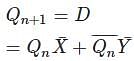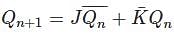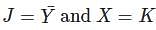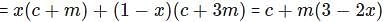UGC NET Paper 2 Computer Science Mock Test - 6 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series 2024 - UGC NET Paper 2 Computer Science Mock Test - 6
Four channels are multiplexed using TDM. If each channel sends 100 bytes/second and we multiplex 1 byte per channel, then the bit rate for the link is
The translator which performs macro calls expansion is called
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
In a typical mobile phone system with hexagonal cells, it is forbidden to reuse a frequency band in adjacent cells. If 840 frequencies are available, then how many can be used in a given cell?
Which of the following statements is/are true?
(i) The grammar S →SS | a is ambiguous (where S is the start symbol).
(ii) The grammar S →0S1 | 01S | e is ambiguous (the special symbol e represents the empty string and S is the start symbol).
(iii) The grammar (where S is the start symbol)
S →T/U
T →x S y ? xy ? e
U →yT
generates a language consisting of the string yxxyy.
Consider the given 8 × 3 encoders. If only I7 input is high at the moment then find the final output.
The optimal solution of the LPP
Minimize Z = x + y subject to
5x + 9y ≤ 45
x + y ≥ 2
y ≤ 4, x, y ≥ 0
attained at
Consider the following statements:
Statement 1: Using a larger block size in a fixed partition scheme may increase internal fragmentation.
Statement 2: Variable partition and segmentation suffer from external fragmentation.
Which of the following is true?
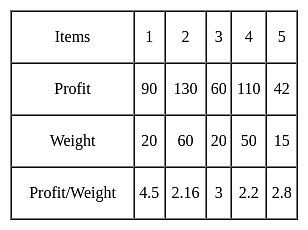
Consider the table given below consisting of 5 items with their profit and weight associated with it.
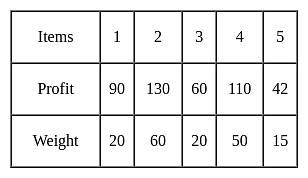
The weight of the knapsack is 90. Find the maximum profit gain by applying fractional knapsack?
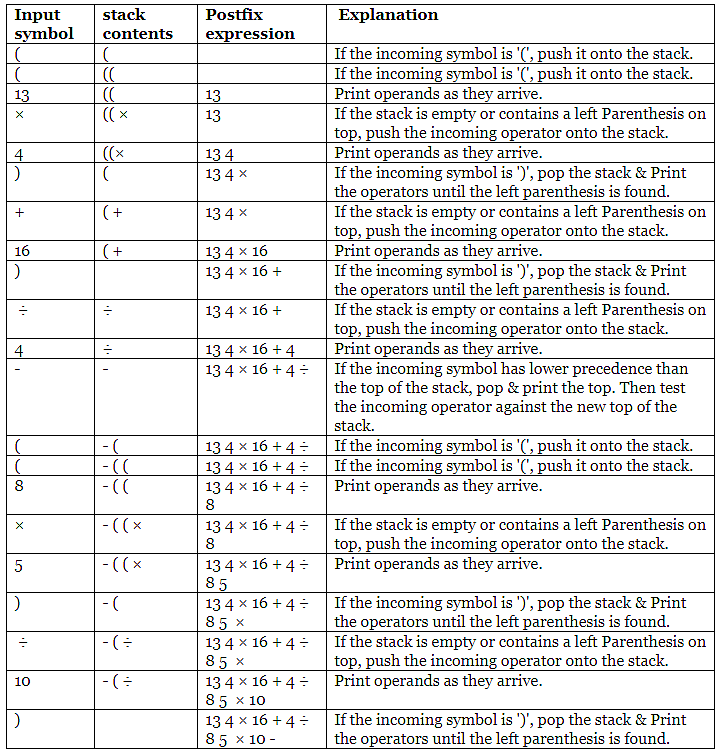
Consider the following infix expression. While converting this infix expression to postfix expression, what will be the stack content (from bottom to top) after scanning operand 5?
((13 × 4) + 16) ÷ 4 – ((8 × 5) ÷ 10)
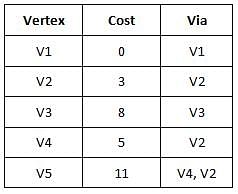
In the following diagram, if link V1-V4 is removed, then how does the routing table for distance vector routing protocol vary for the node V1?
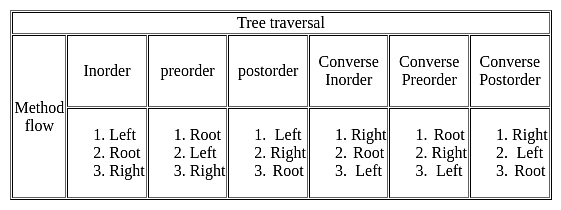
The preorder traversal sequence of a binary search tree is
25, 15, 10, 4, 12, 22, 18, 24, 50, 35, 31, 44, 70, 66, 90
Which one of the following is the postorder traversal sequence of the same tree?
Consider a multi-level paging system. Let 'm' be the main memory access time, 'c' be the TLB access time, 'n' be the n-level paging implementation and 'x' be the TLB Hit Ratio. Which among them can be the Effective Memory Access Time formula for 2-level paging?
Let a schedule be
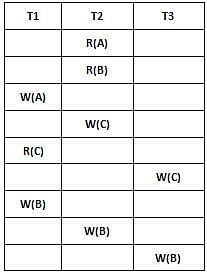
The valid view serializable sequence of the above schedule is
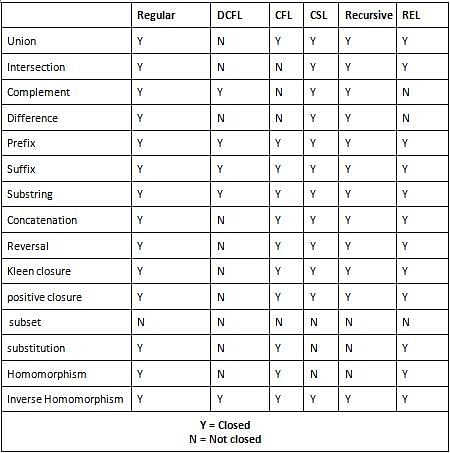
The family of context-free languages is NOT closed under:
Which of the following queries will find all students in the STUDENT table whose class is either 12A or 12B?
Which of the following is the most common shared resource in a computer network?
Which of the following is not a NoSQL database?
Which of the following fundamental notions of software engineering does not account for?
The core of reverse engineering is an activity called:
DNS can obtain the __________ of host if its domain name is known and vice versa.
Which phase of the compiler checks the grammar of the programming?
Which phase of the compiler is also known as Scanner?
|
16 docs|120 tests
|


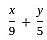 = 1...(i)
= 1...(i)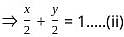
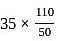 = 269
= 269