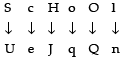Class 10 Computer Application: CBSE Sample Question Paper- Term I (2021-22) - 2 | CBSE Sample Papers For Class 10 PDF Download
| Table of contents |

|
| Class-X |

|
| Time: 90 |

|
| Minutes |

|
| M.M: 25 |

|
| Section - A |

|
| Section - B |

|
| Section - C |

|
Class-X
Time: 90
Minutes
M.M: 25
General Instructions :
Read the following instructions very carefully and strictly follow them:
- The Question Paper contains three sections A, B and C.
- Section A has 20 questions. Attempt any 16 questions.
- Section B has 20 questions. Attempt any 16 questions.
- Section C has 10 questions. Attempt any 8 questions.
- All questions carry equal marks.
- There is no negative marking.
Section - A
Q.1: Which of the following is a code of good behavior on the Internet?
(a) Etiquette
(b) Netiquette
(c) License
(d) Hacking
Correct Answer is Option (b)
Netiquette is a code of good behavior on the Internet. This includes several aspects of the Internet, such as E-mail, social media, online chat, web forums, website comments and other types of online communication.
Q.2: Priceline.com is an example of
(a) B2B
(b) B2C
(c) C2B
(d) C2C
Correct Answer is Option (c)
C2B (Consumer to Business) applies to any consumer that sells a product or service to a business over the Internet. One example of this E-business model is princeline.com where bidders set their prices for items such as airline tickets or hotel rooms and a sellers decide whether to supply them.
Q.3: Factor(s) that contribute to the digital divide is/are
(a) Relevant content
(b) Age
(c) Gender
(d) All of these
Correct Answer is Option (d)
Digital divide is a term that describes the uneven distribution of Information and communication Technology (ICTs) in society. Factors that contribute to the digital divide are relevant content age, lack of ICT skills and support, attitudinal factors, gender etc.
Q.4: Intellectual property is an:
(a) Industrial property
(b) Copyright property
(c) Free property
(d) Both (A) and (B)
Correct Answer is Option (d)
Intellectual property rights are the rights given to the persons over the creation of their mind.
Intellectual property rights reward creativity and human endeavor, which fuel the progress of humankind. The purpose of Intellectual property right is the giving of copyright to the creator of created idea, product, etc.
Q.5: Which of the following is a type of plagiarisim?
(a) Partial
(b) Collusion
(c) Self
(d) All of these
Correct Answer is Option (d)
The word plagiarism comes from the Latin word for kidnapping. You know that kidnapping is called as abducting a person. In the same way. Plagiarism is called as stealing a person’s idea and writing. In Plagiarism, you steal author’s ideas, experience, thought, language, etc.
Q.6: E-commerce means:
(a) Doing business online via the Internet
(b) Doing business off-line
(c) Studying commerce via electronic media
(d) None of these
Correct Answer is Option (a)
E-commerce means buying and selling of goods online.
Q.7: Fraud is:
(a) cheating others
(b) an intentionally false representation of a fact
(c) to deceive another party in order to obtain a profit
(d) All of these
Correct Answer is Option (b)
One who is online may open up the possibility for hackers to cummit fraud and launch spam and virus attacks.
Q.8: Intellectual property does not include:
(a) Creation of mind
(b) Artistic work
(c) Literary
(d) None of these
Correct Answer is Option (d)
Intellectual property right are the rights for the creations of human intellect including inventions; literary and artistic works, and symbols, names and images etc.
Q.9: ______ defines the smallest heading.
(a) <H6>
(b) <H2>
(c) <H3>
(d) <H4>
Correct Answer is Option (a)
<H1> is the largest heading and <H6> is the smallest heading.
Q.10: BACKGROUND is an attribute of:
(a) <BODY> tag
(b) <FONT> tag
(c) <IMG> tag
(d) <A> tag
Correct Answer is Option (a)
The <body> element contains the entire content of a web page. This tag is also commonly referred to as the <body> element. It must be the second element inside of the parent <html> element, following only the <head> element.
