Internet and Viruses | Cyber Olympiad for Class 9 PDF Download
Today, computer is used in many offices and homes to share data and programs among various computers with the advancement of data communication facilities becomes The communication between computers has increased and has extended the power of computer beyond the computer room. Now, a user sitting at one place can communicate with computers of any remote area through communication channel. The aim of this chapter is to introduce you to various aspects of computer network.
Internet
The Internet is a network of networks. Millions of computers all over the world are connected through the Internet. Computer users on the Internet can contact one another anywhere in the world. If your computer is connected to the Internet, you can connect to millions of computers. You can gather information and distribute your data. It is very much similar to the telephone connection where you can talk with any person anywhere in the world. In the Internet, a huge resource of information is accessible to people across the world. Information in every field starting from education, science, health, medicine, history, and geography to business, news, etc. can be retrieved through the Internet. You can also download programs and software packages from anywhere in the world. Due to the tremendous information resources the Internet can provide, it is now indispensable to every organization.
The Internet has the following characteristics:
- Internet is a global system of interconnected computer networks.
- Internet uses the standard Internet Protocol (TCP/IP).
- Every computer in internet is identified by a unique IP address. IP Address is a unique set of numbers that identifies a computer’s location.
- A special computer Domain Name Server, DNS, is given to the IP Address so that user can locate a computer by a name.
- Internet is accessible to every user all over the world.
Origin of Internet
In 1969, Department of Defense (DOD) of USA started a network called ARPANET (Advanced Research Projects Administration Network) with one computer at California and three at Utah. Later on,other universities and R&D institutions were allowed to connect to the Network. ARPANET quickly grew to encompass the entire American continent and became a huge success. Every university in the country wanted to become a part of ARPANET. So the network was broken into two smaller parts called MILNET for managing military sites and ARPANET (smaller) for managing non-military sites. Around 1980, NSFNET (National Science Foundation Network) was created. With the advancement of modern communication facilities, other computers were allowed to be linked with any computer of NSFNET. By 1990, many computers were linked to NSFNET giving birth to the Internet.
How the Internet functions
Internet is not a government organization. The ultimate authority of the Internet is the Internet Society. This is a voluntary membership organization whose purpose is to promote global information exchange. the Internet has more than one million computers attached to it.
Web Browser
A Web browser is a software application used to locate, retrieve and also display content on the World Wide Web, including Web pages, images, video and other files. As a client/server model, the browser is the client run on a computer that contacts the Web server and requests information. The Web server sends the information back to the Web browser which displays the results on the computer or other Internet-enabled devices that support a browser.
The most popular web browsers used today are the following.

