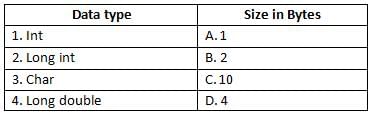
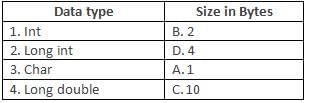
Computer Science: CUET Mock Test - 8 - Humanities/Arts MCQ
30 Questions MCQ Test - Computer Science: CUET Mock Test - 8
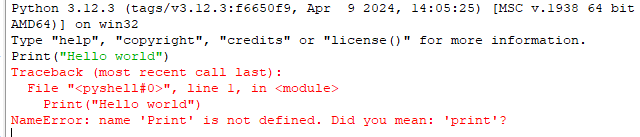
Considering the given statement in Python Print("Hello world")
What type of error will be generated?
The British scientist who invented world wide web in 1990 is ________.
Read the following statements and arrange in correct order.
A. Exception is raised
B. Executes exception
C. Program searches for exception handler
D. Create exception object
E. An error encountered
Choose the correct answer from the options given below:
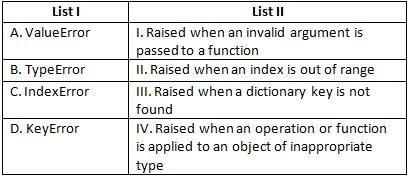
Match List I with List II.
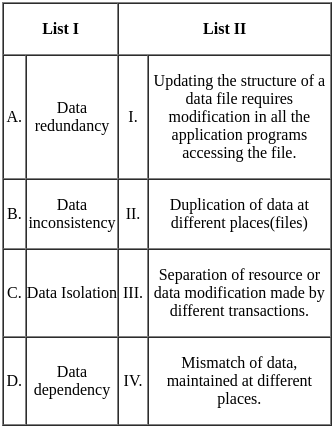
Choose the correct answer from the options given below:
In context with Relational Algebra, which of the following are Unary operators?
1. Select
2. Project
3. Union
4. Product
Two statements are given below:
Statement I: Stack follow Last In First Out (LIFO)
Statement II: Delete is possible from Bottom as well as Top.
Which of the following is not a keyword in SQL?
Which of the following operations in relation algebra requires two relations having the same number of attributes?
Which of the following functions is not performed by DDL?
Two statements are given below:
Statement I: Prefix notation for the (a+b)*(c-d) is +*ab-cd.
Statement II: Postfix notation for the (a+b)*(c-d) is ab+cd-*.
The 'is empty ( )' function can be also be written by using
Directions: Match the contents under List I with those under List II.
Which of the following term includes the mean of the processed data during business operations?
Which rule of a communication protocol prevents a fast sender from flooding a slow receiver with data, by regulating the flow of data on communication lines?
The relational model uses some unfamiliar terminology. A tuple is equivalent to _________.
A database management system (DBMS) is a ________.
SQL commands which come under 'Data Definition Language' are ___________.
Based on transmission technology, computer networks can be classified into _____ type(s) of networks.
In context of computer software, what does spyware mean?
_______ defines the rules and regulations that are to be followed during data communication.