Computer Science Engineering (CSE) Exam > Computer Science Engineering (CSE) Notes > Computer Networks > Overview of Transport Layer
Overview of Transport Layer | Computer Networks - Computer Science Engineering (CSE) PDF Download
Introduction
- TCP was specifically designed to provide a reliable end to end byte stream over unreliable internetwork. Each machine supporting TCP has a TCP transport entity either a user process or part of the kernel that manages TCP streams and interface to IP layer.
- A TCP entity accepts user data streams from local processes, breaks them up into pieces not exceeding 64KB and sends each piece as a separate IP datagram. Client Server mechanism is not necessary for TCP to behave properly.
- The IP layer gives no guarantee that datagram will be delivered properly, so it is up to TCP to timeout and retransmit, if needed. Duplicate, lost and out of sequence packets are handled using the sequence number, acknowledgements, retransmission, timers, etc to provide a reliable service. Connection is a must for this service.Bit errors are taken care of by the CRC checksum.
- One difference from usual sequence numbering is that each byte is given a number instead of each packet. This is done so that at the time of transmission in case of loss, data of many small packets can be combined together to get a larger packet, and hence smaller overhead.
- TCP connection is a duplex connection. That means there is no difference between two sides once the connection is established.
Salient Features of TCP
- Piggybacking of Acknowledgments: The ACK for the last received packet need not be sent as a new packet, but gets a free ride on the next outgoing data frame(using the ACK field in the frame header). The technique is temporarily delaying outgoing ACKs so that they can be hooked on the next outgoing data frame is known as piggybacking. But ACK can't be delayed for a long time if receiver(of the packet to be acknowledged) does not have any data to send.
- Flow and congestion control: TCP takes care of flow control by ensuring that both ends have enough resources and both can handle the speed of data transfer of each other so that none of them gets overloaded with data. The term congestion control is used in almost the same context except that resources and speed of each router is also taken care of. The main concern is network resources in the latter case.
- Multiplexing / Demultiplexing: Many applications can be sending/receiving data at the same time. Data from all of them has to be multiplexed together. On receiving some data from lower layer, TCP has to decide which application is the recipient. This is called demultiplexing. TCP uses the concept of port number to do this.
TCP Segment Header
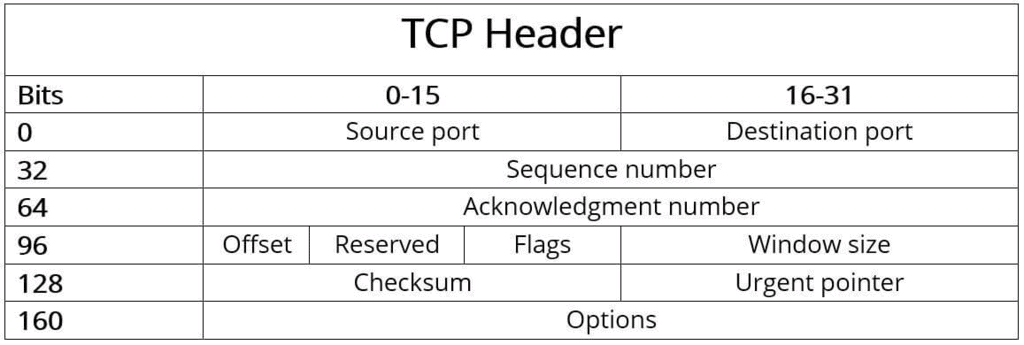
Explanation of header fields
- Source and destination port
These fields identify the local endpoint of the connection. Each host may decide for itself how to allocate its own ports starting at 1024. The source and destination socket numbers together identify the connection. - Sequence and ACK number
This field is used to give a sequence number to each and every byte transferred. This has an advantage over giving the sequence numbers to every packet because data of many small packets can be combined into one at the time of retransmission, if needed. The ACK signifies the next byte expected from the source and not the last byte received. The ACKs are cumulative instead of selective. Sequence number space is as large as 32-bit although 17 bits would have been enough if the packets were delivered in order. If packets reach in order, then according to the following formula:(sender's window size) + (receiver's window size) < (sequence number space) the sequence number space should be 17-bits. But packets may take different routes and reach out of order. So, we need a larger sequence number space. And for optimisation, this is 32-bits. - Header length :This field tells how many 32-bit words are contained in the TCP header.This is needed because the options field is of variable length.
