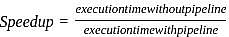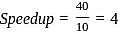UGC NET Paper 2 Computer Science Mock Test - 10 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series 2024 - UGC NET Paper 2 Computer Science Mock Test - 10
System calls are usually invoked by using which of the following?
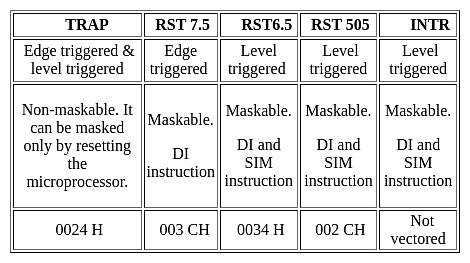
Which of the following 8085 microprocessor hardware interrupts has the lowest priority?
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
Preorder traversal of binary search tree is 38, 14, 8, 23, 18, 20, 56, 45, 82, 70. What is the postorder traversal of binary search tree?
The line graph L(G) of a simple graph G is defined as follows:
- There is exactly one vertex v(e) in L(G) for each edge e in G.
- For any two edges e and e' in G, L(G) has an edge between v(e) and v(e'), if and only if e and e' are incident with the same vertex in G.
Which of the following statements is/are TRUE?
(P) The line graph of a cycle is a cycle.
(Q) The line graph of a clique is a clique.
(R) The line graph of a planar graph is planar.
(S) The line graph of a tree is a tree.The regular expression 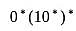 denotes the same set as
denotes the same set as
Assume a program with the following memory requirements.
What is the total size of memory required to load and run this program?
Consider the following grammar G:
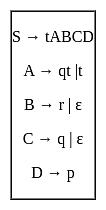
What is the FOLLOW(A)?
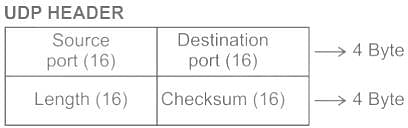
Which one of the following fields is present in both TCP header and UDP header?
Find the utility(max value) of a root node value of the game-tree after applying the min-max algorithm?
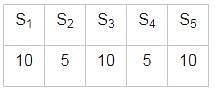
Consider a 5- stage instruction pipeline where the delay of S4 is half to that of S1. S2 has a half delay to S3. S1 is having a delay of 10 ns. S5 and S3 have the same delay as S1 . What will be the speed up achieved in this?
Which of the following statement are true about Feasibility Analysis?
Statement 1: Feasibility Analysis is used to obtain the outline of the problem and decide whether a feasible or appropriate solution exists or not.
Statement 2: A feasibility study can be considered as the final investigation that helps the software development life cycle.
A binary tree T has n leaf nodes, the number of nodes of degree 2 in T is:
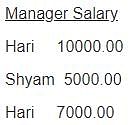
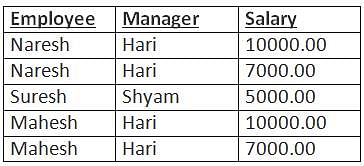
Database table by name Employee_Records is given below
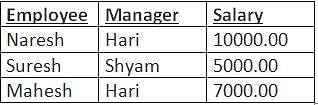
What is the output of the following SQL query?
SELECT Count(*) FROM
( ( SELECT Employee, Manager FROM Employee_Records)
AS S NATURAL JOIN
( SELECT Manager, Salary FROM Employee_Records) AS T );
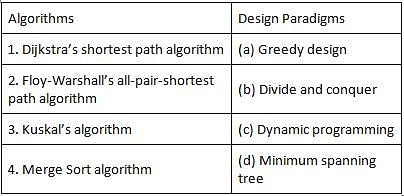
Given below are some famous algorithms and some algorithm design paradigms
The addressing mode which makes use of in-direction pointers is ______.
The minimum number of stacks required to implement a queue is __________.
How many bit strings of length ten either start with a 1 bit or end with two bits 00?
DML language is used to ____________.
Which of the following is a scientific computer language?
Which component of MVC architecture deals the database?
Which is a software configuration management concept that helps us to control change without seriously impeding justifiable change?
Which of the following feature is also known as run-time binding or late binding?
Which of the following parser is a top-down parser?
Which search implements stack operation for searching the states?
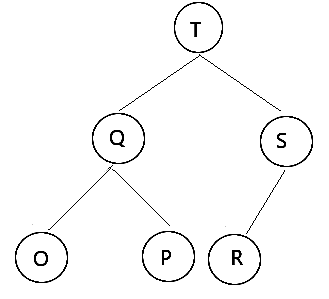
The post-order traversal of a binary tree is OPQRST. Then possible pre-order traversal will be ________.
|
16 docs|120 tests
|



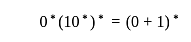
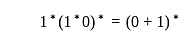
 B
B D = 2 + 3 + 9 = 14 KB
D = 2 + 3 + 9 = 14 KB B
B E = 2 + 3 + 8 = 13 KB
E = 2 + 3 + 8 = 13 KB C
C F = 2 + 4 + 7 = 13 KB
F = 2 + 4 + 7 = 13 KB C
C G = 2 + 4 + 5 = 11 KB
G = 2 + 4 + 5 = 11 KB