Computer Knowledge - 3 - SSC CGL MCQ
20 Questions MCQ Test SSC CGL Tier II Mock Test Series 2024 - Computer Knowledge - 3
What are the startup routines that execute when a machine is turned on?
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
Which of the following are not applications of the Internet?
______ is a technology that allows computers and other devices to communicate via a wireless signal.
In Gmail, what do you use when you receive mail and want to send the mail in response to the same mail and to the original sender only?
Which one of the following registers is used to keep track of the next instruction to be executed?
The 'Ctrl + W' keyboard shortcut is used for which of the following purposes in MS-Word 365?
Which among the following are the two types of computer memory?
Which of the following device is used for generating hard copies of a document?
What is a reserved portion of a hard disk that is used as an extension of random-access memory (RAM)?
What do we call a short block of code which takes in parameters and returns a value?
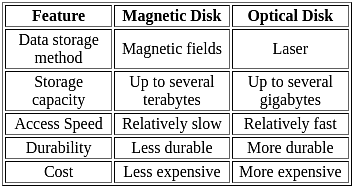
Which of the following term is used for both the data storing and transmitting devices?
Which of the following key is used to create a relationship between two tables in DBMS?
For which type of cell reference in MS-Excel a ‘$’ symbol is used?
A ________ is a continuous memory without any addressing and stores data serially.
What does the ‘Print Range’ option allow you to specify when printing slides in PowerPoint?
|
66 docs|139 tests
|
|
66 docs|139 tests
|