- Flags : There are six one-bit flags.
- URG : This bit indicates whether the urgent pointer field in this packet is being used.
- ACK :This bit is set to indicate the ACK number field in this packet is valid.
- PSH : This bit indicates PUSHed data. The receiver is requested to deliver the data to the application upon arrival and not buffer it until a full buffer has been received.
- RST : This flag is used to reset a connection that has become confused due to a host crash or some other reason. It is also used to reject an invalid segment or refuse an attempt to open a connection. This causes an abrupt end to the connection, if it existed.
- SYN : This bit is used to establish connections. The connection request(1st packet in 3-way handshake) has SYN=1 and ACK=0. The connection reply (2nd packet in 3-way handshake) has SYN=1 and ACK=1.
- FIN : This bit is used to release a connection. It specifies that the sender has no more fresh data to transmit. However, it will retransmit any lost or delayed packet. Also, it will continue to receive data from other side. Since SYN and FIN packets have to be acknowledged, they must have a sequence number even if they do not contain any data.
- Window Size: Flow control in TCP is handled using a variable-size sliding window. The Window Size field tells how many bytes may be sent starting at the byte acknowledged. Sender can send the bytes with sequence number between (ACK#) to (ACK# + window size - 1) A window size of zero is legal and says that the bytes up to and including ACK# -1 have been received, but the receiver would like no more data for the moment.Permission to send can be granted later by sending a segment with the same ACK number and a nonzero Window Size field.
- Checksum : This is provided for extreme reliability. It checksums the header, the data, and the conceptual pseudoheader. The pseudoheader contains the 32-bit IP address of the source and destination machines, the protocol number for TCP(6), and the byte count for the TCP segment (including the header).Including the pseudoheader in TCP checksum computation helps detect misdelivered packets, but doing so violates the protocol hierarchy since the IP addresses in it belong to the IP layer, not the TCP layer.
- Urgent Pointer: Indicates a byte offset from the current sequence number at which urgent data are to be found. Urgent data continues till the end of the segment. This is not used in practice. The same effect can be had by using two TCP connections, one for transferring urgent data.
- Options : Provides a way to add extra facilities not covered by the regular header. eg, o Maximum TCP payload that sender is willing to handle. The maximum size of segment is called MSS (Maximum Segment Size). At the time of handshake, both parties inform each other about their capacity. Minimum of the two is honoured. This information is sent in the options of the SYN packets of the three way handshake. Window scale option can be used to increase the window size. It can be specified by telling the receiver that the window size should be interpreted by shifting it left by specified number of bits. This header option allows window size up to 230
- Data: This can be of variable size. TCP knows its size by looking at the IP size header.
The document Overview of Transport Layer | Computer Networks - Computer Science Engineering (CSE) is a part of the Computer Science Engineering (CSE) Course Computer Networks.
All you need of Computer Science Engineering (CSE) at this link: Computer Science Engineering (CSE)
|
23 videos|171 docs|81 tests
|
FAQs on Overview of Transport Layer - Computer Networks - Computer Science Engineering (CSE)
| 1. What is TCP and what are its salient features? |  |
Ans. TCP stands for Transmission Control Protocol. It is a reliable, connection-oriented protocol used for transmitting data over IP networks. The salient features of TCP include:
- Reliability: TCP ensures that all data packets are delivered without errors, loss, or duplication. It uses acknowledgement and retransmission mechanisms to guarantee reliable data delivery.
- Connection-oriented: TCP establishes a connection between the sender and receiver before transmitting data. This connection is maintained until all data has been successfully transmitted.
