Computer Science: CUET Mock Test - 9 - CUET MCQ
30 Questions MCQ Test CUET UG Mock Test Series 2026 - Computer Science: CUET Mock Test - 9
Which of the following precedence orders is correct in Python?
Rohan starting working on MYSQL server. Kindly arrange the the following commands in a sequence so that he can create a table, then insert a record into it and display all the records.
A. Insert into command
B. Create database ; ;
C. Create table command
D. Use ;
E. Select * from ;
Choose the correct answer from the options given below:
A. Insert into command
B. Create database ;
C. Create table command
D. Use
E. Select * from
Choose the correct answer from the options given below:
Mr. Sameer wants to connect 20 systems, which are present within a single hall. Help him choose the best device out of the following to achieve his purpose.
[Note that the data arriving on any of the lines should be sent to the intended node / receiver only]
In file mode _________, the file offset position is end of the file.
Which of the following is not an SQL commands category?
What will be the output of the following python code?
x=['ab', 'cd']
for i in x:
x.append(i.upper())
print(x)
Secure transfer of data over an unsecured network such as internet can be done using
Consider the usual algorithm for determining whether a sequence of parentheses is balanced. The maximum number of parentheses that appear on the stack AT ANY ONE TIME when the algorithm analyzes: (()(())(()))is:
Two statements are given below:
Statement I: strings = ['apple', 'banana', 'cherry', 'date']lengths = list(map(lambda s: len(s), strings))print(lengths)# Output: [5, 6, 6, 4]
Statement II: strings = [ 'cherry', 'date', 'apple', 'banana',]lengths = list(map(lambda s: len(s), strings))print(lengths)# Output: [6, 4, 5, 6]
____ are instructions given by the user to the database also known as statements.
Match List-I with List-II:
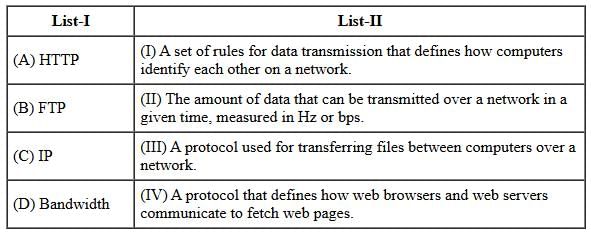
Choose the correct answer from the options given below:
Which commands provide definitions for creating table structure, deleting relations and modifying relation schemas?
A text file student.txt is stored in the storage device. Identify the correct option out of the following to open the file in read mode.
i. myfile = open('student.txt','rb')
ii. myfile = open('student.txt','w')
iii. myfile = open('student.txt','r')
iv. myfile = open('student.txt')
Which of the following components is/are part(s) of a function header in Python?
Which of the following communication channels is established during telephone conversation?
Two statements are given below:
Statement I: Purpose of the hue parameter in the seaborn library is to specify the color of the plot.
Statement II: Purpose of the hue parameter in the seaborn library to specify the variable to use for color encoding.
Directions: Match the contents under List I with those under List II.
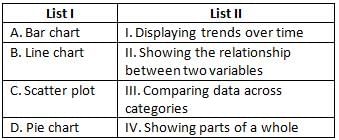
Which of the following is not a type of computer network?
The writelines() function is used for ___________________.
When a particular section of code can raise more than one errors then to handle this __________ number of except block can be possible for one try block.
Which of the following error will be raised by the given Python code:
randomList = ['a', 2, 3]
for element in randomList:
print("The element is ", element)
x = int(element+1)
print("The incremeant of ", element, "is", x)
Which exception is raised when an interpreter does not find the requested module definition?
Which statement is generally used in the beginning of the function or after a function call to check for valid input?
Match List-I with List-II:
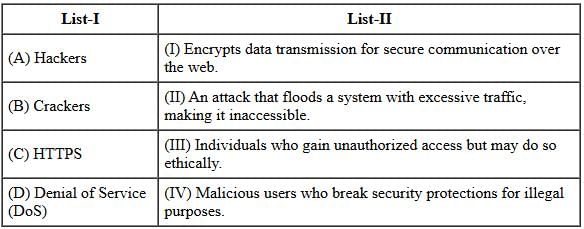
Choose the correct answer from the options given below:
|
39 docs|145 tests
|














