Automated Business Processes: Notes (Part - 1) | Financial Management & Strategic Management for CA Intermediate PDF Download
| Table of contents |

|
| Chapter Overview |

|
| Introduction |

|
| Enterprise Business Processes |

|
| Automated Business Processes |

|
| Risks and Its Management |

|
Chapter Overview
 Introduction
Introduction
In today’s connected world where information flows at speed of light, success of any organization depends on its ability to respond to fast changing environment. The capability of any organization depends on its ability to take fast decisions. A large organization typically has several different kinds of Information systems built around diverse functions, organizational levels, and business processes that can automatically exchange information. All these information systems have fragmentation of data in hundreds of separate systems, degrades organizational efficiency and business performance. For instance – sales personnel might not be able to tell at the time they place an order whether the ordered items are in inventory, and manufacturing cannot easily use sales data to plan for next production.
The solution to this problem is provided by Enterprise Information Systems, by collecting data from numerous crucial business processes like manufacturing and production, finance and accounting, sales and marketing, and human resources and storing the data in single central data repository. An Enterprise Information System (EIS) may be defined as any kind of information system which improves the functions of an enterprise business processes by integration.
An EIS provides a technology platform that enables organizations to integrate and coordinate their business processes on a robust foundation. An EIS provides a single system that is central to the organization that ensures information can be shared across all functional levels and management hierarchies. It may be used to amalgamate existing applications. An EIS can be used to increase business productivity and reduce service cycles, product development cycles and marketing life cycles. Other outcomes include higher operational efficiency and cost savings.
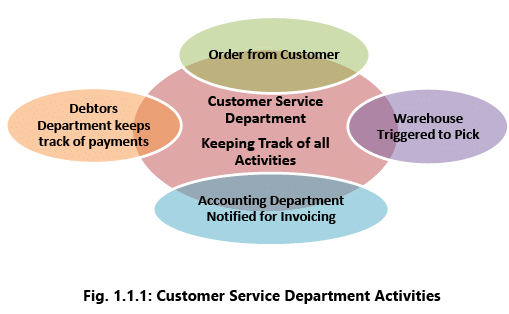
Example 1: When a customer places an order, the data flow automatically to other fractions of the company that are affected by them leading to the enhanced coordination between these different parts of the business which in turn lowers costs and increases customer satisfaction. Refer to the Fig. 1.1.1.
- The order transaction triggers the warehouse to pick the ordered products and schedule shipment.
- The warehouse informs the factory to replenish whatever has depleted.
- The accounting department is notified to send the customer an invoice.
- Debtors Department keeps track of payments.
- Customer service representatives track the progress of the order through every step to inform customers about the status of their orders.

