Automated Business Processes: Notes (Part - 3) | Financial Management & Strategic Management for CA Intermediate PDF Download
Regulatory and Compliance Requirements
Major corporations worldwide have used Information Technology (IT) to stay ahead in business. The competitive edge in terms of fast information flow, to support the business, can be an important factor between success and failure.
The efficiency of an enterprise depends on the quick flow of information across the complete supply chain i.e. from the customer to manufacturers to the suppliers. With the globalization of the market place coupled with competition and increasing customer expectations enterprises should address certain fundamental areas like lowering costs in the supply chain, reducing throughput times, optimizing stock levels, improving product quality, improving service to the customer, efficiently handling cross border data flow etc. Today’s IT systems achieve all this.
The core to any enterprise’s success is to have an efficient and effective financial information system to support decision-making and monitoring. The risks, controls and security of such systems should be clearly understood to pass an objective opinion about the adequacy of control in an IT environment.
The Companies Act, 2013
The Companies Act, 2013 has two very important Sections - Section 134 and Section 143, which have a direct impact on the audit and accounting profession.
(i) Section 134
Section 134 of the Companies Act, 2013 on “Financial statement, Board’s report, etc.” states inter alia:
The Directors’ Responsibility Statement referred to in clauses (c e) of sub-section (3) shall state that:
the Directors had taken proper and sufficient care for the maintenance of adequate accounting records in accordance with the provisions of this Act for safeguarding the assets of the company and for preventing and detecting fraud and other irregularities;
- the Directors, in the case of a listed company, had laid down internal financial controls to be followed by the company and that such internal financial controls are adequate and were operating effectively.
Explanation: For the purposes of this clause, the term “Internal Financial Controls” means the policies and procedures adopted by the company for ensuring the orderly and efficient conduct of its business, including adherence to company’s policies, the safeguarding of its assets, the prevention and detection of frauds and errors, the accuracy and completeness of the accounting records, and the timely preparation of reliable financial information.
(ii) Section 143
Section 143, of the Companies Act 2013, on “Powers and duties of auditors and auditing standards” states inter alia:
Section 143(3)(i) contains the Auditor’s Report which shall state that:
“Whether the company has adequate internal financial controls system in place and the operating effectiveness of such controls”;
When we talk in terms of “adequacy and effectiveness of controls”; it refers to the adequacy of the control design and whether the control has been working effectively during the relevant financial year.
Example 20: Let us assume that a company has a sales invoicing control wherein all sales invoices raised by the salesman which is greater than ₹ 50,000/- are reviewed and approved by the sales manager. In terms of the control, design this control may seem adequate. However, if during audit, it was found that, during the year, there were many invoices raised by the salesman which was greater than ₹ 50,000/- and not reviewed and approved by the sales manager. In such a case, although the control design was adequate, the control was not working effectively, due to many exceptions without proper approval.
As per ICAI’s "Guidance Note on Audit of Internal Financial Controls Over Financial Reporting”:
Clause (i) of Sub-section 3 of Section 143 of the Companies Act, 2013 (“The 2013 Act” or “The Act”) requires the auditors’ report to state whether the company has adequate internal financial controls system in place and the operating effectiveness of such controls.
I. Management’s Responsibility
- The Companies Act, 2013 has significantly expanded the scope of internal controls to be considered by the management of companies to cover all aspects of the operations of the company. Clause (e) of Sub-section 5 of Section 134 to the Act requires the directors’ responsibility statement to state that the directors, in the case of a listed company, had laid down internal financial controls to be followed by the company and that such internal financial controls are adequate and were operating effectively.
- Clause (e) of Sub-section 5 of Section 134 explains the meaning of the term, “internal financial controls” as “the policies and procedures adopted by the company for ensuring the orderly and efficient conduct of its business, including adherence to company’s policies, the safeguarding of its assets, the prevention and detection of frauds and errors, the accuracy and completeness of the accounting records, and the timely preparation of reliable financial information.”
- Rule 8(5)(viii) of the Companies (Accounts) Rules, 2014 requires the Board of Directors’ report of all companies to state the details in respect of adequacy of internal financial controls with reference to the financial statements.
- The inclusion of the matters relating to internal financial controls in the directors’ responsibility statement is in addition to the requirement for the directors to state that they have taken proper and sufficient care for the maintenance of adequate accounting records in accordance with the provisions of the 2013 Act, for safeguarding the assets of the company and for preventing and detecting fraud and other irregularities.