Internet Explorer (IE)
Internet Explorer (sometimes referred to as Microsoft Internet Explorer) is a web browser. This Explorer is a graphical web browser developed by Microsoft and included as part of the Microsoft Windows operating systems. It was first released with Windows 95 starting in 1995. Tool Bar The Internet Explorer tool bar looks like the one shown below. The tool bar is essential for navigation and frequently performed functions.
Tool Bar
The Internet Explorer tool bar looks like the one shown below. The tool bar is essential for navigation and frequently performed functions
- Back eturns you to the previous page.
- Forward goes forward again after you have gone back a few pages.
- Stop stops loading a page you have selected (useful for files that are very large)
- Refresh reloads the page you requested, ignores contents of your local cache (to ignore higher levels of cache, Ctrl + Refresh button)
- Home returns you to the homepage
- Search links you to a search engine (more about searching later)
- Favorites list sites you have been to and bookmarked because you thought you might revisit the page.
- History: records where you have been by day, week and month for fast return
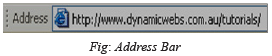
Address Bar
The address or URL of the current page you are browsing appears in the “Address Bar” below the tool bar. You can click here at any time and overwrite this address with another. Leave the “http://” as it is required at the start of the URL, it indicates that the browser is to use hypertext transfer protocol to request the web page. URL stands for “Uniform Resource Iocator”. In non-technical terms, you can think of it as simply the address of a web page.
Caching
As you browse the web, your machine saves HTML files and images that you request. This process is called “caching”. Internet Explorer calls cached files “Temporary Internet Files”. Caching is designed to speed up your experience on the web. Caching occurs on your machine and sometimes on the servers of your Internet Service Provider. If you own a web site or make changes to a web site, you may have to refresh your browser to see your changes. The quick way to do this is to click the refresh button on your browser. This sometimes does not work if other servers above you have cached your page. To go through this, and back to the original server, press Ctrl + F5 (or hold Shift while pressing the Refresh button). You can control your caching option by going through Tools > Internet Options. On the general tab, you will see an area called Temporary Internet Files.
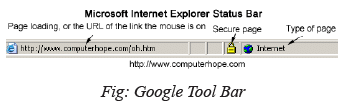
Status Bar
The bottom portion of the Internet browser and other program window displays the current status of the web page or window currently being viewed. For example, in Internet Explorer, it displays whether or not the page is secure, what is currently being loaded on the page, the page, and the certificate. Other browsers, such as Netscape and Opera, also include a status bar, although it may not display the same information. Below is an example image of what the Microsoft Internet Explorer status bar may look like.
Web Directory
A web directory or link directory is a directory on the World Wide Web. It specializes in linking to other websites and in categorizing those links. A web directory is not a search engine and does not display lists of web pages based on keywords; instead, it lists websites by category and subcategory. Most web directory entries are also not found by web crawlers but by humans.
Directories have various features in listing and often depend upon the price paid for inclusion.
Some features of directories are :
- Free submission: there is no charge for the review and listing of the site.
- Reciprocal link: a link back to the directory must be added on the submitted site in order to get listed in the directory.
- No Reciprocal link: a web directory where you submit your links for free and no adding link back to your website is required.
- Paid submission: a one-time or recurring fee is charged for reviewing/listing the submitted link.
- No follow: It means that search engines will give no weight to the link.
- Featured listing: the link is given a premium position in a category (or multiple categories) or other sections of the directory, such as the homepage. Sometimes it is called sponsored listing.
- Bid for position: where sites are ordered based on bids.
- Affiliate links: where the directory earns commission for referred customers from the listed websites.
How to Search
If you do a search on one word called a keyword in the language of the Internet, you will get thousands of links. So you would consider adding a second keyword to your keyword to make your search more specific. For example, instead of just “guitar music”, try “classical guitar music” which is likely to restrict the number of pages that come back as result. Here are some common ways to restrict or target your searches.
The Exact Phrase
Also make use of single quotes in place of quotations marks.
Place quotations around your keywords e.g. “Indian wildlife” will find occurrences of the words “Indian” and “wildlife” beside each other, in the specified order.
All of the Words
Just use two or three keywords together without quotation marks or place an “AND” between your keywords.
For examples: Indian wildlife or Indian AND wildlife will find web pages containing the words ‘Indian’ and ‘wildlife’ on the same page, but not side by side or in the specified order. In other words, “all of the words”.
Any of the Words
Place ‘OR’ between your keywords to find sites containing ‘Indian’ or ‘wildlife’ or both. In other words, “any of the words”
‘Required’ and ‘Prohibited’ Search Words
Attaching one of the following operators will either require or prohibit words from appearing in the search results. In other words,
- + or “must contain”
Attaching a ‘+’ to a word requires that the word be found in all of the search results. compare: Indian and Indian + wildlife - - or “must not contain”
Attaching a – in front of a word requires that the word not be found in any of the search results. Compare: Indian and Indian -culture
E-mail (Electronic Mail)
E-mail or electronic mail is one of the most popular uses of the Internet today. E-mail allows you to exchange messages with friends who are connected to the internet anywhere in the world. The advantages of e-mail over regular mail is that it is free, it is delivered almost instantly and you can attach all types of files to your messages. The following tutorials will introduce you to e-mail and help you set up your own e-mail account.
E-mail address
Similar to Web pages, all e-mail accounts have unique addresses indicating which computer to send are mail to. For email, an address usually has two parts, your user ID (usually your name) and the identity of your e-mail service. These two parts are separated by the symbol @.
The following e-mail address demonstrates these parts:
marifs 29@hotmail.com
marifs 29
This is called your user ID and is used when you sign in to your e-mail service. Notice how “_” is used to separate words in the name. Because e-mail names cannot contain spaces, the symbol “_” is used to connect many words into one long word.
@
This is an “at” sign. It separate’s the user name from the name of the e-mail service he/she is using.
hotmail.com
This indicates which e-mail service you are using and its location on the web. This address is for Hotmail, Microsoft’s free e-mail service.
Difference between the World Wide Web and the Internet
- The World Wide Web (The Web) is only a port of what makes up the internet, but it is the fastest growing part of the internet. Through web, people, organizations and companies can publish information for other people to see. This makes the Web a very useful tool for finding information on just about any topic.
- The Web is a large number of computer documents or “Web pages” that are stored on computers around the world and are connected to one another using hyperlinks. These Web pages can be seen by anyone through their computer’s “Web Browser”, which is the program you are using now.
- A group of Web pages that follow the same theme and are connected together with hyperlinks is called a “Website”. Websites and Web pages are written in a coding language that makes it possible to add pictures, sound and interactivity to plain old text, making people’s reading experience more exciting.
Briefcase
In Microsoft Windows, the Briefcase is a special folder that supports simple two-way file synchronization between itself and another folder. The Briefcase is designed for mobile PC users so that they may transfer it to a removable drive and could synchronize it with the computer to which the removable drive is attached.While the file management tasks are performed by Windows Explorer, the briefcase behaves just like another folder, i.e. with support for copy-paste and drag-and-drop options. It has additional functions and toolbar buttons for updating out-of-sync files. The Windows Briefcase was first introduced in Windows 95.
Virus
Virus is a short piece of computer code which enters your system without your knowledge and replicates. Since it is capable of self replicating, it multiplies quickly taking up the entire memory space. When the memory space is used up, the computer cannot perform any function and it gets stalled. Computer viruses are called viruses because they pass from computer to computer like a biological virus passes from person to person.
More dangerous virus is the one which can transmit itself from one network to another and causing security breach in the system.
- E-mail viruses: An e-mail virus is transmitted as an attachment in e-mails. It usually replicates itself by automatically mailing itself to dozens of people in the victim’s e-mail address book. Some e-mail viruses launch into your system when you view the infected message in the preview pane of your e-mail.
- Trojan horses: Trojan horse is simply a non self-replicating computer program. The program may claim to perform a task or play a game but instead damages your system when you run it. It is capable of erasing the hard disk.
- Worms: A worm is a small piece of coded program that uses computer networks to replicate itself. A copy of the worm scans the network for another machine that has a specific security loophole. It copies itself to the new machine using the security hole, and then starts multiplying there as well thus bringing down the system.
Worm
A worm is a computer program that is capable of copying itself from one machine to another. Worms use up computer processing time when they replicate and do considerable damage. A worm called Code Red made huge headlines in 2001. Experts predicted that this worm could effectively bring the internet service to a halt.
How to protect your system against a virus?
To protect your system against a virus, the system needs to have an updated anti virus software. Some of the anti virus software are Avast, Kaspersky, McAfee and Norton. One can also avoid opening files form unknown sources or scan any external storage devices when you plug it into your computer.
|
7 videos|27 docs|69 tests
|

|
Explore Courses for Class 9 exam
|

|

















