RRB JE IT (CBT II) Mock Test- 2 - Computer Science Engineering (CSE) MCQ
30 Questions MCQ Test - RRB JE IT (CBT II) Mock Test- 2
Which among the following is the capital of Belgium?
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
Which type of volcano is the Popocatepetl Mountain?
The output of an AND gate with three inputs, A, B and C, is HIGH when ______.
Which is not the component of the information system.
________ is a Linux command that shows the running processes as a tree.
What will be the integer printed in the output of the below given statements in Java?
int a = 0, b = 2;
int tb = b == 0 ? 10 : 20;
System.out.println(“Ternary operator: ” + tb);
_________ is used to repeat the last executed command.
In _____, lack of change in the level of voltage determines the value of the bit.
In Java, which operator dynamically allocates memory for an object and returns a reference to it?
What are the methods in the Applet Class that controls an applet’s execution?
I. start()
II. destroy()
III. initialize()
IV. end()
Which of the variable declaration or initialization in Java is not allowed?
Which is not the development phase of the classical waterfall model?
Sea salt, pollen, ash, smoke soot, fine soil — these are associated with:
Servers, workstations, networks, telecommunications equipment, fiber-optic cables, mobile devices, scanners, digital capture devices, and other technology-based infrastructure is an example of ____ component of the information system.
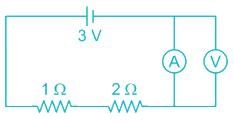
In the circuit shown in figure, the voltmeter reading would be
Which system privilege a user must have to create a function in their own schema or in another user’s schema or to replace a function in another user’s schema?
Who has been appointed as the head coach of the Indian table tennis team in July 2019?
Who predicted that the number of transistors on an integrated circuit chip would double about every 24 months? What are his concepts called?

