II. Auditors’ Responsibility
The auditor’s objective in an audit of internal financial controls over financial reporting is to express an opinion on the effectiveness of the company’s internal financial controls over financial reporting and the procedures in respect thereof are carried out along with an audit of the financial statements. Because a company’s internal controls cannot be considered effective if one or more material weakness exists, to form a basis for expressing an opinion, the auditor should plan and perform the audit to obtain sufficient appropriate evidence to obtain reasonable assurance about whether material weakness exists as of the date specified in management’s assessment. A material weakness in internal financial controls may exist even when the financial statements are not materially misstated.
III. Corporate Governance Requirements
Corporate Governance is the framework of rules and practices by which a board of directors ensures accountability, fairness, and transparency in a company’s relationship with its all stakeholders (financiers, customers, management, employees, government, and the community). The directors of a company are responsible to the shareholders for their actions in directing and controlling the business of the company. Good corporate governance requires establishment of sound internal control practices, risk management, and compliance with relevant laws and standards such as corporate disclosure requirements. Good management practices are one of the important elements of corporate governance. The major elements of corporate governance include management’s commitment, good management practices, functional and effective control environment, transparent disclosure and well defined shareholder rights.
The Corporate Governance framework consists of:
(i) explicit and implicit contracts between the company and the stakeholders for distribution of responsibilities, rights, and rewards.
(ii) procedures for reconciling the sometimes-conflicting interests of stakeholders in accordance with their duties, privileges, and roles, and
(iii) procedures for proper supervision, control, and information-flows to serve as a system of checks-and-balances.
Information Technology Act, 2000 (IT Act)
Cyber Crime: The term ‘Cyber Crime’ finds no mention either in The Information Technology Act 2000 or in any legislation of the Country. Cyber Crime is not different than the traditional crime. The only difference is that in Cyber Crime the computer technology is involved and thus it is a Computer related crime. This can be explained by the following instance:
- Traditional Theft: Thief ‘A’ enters in B’s house and steals an object kept in the house.
- Hacking: Many business organizations store their confidential information in computer system which is often targeted by rivals, criminals and disgruntled employees. Hacking generally refers to unauthorized intrusion into a computer or a network. This may be done by either altering system or security features to accomplish a goal that differs from the original purpose of the system. For example - Mr. A, a cyber-criminal while sitting in his own house, through his computer hacks the computer of Mr. B and steals the data saved in Mr. B’s computer without physically touching the computer or entering in B’s house.
The IT Act, 2000 aims to provide the legal infrastructure for e-commerce in India. And the cyber laws have a major impact for e-businesses and the new economy in India. So, it is important to understand what the various perspectives of the IT Act 2000 (as amended in 2008) are and what it offers.
The Act also aims to provide for the legal framework so that legal sanctity is accorded to all electronic records and other activities carried out by electronic means. The Act states that unless otherwise agreed, an acceptance of contract maybe expressed by electronic means of communication and the same shall have legal validity and enforceability.
I. Some Definitions in IT Act
The IT Act, 2000 defines the terms Access in Section 2(a), computer in Section 2(i), computer network in Section (2j), data in Section 2(o) and information in Section 2(v). These are all the necessary ingredients that are useful to technically understand the concept of Cyber Crime.
2(a) “Access” with its grammatical variations and cognate expressions means gaining entry into, instructing or communicating with the logical, arithmetical, or memory function resources of a computer, computer system or computer network;
2(i) “Computer” means any electronic, magnetic, optical or other high-speed data processing device or system which performs logical, arithmetic, and memory functions by manipulations of electronic, magnetic or optical impulses, and includes all input, output, processing, storage, computer software, or communication facilities which are connected or related to the computer in a computer system or computer network;
2(j) “Computer Network” means the interconnection of one or more Computers or Computer systems or Communication device through-
- the use of satellite, microwave, terrestrial line, wire, wireless or other communication media; and
- terminals or a complex consisting of two or more interconnected computers or communication device whether or not the interconnection is continuously maintained;
2(o) “Data” means a representation of information, knowledge, facts, concepts or instructions which are being prepared or have been prepared in a formalized manner, and is intended to be processed, is being processed or has been processed in a computer system or computer network and may be in any form (including computer printouts magnetic or optical storage media, punched cards, punched tapes) or stored internally in the memory of the computer;
2(v) “Information” includes data, message, text, images, sound, voice, codes, computer programmes, software and databases or microfilm or computer generated microfiche;
In a cyber-crime, computer or the data are the target or the object of offence or a tool in committing some other offence. The definition of term computer elaborates that computer is not only the computer or laptop on our tables, as per the definition computer means any electronic, magnetic, optical or other high speed data processing devise of system which performs logical, arithmetic and memory function by manipulations of electronic, magnetic or optical impulses, and includes all input, output, processing, storage, computer software or communication facilities which are connected or related to the computer in a computer system or computer network. Thus, the definition is much wider to include mobile phones, automatic washing machines, micro-wave ovens etc.
