Computer Science: CUET Mock Test - 6 - CUET MCQ
30 Questions MCQ Test CUET UG Mock Test Series 2026 - Computer Science: CUET Mock Test - 6
Two statements are given below:
Statement I: Normalization is the process of organizing data in a database into tables to reduce redundancy.
Statement II: Normalization is the process of organizing data in a database into tables to reduce dependancy.
Statement II: Normalization is the process of organizing data in a database into tables to reduce dependancy.
________ is world wide interoperability for microwave access, uses a larger spectrum to deliver connections to various devices.
Examples of Guided media are _______.
A. Radio Waves
B. Optical - fiber
C. Micro waves
D. Twisted pair
E. Coaxial cable
Choose the correct answer from the options given below:
Consider the following function for insertion_sort
def insertion_sort(list3):
n = len(list3)
for i in _______ : # [statement-1]
temp = ________ : # [ statement-2]
j = i - 1
while j>= 0 and : # [statement-3]
list3 [j+1] = list3 [j]
j = _______ # [statement-4]
_______ = temp # [statement-5]
Given the following options for the statements.
A. temp <list3[j]
B. list3[i]
C. list3 [j+1]
D. range(n)
E. j-1
Choose the correct sequence of statement.
Which of the following is (are) attribute(s) of file object?
A. closed
B. mode
C. next
D. name
E. tell
Choose the correct answer from the options given below:
A sort algorithm works on the following principle.
- Find the smallest item in the list, and exchange it with the left-most unsorted element.
- Repeat the process from the first unsorted element.
Which of the following sorting algorithms does it correspond to?
A repeater is a device which operates only in the:
Which of the following string functions in 'C' converts lowercase input string into uppercase?
What is the fundamental unit of data transport on computer networks?
172.16.122.204 IP address belongs to which IP addresses class?
Two statements are given below:
Statement I: Hashing technique is very fast and efficient for large collections, but requires additional memory to store the hash table.
Statement II: Binary search technique is suitable for small collections but can be slow for larger collections.
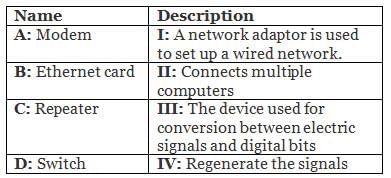
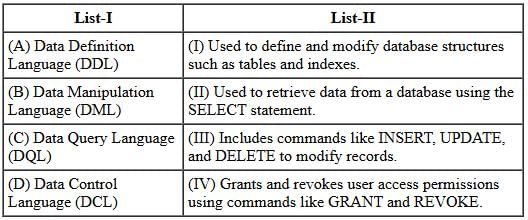
Directions: Match the contents under List I with those under List II.
Which of the following operators cannot be used with string data type?
Database management systems are intended to:
Which statement is true about denial of service (DOS attack)?
Consider a tuple tup1 = (10, 15, 25 and 30). Identify the statement that will result in an error.
Which of the following statements correctly describe stack operations?
(A) A stack follows the Last-In, First-Out (LIFO) principle.
(B) The PUSH operation adds an element to the top of the stack.
(C) The POP operation removes an element from the bottom of the stack.
(D) A stack can be implemented using lists in Python.
Choose the correct answer from the options given below:
A text file student.txt is stored in the storage device. Identify the correct option out of the following options to open the file in read mode.
(i) myfile = open('student.txt','rb')
(ii) myfile = open('student.txt','w')
(iii) myfile = open('student.txt','r')
(iv) myfile = open('student.txt')
Which module is to be imported for working in binary file?
What will be the output of the following program?
tuple=("Check")*3
print (tuple)
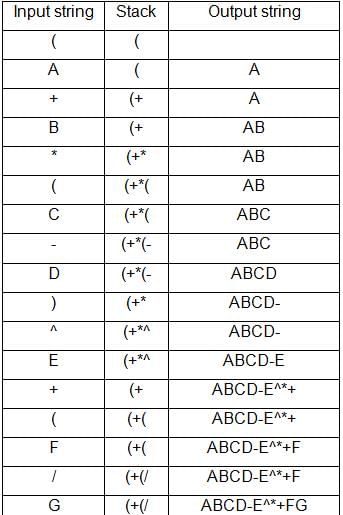
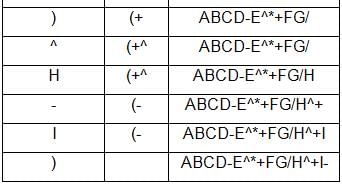
Convert the following infix expression to postfix expression using stack:
(A+B*(C-D)^E+(F/G)^H-I)
In python, Which of the following method is used find weather the queue is empty or not?
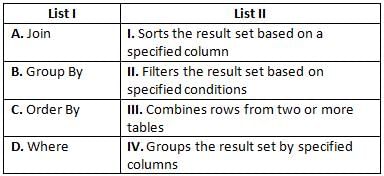
Match List-I with List-II:
Choose the correct answer from the options given below:
|
39 docs|145 tests
|