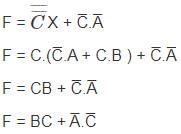UGC NET Paper 2 Computer Science Mock Test - 5 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series 2025 - UGC NET Paper 2 Computer Science Mock Test - 5
Which of the following is not a congestion policy at network layer?
The process of dividing an analog signal into a string of discrete outputs, each of constant amplitude, is called
In link state routing algorithm, after construction of link state packets, new routes are computed using
Consider the following two statements.
(A) Data scrubling is a process to upgrade the quality of data, before it is moved into data warehouse.
(B) Data scrubling is a process of rejecting data from data warehouse to create indexes.
Which of the following options is correct?
Identify whether the given statements are true or false.
(i) Relative URL does not require protocol identifier.
(ii) Scheme://Server/Path/Resource is the correct syntax for an absolute URL.
Consider three floating-point numbers A, B and C stored in registers RA, RB and RC, respectively as per IEEE-754 single-precision floating point format. The 32-bit content stored in these registers (in hexadecimal form) are as follows.
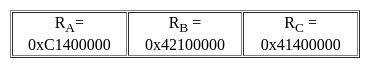
Which one of the following is FALSE?
Consider the two cascaded 2-to-1 multiplexers as shown in the figure.
What is the output F of the above logic circuit?
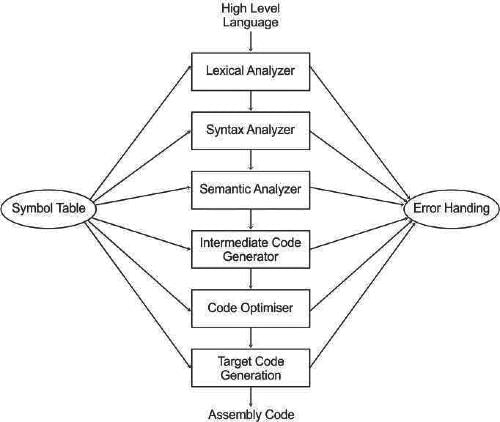
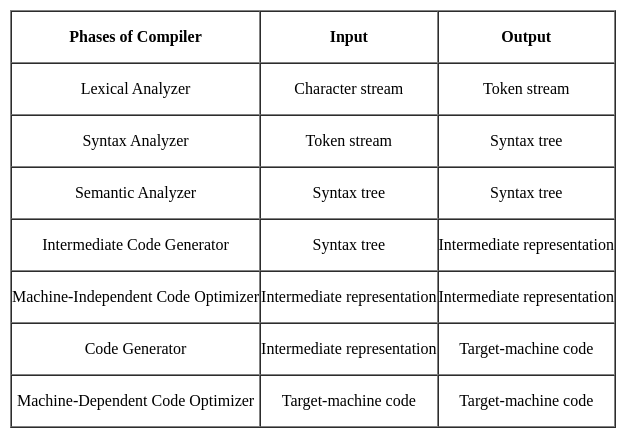
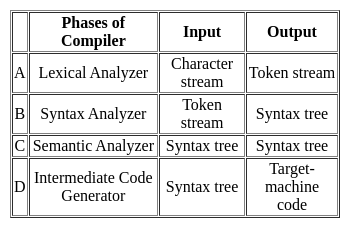
Which of the following not correct according to input to output, the compiler phase that is processes by it?
The correct statement regarding WiFi and Wi-Max technology is/are -
(I) WiFi uses radio waves to create wireless connection, WiMax uses spectrum to deliver the connection.
(II) WiFi is defined under IEEE 802.11x standards, while WiMax is defined under IEEE 803.16y standards
(III) WiMax covers a comparatively larger area than WiFi.
Consider the following statements:
I. A proxy firewall filters at the application layer.
Il: A packet-filter firewall filters at the network or transport layer.
Which of the above statements is/are true?
Consider the given binary search tree, if the root node will be deleted, the new root can be -
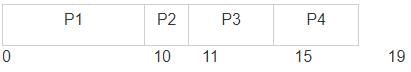
What is the average waiting time of processes in this schedule? (Assume Pre-emptive priority scheduling policy, further assume lower number represents higher priority).
The following Schedule is an example of which scheduling policy?
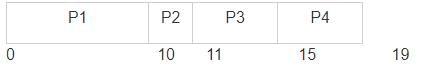
What is the average waiting time of processes in this schedule? (Assume FCFS).
Which one indicates a technique of building cross compilers?
Shell is the exclusive feature of-
Coaxial cable has conductors with _____.
Which module gives control of the CPU to the process selected by the short-term scheduler?
The transmission signal coding method for T1, the carrier is called:
Which is considered as the sequence of characters in a token?
While transmitting odd-parity coded symbols, the number of zeros in each symbol is.
Which graph describes the basic block and successor relationship?
Which of the following testing technique deeply emphasizes on testing of one specific module?
|
92 docs|125 tests
|