A. Key Provisions of IT Act
Some of key provisions of IT related offences as impacting the banks are given here.
[Section 43] Penalty and compensation for damage to computer, computer system, etc.
If any person without permission of the owner or any other person who is in-charge of a computer, computer system or computer network -
(a) accesses or secures access to such computer, computer system or computer network or computer resource;
(b) downloads, copies or extracts any data, computer database or information from such computer, computer system or computer network including information or data held or stored in any removable storage medium;
(c) introduces or causes to be introduced any computer contaminant or computer virus into any computer, computer system or computer network;
(d) damages or causes to be damaged any computer, computer system or computer network, data, computer database or any other programmes residing in such computer, computer system or computer network;
(e) disrupts or causes disruption of any computer, computer system or computer network;
(f) denies or causes the denial of access to any person authorized to access any computer, computer system or computer network by any means;
(g) provides any assistance to any person to facilitate access to a computer, computer system or computer network in contravention of the provisions of this Act, rules or regulations made there under;
(h) charges the services availed of by a person to the account of another person by tampering with or manipulating any computer, computer system, or computer network;
(i) destroys, deletes or alters any information residing in a computer resource or diminishes its value or utility or affects it injuriously by any means;
(j) steal, conceals, destroys or alters or causes any person to steal, conceal, destroy or alter any computer source code used for a computer resource with an intention to cause damage, he shall be liable to pay damages by way of compensation to the person so affected.
Explanation - For the purposes of this section -
(i) "computer contaminant" means any set of computer instructions that are designed—
(a) to modify, destroy, record, transmit data or programme residing within a computer, computer system or computer network; or
(b) by any means to usurp the normal operation of the computer, computer system, or computer network;
(ii) "computer database" means a representation of information, know-ledge, facts, concepts or instructions in text, image, audio, video that are being prepared or have been prepared in a formalized manner or have been produced by a computer, computer system or computer network and are intended for use in a computer, computer system or computer network;
(iii) "computer virus" means any computer instruction, information, data or programme that destroys, damages, degrades or adversely affects the performance of a computer resource or attaches itself to another computer resource and operates when a programme, data or instruction is executed or some other event takes place in that computer resource;
(iv) "damage" means to destroy, alter, delete, add, modify or rearrange any computer resource by any means;
(v) "computer source code" means the listing of programmes, computer commands, design and layout and programme analysis of computer resource in any form.
[Section 43A] Compensation for failure to protect data
Where a body corporate, possessing, dealing or handling any sensitive personal data or information in a computer resource which it owns, controls or operates, is negligent in implementing and maintaining reasonable security practices and procedures and thereby causes wrongful loss or wrongful gain to any person, such body corporate shall be liable to pay damages by way of compensation to the person so affected.
Explanation - For the purposes of this section -
(i) "body corporate" means any company and includes a firm, sole proprietorship or other association of individuals engaged in commercial or professional activities;
(ii) "reasonable security practices and procedures" means security practices and procedures designed to protect such information from unauthorized access, damage, use, modification, disclosure or impairment, as may be specified in an agreement between the parties or as may be specified in any law for the time being in force and in the absence of such agreement or any law, such reasonable security practices and procedures, as may be prescribed by the Central Government in consultation with such professional bodies or associations as it may deem fit;
(iii) "sensitive personal data or information" means such personal information as may be prescribed by the Central Government in consultation with such professional bodies or associations as it may deem fit.
[Section 65] Tampering with Computer Source Documents
Whoever knowingly or intentionally conceals, destroys or alters or intentionally or knowingly causes another to conceal, destroy or alter any computer source code used for a computer, computer program, computer system or computer network, when the computer source code is required to be kept or maintained by law for the time being in force, shall be punishable with imprisonment up to three years, or with fine which may extend up to 2 lakh rupees, or with both. The explanation clarifies ‘Computer Source Code” means the listing of programme, Computer Commands, Design and layout and program analysis of computer resource in any form.
[Section 66] Computer Related Offences
If any person, dishonestly, or fraudulently, does any act referred to in Section 43, he shall be punishable with imprisonment for a term which may extend to three years or with fine which may extend to 5 lakh rupees or with both.
