Computer Knowledge - 9 - SSC CGL MCQ
20 Questions MCQ Test SSC CGL Tier II Mock Test Series 2024 - Computer Knowledge - 9
Which of the following input devices is widely used in tests such as aptitude tests?
Which of the following is NOT a valid file format in MS-Word 365?
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
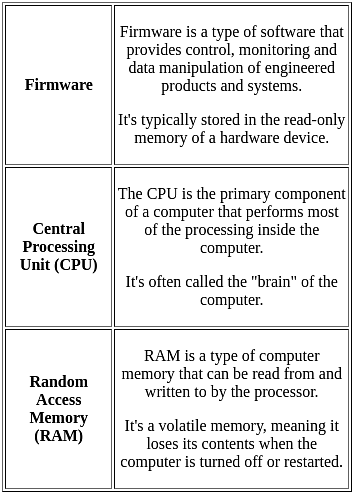
Which of the following memory is used to bridge the gap between the speed of CPU and RAM?
Which of the following options displays the name of the web page in an Internet Explorer browser?
______ is the key circuit board holding the essential processing parts of a computer.
Which cyber security measure involves verifying the identity of users before granting access to a system or network?
The devices that work with computer systems as soon as they are connected are described as
Personnel who design, program, operate and maintain computer equipment refers to _______ .
Which of the following can be used to acquire sensitive information from a device?
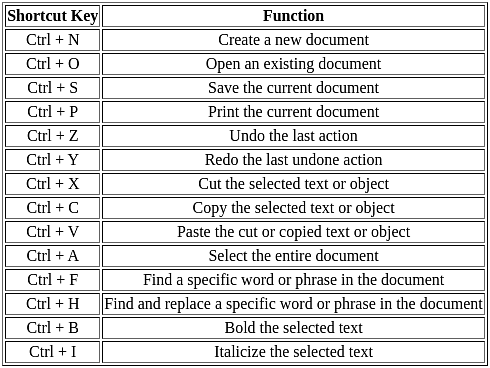
Which of the following keyboard shortcut is used for double underlining the text in MS-Word?
Which of the following is used by Windows to start the boot sequence?
A ________ is a command that returns the cursor to the next line and does not create a new paragraph in MS-Word.
In the context of computers, what is the full form of DFS?
Which of the following network devices are used to regenerate signals when they travel over a longer distance?
The input device used for selecting and drawing things on the screen is called ____
When a group of computers and devices are connected together, it is called ______.
|
66 docs|139 tests
|
|
66 docs|139 tests
|