Wi-fi Ethernet (802.11) | Computer Networks - Computer Science Engineering (CSE) PDF Download
WI-FI (802.11)
This section takes a closer look at a specific technology centered on the emerging IEEE 802.11 standard, also known as Wi-Fi. Wi-Fi is technically a trademark, owned by a trade group called the Wi-Fi alliance that certifies product compliance with 802.11. 802.11 is designed for use in a limited geographical area (homes, office buildings, campuses) and its primarily challenge is to mediate access to a shared communication medium in this case, signals propagating through space.
Physical Properties:
802.11 run over six different physical layer protocols. Five are based on spread spectrum radio, and one on diffused infrared (and is of historical interest only at this point). The fastest runs at a maximum of 54 Mbps.The original 802.11 standard defined two radio based physical layers standards, one using frequency hopping and the other using direct sequence. Both provide up to 2 Mbps. Then physical layer standard 802.11 b was added. Using a variant of direct exempt 2.4GHz frequency band of the electromagnetic spectrum. Then came 802.11a, which delivers up to 54 Mbps using a variant of FDM called orthogonal frequency division multiplexing (OFDM). 802.11 a runs in the license-exempt 5GHz band. The most recent standard is 802.11g, which is backward compatible with 802.11b.
Collision Avoidance:
A wireless protocol wait until the link becomes idle before transmitting and back off should a collision occur. Consider the situation where A and C are both within range of B but not each other. Suppose both A and C want to communicate with B and so they each send it a frame. A and C are unaware of each other since their signals do not carry that far. These two frames collide with each other at B, but unlike an Ethernet, neither A or C is aware of this collision. A and C are said to be hidden nodes with respect to each other.
A related problem called the exposed node problem where each of the four nodes is able to send and receive signals that reach just the nodes to its immediate left and right. For EX: a B can exchange frames with A and C but it cannot reach D , while C can reach B and D but not A. Suppose B is sending to A. Node C is aware of this communication because it hear B‟s transmission. It would be a mistake, however, for C to conclude that it cannot transmit to anyone just because it can hear B‟s transmission. For example, suppose C wants to transmit to node D. This is not a problem since C‟s transmission to D will not interfere with A‟s ability to receive from B.
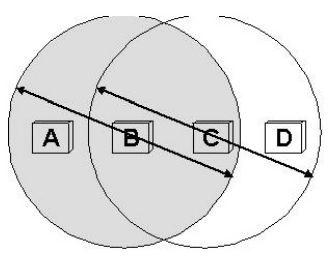
802.11 addresses these two problems with an algorithm called multiple access with collision avoidance (MACA). The idea is for the sender and receiver ot exchange control frames with each other before the sender actually transmits any data. This exchange informs all nearby nodes that a transmission is about to begin. Specifically, the sender transmits a Request to send (RTS) frame to the receiver; the RTS frame includes a field that indicates how long the sender wants to hold the medium. The receiver then replies with a clear to send (CTS) frame. This frame echoes this length field back to the sender. Any node that sees the RTS frame will collide with each other.
802.11 does not support collision detection, but instead the senders realize the in which case they each wait a random amount of time before trying again. The amount of time a given node delay is defined by the same exponential backoff algorithm used on the Ethernet.
Distribution System
Instead of all nodes created equal, some nodes are allowed to roam and some are connected to a wired network infrastructure. 802.11 calls these base stations access points (AP), and they are connected to each other by a so-called distribution system. A distribution system that connects three access points, each of which services the nodes in some region. Although two nodes can communicate directly with each other if they are within reach of each other, the idea behind this configuration is that each node associates itself with one access point. For node A to communicate with node E, for example, A first sends a frame to its access point (AP-1), which forwards the frame across the distribution system to AP-3 , which finally transmits the frame to E.
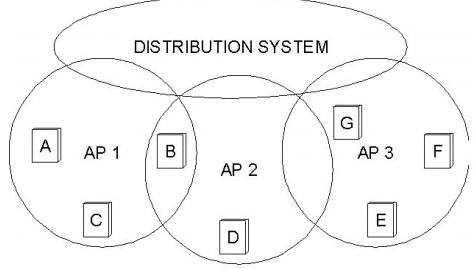
The technique for selecting an AP is called scanning and involves the following four steps:
1. The node sends a probe frame;
2. All APs within reach reply with a probe Response frames;
3. The node selects one of the access points, and sends that AP an Association Request frames;
4. The AP replies with an Association Response frame.
Because the signal from its current AP has weakened due to the node moving away from it. Whenever a node acquires a new AP, the new AP notifies the old AP of the change via the distribution system.Here in this fig., where node C moves from the cell serviced by AP-1 to the cell serviced by AP-2. At some point, C prefers AP-2 over AP-1,and so it associates itself with that access point.The mechanism just described is called active scanning since the node is actively searching for an access point. APs also periodically send a BEACON frame that the capabilities of the access point; these include the transmission rates supported by the AP.
This is called passive scanning, and a node can change to this AP based on the BEACON frame simply by sending an ASSOCIATION REQUEST frame back to the access point.
Frame Format:
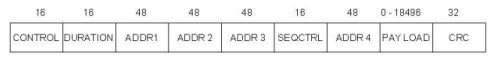
The frame contains the source and destination node address, each of which is 48 bits long, up to 2,312 bytes of data, and a 32-bit CRC. The Control field contains three subfields of interest : a 6-bit Type field that indicates whether the frame carries data, is an RTS or CTS frame, or is being used by the scanning algorithm; and a pair of 1-bit fields-called ToDS and .The 802.11 frame format is that it contains four, rather than two, address. how these address are interpreted depends on the settings of the ToDS and FromDS bits in the frame‟s Control field. This is to account for the possibility that the frame had to be forwarded across the distribution systems, which would mean that the original sender is not necessarily the same as the most recent transmitting node.
Similar reasoning applies to the destination address. In the simplest case, when one node is sending directly to another, the DS bits are 0, Addr1 identifies the target node, and Addr2 identifies the source node.In the most complex case, both DS bits are set to 1, indicating that the message went from a wireless node onto the distribution system and then from the distribution system to another wireless node. With both bits set, Addr1 identifies the ultimate destination, Addr2 identifies the immediate sender (the one that forwarded the frame from the distribution system to the ultimate destination), Addr3 identifies the intermediate destination (the one that accepted the frame from a wireless node and forwarded it across the distribution system), and Addr4 identifies the original source. In terms of the example given in fig., Addr1 corresponds to E, Addr2 identifies AP-3, Addr3 corresponds to AP-1, and Addr4 identifies A.
|
21 videos|113 docs|66 tests
|
FAQs on Wi-fi Ethernet (802.11) - Computer Networks - Computer Science Engineering (CSE)
| 1. What is Wi-Fi Ethernet (802.11)? |  |
| 2. How does Wi-Fi Ethernet (802.11) work? |  |
| 3. What is the difference between Wi-Fi and Ethernet? |  |
| 4. What are the advantages of Wi-Fi Ethernet (802.11)? |  |
| 5. How secure is Wi-Fi Ethernet (802.11)? |  |

|
Explore Courses for Computer Science Engineering (CSE) exam
|

|

