[Section 66B] Punishment for dishonestly receiving stolen computer resource or communication device
Whoever dishonestly receives or retains any stolen computer resource or communication device knowing or having reason to believe the same to be stolen computer resource or communication device, shall be punished with imprisonment of either description for a term which may extend to three years or with fine which may extend to rupees one lakh or with both.
[Section 66C] Punishment for identity theft
Whoever, fraudulently or dishonestly make use of the electronic signature, password or any other unique identification feature of any other person, shall be punished with imprisonment of either description for a term which may extend to three years and shall also be liable to fine which may extend to rupees one lakh.
[Section 66D] Punishment for cheating by personation by using computer resource
Whoever, by means of any communication device or computer resource cheats by personation, shall be punished with imprisonment of either description for a term which may extend to three years and shall also be liable to fine which may extend to one lakh rupees.
[Section 66E] Punishment for violation of privacy
Whoever, intentionally or knowingly captures, publishes or transmits the image of a private area of any person without his or her consent, under circumstances violating the privacy of that person, shall be punished with imprisonment which may extend to three years or with fine not exceeding two lakh rupees, or with both.
[Section 66F] Punishment for cyber terrorism
- Whoever -
(A) with intent to threaten the unity, integrity, security or sovereignty of India or to strike terror in the people or any section of the people by –
(i) denying or cause the denial of access to any person authorized to access computer resource; or
(ii) attempting to penetrate or access a computer resource without authorization or exceeding authorized access; or
(iii) introducing or causing to introduce any computer contaminant, and by means of such conduct causes or is likely to cause death or injuries to persons or damage to or destruction of property or disrupts or knowing that it is likely to cause damage or disruption of supplies or services essential to the life of the community or adversely affect the critical information infrastructure specified under section 70; or
(B) knowingly or intentionally penetrates or accesses a computer resource without authorization or exceeding authorized access, and by means of such conduct obtains access to information, data or computer database that is restricted for reasons of the security of the State or foreign relations; or any restricted information, data or computer database, with reasons to believe that such information, data or computer database so obtained may be used to cause or likely to cause injury to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, public order, decency or morality, or in relation to contempt of court, defamation or incitement to an offence, or to the advantage of any foreign nation, group of individuals or otherwise, commits the offence of cyber terrorism.
(2) Whoever commits or conspires to commit cyber terrorism shall be punishable with imprisonment which may extend to imprisonment for life.
[Section 67] Punishment for publishing or transmitting obscene material in electronic form
Whoever publishes or transmits or causes to be published or transmitted in the electronic form, any material which is lascivious or appeals to the prurient interest or if its effect is such as to tend to deprave and corrupt persons who are likely, having regard to all relevant circumstances, to read, see or hear the matter contained or embodied in it, shall be punished on first conviction with imprisonment of either description for a term which may extend to three years and with fine which may extend to five lakh rupees and in the event of a second or subsequent conviction with imprisonment of either description for a term which may extend to five years and also with fine which may extend to ten lakh rupees.
[Section 67A] Punishment for publishing or transmitting of material containing sexually explicit act, etc. in electronic form
Whoever publishes or transmits or causes to be published or transmitted in the electronic form any material which contains sexually explicit act or conduct shall be punished on first conviction with imprisonment of either description for a term which may extend to five years and with fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees.
[Section 67B] Punishment for publishing or transmitting of material depicting children in sexually explicit act, etc. in electronic form
Whoever, -
(a) publishes or transmits or causes to be published or transmitted material in any electronic form which depicts children engaged in sexually explicit act or conduct; or
(b) creates text or digital images, collects, seeks, browses, downloads, advertises, promotes, exchanges or distributes material in any electronic form depicting children in obscene or indecent or sexually explicit manner; or
(c) cultivates, entices or induces children to online relationship with one or more children for and on sexually explicit act or in a manner that may offend a reasonable adult on the computer resource; or
(d) facilitates abusing children online; or
(e) records in any electronic form own abuse or that of others pertaining to sexually explicit act with children, shall be punished on first conviction with imprisonment of either description for a term which may extend to five years and with a fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees:
PROVIDED that provisions of Section 67, Section 67A and this section does not extend to any book, pamphlet, paper, writing, drawing, painting representation or figure in electronic form -
(i) the publication of which is proved to be justified as being for the public good on the ground that such book, pamphlet, paper writing, drawing, painting, representation or figure is in the interest of science, literature, art or learning or other objects of general concern; or
(ii) which is kept or used for bona fide heritage or religious purposes.
Explanation - For the purposes of this section, "children" means a person who has not completed the age of 18 years.
B. Computer Related Offences
Let us look at some common cyber-crime scenarios which can attract prosecution as per the penalties and offences prescribed in Information Technology Act, 2000 (amended via 2008).
