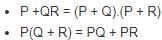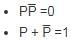UGC NET Paper 2 Computer Science Mock Test - 9 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series - UGC NET Paper 2 Computer Science Mock Test - 9
Consider the following statements related to compiler construction.
I. Lexical analysis is specified by context free grammar and implemented by pushdown automata.
II. Syntax analysis is specified by regular expressions and implemented by finite-state machine.
Which of the above statements is/are correct?
Which of the following things are considered to be very important to design the algorithm.
If an image has a height of 4 inches and an aspect ratio of 3 : 2, then what will be the width of the image?
Which of the following basic steps are needed in order to perform a memory read operation?
1. The address of the location from which the word is to be read is loaded into the memory address register (MAR).
2. A signal, called read (issued by the CPU indicating that the word whose address is in the MAR) is to be read into the MDR.
3. Corresponding to the memory delay in reading the specified word, the required word will be loaded by the memory into the MDR ready for use by the CPU.
Select the correct answer using the code given below.
How many minimum number of states will be there in the DFA (over the alphabet {a, b}) accepting all the strings with the number of a’S divisible by 4 and number of b’S divisible by 5?
Mark is interviewing for the role of a database developer. To help with the revisions, he made himself a quiz. Help him answer the questions.
The default format for the DATE datatype in MySQL is:
There are n jobs are waiting in the ready queue and the CPU uses a non-preemptive shortest job first scheduling algorithm. what is the time complexity of the shortest job first algorithm when jobs are non-preemptive in nature?
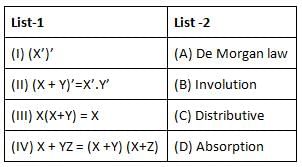
The simplified SOP (Sum of Product) form of the Boolean expression
(P + Q̅ + R̅)⋅(P + Q̅ + R)⋅(P + Q + R̅) is
The reason for software bugs and failures is due to ____________.
Which action sequences are used to achieve the agent’s goal?
The assembler stores all the names and their corresponding values in ______.
Which tool is used for structured designing?
The computer architecture aimed at reducing the time of execution of instructions is ________.
The primary aim of structural optimization is to determine the __________.
Which of the following is not of the same group?
A line drawn in the background color is:
Which search strategy is also called as blind search?
What is another name for the circular queue among the following options?
Does the Load instruction do the following operation/s?
Entries in the bundle table for line attributes are set using the function:
|
92 docs|125 tests
|