Q.11: What is the purpose of a web form?
(a) An outdated feature still used to help the page load faster
(b) An useful way to send information from the user directly to the search engines
(c) A way to input data into a website or an application
(d) To enable the user to navigate the website with ease
Correct Answer is Option (c)
Web Forms are pages that you users request using their browser.
Q.12: The alternate text of an image can be displayed by using the <IMG> tag.
(a) src
(b) ALT
(c) align
(d) None of these
Correct Answer is Option (b)
The Alt attribute contains the alternate text for an image. It appears on the web page due to some reason.
Syntax:
<IMG SRC = “URL” ALT = “Text”>
Q.13: ALT attribute allows
(a) addition of an alternate hyperlink
(b) addition of a border to image
(c) use of an alternate image in place of the specified image
(d) addition of alternate text about an image
Correct Answer is Option (d)
The text in the ALT attribute appears whenever the image is not shown by the browser for some reason.
Q.14: This tag identifies the documents as an HTML document.
(a) HEAD
(b) HTML
(c) TITLE
(d) BODY
Correct Answer is Option (b)
HTML stands for Hypertext Markup Language.
This tag identifies the documents as an HTML document. This is a container tag that has opening tag as well as closing tag.
Q.15: Which of the following tag accepts a full paragraph of text?
(a) <UL>
(b) <DT>
(c) <DD>
(d) <DL>
Correct Answer is Option (c)
<DD> tag accepts a full paragraph of text. This tag is used under <DL> tag.
Q.16: This tag defines the HTML header and does not affects the appearance of the document.
(a) HTML
(b) BODY
(c) TITLE
(d) HEAD
Correct Answer is Option (d)
HEAD tag defines the HTML header and does not affects the appearance of the document. <HEAD> tag is always used within <BODY> tags.
Q.17: HTML web pages can be read and rendered by _______.
(a) web server
(b) web browser
(c) domain name
(d) notepad
Correct Answer is Option (b)
HTML web pages can be read and rendered by web browser. Some popular web browser are Mozilla Firefox, Internet Explorer, Google chrome etc.
Q.18: Identify the HTML code to display a horizontal line of red colour
(a) <hr color = “red”>
(b) <hrcoour = red>
(c) <br = “red”>
(d) <br colour = “red”>
Correct Answer is Option (a)
<hr> tag is used to display a horizontal line in HTML document. <hr color = “red”> code is used to display a horizontal line of red colour.
Q.19: Sarita is designing a webpage and wants to change the name of the font (font-type) for certain text. Which attribute of the FONT tag she should use?
(a) type
(b) face
(c) size
(d) font
Correct Answer is Option (b)
Face is an attribute of <FONT> tag face attribute is used to change the name of the font or fact type for certain text. So, sarita should use the face attribute.
Q.20: Which heading element gives the most prominent headings?
(a) <H3>
(b) <H4>
(c) <H2>
(d) <H1>
Correct Answer is Option (d)
In HTML, heading tags are used to display the text as a heading. There are six levels of headings ranging from <H1> to <H6>, in which <H1> gives the most prominent headings.
Section - B
Q.21: Find the error(s) in the following code?
<p>
<font color : “blue”>
</font>
</p>
(a) <font color = “blue”>
(b) <font bgcolor = “blue”>
(c) <font color : “blue”>
(d) <font> <color = “blue”>
Correct Answer is Option (a)
<font color = “blue”> is the correct code. After color attribute the equal = sign is used to give color name.
Q.22: The gap between those individuals in our society who are computer literate and have access to information resources like the internet and those who do not is referred to as the
(a) privacy divide
(b) computer literacy
(c) digital divide
(d) computer crime
Correct Answer is Option (c)
There are many reasons which are responsible for the existence of the divide:
First the non-availability of a reliable ICT infrastructure to access the internet.
Secondly, these are problems in accessing the internet regularly.
