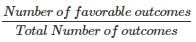UGC NET Paper 2 Computer Science Mock Test - 7 - UGC NET MCQ
30 Questions MCQ Test UGC NET Mock Test Series 2025 - UGC NET Paper 2 Computer Science Mock Test - 7
An analog signal has a bit rate of 8000 bps and a baud rate of 1000. Then, analog signal has _____ signal elements and carries _____ data elements in each signal.
Integrity constraints ensure that changes made to the database by authorised users do not result into loss of data consistency. Which of the following statements is/are true regarding the examples of integrity constraints?
(A) An instructor ID number cannot be null, provided instructor ID number being primary key.
(B) No two citizens have same Adhar ID.
(C) Budget of a company must be zero.
(A) An instructor ID number cannot be null, provided instructor ID number being primary key.
(B) No two citizens have same Adhar ID.
(C) Budget of a company must be zero.
Consider the following statements regarding key -
(I) A super key is an attribute or combination of attributes that uniquely identify records in an RDBMS table.
(II) A candidate key is a subset of a super key.
(III) All super keys are candidate keys but vice versa is not true.
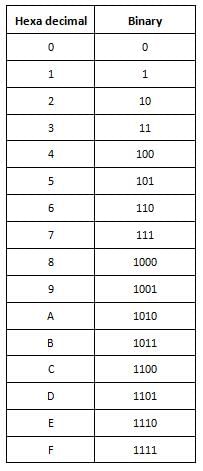
A Hexa-decimal number system has n digits to accommodate the number X. What maximum and minimum number digits are required to represent the number X in a binary number system?
Consider the following schedule for transactions T1, T2 and T3:
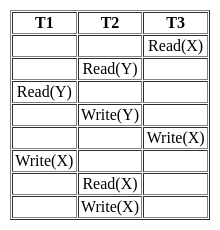
Which one of the schedules below is the correct serialization of the above transactions?
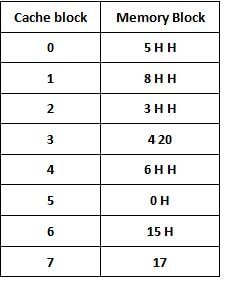
Consider a fully associative cache with 8 blocks. The memory block requests in the order.
5 8 5 3 4 6 3 8 5 6 0 15 6 17 20 15 0 8
If LRU is used for page replacement then which cache block will have memory block 20.
Consider the grammar G:
(assume Bottom up parsing)
S → 0{ printf(“a”) }A
A → 1{ printf(“b”) }B
A → 2{ printf(“c”) }
A → ϵ { printf(“-“) }
B → 3 { printf(“b”) }A
B → ϵ { printf(“a”) }
What will be the input for the output “cbbbba”?
Consider the transition diagram of a PDA given below with input alphabet ∑ = {a, b} and stack alphabet Γ = {X, Z}. Z is the initial stack symbol. Let L denote the language accepted by the PDA.
What will be the A and B transition respectively in order for PDA to accept the language { an|n ≥ 0} ∪ {anbn|n ≥ 0}?
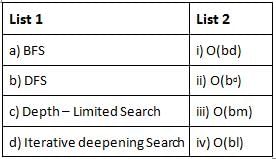
Consider the following terminology and match List 1 and List 2 and choose the correct answer from the code given below
b = branch factor
d = depth of shallowest solution
M = Maximum depth of the search tree
I = depth limit
In an examination there are 3 multiple-choice questions and each question hash 4 choice. If a student randomly selects an answer for all the three questions, what is the probability that the students will not answer all the three questions correctly?
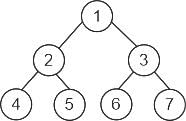
The above mentioned picture shows the:
Whenever a particular color code is specified in an application program, where is the corresponding binary value placed?
Which of the following is an application of depth-first search?
What is the minimum number of nodes in an AVL tree of height 5?
How do you represent “All dogs have tails”?
Automatic variables use which data structure for space allocation in memory?
If the size of the stack is 10 and we try to add the 11th element in the stack then the condition is known as ___________.
A dotted line can be displayed by generating:
Wide area networks (WANs) always require:
A production rule consists of ____________.
Heap allocation is required for languages that:
Which one of the following is not the type of the Queue?
What is developed by utilizing the historical cost function?
Table entries for bundled area-fill attributes are set using the function:
According to the given language, which among the following expressions does it corresponds to?
Language L={xϵ{0,1}|x is of length 4 or less}
|
92 docs|120 tests
|