- Flow control: TCP employs flow control mechanisms to manage the rate at which data is sent, preventing overwhelming the receiver. It uses sliding window techniques to optimize data transmission.
- Congestion control: TCP monitors network congestion and adjusts its transmission rate accordingly. It dynamically reduces or increases the amount of data sent to prevent network congestion.
- Error detection and recovery: TCP includes error detection and recovery mechanisms like checksums and sequence numbers to ensure data integrity and order.
| 2. How does TCP operate at the transport layer? |  |
Ans. TCP operates at the transport layer of the TCP/IP protocol suite. It provides reliable, connection-oriented communication between two hosts. TCP performs the following operations:
- Connection establishment: TCP uses a three-way handshake process to establish a connection between the sender and receiver. This involves exchanging synchronization (SYN) and acknowledgment (ACK) packets.
- Data transmission: Once the connection is established, TCP segments the data into smaller packets and adds header information. It then sends these packets over the network.
- Acknowledgment and retransmission: Upon receiving data packets, the receiver sends acknowledgment packets (ACK) back to the sender. If the sender does not receive an ACK within a specified time, it retransmits the packet.
- Flow control: TCP uses a sliding window mechanism to manage the flow of data. The sender adjusts the window size based on the receiver's ability to process data, preventing overflow or underflow.
- Connection termination: When all data has been transmitted, TCP initiates a connection termination process. It uses a four-way handshake to ensure all data is received correctly before closing the connection.
| 3. How does TCP ensure reliable data delivery? |  |
Ans. TCP ensures reliable data delivery through various mechanisms:
- Acknowledgment: TCP receiver sends acknowledgment packets (ACK) to the sender for each successfully received data packet. This confirms the successful delivery of data.
- Retransmission: If the sender does not receive an acknowledgment within a specified time, it assumes that the packet was lost and retransmits it. This ensures that all data packets reach the receiver.
- Sequence numbers: TCP assigns a sequence number to each data packet. The receiver uses these sequence numbers to rearrange the packets in the correct order. If any packets are missing, TCP requests their retransmission.
- Checksum: TCP includes a checksum in each packet to detect errors during transmission. The receiver verifies the checksum and discards packets with errors, requesting their retransmission.
- Sliding window: TCP uses a sliding window mechanism to manage the flow of data. It ensures that the sender does not overwhelm the receiver by adjusting the window size dynamically based on available buffer space.
| 4. What is the purpose of TCP's flow control mechanism? |  |
Ans. The purpose of TCP's flow control mechanism is to prevent overwhelming the receiver with a large amount of data. It ensures that the sender does not transmit data at a rate that exceeds the receiver's processing capability. TCP achieves flow control through a sliding window mechanism. The receiver advertises its available buffer space to the sender using a window size. The sender adjusts the amount of data it sends based on the receiver's window size. If the window size is small, the sender reduces its transmission rate. If the window size is large, the sender increases its transmission rate. This mechanism prevents buffer overflow at the receiver and ensures smooth data transmission.
| 5. How does TCP handle network congestion? |  |
Ans. TCP handles network congestion through its congestion control mechanism. It dynamically adjusts its transmission rate based on the level of network congestion. TCP employs the following techniques for congestion control:
- Slow start: When a TCP connection is established, the sender starts by sending a small number of packets. If these packets are successfully delivered, the sender exponentially increases the transmission rate until it detects congestion.
- Congestion avoidance: Once congestion is detected, TCP switches to a congestion avoidance phase. The sender increases its transmission rate linearly and monitors the network for any signs of congestion. If congestion is detected, it reduces the transmission rate.
- Fast retransmit and recovery: If the sender receives duplicate acknowledgments for a particular packet, it assumes that the packet was lost and immediately retransmits it. This reduces the time required for recovery and keeps the network congestion under control.
- Explicit congestion notification (ECN): TCP can also use ECN, a mechanism where routers explicitly mark packets to indicate congestion. The sender adjusts its transmission rate based on these marked packets, reducing congestion in the network.
Related Searches





















