Peer-to-Peer File Sharing | Computer Networks - Computer Science Engineering (CSE) PDF Download
| Table of contents |

|
| Introduction |

|
| How Does P2P (Peer-to-Peer) Work? |

|
| P2P Architecture |

|
| P2P File Sharing Security Concerns |

|
Introduction
In computer networking, P2P (Peer-to-Peer) is a file-sharing technology that allows users to access multimedia files like videos, music, e-books, games, and more. Users in this network are called peers, who request files from each other by establishing TCP or UDP connections.
How Does P2P (Peer-to-Peer) Work?
A P2P network enables communication between computer hardware and software without the need for a server. Unlike client-server architecture, a P2P network lacks a central server for processing requests. Instead, peers directly interact without a central server.
When a peer requests a file, multiple peers may have copies of that file. The underlying architecture of the P2P system determines how to obtain the IP addresses of these peers. Using specific methods, the requesting peer identifies peers that have the requested file, and the file transfer occurs directly between them.
P2P Architecture
Centralized Directory
A centralized directory is similar to client-server architecture, where a central server provides directory services. Peers inform this server of their IP addresses and the files they share. The server periodically queries peers to check their connectivity and maintain a database of file locations. Napster, which distributed MP3 files, used this method.
Working:
- A requesting peer sends a query to the server.
- The server, having all peer information, returns the IP addresses of peers with the requested file.
- The file transfer occurs directly between the peers.
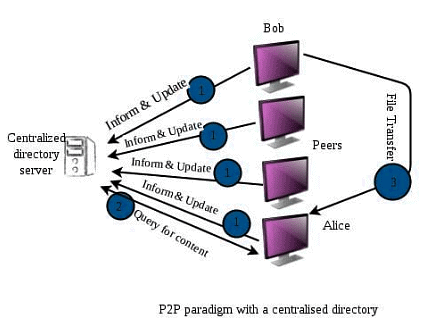 Centralized Directory
Centralized Directory
Disadvantages:
- Single point of failure: If the server crashes, the entire P2P network fails.
- High processing load on a single server, requiring a vast and regularly updated database.
Query Flooding
Unlike the centralized approach, this method utilizes distributed systems. Peers connect to an overlay network, meaning any existing connection/path between peers forms part of this network. In this context, peers are referred to as nodes, and the connections between them are called edges, creating a graph-like structure. Gnutella was the first decentralized peer-to-peer network to implement this method.
Working:
- When a peer requests a file, the request is sent to all its neighboring nodes (i.e., all nodes directly connected to it).
- If those nodes don't have the requested file, they forward the query to their neighbors, continuing this process (called query flooding).
- When a peer with the requested file is found (a query hit), the query flooding stops, and the peer sends back the file name and file size to the client, following the reverse path.
- If multiple query hits occur, the client selects one of the responding peers.
Gnutella:
- Gnutella represents a new wave of P2P applications that provide distributed discovery and resource sharing across the Internet.
- It is distinguished by its support for anonymity and its decentralized architecture.
- A Gnutella network consists of a dynamically changing set of peers connected via TCP/IP.
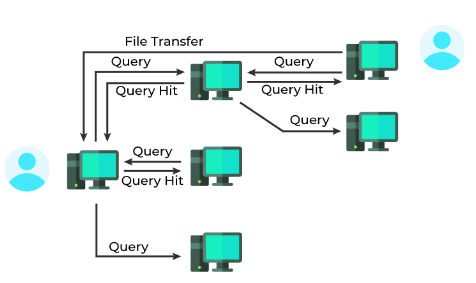 Query Flooding
Query Flooding
Exploiting Heterogeneity
This architecture combines centralized and distributed systems. It features supernodes (high-priority peers with higher bandwidth and connectivity) and regular peers assigned to these supernodes. Supernodes interconnect, and peers inform their respective leaders about their connectivity, IP address, and shared files. KaZaA used this hybrid approach.
Working:
- Supernodes can either merge databases with other supernodes or forward queries to neighboring supernodes until a match is found, limiting query flooding scope.
- This system exploits peer heterogeneity by designating group leaders/supernodes and their child peers.
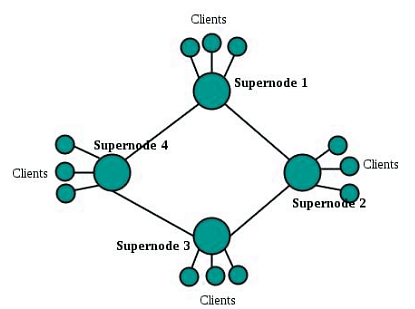 Exploiting heterogeneity
Exploiting heterogeneity
P2P File Sharing Security Concerns
To secure sensitive information on the network, consider the following steps:
- Delete unnecessary sensitive information and apply restrictions to important files.
- Minimize or remove P2P file-sharing programs on computers accessing sensitive information.
- Monitor the network for unauthorized file-sharing programs.
- Block unauthorized P2P file-sharing programs within the network perimeter.
- Implement strong access controls and authentication mechanisms to prevent unauthorized access.
- Use encryption techniques like Secure Socket Layer (SSL) or Transport Layer Security (TLS) to protect data in transit.
- Employ firewalls, intrusion detection and prevention systems, and other security measures to prevent unauthorized access and detect/block malicious activity.
- Regularly update software and apply security patches to address vulnerabilities.
- Educate users about P2P file-sharing risks and provide training on safe and responsible usage.
- Use data loss prevention tools to monitor and prevent the transmission of sensitive data outside the network.
- Implement network segmentation to limit the scope of a security breach and prevent unauthorized access to sensitive areas.
- Regularly review and audit the network to identify potential security threats and ensure security controls are effective and up-to-date
|
21 videos|145 docs|66 tests
|
FAQs on Peer-to-Peer File Sharing - Computer Networks - Computer Science Engineering (CSE)
| 1. What is P2P file sharing? |  |
| 2. How does P2P technology work? |  |
| 3. What are the security concerns associated with P2P file sharing? |  |
| 4. Are there any legal implications of using P2P file sharing? |  |
| 5. What are some popular P2P file sharing platforms? |  |




















