UGC NET Paper 2 Computer Science Mock Test - 1 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series 2025 - UGC NET Paper 2 Computer Science Mock Test - 1
A 4-bit synchronous UP counter is holding a state 0101. What will be the count after 27th clock pulse?
A slotted ALOHA network transmits 200 bits frames using a shared channel with 200 kbps bandwidth. If the system (all stations put together) produces 1000 frames per second, then the throughput of the system is
For a program of k variables, boundary value analysis yields ______ test cases.
Which of the following statements are useful for the Internet of Things to Grow Ecommerce Businesses?
Statement 1:Better tracking and logistics
Statement 2: Automated management of inventory
Which of the following is/are the examples of symmetric encryption methods?
(i) Data Encryption Standard (DES)
(ii) Advanced Encryption Standard (AES)
(iii) Rivest – Shamir – Adleman (RSA)
(iv) Public Key Infrastructure (PKI)
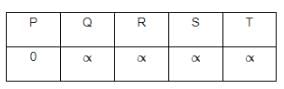
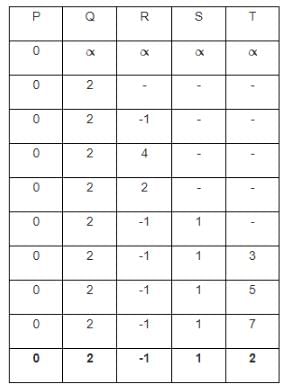
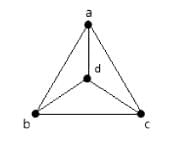
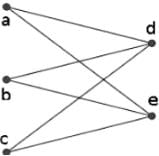
Taking into account the provided weighted graph, the Bellman-Ford algorithm is applied with vertex P serving as the source. The minimum distance from the starting point P to the target vertex T is determined as _______.
Which of the following statements are TRUE?
1. The problem of determining whether there exists a cycle in an undirected graph is in P.
2. The problem of determining whether there exists a cycle in an undirected graph is in NP.
3. If a problem A is NP-Complete, there exists a non-deterministic polynomial time algorithm to solve A.
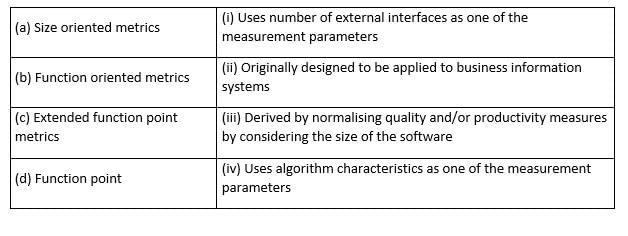
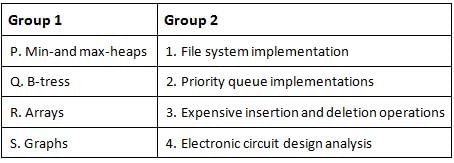
Match all items in Group 1 with the best match from the options given in Group 2.
Which of the following statements are true?
A) Classification and Regression are supervised learning techniques.
B) Clustering and Density Estimation are unsupervised learning techniques.
C) Supervised learning is learn input and output map.
D) Unsupervised learning is discover pattern in the input data.
E) Reinforcement learning describes a class of problems where an agent operates in an environment and must learn to operate using feedback.
Which of the following is true?
(i) On average, neural networks have higher computational rates than conventional computers.
(ii) Neural networks learn by example.
(iii) Neural networks mimic the way the human brain works.Maximal matching of a wheel graph W4 is W, chromatic number of cycle graph C4 is X, vertex connetivity of bipartite graph K2,3 is Y and Edge connectivity of bipartite graph K2,3 is Z. Then W+X+Y+Z= _________?
State whether True or False.
I. A Packet-Filter Firewall filters at the Application Layer whereas a Proxy Firewall filter at the Network or Transport Layer.
II. The idea that the cryptanalyst knows the algorithms and that the secrecy lies exclusively in the keys is called Kerckhoff’s principle.
A digital circuit has 3 input lines, 1 enable line and 8 output lines. This circuit will be called:
Name the database that must be independent of the application that uses it.
Which of the following is correct statement?
While using the iterative construct (Branching) in execution _____________ instruction is used to check the condition.
The public key of a given user, in an RSA encryption system is e = 57 and n = 3901. What is the value of Euler’s totient function ϕ(n) for calculating the private key of the user?
Which transformation distorts the shape of an object such that the transformed shape appears as if the object were composed of internal layers that had been caused to slide over each other?
The assembler stores the object code in ___________.
The open source movement has meant that there is a huge reusable code base available at ____________.
What field type is best to store serial numbers?
Which of the following is not a component of relational database?
A particular text index value is chosen with the function:
The memory allocation scheme subject to "external" fragmentation is:
|
92 docs|125 tests
|