|
The Internet is defined as a system architecture that revolutionizes global communications and commerce by linking ___ worldwide. |
Card: 1 / 30 |
|
True or False: The complexity of information in cyberspace has made it less important to maintain operational systems for safety and security. |
Card: 3 / 30 |
|
False - It is crucial to maintain operational systems for safety and security due to the complexity of information. |
Card: 4 / 30 |
|
Cyber Law is important because it encompasses all transactions and interactions online. (True/False) |
Card: 5 / 30 |
|
True. Cyber Law is essential because virtually every online action has legal implications. |
Card: 6 / 30 |
|
The anonymous nature of the internet ___ the detection of various criminal activities. |
Card: 7 / 30 |
|
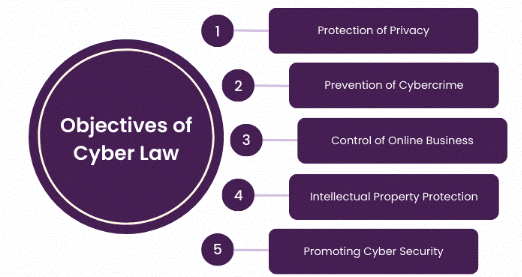
To address the legal implications of online activities and protect users from cybercrime. |
Card: 10 / 30 |
|
True or False: Cyber law includes regulations regarding electronic signatures and data protection. |
Card: 13 / 30 |
|
The transition of the internet from a research tool to a platform for e-business signifies its ___ in modern society. |
Card: 15 / 30 |
 Unlock all Flashcards with EduRev Infinity Plan Starting from @ ₹99 only
|
|
Cyber safety encompasses the secure and responsible use of ___ and ___ technology. |
Card: 17 / 30 |
|
True or False: Cyber-crime is limited to hacking and does not include activities like phishing or data theft. |
Card: 19 / 30 |
|
False. Cyber-crime includes a range of activities such as hacking, phishing, data theft, and cyber stalking. |
Card: 20 / 30 |
|
Cyber crime against government primarily includes ___, which is a form of cyber terrorism. |
Card: 21 / 30 |
|
True or False: Cyber bullying can occur through various platforms such as SMS, email, and social forums. |
Card: 23 / 30 |
|
Cybersecurity involves protecting information from unauthorized access, use, disclosure, disruption, modification, or destruction. True or False? |
Card: 25 / 30 |
|
True. Cybersecurity is fundamentally about safeguarding information and systems from various forms of unauthorized access and threats. |
Card: 26 / 30 |
|
The Information Technology Act of 2000 in India was enacted to recognize transactions conducted through ___ and ___ methods. |
Card: 27 / 30 |
|
What was the significance of the Model Law on Electronic Commerce adopted by UNCITRAL in 1996? |
Card: 29 / 30 |
|
It aimed to establish consistency in laws across different countries to facilitate electronic commerce by providing universally acceptable rules. |
Card: 30 / 30 |