CUET PG Computer Science Mock Test - 1 - CUET PG MCQ
30 Questions MCQ Test - CUET PG Computer Science Mock Test - 1
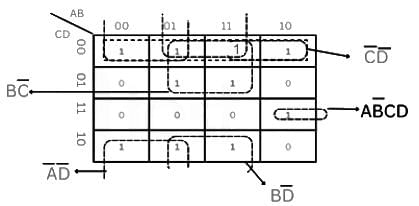
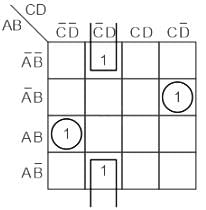
The minimized equation for the following logic function using K-map is ___________.
F(A, B, C, D) = ∑m(0, 1, 2, 3, 5, 7, 8, 9, 11, 14)
Which of the following options best describes the accuracy of the given statements?
i) URL stands for Uniform Resource Locator.
ii) The meaning of XML is Extensible Markup Language.
iii) ROM stands for Read-Only Memory.
ii) The meaning of XML is Extensible Markup Language.
iii) ROM stands for Read-Only Memory.
At what point the line y = x + 1 is a tangent to the curve y2 = 4x?
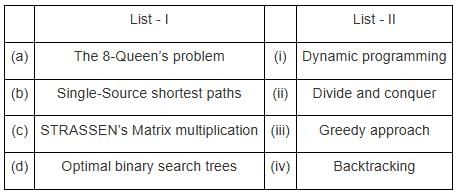
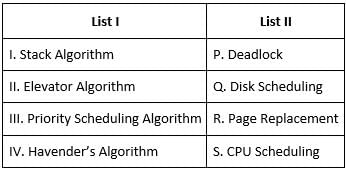
Match the following with respect to algorithm paradigms:
Consider the following program
main()
{
int x = 0, i, j;
for (i = 0, j = 10; i < 5,j>0; i+=2, j--)
++x;
printf("%d",x);
}
The output of the above program will be
Find the area of the region bounded by the curves y = x3, the line x = 2, x = 5 and the x - axis?
Which of the following operation easily performed by using a single stack?
Operation 1: Job Scheduling
Operation 2: Reversing the elements
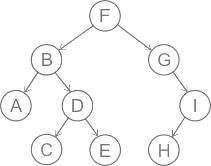
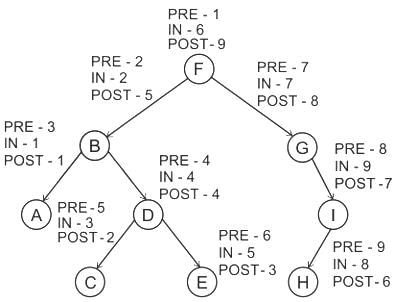
What is the sequence of nodes when applying in-order traversal on the binary tree given below?
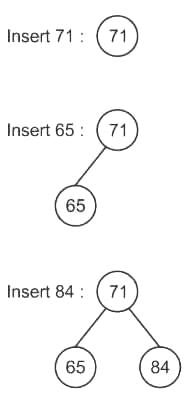
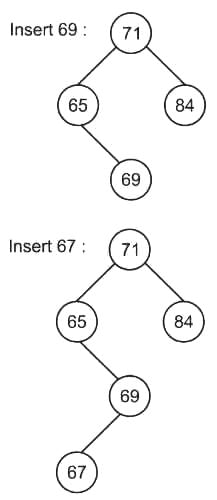
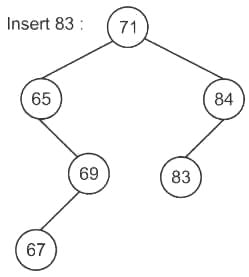
While inserting the elements 71, 65, 84, 69, 67, 83 in an empty binary search tree (BST) in the sequence shown, the element in the lowest level is
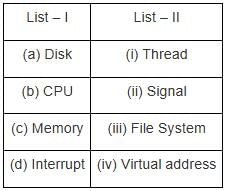
Match List - I with List - II.
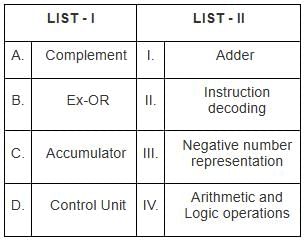
Choose the correct answer from the options given below :
Match List-I with List-II
Choose the correct option from those given below:
The boolean expression
Z = A̅B̅C̅D + A̅BCD̅ + AB̅C̅D + ABC̅D̅
can be minimized to?
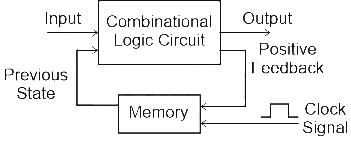
The basic building block of sequential logic circuit is-
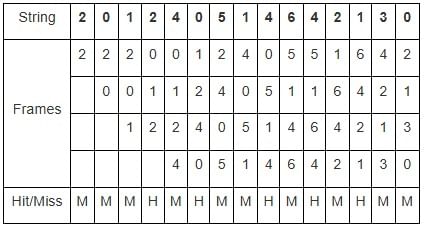
What is number of page faults by least recently used page replacement for a memory with 4 frames for the page reference string 2, 0, 1, 2, 4, 0, 5, 1, 4, 6, 4, 2, 1, 3, 0 ?
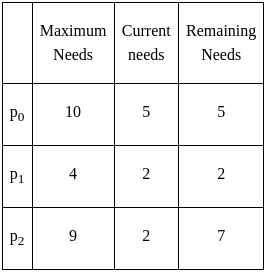
Suppose a system has 12 magnetic tape drives and at time t0, three processes are allotted tape drives out of their as given below:
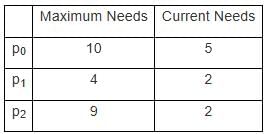
At time t0, the system is in safe state. Which of the following is safe sequence so that deadlock is avoided?
NOTE: Current Need is currently allocated resource to a process
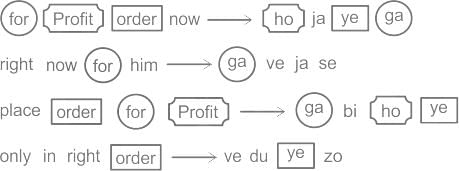
In a certain code,
'for profit order now' is written as 'ho ja ye ga'
'right now for him' is written as 'ga ve ja se'
'place order for profit' is written as 'ga bi ho ye'
'only in right order' is written as 've du ye zo'
What does 'bi' stand for?


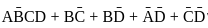
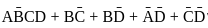

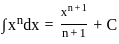
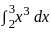
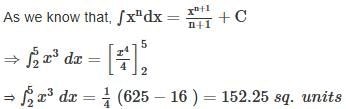
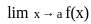
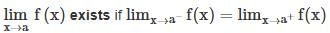
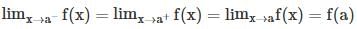
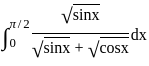 is
is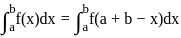
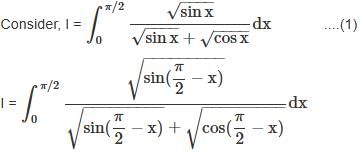
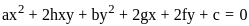
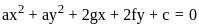
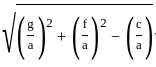 and center
and center 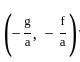
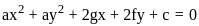
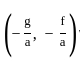 = (0, -3)
= (0, -3)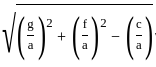
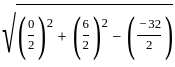
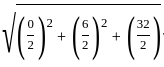
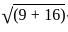 = 5
= 5