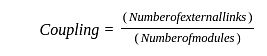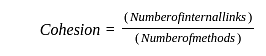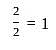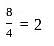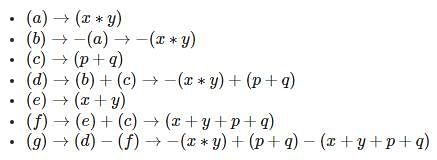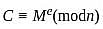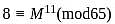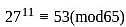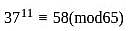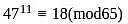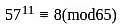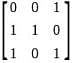UGC NET Paper 2 Computer Science Mock Test - 8 - UGC NET MCQ
30 Questions MCQ Test - UGC NET Paper 2 Computer Science Mock Test - 8
In C++, which of the following system-provided functions is called when no handler is provided to deal with an exception?
Consider a schema R(ABCD) and functional dependencies A → B, C → D. The decomposition of R into R1(AB) and R2(CD) is
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
The following figure represents access graphs of two modules M1 and M2. The filled circles represent methods and the unfilled circles represent attributes. If method m is moved to module M2 keeping the attributes where they are, what can we say about the average cohesion and coupling between modules in the system of two modules?
Which of the following statement are true?
Statement 1: Depth First Search uses the stack data structure.
Statement 2: Breadth First Search uses the queue data structure.
Statement 3: Depth First Search uses a backtracking technique.
Statement 4: Breadth-first search uses the Branch-and-Bound traverse technique.
Consider the given three address code table given below:
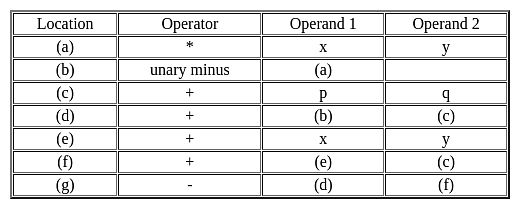
Which of the following expression represents the above given three address code?
Consider the following Statements
S1: Regular languages are a subset of the set of languages accepted by TMs which do not write anything on the tape.
S2: The set of languages accepted by halting TMs with a bidirectional infinite tape is a proper superset of decidable language.
S3: Every decidable language can be accepted by a DFA with a priority queue.
Which of the statements are not true?
Given F(A,B,C,D) = Σm (0, 1, 2, 5, 10, 15)
d(A, B, C, D) = Σm (6, 7, 8, 13)
Then Number of prime implicants and essential prime implicants respectively are__________:
A participant uses two prime numbers p and q are 5 and 13 in an RSA cryptosystem, to create public and private keys. If the participant's public key is 11 and the ciphertext (C) is 8, what is the original message (M)?
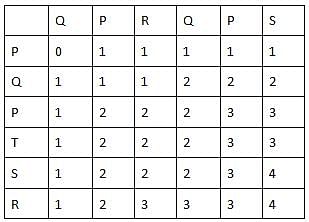
Consider the following strings:
S1 = PQPTSR
S2 = QPRQPS
Find the length of the longest common subsequence by using dynamic programming.
Consider a system with a logical address of 23 bits, a physical address of 128 MB, and a page size of 8 KB. Calculate the page table size in bytes.
HART is a digital communication protocol for sending and receiving information. It uses which of the following current loop standards?
Classless Inter-domain Routing (CIDR) receives a packet with address 182.25.110.68. The router’s routing table has the following entries:
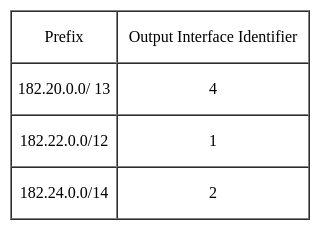
The identifier of the output interface on which this packet will be forwarded is ______.
For any three sets A, B and C the set
(A U B U C) ∩ (A ∩ B' ∩ C')' ∩ C' is equal to
Consider the following Statements
Statement 1: Greedy technique solves the problem correctly and always provides an optimized solution to the problem.
Statement 2: Bellman ford, Floyd-warshal, and Prim’s algorithms use the Dynamic Programming technique to solve the Path problems.
Which of the following is true?
Let the following is the sub-image 3 x 3, where each pixel is represented with 4-bits. Obtain all the bit plane slicing images of this.

Which of the following is not a valid bit plan slicing?
Consider the following segment of codes related to process creation. How many times the message “child process created” will be printed?
#include<stdio.h>
void main() {
fork(); fork(); fork();
printf(“child process created”);
}What is the minimum number of nodes that must be examined in order to find the minimum value in an AVL tree of height 5?
______ structure is usually used to connect I/O devices.
A heavy line on a video monitor could be displayed as:
The processes that are residing in main memory and are ready and waiting to execute are kept on a list called _____________.
The importance of software design can be summarized in a single word which is:
Direction:- Consider the following postfix expression with single digit operands:
623∗/42∗+68∗−
The top two elements of the stack after the second ∗ is evaluated, are:
Which is the best way to solve game playing problem?
A language can be generated from simple primitive language in a simple way if and only if:
Hasse diagrams are first made by _________.