Q.23: Consider the following HTML code:
<ul type = “circle”>
<li>Red</li>
<li>Green</li>
<li>Blue</li>
</ul>
Choose the correct output that would be shown upon execution of the above code, from the choices given below:
(a) 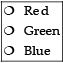
(b)
(c)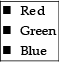
(d) 
Correct Answer is Option (a)
In ul (unordered list) type attributes set the bullet style for the list. The value could be circle
disc
square
Q.24: Plagiarism in research is:
(a) Creative use of previous data
(b) Copying unscrupulously and making use of it.
(c) Quoting someone and citing him/her
(d) Referring to previous data and working over it with new objective
Correct Answer is Option (b)
It is unscrupulously copying from someone else’s work and making use of it without their knowledge.
Q.25: The web standard allow programmers on many different computer platforms to dispersed format and display the information server. These programs are called …….
(a) web browser
(b) HTML
(c) Internet explorer
(d) None of the above
Correct Answer is Option (a)
A web browser (commonly referred to as a browser) is a application software for accessing the world wide web.
Q.26: Meena has written the following code snippet as part of on HTML program.
<u>Hello World</u>
Predict the output of the above from the following:
(a) Hello World
(b) HELLO WORLD
(c) Hello World
(d) Hello-World
Correct Answer is Option (c)
The <u> tag is used to underline the text enclosed within the </u> tag.
Q.27: From which tag descriptive list starts in HTML?
(a) <DS>
(b) <u>
(c) <DD>
(d) <DL>
Correct Answer is Option (d)
The <dl> tag in HTML is used to represent the description list.
syntax – <dl> content – </dl>
Q.28: The users must agree to the ________ terms and agreements when they use an open source software.
(a) System
(b) License
(c) Community
(d) Programmer
Correct Answer is Option (b)
Open-source software (OSS) is computer software that is released under a license in which the copyright holder grants users the rights to use.
Q.29: One of the most popular method of encrypting data is creaser cipher where original data is replaced by a key character like if key is –2 than ‘a’ will be replaced by ‘y’, ‘b’ is replaced by ‘z’ and so on.
If the key is 2 i.e., every letter is replaced by its next to next letter means the letter ‘A’ will be replaced by ‘C’ the letter ‘B’ is replaced by ‘D’ and so on then what will be the replacement of the word–ScHoOl
(a) UbJnRJ
(b) WakmQj
(c) UeJqQn
(d) TcJnRk
Correct Answer is Option (c)
If the key is 2 i.e, every letter is replaced by its next to next letter
So, the replacement of the word ‘ScHoOl’ is ‘UeJqQn’.
Q.30: Which of the following is not used with password attributes?
(a) name
(b) size
(c) maxlength
(d) min
Correct Answer is Option (d)
The password value of the input attribute displays a field where the user can type a password into a form.
Q.31: The dimension of ecommerce that enable commerce across national boundaries is called _______.
(a) integrity
(b) global reach
(c) richness
(d) ubiquity
Correct Answer is Option (b)
The dimension of e-commerce that enables commerce across national boundaries is called global reach. Global reach refers to a business initiative to increase the access between a company and their current and potential customers through the use of the internet.
Q.32: Observe the HTML code given below and identify the line that will be ignored and not displayed by the browser:
<html>
<head><title>web page
<title></head>
<body>welcome to page
<!...check…>
</body>
</html>
(a) <title> web page
(b) <body> welcome to page
(c) <!...check…>
(d) none of the above
Correct Answer is Option (c)
</…check…> not displayed by the brows because this element is used to add a comment to an HTML document. Commenting in HTML allows developers to leave notes about their code.
Q.33: Which of the following is the correct code of HTML page?
(a)
<HTML>
<TITLE>Hello
</TITLE>
</HTML>
(b)
<HTML>
<HEAD>
<TITLE>Hello
</TITLE>
</HEAD>
</HTML>
(c)
<HTML>
<BODY>Hello
</HTML>
(d)
<HTML><HEAD>Hello
<BODY>
</HTML>
Correct Answer is Option (b)
Because <TITLE> tag must close inside the <HEAD> tag.