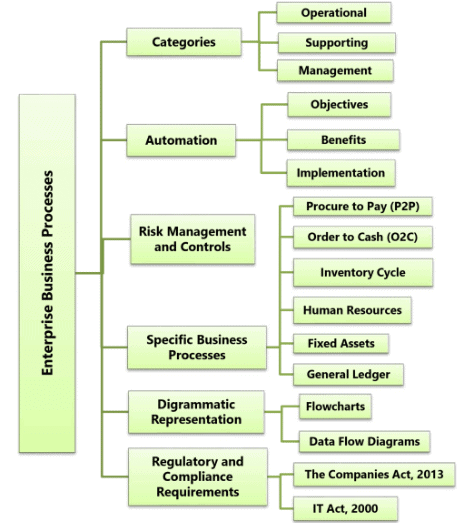
Enterprise Business Processes
A Business Process is an activity or set of activities that will accomplish a specific organizational goal. Business processes are designed as per vision and mission of top management. Business processes are reflection of entities management thought process. The success or failure of an organization is dependent on how meticulously business processes have been designed and implemented.
Business Process Management (BPM) helps an organization achieve 3E’s for business processes, namely Effectiveness, Efficiency and Economy. BPM is a systematic approach to improving these processes. Business Process Management is an all-round activity working on a 24x7 basis to ensure improvement in all parameters all the time. The key components of business process are outlined below.
The details of these processes are shown in the Fig. 1.2.1 below: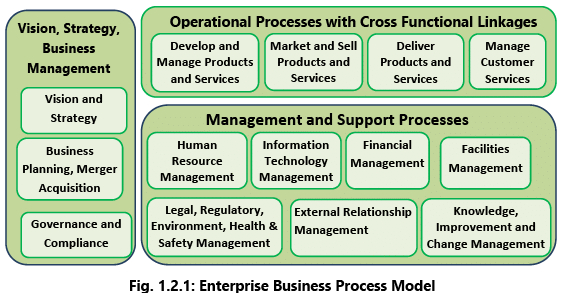 The key guiding factor for any business process shall be top management vision and mission. This vision and mission shall be achieved through implementing Operational, Support and Management services. These are referred to as categories of business process.
The key guiding factor for any business process shall be top management vision and mission. This vision and mission shall be achieved through implementing Operational, Support and Management services. These are referred to as categories of business process.
Categories of Business Processes
Depending on the organization, industry and nature of work; business processes are often broken up into different categories as shown in the Fig. 1.2.2.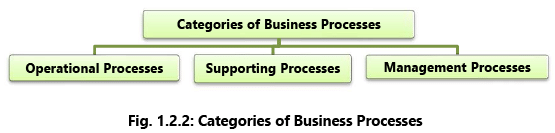
I. Operational Processes (or Primary Processes)
Operational or Primary Processes deal with the core business and value chain. These processes deliver value to the customer by helping to produce a product or service. Operational processes represent essential business activities that accomplish business objectives e.g. purchasing, manufacturing, and sales. Also, Order to Cash cycle (O2C) and Purchase to Pay (P2P) cycles are associated with revenue generation.
II. Supporting Processes (or Secondary Processes)
Supporting Processes back core processes and functions within an organization. Examples of supporting or management processes include Accounting, Human Resource (HR) Management and workplace safety. One key differentiator between operational and support processes is that support processes do not provide value to customers directly. However, it should be noted that hiring the right people for the right job has a direct impact on the efficiency of the enterprise.
Example 2: Human Resource Management
The main HR Process areas are grouped into logical functional areas - Recruitment and Staffing; Goal Setting; Training and Development; Compensation and Benefits; Performance Management; Career Development and Leadership Development.
III. Management Processes
Management Processes measure, monitor and control activities related to business procedures and systems. Examples of management processes include internal communications, governance, strategic planning, budgeting, and infrastructure or capacity management. Like supporting processes, management processes do not provide value directly to the customers. However, it has a direct impact on the efficiency of the enterprise.
Example 3: Process of Budgeting
Referring to the Fig. 1.2.3, in any enterprise, budgeting needs to be driven by the vision (what enterprise plans to accomplish) and the strategic plan (the steps to get there). Having a formal and structured budgeting process is the foundation for good business management, growth and development.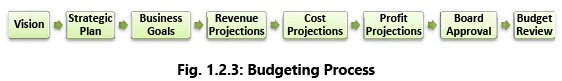 Table 1.2.1 summarises various categories of Business Processes through an example.
Table 1.2.1 summarises various categories of Business Processes through an example.
Table 1.2.1: Examples representing all categories of Business Processes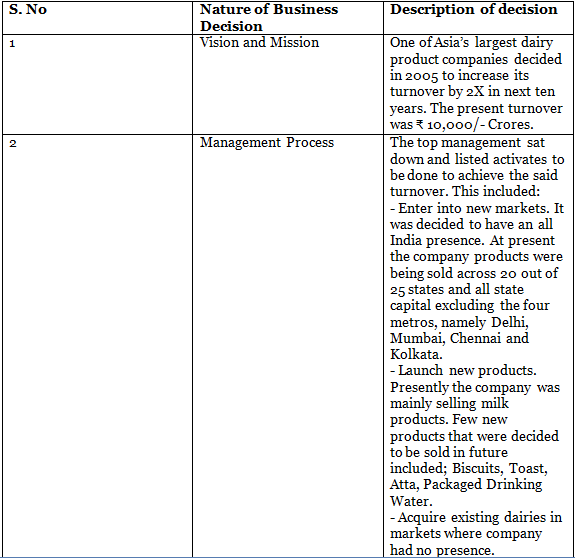
Automated Business Processes
Today technology innovations are increasing day by day, technology is becoming easily available, cost of accessing and using technology is going down, internet connectivity in terms of speed and geographical spread is increasing day by day. All these factors are having a profound impact on the business processes being used by entity.
In the days of manual accounting, most business processes were carried out manually. For example, a sales invoice would be raised manually and based on the shipment of goods the inventory would be manually updated for reducing the stock. Subsequently the accounting entries would be manually passed by debiting and crediting the respective accounts, through journal entries. Today most of the business processes have been automated to make enterprises more efficient and to handle the large volumes of transactions in today’s world. This is what has led to Business Process Automation (BPA). The manual example given above would be performed in an integrated computer system as follows:
- Raise invoice to customer in a computer system using relevant application software;
- The system automatically reduces the stock;
- The system instantly passes the necessary accounting entries by adding relevant transactions in relevant database tables:

