Computer Science: CUET Mock Test - 2 - CUET Humanities MCQ
30 Questions MCQ Test Computer Science Practice Tests: CUET Preparation - Computer Science: CUET Mock Test - 2
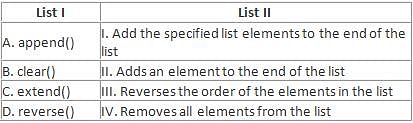
What do we use to define a block of code in Python language?
Two statements are given below, one is Assertion (A) and the other is Reason (R). Read the statements carefully and choose the correct answer.
Assertion (A): Network security is essential to protect computer networks from unauthorised access, use, disclosure, disruption, modification or destruction.
Reason (R): Network security includes measures such as firewalls, encryption, and access control to prevent or detect unauthorised access to network resources.
Assertion (A): Network security is essential to protect computer networks from unauthorised access, use, disclosure, disruption, modification or destruction.
Reason (R): Network security includes measures such as firewalls, encryption, and access control to prevent or detect unauthorised access to network resources.
Referential integrity constraint in a relational database is specified with the help of a _________.
Which among the following SQL commands does not fall under the category of data manipulation language?
Which of the following networking components is called a three-layer switch?
Which of the following operators cannot be used with string data type?
To read the next line of the file from a file object infile, we use _____.
Two statements are given below:
Statement I: Cloud Computing is essential for Internet of Things.
Statement II: Purpose of Internet of Things is to make everyday objects smarter and more connected.
Directions: Match the contents under List I with those under List II.
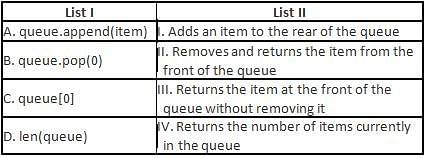
Insertions take place at the rear end of the queue and deletions take place at the 'front' end of the queues. On which principal does this work?
Two statements are given below, one is Assertion (A) and the other is Reason (R). Read the statements carefully and choose the correct answer.
Assertion (A): Infix notation is the most commonly used notation in mathematics.
Reason (R): Infix notation is easy to read and understand, and it is also the default notation used in most programming languages.
Computers manipulate data in many ways, this manipulation is called _____.
What are the two advantages of database management system?
Which method is used to protect online images from hackers?
______ switching is well suited for voice communication while _________switching is better suited for data and other non-voice communication.
Consider a declaration, L = (1, 'Python', '3.14').
Which of the following represents the data type of L?
Which of the following file modes is not valid?
Two statements are given below, one is Assertion (A) and the other is Reason (R). Read the statements carefully and choose the correct answer.
Assertion (A): SQL is a programming language.
Reason (R): SQL supports procedural programming constructs such as loops and conditional statements.
Two statements are given below:
Statement I: An exception is an error that occurs during the execution of a Python program.
Statement II: Exceptions can be handled in Python using the try-catch statement.
A relational database, which is in 3NF, may have undesirable data redundancy because there may exist
____ constraints apply only to individual column.
Directions: Match the contents under List I with those under List II.
We know that RJ-45 is an eight-wire connector that connects a computer to LAN, especially Ethernets. Here, what is the expansion of RJ?
Two statements are given below:
Statement I: Enqueue: adds an element to the rear of the queue.
Statement II: Peek: retrieves the element at the front of the queue without removing it.
Directions: Match the contents under List I with those under List II.
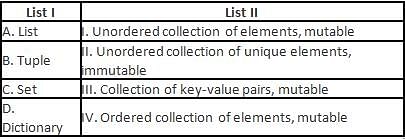
A basic approach to share large amount of data among different organizations is through:
Study the following program:
x = 1
while true:
if x % 5 = = 0:
break print(x) x + = 1
What will be the output of this code?
Which of the following statements is incorrect in the context of binary files?


