Q.34: Which attribute is not supported by a <BODY> tag?
(a) bgcolor
(b) size
(c) text
(d) link
Correct Answer is Option (b)
Size is not an attribute of <BODY> tag. This attribute can be used by <input> tag. Such as, <input type = “text size = “35”>
Q.35: What do you do if you or someone you know is being cyber bullied?
(a) Get into a fight with that person
(b) Keep it to yourself
(c) Delete the text messages
(d) Let someone know
Correct Answer is Option (d)
To stop cyberbullying tell children not to respond to any cyberbullying threats or comment online. Talk regularly and specifically with children about online issue, so the Option (D) is correct.
Q.36: Consider the following form control in HTML form: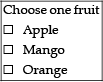
Now choose the correct code for the above:
(a)
<input type = “checkbox”>Apple<br>
<input type = “checkbox”>Mango<br>
<input type = “checkbox”>Orange<br>
(b)
<input type = “check”>Apple<br>
<input type = “check”>Mango<br>
<input type = “check”>Orange<br>
(c)
<input type = “check_box1”>Apple<br>
<input type = “check_box2”>Mango<br>
<input type = “check_box3”>Orange<br>
(d) <input type = “checkbox”; Apple; Mango; Orange>
Correct Answer is Option (a)
Three checkbox which has value here is Apple, Mango and Orange.
So, the correct code is
<input type = “checkbox”>Apple<br>
<input type = “checkbox”>Mango<br>
<input type = “checkbox”>Orange <br>
Q.37: Riya is working on HTML5, she wants to use the visited link in a document. Which option is correct for visited link help her to out of the following.
(a) <body visited_link = “color_name”>
(b) <body vlink = “color_name”>
(c) <body v_link : “color_name”>
(d) <body v_link == “color_name”>
Correct Answer is Option (b)
The HTML <body> vlink attribute is used to specify a color of a visited link in a document.
So, the correct answer is,
<body vlink = “color-name”>
Q.38: Which option is correct about the <font>, choose the correct statement.
(a) <font>tag size attribute is used to adjust the size.
(b) <font>tag range of size of the font in html is from 1 to 7.
(c) <font>tag, size attribute by default is 3.
(d) All of the above.
Correct Answer is Option (d)
Font, size attribute is used to adjust the size of the text in the HTML document using font tag with size attribute. The range of size of the font in HTML is 1 to 7 and the default size is 3. So, the correct answer is all of the above.
Q.39: Any person ‘XYZ’ has received an encrypted message and wants to convert this message into the actual message (message before encryption). The technique he should use is called.
(a) Conversion
(b) Encryption
(c) Decryption
(d) None of the above
Correct Answer is Option (c)
Decryption is the process of converting an encrypted message back to its original (readable) format.
Q.40: Consider the following code:
<img src = “Image.jpg” width = “_____” height = “______”>
Fill in the blanks to set the image size to be 100 pixels wide and 200 pixels tall.
(a) 100, 200
(b) 200, 100
(c) <100>, <200>
(d) <100, 200><200, 100>
Correct Answer is Option (a)
<img src = “Image.jpg” width = “100” height = “200”> because 100 pixels is given for width and 200 pixels is given for height of an image.
Section - C
Read the following text and answer the following questions on the basis of the same:
E-Commerce or Electronic Commerce means buying and selling of goods, products or services over the internet. E-Commerce is also known as electronic commerce or internet commerce. These services provided online over the internet network. Transaction of money, funds and data are also considered as E-commerce. These business transactions can be done in four ways: Business to Business (B2B), Business to Customer (B2C), Customer to Customer(C2C), Customer to Business (C2B). The standard definition of E-commerce is a commercial transaction which is happened over the internet. Online stores like Amazon, Flipkart, Shopify, Myntra, Ebay, Quikr, Olx are examples of E-commerce websites.
Based on the given information, answer the Questions No. 41-45.