- Harassment via fake public profile on social networking site: A fake profile of a person is created on a social networking site with the correct address, residential information or contact details but he/she is labelled as ‘prostitute’ or a person of ‘loose character’. This leads to harassment of the victim. Section 67 of the IT Act, 2000 is applicable here.
- Email Account Hacking: If victim’s email account is hacked and obscene emails are sent to people in victim’s address book. Sections 43, 66, 66A, 66C, 67, 67A and 67B of IT Act, 2000 are applicable in this case.
- Credit Card Fraud: Unsuspecting victims would use infected computers to make online transactions. Sections 43, 66, 66C, 66D of IT Act, 2000 are applicable in this case.
- Web Defacement: The homepage of a website is replaced with a pornographic or defamatory page. Government sites generally face the wrath of hackers on symbolic days. Sections 43 and 66 of IT Act and Sections 66F and 67 of IT Act, 2000 also apply in some cases.
- Introducing Viruses, Worms, Backdoors, Rootkits, Trojans, and Bugs: All these are some sort of malicious programs which are used to destroy or gain access to some electronic information. Sections 43 and 66 of IT Act, 2000 are applicable in this case.
- Cyber Terrorism: Cyber terrorism is the terrorism conducted in cyberspace, where the criminals attempt to damage or disrupt computer systems or telecommunication services. Examples are hacking into computer systems, introducing viruses to vulnerable networks, web site defacing, denial-ofservice attacks, or terroristic threats made via electronic communication. Many terrorists use virtual (Drive, FTP sites) and physical storage media (USB’s, hard drives) for hiding information and records of their illicit business. Sections 43, 66, 66A of IT Act, 2000 are applicable in this case.
Online sale of illegal Articles: Where sale of narcotics, drugs, weapons and wildlife is facilitated by the Internet.
Cyber Pornography: Among the largest businesses on Internet, pornography may not be illegal in many countries, but child pornography is. Sections 67, 67A and 67B of the IT Act, 2000 are applicable in this case.
Phishing and Email Scams: Phishing involves fraudulently acquiring sensitive information through masquerading oneself as a trusted entity (e.g. usernames, Passwords, credit card information). Sections 66, 66C and 66D of IT Act, 2000 are applicable in this case.
Theft of Confidential Information: Many business organizations store their confidential information in computer systems. This information is targeted by rivals, criminals and disgruntled employees. Sections 43, 66 and 66B of IT Act, 2000 are applicable in this case.
Source Code Theft: A Source code generally is the most coveted and important “crown jewel” asset of a company. Sections 43, 65, 66 and 66B of IT Act, 2000 are applicable in this case.
C. Advantages of Cyber Laws
The IT Act 2000 attempts to change outdated laws and provides ways to deal with cyber-crimes. We need such laws so that people can perform purchase transactions over the internet without fear of misuse. The Act offers the much-needed legal framework so that information is not denied legal effect, validity or enforceability, solely on the ground that it is in the form of electronic records.
D. Privacy of Online Data
When people access the Web, they often entrust vital personal information such as their name, address, credit card number, etc. to their Internet Service Providers and to the websites they accessed. This information may fall into wrong hands and may be used for illegitimate purposes. The organizations that collect and manage the personal information of people must also protect it against misuse. The collection of personal information by an organization is an important issue related to the privacy of online data. Privacy laws vary in different countries. Multi-national companies often receive information in one country and process this information in some other country where privacy laws are altogether different. Therefore, in a globalized world it becomes very challenging for these companies to ensure uniform standards of privacy.
The main principles on data protection and privacy enumerated under the IT Act, 2000 are as follows:
- defining ‘data’, ‘computer database’, ‘information’, ‘electronic form’, ‘originator’, ‘addressee’ etc.
- creating civil liability if any person accesses or secures access to computer, computer system or computer network
- creating criminal liability if any person accesses or secures access to computer, computer system or computer network
- declaring any computer, computer system or computer network as a protected system
- imposing penalty for breach of confidentiality and privacy
- setting up of hierarchy of regulatory authorities, namely adjudicating officers, the Cyber Regulations Appellate Tribunal etc.
Example 21: A sample privacy policy is given below which highlights key aspects of how and what type of information is collected from the customer, how it is used and secured and options for user providing the information:
“At ABC Ltd., we take your privacy very seriously. Because of this, we want to provide you with explicit information on how we collect, gather and identify information during your visit to our site. This information may be expanded or updated as we change or develop our site. For this reason, we recommend that you review this policy from time-to-time to see if anything has changed. Your continued use of our site signifies your acceptance of our privacy policy.”
