Wifi: Basics, WPS, WPA | Computer Networks - Computer Science Engineering (CSE) PDF Download
| Table of contents |

|
| Basics of Wi-Fi |

|
| Wifi Protected Setup (WPS) |

|
| What can WPS do? |

|
| Wifi Protected Access (WPA) |

|
Basics of Wi-Fi
- We've been studying wired networks, with Ethernet being the most common example. Unlike wireless networks, which use radio waves, wired networks transmit electrical signals through cables. Wi-Fi, short for Wireless Fidelity, is a technology for wireless local area networking (WLAN) based on IEEE 802.11 standards. Devices compatible with Wi-Fi can connect to the internet via a WLAN network and a wireless access point (AP).
- Every WLAN has an access point responsible for receiving and transmitting data to and from users. The IEEE has defined specifications for wireless LANs under the IEEE 802.11 standard, covering the physical and data link layers. An access point (AP) acts as a wireless LAN base station, capable of connecting multiple wireless devices to the internet simultaneously.
The architecture of the IEEE 802.11 standard includes two types of services: Basic Service Set (BSS) and Extended Service Set (ESS).
- Basic Service Set (BSS): This is the fundamental building block of a WLAN. It consists of wireless mobile stations and an optional central base station called an access point (AP). Stations can form a network without an AP and agree to be part of a BSS. A BSS without an AP cannot send data to other BSSs, creating a standalone network known as an ad-hoc network or Independent BSS (IBSS). A BSS with an AP is called an infrastructure network.
The figure below illustrates an IBSS and a BSS, with the green-colored box representing an AP.
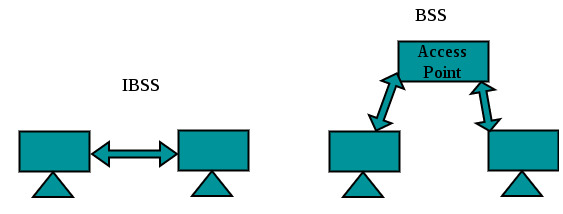
ESS is made up of 2 or more BSSs with APs. BSSs are connected to the distribution system via their APs. The distribution system can be any IEEE LAN such as Ethernet.
ESS has 2 kinds of stations:
1. Mobile – stations inside the BSS
2. Stationary – AP stations that are part of wired LAN.
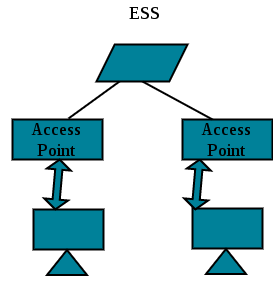
The topmost green box represents the distribution system and the other 2 green boxes represent the APs of 2 BSSs.
Features of Wi-Fi include
- Wireless Connectivity: Wi-Fi enables devices to connect to a network without using physical cables, offering increased mobility and flexibility.
- High Speed: Wi-Fi networks provide high-speed internet access, allowing for quick downloading and uploading of data.
- Easy Setup: Wi-Fi networks are simple to set up and configure, requiring minimal technical expertise. Most modern devices come with built-in Wi-Fi connectivity.
- Multiple Device Connectivity: Wi-Fi networks can support multiple devices simultaneously, allowing several users to connect to the same network and access the internet at the same time.
- Security: Wi-Fi networks can be secured with encryption and other security measures to protect against unauthorized access and hacking.
- Range: Wi-Fi networks can cover a wide range of distances, depending on the type of router and the environment in which they are used.
- Compatibility: Wi-Fi is a widely adopted technology and is compatible with a variety of devices, including smartphones, laptops, tablets, and smart home devices.
- Interference: Wi-Fi signals can be affected by interference from other wireless devices and physical obstacles, such as walls and buildings, which can impact network performance.
- Reliability: Wi-Fi networks can sometimes experience dropouts or signal loss, particularly in areas with high network congestion or interference.
Wifi Protected Setup (WPS)
- Wi-Fi Protected Setup (WPS) is a wireless network security standard designed to simplify and expedite the connection process between a router and wireless devices. WPS is compatible only with wireless networks that use passwords protected by Wi-Fi Protected Access Personal (WPA) or Wi-Fi Protected Access 2 (WPA2) Personal security protocols. It is not compatible with networks using the outdated Wired Equivalent Privacy (WEP) security, which can be easily breached by hackers with basic skills.
- Wi-Fi Protected Setup™ is an optional certification program that facilitates the setup of security-enabled Wi-Fi® networks in homes and small offices. This technology allows users to configure their networks and activate security features using simple methods, such as pressing a button or entering a PIN, making it accessible to most users.
- Typically, connecting a wireless device to a network requires knowing the network name (SSID) and its password (WPA-PSK key). To connect a device, such as a smartphone or laptop, to your wireless network, you must select the desired network on the device and enter its security password.
 WPS
WPS
What can WPS do?
WPS can sometimes simplify the connection process. Here’s how WPS connections can be performed:
