UGC NET Paper 2 Computer Science Mock Test - 1 - UGC NET MCQ
30 Questions MCQ Test - UGC NET Paper 2 Computer Science Mock Test - 1
Requirements established during requirements analysis are validated against developed software in
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
Which of the following statements are useful for the Internet of Things to Grow Ecommerce Businesses?
Statement 1:Better tracking and logistics
Statement 2: Automated management of inventory
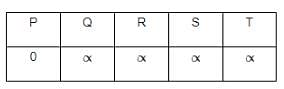
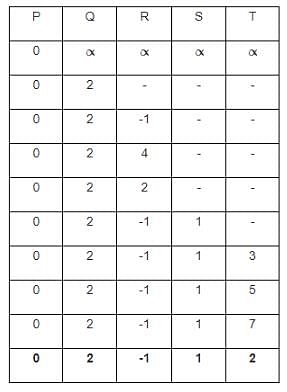
Taking into account the provided weighted graph, the Bellman-Ford algorithm is applied with vertex P serving as the source. The minimum distance from the starting point P to the target vertex T is determined as _______.
Which of the following statements are False for cache misses?
I. Larger blocks reduce compulsory misses by improving temporal locality.
II. A direct mapped cache of size N has the miss rate of half of the 2-way cache of size N/2.
III. Victim cache does not affect cycle time or miss penalty.
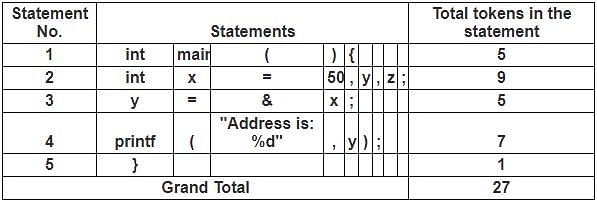
Consider the following C program:
int main() {
int x = 50, y, z;
y = &x;
printf("Address is: %d", y);
}
Count the number of tokens in the above program.
Which of the following is true?
(i) On average, neural networks have higher computational rates than conventional computers.
(ii) Neural networks learn by example.
(iii) Neural networks mimic the way the human brain works.Consider the following graph:
i) Minimum spanning tree is unique with weight 7.
ii) Second best minimum spanning tree is unique with weight 8.
iii) Maximum spanning tree is unique with weight 15.
Which of the above statements is/are TRUE?
Maximal matching of a wheel graph W4 is W, chromatic number of cycle graph C4 is X, vertex connetivity of bipartite graph K2,3 is Y and Edge connectivity of bipartite graph K2,3 is Z. Then W+X+Y+Z= _________?
MergeSort algorithm given with (n × k) sorted subarrays, where each subarray is having size of 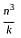 , What is the time complexity for finding single sorted array?
, What is the time complexity for finding single sorted array?
Assume that p and q are non-zero positive integers, the following program segment will perform -
While (p! = 0)
{
If (p>q)
p=p-q;
else,
q=q-p;
printf("%d",p);
}
Name the database that must be independent of the application that uses it.
The translator which perform macro expansion is called a-
While using the iterative construct (Branching) in execution _____________ instruction is used to check the condition.
Name the database object in MS Access that stores a question about the data in the database?
“Sharding” a database across many server instances can be achieved with _______________.
The maximum number of nodes in a binary tree of depth 10 is:
Determine the value of x, where y = 7, e = 12 and n = 566 using modular exponentiation method (x ≡ ye (mod n)).
Dynamic programming developed in optimization techniques are widely applied in __________.
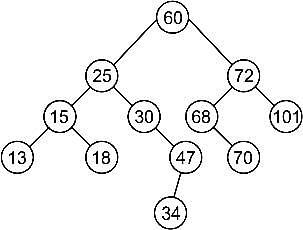
Direction:- A binary search tree is constructed by inserting the following numbers in order:
60, 25, 72, 15, 30, 68, 101, 13, 18, 47, 70, 34
The number of nodes in the left subtree is:
Which transformation distorts the shape of an object such that the transformed shape appears as if the object were composed of internal layers that had been caused to slide over each other?
The assembler stores the object code in ___________.
What field type is best to store serial numbers?
Which of the following is not a component of relational database?
The language used in application programs to request data from the DBMS is referred to as __________.