Q.41: Which of the following E-commerce applies to businesses buying from and selling to each other over the Internet ?
(a) B2B
(b) B2C
(c) C2B
(d) C2C
Correct Answer is Option (a)
B2B (Business to Business) applies to business buying from and selling to each other over the internet. It describes truncations between business, such as a business between a manufacture and a wholesaler or between a wholesaler and a retailer.
Q.42: _______ is the most successful C2C online auction website.
(a) Priceline.com
(b) e-Bay
(c) e-mail
(d) e-Ships
Correct Answer is Option (b)
E-Bay is the most successful C2C online auction website. C2C(Consumer to Consumer) involves the electronically facilitated transactions between consumers through third party.
Q.43: Which of the following is considered as a powerful tool to collect consumer ’s private information?
(a) Hacking
(b) Plagiarism
(c) e-Commerce
(d) Digital divide
Correct Answer is Option (c)
E-commerce is considered as a powerful tool to collect consumer’s private information. The same tool and their use in business also interfere on the privacy of individuals.
Q.44: B2C model is a variant of
(a) C2B model
(b) C2C model
(c) B2B model
(d) B2C model
Correct Answer is Option (c)
B2C model is a variant of B2B model. Such websites are used by governments to trade and exchange information with various business organization. Such websites are accredited by the government and provide a medium to business to submit application forms to the government.
Q.45: Which of the following methods of fraud that is/are used to target E-commerce?
(a) Refund fraud
(b) Merchant fraud
(c) Fraud via Identity theft
(d) All of these
Correct Answer is Option (d)
E-commerce fraud shows no sign of slowing down. Online businesses are quickly becoming easy targets for cybercriminals as fraud in E-commerce continues to rise. Here are some methods of fraud that are used do target E-commerce are refund fraud, merchant fraud, fraud via Identity fraud and friendly fraud.
Read the following text and answer the following questions on the basis of the same:
Consider the following code created by Roman for a web page:
<HTML>
<HEAD><TITLE>Dance of India</TITLE></HEAD>
<BODY bgcolor = “yellow” link = “given” alink = “blue” vlink = “red”>
<P><FONT color = “maroon”><H1>Dance of India</H1></FONT>______<BR> #line 1
<P><_____ src = “dmage004.jpg “height = “150” width = “100” align = “right”>
#line 2
There are many types of dance of India, from those which are deeply religious in content to those which are danced on more trivial happy occasions. Classical dance of India are usually always spiritual in content, although this is often true also of folk dance. _______ #line 3
Based on the given information, answer the questions NO. 46-50.
Q.46: Choose the correct option from the following to fill up in line 1:
(a) <P>
(b) </P>
(c) </H>
(d) </H1>
Correct Answer is Option (b)
</P> is used to fill up in line 1. It is the closing tag of <P>. <P> is a container tag so its closing tag must be required.
Q.47: Choose the correct option from the following to fill up in line 2:
(a) IMAGE
(b) IM
(c) IMG
(d) IMGE
Correct Answer is Option (c)
IMG is used to fill up in line 2 IMG is a tag that is used to set the image in the HTML document.
Q.48: Choose the correct option from the following to fill up in line 3:
(a) </P>
(b) </HR>
(c) <P>
(d) <//P>
Correct Answer is Option (a)
</P>is used to fill up in line 3. It is the closing tag of <p>. It is used to set the paragraph in the HTML document.
Q.49: Choose the correction option from the following to fill up in line 4:
(a) HEAD
(b) BOR
(c) BODY
(d) TITLE
Correct Answer is Option (c)
</BODY> is used to fill up in line 4. This tag is used to close the <BODY> tag.
Q.50: Choose the correct option from the following to fill up in line 5:
(a) <HTML>
(b) </HTML>
(c) </HEAD>
(d) </TITLE>
Correct Answer is Option (b)
</HTML>is used to fill up in line 5. This tag is used to close the <HTML> tag.
|
363 docs|7 tests
|