- First, press the WPS button on your router to enable the discovery of new devices. Then, select the network you want to connect to on your device. The device will automatically connect to the wireless network without needing to enter the network password. Devices like wireless printers or range extenders have their own WPS button, allowing for quick connections. To connect these devices, simply press the WPS button on both the router and the device. There is no need to input any data during this process, as WPS automatically sends the network password, which the devices will remember for future use. They will be able to connect to the same network in the future without using the WPS button again.
- A third method involves using an eight-digit PIN. All routers with WPS enabled have a PIN code that is generated automatically and cannot be configured by users. This PIN can be found on the WPS configuration page on your router. Some devices without a WPS button but with WPS support will ask for this PIN. Once entered, the device will authenticate and connect to the wireless network. Another method also involves an eight-digit PIN. Some devices without a WPS button but with WPS support generate a client PIN. This PIN can be entered into your router’s wireless configuration panel, allowing the router to add the device to the network. The first two methods are fast, but the last two methods do not provide any time-saving benefits. Typing the eight-digit PIN or the wireless network password is slow. The fourth method is even slower because it requires accessing the router’s wireless configuration section and typing the PIN provided by the client device.
WPS Operation Methods
- Push Button: Requires pressing buttons on the router and client devices. Some routers and devices have virtual buttons that require activation through software. Once activated, the device connects automatically without a password.
- PIN: Involves entering the PIN found on the access point’s sticker or provided by the router. Devices that do not support WPS but support the protocol use this instant PIN feature.
- Near Field Communication (NFC): Involves bringing the client device close to the access point to connect and authenticate using NFC. This out-of-band method transfers data directly without using WPS.
- USB: Data is transferred between the new device and the access point using a USB flash drive. Although deprecated, optional support is still available.
Advantages of WPS
- Automatically configures the network name (SSID) and WPA security key for WPS-enabled access points.
- No need to know the SSID security key or passphrase when connecting WPS-enabled devices.
- WPS keys are randomly generated, making them difficult to guess or figure out.
- Eliminates the need to enter long sequences of hexadecimal codes or passphrases.
- Uses Extensible Authentication Protocol (EAP) to securely exchange information and network credentials, reducing the possibility of a network breach.
Disadvantages of WPS
- Does not support "Ad Hoc" connections where devices communicate directly without an access point.
- Cannot be used if Wi-Fi devices on the network are not WPS certified or compatible.
- Adding non-WPS client devices to the network is difficult due to the long hexadecimal characters generated by WPS.
- Increased security offered by WPS is not available to non-WPS certified devices.
- Users must manually enter the lengthy hexadecimal passphrase on non-WPS devices.
- WPS is a relatively new technology, so not all devices support it.
Wifi Protected Access (WPA)
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are security protocols developed by the Wi-Fi Alliance to secure wireless networks. These protocols were established to address the significant vulnerabilities found in the earlier Wired Equivalent Privacy (WEP) system. This article explores WEP, WPA, different versions of WPA, how WPA works, and how to identify your Wi-Fi security type.
What is WEP?
Wired Equivalent Privacy (WEP) is an early security protocol for wireless networks introduced in 1997. Designed to provide security comparable to wired networks by encrypting data sent over Wi-Fi, WEP uses a static key shared between devices and the wireless router. However, WEP has major weaknesses, including vulnerabilities to various hacking methods, making it easy for attackers to break the encryption and access the network. Due to these issues, WEP has been largely replaced by more secure protocols like WPA and WPA2.
What is Wi-Fi Protected Access (WPA)?
WPA, also known as the draft IEEE 802.11i standard, became available in 2003. The Wi-Fi Alliance developed WPA as an intermediate measure before the more secure and complex WPA2, which became available in 2004 and is a common abbreviation for the full IEEE 802.11i standard. In January 2018, the Wi-Fi Alliance announced the release of WPA3, which included several security improvements over WPA2.
Versions of WPA
Different versions of WPA offer various features. The main versions are WPA, WPA2, and WPA3:
WPA
- Introduced as an interim solution to replace WEP, WPA could be implemented through firmware upgrades on wireless network interface cards designed for WEP. However, significant changes were required in wireless access points (APs), making most pre-2003 APs incompatible with WPA.