Personally, identifiable information refers to information that tells us specifically who you are, such as your name, phone number, email or postal address. In many cases, we need this information to provide the personalized or enhanced service that you have requested. The amount of personally identifiable information that you choose to disclose to ABC Ltd. is completely up to you. The only way we know something about you personally is if you provide it to us in conjunction with one of our services.
What information do we collect and how do we use it?
- ABC Ltd. collects information on our users by your voluntary submissions (e.g., when you sign up for a white paper or request product information).We also collect, store and accumulate certain non-personally identifiable information concerning your use of this web site, such as which of our pages are most visited.
- The information ABC Ltd. collects is used in a variety of ways: for internal review; to improve the content of the site, thus making your user experience more valuable; and to let you know about products and services of interest.
- If you have provided us your email address, ABC Ltd. periodically sends promotional emails about products offered by us. If you do not wish to receive email information from ABC Ltd. please let us know by emailing us.
- ABC Ltd. does not sell, rent, or give away your personal information to third parties. By using our web site, you provide consent to the collection and use of the information described in this by Privacy Policy of ABC Ltd.
IV. Sensitive Personal Data Information (SPDI)
Reasonable Security Practices and Procedures and Sensitive Personal Data or Information Rules 2011 formed under Section 43A of the Information Technology Act 2000 define a data protection framework for the processing of digital data by Body Corporate.
Scope of Rules: Currently the Rules apply to Body Corporate and digital data. As per the IT Act, Body Corporate is defined as “Any company and includes a firm, sole proprietorship or other association of individuals engaged in commercial or professional activities.”
The present scope of the Rules excludes from its purview several actors that do or could have access to Big Data or use Big Data practices. The Rules would not apply to government bodies or individuals collecting and using Big Data. Yet, with technologies such as IoT (Internet of Things) and the rise of Smart Cities across India – a range of government, public, and private organizations and actors could have access to Big Data.
Definition of Personal and Sensitive Personal data: Rule 2(i) defines personal information as “information that relates to a natural person which either directly or indirectly, in combination with other information available or likely to be available with a body corporate, is capable of identifying such person.”
Rule 3 defines sensitive personal information as Passwords; Financial information; Physical/physiological/mental health condition; Sexual orientation; Medical records and history; and Biometric information.
The present definition of personal data hinges on the factor of identification (data that is capable of identifying a person). Yet this definition does not encompass information that is associated to an already identified individual - such as habits, location, or activity.
The definition of personal data also addresses only the identification of ‘such person’ and does not address data that is related to a particular person but that also reveals identifying information about another person - either directly - or when combined with other data points. By listing specific categories of sensitive personal information, the Rules do not account for additional types of sensitive personal information that might be generated or correlated through the use of Big Data analytics.
Importantly, the definitions of sensitive personal information or personal information do not address how personal or sensitive personal information - when anonymized or aggregated – should be treated.
Consent to collect: Rule 5(1) requires that Body Corporate should, prior to collection, obtain consent in writing through letter or fax or email from the provider of sensitive personal data regarding the use of that data.
In a context where services are delivered with little or no human interaction, data is collected through sensors, data is collected on a real time and regular basis, and data is used and re-used for multiple and differing purposes - it is not practical, and often not possible, for consent to be obtained through writing, letter, fax, or email for each instance of data collection and for each use.
Consent to Disclosure: Rule 6 provides that Disclosure of sensitive personal data or information by body corporate to any third party shall require prior permission from the provider of such information, who has provided such information under lawful contract or otherwise, unless such disclosure has been agreed to in the contract between the body corporate and provider of information, or where the disclosure is necessary for compliance of a legal obligation.
Illustration 1:
ABC Ltd. is engaged in the business of producing consumer durable products. It is facing the problem of poor customer service due to its broken, inefficient, and manual processes. The customers of the company are becoming more demanding with respect to higher quality of products and delivery time.
To remain competitive in the market and to overcome the issues faced by its customers, the company decided to optimize and streamline its essential business processes using the latest technology to automate the functions involved in carrying out these essential processes. The management of the company is very optimistic that with automation of business processes, it will be able to extract maximum benefit by using the available resources to their best advantage. Moreover, with automation the company will be able to integrate various processes and serve its customers better and faster. The management is aware that the automation of business processes will lead to new types of risks in the company’s business. The failure or malfunction of any critical business process will cause significant operational disruptions and materially impact its ability to provide timely services to its customers. The management of ABC Ltd. adopted different Enterprise Risk Management (ERM) strategies to operate more effectively in environment filled with risks. To reduce the impact of these risks, the company also decided to implement necessary internal controls.
