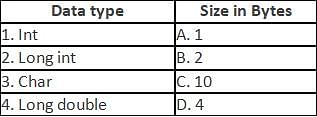
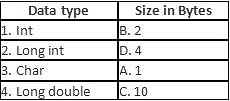
Computer Science: CUET Mock Test - 1 - CUET Humanities MCQ
30 Questions MCQ Test Computer Science Practice Tests: CUET Preparation - Computer Science: CUET Mock Test - 1
Given below are two statements, one labelled as Assertion (A) and the other labelled as Reason (R):
Assertion (A): Database Management System (DBMS) provides a variety of software tools for organising data.
Reason (R): Normalisation is the process for removing data redundancy.
Assertion (A): Database Management System (DBMS) provides a variety of software tools for organising data.
Reason (R): Normalisation is the process for removing data redundancy.
When will the bad_alloc exception be thrown by a program?
A file management system can typically access records from:
Two statements are given below, one is Assertion A and the other is Reason R.
Assertion A: Data is any form of information that can be processed by a computer.
Reason R: Data can be in the form of text, numbers, images, audio, and video.
Directions: Match the contents under List I with those under List II.
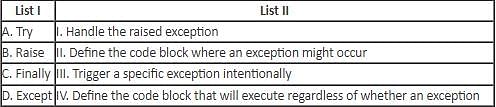
Two statements are given below:
Statement I: The 'x' file access mode allows you to create a new file but will raise an error if the file already exists.
Statement II: The 'a' file access mode allows you to write to the file but not overwrite any existing content.
Testing stack for overflow is performed by comparing the values of the top with value ______.
What is the similarity between the operations on stacks and those on queues, although they are entirely different?
Which of the following is not a limitation of the binary search algorithm?
Two statements are given below, one is Assertion A and the other is Reason R.
Assertion A: Data visualization is the process of creating visual representations of data to communicate information effectively.
Reason R: Data visualization helps to uncover patterns, trends, and insights in data that might not be apparent in raw data.
Directions: Match the contents under List I with those under List II.
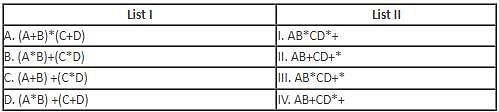
Two statements are given below, one is Assertion A and the other is Reason R.
Assertion A: A LAN (Local Area Network) is a computer network that connects devices within a small geographic area such as a city.
Reason R: LANs typically use wired or wireless connections to enable devices to communicate with each other and share resources such as printers and files.
Which of the following is correct about NOT NULL constraint?
A. NOT NULL constraint demands a column not to accept NULL values.
B. NOT NULL constraint demands a field to always contains some value.
C. One cannot insert a new record with a NULL value, when NOT NULL constraint is specified.
Which of the following statements is false about the adware exploit in hacking?
Two statements are given below:
Statement I: Stack follow Last In First Out (LIFO)
Statement II: Delete is possible from Bottom as well as Top.
Which of the following is not a keyword in SQL?
Which of the following operations in relation algebra requires two relations having the same number of attributes?
Which of the following functions is not performed by DDL?
Two statements are given below:
Statement I: Prefix notation for the (a+b)*(c-d) is +*ab-cd.
Statement II: Postfix notation for the (a+b)*(c-d) is ab+cd-*.
The 'is empty ( )' function can be also be written by using