- WPA implements almost all of the IEEE 802.11i standard. Unlike WEP's static 64-bit or 128-bit encryption keys, WPA uses the Temporal Key Integrity Protocol (TKIP), which dynamically generates a new 128-bit key for each packet, preventing the types of attacks that compromised WEP.
- WPA includes a Message Integrity Check to prevent attackers from altering or resending data packets, replacing the less secure cyclic redundancy check (CRC) used by WEP.
WPA2
- WPA2 replaced WPA in 2004 and required testing and certification by the Wi-Fi Alliance. It implemented the mandatory elements of IEEE 802.11i, including support for the Advanced Encryption Standard (AES) based CCMP (Counter Mode CBC-MAC Protocol) encryption mode. WPA2 certification has been mandatory for all new devices since March 13, 2006.
- WPA2 offers robust security through the Block Chaining Message Authentication Code Protocol (CCMP), which is based on the AES algorithm, providing stronger security compared to WPA's TKIP. However, WPA2 also has vulnerabilities, particularly related to Wi-Fi Protected Setup (WPS) access points, making it advisable to disable WPS.
WPA3
- In 2018, WPA3 replaced WPA2 as the latest and most improved version of WPA. The Wi-Fi Alliance began certifying WPA3-approved products in 2018. Users must purchase new routers supporting WPA3 or have existing equipment upgraded by the manufacturer to use WPA3 features.
- WPA3 offers enhanced security features, including a 192-bit cryptographic strength in WPA3-EAP enterprise mode, 384-bit Hashed Message Authentication Mode (HMAC), 256-bit Broadcast/Multicast Integrity Protocol (BIP-GMAC-256), 256-bit Galois/Counter Mode Protocol encryption (GCMP-256), SAE exchange, and Wi-Fi Device Provisioning Protocol (DPP).
Working with WPA
When setting up a network or connecting to a wireless network, you may encounter options for using WPA. Some older devices, originally using WEP, may only support WPA after a firmware update. However, some devices may not be compatible with WPA. While WPA is more secure than WEP, it is still susceptible to attacks on pre-shared keys. Using a strong passphrase can help protect against brute-force attacks.
Security Issues with WPA
- Pre-shared Key Vulnerability: Weak passwords or passphrases can make WPA and WPA2 susceptible to password cracking attempts.
- Lack of Forward Secrecy: WPA and WPA2 do not offer forward secrecy, allowing adversaries to potentially decrypt past and future packets once the pre-shared key is known.
- Denial of Service Attacks: Attackers can flood the network with messages, disrupting the availability of network resources.
- Eavesdropping: Unauthorized third parties can intercept data transmitted over the network.
- Spoofing and Session Hijacking: Attackers can gain access to network resources and data by impersonating legitimate users.
How to Identify Your Wi-Fi Security Type
To identify your Wi-Fi security type:
On Windows:
- Click the Wi-Fi icon in the taskbar and select your network.
- Right-click on your Wi-Fi network and select Properties.
- Look for the Security type under the "Network security settings" section.
On macOS:
- Click the Wi-Fi icon in the menu bar and select Open Network Preferences.
- Click Advanced, then select your network.
- Look for the Security field in the details.
On Mobile Devices:
- iOS: Open Settings > Wi-Fi > Tap on your network (i) > Check the Security field.
- Android: Open Settings > Wi-Fi > Tap on your network > Check the Security field.
Router Settings:
- Log in to your router’s admin page (typically by entering the router’s IP address in your browser).
- Navigate to the Wireless or Security settings section.
- Check the Security Mode or Encryption settings to see your Wi-Fi security type.
- Common security types include WPA2, WPA3, WEP, and WPA.
Difference Between WEP and WPA
A security standard for computers with wireless internet connections is called Wi-Fi Protected Access (WPA). The Wi-Fi Alliance developed it to improve upon the original Wi-Fi security standard, Wired Equivalent Privacy (WEP), in terms of data encryption and user authentication.
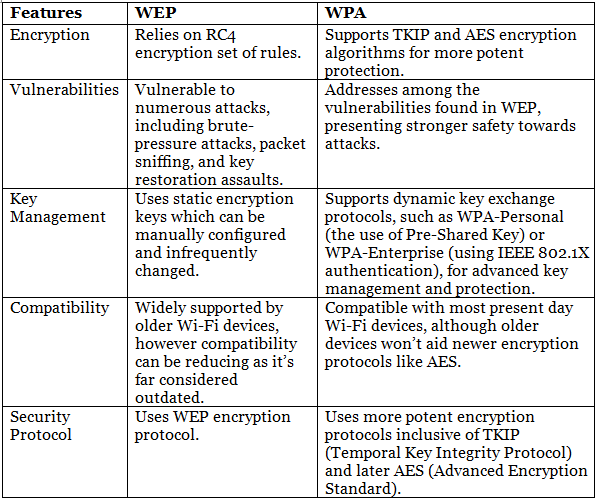
Conclusion
Wi-Fi Protected Access (WPA) improved the security of wireless networks by fixing the weaknesses in older methods like WEP. It introduced better encryption and key management. While WPA2 and WPA3 are now more commonly used because they are even more secure, WPA was an important step in making Wi-Fi safer. Knowing about WPA helps us understand why it’s important to use up-to-date security for protecting Wi-Fi connections.
|
21 videos|143 docs|66 tests
|
FAQs on Wifi: Basics, WPS, WPA - Computer Networks - Computer Science Engineering (CSE)
| 1. What is the basic function of Wi-Fi? |  |
| 2. How does Wifi Protected Setup (WPS) work? |  |
| 3. What are the benefits of using Wifi Protected Access (WPA) for securing a Wi-Fi network? |  |
| 4. Can WPS be disabled on a Wi-Fi router for added security? |  |
| 5. How can users troubleshoot common Wi-Fi connectivity issues at home? |  |




