Read the above illustration carefully and answer the following questions:
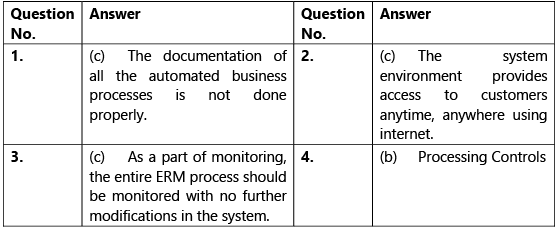
- The processes automated by ABC Ltd. are susceptible to many direct and indirect challenges. Which of the following factor cannot be considered valid in case the company fails to achieve the desired results?
(a) The business processes are not well thought or executed to align with business objectives.
(b) The staff may perceive automated processes as threat to their jobs.
(c) The documentation of all the automated business processes is not done properly.
(d) The implementation of automated processes in the company may be an expensive proposition. - The processes automated by ABC Ltd. are technology driven. The dependence on technology in key business processes exposed the company to various internal as well as external threats. According to you, external threats leading to cyber-crime in BPA is because:
(a) Organizations may have a highly-defined organization structure with clearly defined roles, authority and responsibility.
(b) There may not be one but multiple vendors providing different services.
(c) The system environment provides access to customers anytime, anywhere using internet.
(d) The dependence on technology is insignificant. - The management of ABC Ltd. adopted a holistic and comprehensive approach of Enterprise Risk Management (ERM) framework by implementing controls across the company. Identify the false statement w.r.t components of ERM framework.
(a) As a part of event identification, potential events that might have an impact on the entity should be identified.
(b) As a part of risk assessment component, identified risks are analyzed to form a basis for determining how they should be managed.
(c) As a part of monitoring, the entire ERM process should be monitored with no further modifications in the system.
(d) As a part of control activities, policies and procedures are established and executed to help ensure that the risk responses that management selected are effectively carried out. - The management of ABC Ltd. implemented different Information Technology General Controls (ITGCs) across different layers of IT environment with an objective to minimize the impact of risks associated with automated processes. Which of the following is not an example of ITGC?
(a) Information Security Policy
(b) Processing Controls
(c) Backup, Recovery and Business Continuity
(d) Separation of key IT functions
Illustration 2:
DXN Ltd. is engaged in manufacturing consumer products for women. The company released a new product recently which met with unexpected success. The company was established as a market leader in that product. The growing volume of sales transactions started to put a strain on company’s internal processes. The company employed 300 more employees to ensure that the customers are served better and faster. But with the increase in number of monthly transactions to 1.5 million, the manual processes which were being followed by the company at present, were holding it back. The company was not able to meet consumer demands even after employing addition 300 employees. The management consultant Mr. X of DXN Ltd. advised to automate the key business processes of the company to handle large volume of transactions to meet the expectations of its customers and maintain its competitive edge in the market.
Mr. X gathered extensive information about the different activities involved in the current processes followed by DXN Ltd. like - what the processes do, the flow of various processes, the persons who are in charge of different processes etc. The information so collected helped him in understanding the existing processes such as flaws, bottlenecks, and other less obvious features within the existing processes. Based on the information gathered about the current processes, Mr. X prepared various flowcharts depicting how various processes should be performed after automation and submitted his report to the management covering the following points:
- The major benefits of Business Process Automation;
- The processes that are best suited to automation;
- Challenges that DXN Ltd. may face while implementing automated processes;
- Risks involved in Business Process Automation and how the management should manage these risks
Read the above illustration carefully and answer the following Questions:
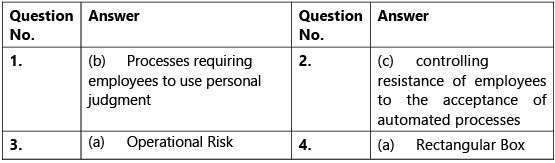
- As the DXN Ltd. was implementing the automated processes for the first time, the consultant suggested not to automate all the processes at a time and automate only critical processes which would help the company to handle large volume of transactions. Which of the following business processes are not best suited to automation:
(a) Processes involving repetitive tasks
(b) Processes requiring employees to use personal judgment
(c) Time sensitive processes
(d) Processes having significant impact on other processes and systems - While understanding the criticality of various business processes of DXN Ltd., the consultant Mr. X documented the current processes and identified the processes that needed automation. However, documentation of existing processes does not help in _______.
