Computer Science: CUET Mock Test - 5 - CUET Humanities MCQ
30 Questions MCQ Test Computer Science Practice Tests: CUET Preparation - Computer Science: CUET Mock Test - 5
Which of the following words cannot be a variable in python language?
Two statements are given below:
Statement I: A ring topology is a type of network topology in which all devices are connected to a single cable.
Statement II: A bus topology is a type of network topology in which all devices are connected to a central hub or switch.
Statement I: A ring topology is a type of network topology in which all devices are connected to a single cable.
Statement II: A bus topology is a type of network topology in which all devices are connected to a central hub or switch.
Identify 'Y', where 'Y' is a computer network comprised by the interconnection of two or more LANs within a limited area.
What is the purpose of the rewind() function?
Directions: Match the contents under List I with those under List II.

What will the following statement do?
FILE *fp1;
Char Tch;
fp1=fopen("TCY.c","r");
while((Tch=getc(fp1)) != EOF)
printf("%c",Tch);
This method returns an integer that specifies the current position of the file object.
What is the output of the following program:
print((1, 2) + (3, 4))
Which of the following is an application of stack?
_____ requires user to specify what data is needed without specifying how to get it.
___ command helps to add new data to the database.
Which of the following best describes a white hat hacker?
Communication bandwidth that has the highest capacity and is used by microwave, cable and fibre optic lines is known as
What is the correct syntax of open() function?
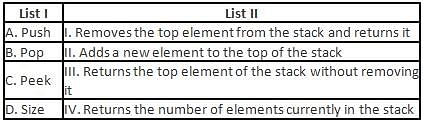
Directions: Match the contents under List I with those under List II.
Which of the following functions is used to read data in a binary file?
Which of the following networks is suited for transferring songs from one mobile to another mobile?
Which of the following is one of the two built-in functions to read a line of text from standard input, which are on the keyboard by default?
Which of the following precedence orders is correct in Python?
Which of the following is not an SQL commands category?
What will be the output of the following python code?
x=['ab', 'cd']
for i in x:
x.append(i.upper())
print(x)
Two statements are given below, one is Assertion (A) and the other is Reason (R). Read the statements carefully and choose the correct answer.
Assertion (A): Queue is a data structure that follows the First-In-First-Out (FIFO) principle.
Reason (R): The last item added to the queue is the first item to be removed from the queue.
Which set of functions can be used to read or write a file randomly?
Ram opened a file in a certain mode. After opening the file, he forgot the mode. The interesting facts about that mode are " If the file doesn't exist, then a new file will be created" and "After opening file in that mode, the file handle will be at the end of the file". Help him identify the correct mode.
When we open an internet site, we see 'www'. What does 'www' stand for?
Secure transfer of data over an unsecured network such as internet can be done using
Consider the usual algorithm for determining whether a sequence of parentheses is balanced. The maximum number of parentheses that appear on the stack AT ANY ONE TIME when the algorithm analyzes: (()(())(()))is:


















