UGC NET Paper 2 Computer Science Mock Test - 4 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series - UGC NET Paper 2 Computer Science Mock Test - 4
Which of the following is/are restriction(s) in classless addressing?
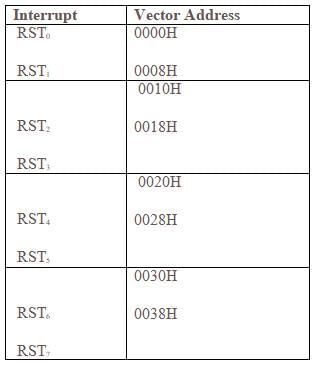
The RST 7 instruction in 8085 microprocessor is equivalent to
Which of the following tags is an extension to HTML that can enclose any number of Javascript statements?
This set of Microprocessor Multiple Choice Questions & Answers (MCQs) focuses on “Numeric Processor 8087 -1”.
1. The unit that executes all the numeric processor instructions in 8087 is
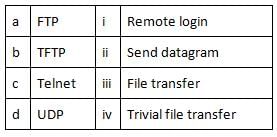
Match the following TCP/IP protocols with their uses.
The Boolean expression for the output f of the multiplexer shown below is
A local area network operates Ethernet with CSMA/CD mechanism and runs at a transmission rate of 8 Mbps and a one-way signal propagation time of 25 μs. How long (us) has a station to wait before trying to access the channel again, after experiencing 5 successively collisions?
If S = {a, b, c, d) and p = {(a, a), (b, b), (c, c), (d, d), (a, b), (b, a),(b, c), (c, b)}, then p is-
Which of the following is Not a NP Complete problem?
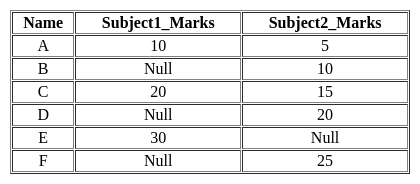
Consider the following student relation.
Student relation has Name, Subject1_Marks, and Subject2_Marks attributes.
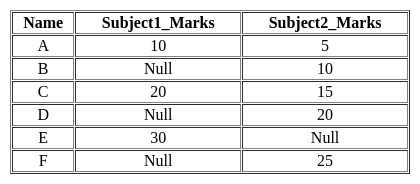
Query1:
Select count (*)
From student;
Query2:
Select count (10)
From student;
Query1 prints the Q1 and Query2 prints Q2. Which of the following condition is true?
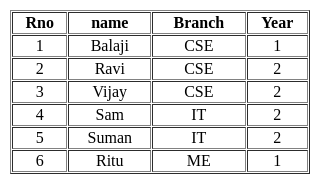
Consider the following relation.
Student(Rno, name, Branch, Year)
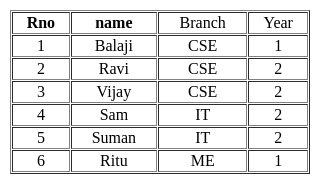
What is the output for the given query?
Query:
Select distinct branch
from student ;
Relation R has eight attributes ABCDEFGH. Fields of R contain only atomic values.
F={CH→G, A→BC, B→CFH, E→A, F→EG} is a set of functional dependencies (FDs) so that F+ is
exactly the set of FDs that hold for R.
The relation R is
Which of the following statements is False?
Statement 1: A single deque can support both stack and queue operations.
Statement 2: A single stack can support both deque and queue operations.
Statement 3: A single queue can support both stack and queue operations.
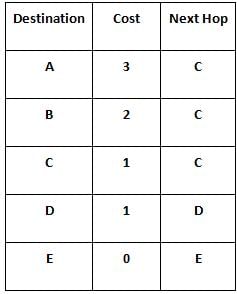
Consider a network with 5 routers A, B, C, D and E as shown below.
All the routers use the distance vector routing algorithm to update their routing tables. The cost of link D - E reduces to 1. After the next round of updates, what will be the new distance vector at router E?
The height of a tree is the length of the longest root-to-leaf path in it. The maximum and the minimum number of nodes in a binary tree of height 5 are:
Which of the following is page fault?
If any intensity input value near 0.33 would be stored as the binary value 1 in the frame buffer, then it displays-
Which of the following is true in Statistical reasoning?
The "turn-around" time of a user job is the:
If the angle between 2 connected line segments is very small then ________ can generate a long spike that distorts the appearance of the polyline.
The Flag ‘V’ is set to 1 indicates that _____________.
Which algorithm is used to solve any kind of problem?
Given an unsorted array. The array has this property that every element in array is at most k distance from its position in sorted array where k is a positive integer smaller than size of array. Which sorting algorithm can be easily modified for sorting this array and what is the obtainable time complexity?
|
92 docs|125 tests
|



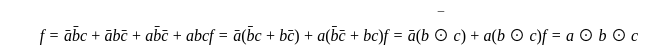
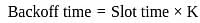
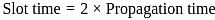
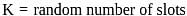
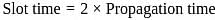
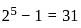 (as per Ethernet standard).
(as per Ethernet standard).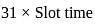 :
: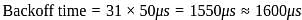
 x ∈ A ,i.e xRx, ∀ x,y
x ∈ A ,i.e xRx, ∀ x,y  R ⇒ (y, x)
R ⇒ (y, x) R
R