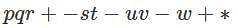
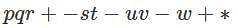
Which of the following logic families is well suited for high-speed operations?
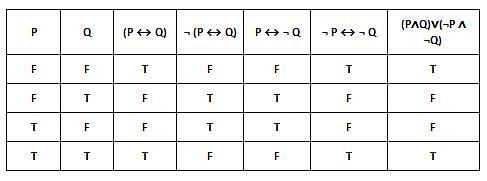
Which of the following is true?
I. ¬ (P ↔ Q) ≡ P ↔ ¬ Q
II. (P ↔ Q) ≡ (P ∧ Q) ∨ (¬ P ∧ ¬ Q)
III. (P ↔ Q) ≡ ¬ P ↔ ¬ Q
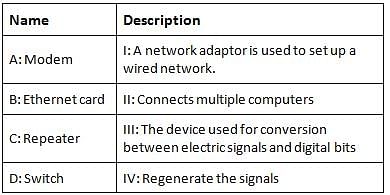
Consider the following:
Matching A, B, C, D in the same order gives:
Which of the following properties of the circuits of a graph are correct?
1. The minimum number of branches possible in a circuit will be equal to the number of elements in a circuit.
2. There are exactly two paths between any pair of vertices in a circuit.
3. There are at least two branches in a circuit.
Select the correct answer using the code given below.
Consider a counting Semaphore variable 'S'. Following are the semaphore operations performed: 18P, 3V, 7V, 2P, 6V. What can be the largest initial value of S to keep one process in suspended list?
Consider the following statements related to AND-OR Search algorithm.
S1: A solution is a subtree that has a goal node at every leaf.
S2: OR nodes are analogous to the branching in a deterministic environment
S3: AND nodes are analogous to the branching in a non-deterministic environment.
Which one of the following is true referencing the above statements?
Choose the correct answer from the code given below:
How many bytes of data can be sent in 33 seconds over a serial link with baud rate of 6000 in asynchronous mode with odd parity and two stop bits in the frame?
Which is true about conditional statement (a ∨ (¬ a ∧ b)) ↔ ¬ (b ∨ a)?
What is the smallest number of A’s that might be printed when this set of processes runs?
The Adjacency matrix of a directed graph G is given below.
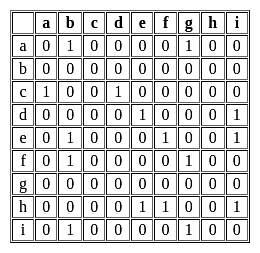
Which of the following is a valid topological sort of G?
A network with a ring topology having link bandwidths of 100 Mbps and propagation speed 2×108 m/sec. If packet size is 12000 bits, considering nodes do not introduce delay, then what would be the circumference if there was a node every 100 m and each node introduced 10 bits of delay?
Read the given program in C and answer the following question.
main()
{
int x,y;
clrscr();
printf("Read the integer from keyboard(x):")
scanf("%d",&x);
x>>2;
y=x;
printf("OutputA=%d",y);
}
If 'Read the integer from keyboard (x) = 8 then what would be the value of Output A?
Entities having a primary key are called?
Which of the following is system software?
Which search is complete and optimal when h(n) is consistent?
The limitation of dynamic programming is that it does not allow itself for __________.
In 1985, the famous chess player David Levy beat a world champion chess program in four straight games by using orthodox moves that confused the program. What was the name of the chess program?
Which of the following does not represents the given language?
Language: {0,01}
A full binary tree can be generated using __________.
A series of statements explaining how the data is to be processed is called _________.
|
16 docs|120 tests
|