(a) providing clarity on the process
(b) determining the sources of inefficiency, bottlenecks, and problems
(c) controlling resistance of employees to the acceptance of automated processes
(d) designing the process to focus on the desired result with workflow automation - When DXN Ltd. decided to adopt automation to support its critical business processes, it exposed itself to number of risks. One risk that the automated process could lead to breakdown in internal processes, people and systems is a type of _____.
(a) Operational Risk
(b) Financial Risk
(c) Strategic Risk
(d) Compliance Risk - Mr. X of DXN Ltd. prepared various flowcharts depicting how various processes should be performed after automation and submitted his report to the management. The flowcharting symbol that he used to depict processing step is ______.
(a) Rectangular Box
(b) Diamond
(c) Oval
(d) Line
Summary
Technology is the enabler of business process automation (BPA), and it can automate business processes to the point where human intervention is unnecessary. Automation can save time and money, delight customers who no longer must wait in line for a person to assist them with a transaction and avoid human errors.
But not every business process is a good fit for automation, so it’s incumbent upon companies to determine which processes are best suited to automation and which ones are best handled manually. How do companies select which business processes to automate? Companies start by looking at the strategic and operating drivers for process improvement in their organizations and industries. For instance, in today’s global market, nearly every company is feeling pressure to get goods to market quickly and to be first to market whenever possible. In a highly pricecompetitive environment, companies are also under great pressure to economize their operations to improve their profitability. Consequently, companies look to automate business processes that are time and resource intensive operationally, that are subject to human error, and that can be accelerated with automated process improvements achievable through computers and technology. If automating business processes speeds product to market, improves revenue, reduces operating expenses so margins can improve and brings efficiency and effectiveness in the enterprise, the case for automation is substantiated.
Enhanced automated controls within accounting and transaction recording applications can control risk much before they can actually materialize. In addition, companies are under added pressure as regulators, rating agencies and stock exchanges drive improved standards of risk management at an enterprise level, with special emphasis on good corporate governance. Enterprises are therefore in the process of adopting a variety of automated controls to help them combat risk and advance to a proactive approach that reduces the incidence of errors or focuses on them well before the point of impact.
By definition, an automated control is a mechanism or device inside an application, interface or appliance that enforces or controls a rule-set or validation on one or more conditions inside a process. A very simple example of an automated control in accounting parlance is a “drop-down list” of vendors to ensure that the user selects one of the multiple choices provided therein. This would ensure that the transaction is conducted with the authorized set of vendors, which have been set elsewhere by another team that is responsible for vendor on-boarding. Similarly, there are several applications of automated controls in accounting with the prime objective of:
- Mitigating/Eliminating Frauds through enforced segregation of duties and ensuring adherence to a set of delegation of financial powers.
- Business Process Improvement through elimination of manual controls thereby enhancing efficiency and reducing costs.
- Reduced Audit Costs by shifting from “transaction” audit to “controls” audit.
- Adherence to Regulatory Compliance requirements such as Companies Act 2013, IT Act, and the likes, entailing testing of key controls through sampling techniques, which again can be reduced substantially by monitoring the effectiveness of automated controls.
IT is primary driver for enterprises to survive and thrive in this digital age. Regulators have recognized critical importance of IT and hence facilitate digital economy by providing legislative framework and mandating compliances as required. The IT Act, 2000 and Companies have been updated to meet the needs of digital economy. Protection of privacy and personal information is also mandated. Cyber-crime is a reality of digital world when operates without geographical boundaries. Various types of computer related defines have been defined and penalties specified for these offences. Digitization of business processes should for modern enterprises and this leads to new risks which should be mitigated by implementing appropriate controls.
What you've learned?
- Build an understanding on the concepts of Business Process, its automation and implementation.
- Understand concepts, flow and relationship of internal and automated controls.
- Acknowledge risks and controls of various business processes.
- Grasp the understanding on the structure and flow of business processes, related risks and controls.
- Comprehend the specific regulatory and compliance requirements of The Companies Act, 2013 and The Information Technology Act as applicable to Enterprise Information Systems.
FAQs on Automated Business Processes: Notes (Part - 3) - Financial Management & Strategic Management for CA Intermediate
| 1. What are regulatory and compliance requirements for automated business processes? |  |
| 2. How do regulatory and compliance requirements impact automated business processes? |  |
| 3. What are some common regulatory and compliance requirements for automated business processes? |  |
| 4. How can organizations ensure compliance with regulatory and compliance requirements for automated business processes? |  |
| 5. What are the consequences of non-compliance with regulatory and compliance requirements for automated business processes? |  |