Business Process Automation (BPA) is the technology-enabled automation of activities or services that accomplish a specific function and can be implemented for many different functions of company activities, including sales, management, operations, supply chain, human resources, information technology, etc. In other words, BPA is the tactic a business uses to automate processes to operate efficiently and effectively. It consists of integrating applications and using software applications throughout the organization. BPA is the tradition of analyzing, documenting, optimizing and then automating business processes.
Factors affecting BPA success
The success of any Business Process Automation shall only be achieved when BPA ensures the following:
- Confidentiality: To ensure that data is only available to persons who have right to see the same;
- Integrity: To ensure that no un-authorized amendments can be made in the data;
- Availability: To ensure that data is available when asked for; and
- Timeliness: To ensure that data is made available at the right time.
To ensure that all the above parameters are met, BPA needs to have appropriate internal controls put in place.
Benefits of Automating Business Process
A process is a repetitively used network of orderly linked activities using information and resources for transforming inputs to outputs. And the business process is the flow of information, customized by value-added tasks, that begins with the primary contact with a potential customer and continues through deliverance of a finished product. Well -developed business processes can generate a flawless link from initial customer interface through the supply chain. Automation of these processes maintains the accuracy of the information transferred and certifies the repeatability of the value-added tasks performed.
Table 1.3.1 elaborates on major benefits of automating Business Processes.
Quality and Consistency
- Ensures that every action is performed identically resulting in high quality, reliable results and stakeholders will consistently experience the same level of service.
Time Saving
- Automation reduces the number of tasks employees would otherwise need to do manually.
- It frees up time to work on items that add genuine value to the business, allowing innovation and increasing employees’ levels of motivation.
Visibility
- Automated processes are controlled, and they consistently operate accurately within the defined timeline. It gives visibility of the process status to the organization.
Improved Operational Efficiency
- Automation not only ensures systems run smoothly and efficiently, but also that errors are eliminated and that best practices are constantly leveraged.
Governance & Reliability
- The consistency of automated processes means stakeholders can rely on business processes to operate and offer reliable services to customers, maintaining a competitive advantage.
Reduced Turnaround Time
- Eliminate unnecessary tasks and realign process steps to optimize the flow of information throughout production, service, billing and collection. This adjustment of processes distils operational performance and reduces the turnaround time for both staff and external customers.
Reduced Costs
- Manual tasks, given that they are performed one-at-a-time and at a slower rate than an automated task, will cost more. Automation allows to accomplish more by utilizing fewer resources.
Which Business Processes should be automated?
Technology is the enabler of Business Process Automation (BPA). BPA offers many advantages to the business. But every business process is not a good fit for automation. Companies tend to automate those business processes that are time and resource-intensive operationally or those that are subject to human error. Following are the few examples of processes that are best suited to automation:
- Processes involving high-volume of tasks or repetitive tasks: Many business processes such as making purchase orders involve high-volume of repetitive tasks. Automating these processes results in cost and work effort reductions.
- Processes requiring multiple people to execute tasks: A business process which requires multiple people to execute tasks often results in waiting time that can lead to increase in costs. E.g. Help desk services. Automating these processes results in reduction of waiting time and in costs.
- Time-sensitive processes: Business process automation results in streamlined processes and faster turnaround times. The streamlined processes eliminate wasteful activities and focus on enhancing tasks that add value. Time-sensitive processes are best suited to automation. For example - online banking system, railway/aircraft operating and control systems etc.
- Processes involving need for compliance and audit trail: With business process automation, every detail of a particular process is recorded. These details can be used to demonstrate compliance during audits. For example- invoice issue to vendors.
- Processes having significant impact on other processes and systems: Some processes are cross-functional and have significant impact on other processes and systems. In cross functional processes, different departments within the same company work hand in hand to achieve a common goal, e.g., the marketing department may work with sales department. Automating these processes results in sharing information resources and improving the efficiency and effectiveness of business processes.
Challenges involved in Business Process Automation
Automated processes are susceptible to many challenges, some of them are discussed below:
- Automating Redundant Processes: Sometimes organizations start off an automation project by automating the processes they find suitable for automation without considering whether such processes are necessary and create value. In other cases, some business processes and tasks require high amount of tacit knowledge (that cannot be documented and transferred from one person to another) and therefore seek employees to use their personal judgment. These processes are generally not good candidates for automation as these processes are hard to encode and automate.
- Defining Complex Processes: BPA requires reengineering of some business processes that requires significant amount of time to be allocated and spent at this stage. This requires a detailed understanding of the underlying business processes to develop an automated process.
- Staff Resistance: In most cases, human factor issues are the main obstacle to the acceptance of automated processes. Staff may see process automation as a way of reducing their decision-making power. This is due to the reason that with automated processes, the management has a greater visibility of the process and can make decisions that used to be made by the staff earlier. Moreover, the staff may perceive automated processes as threat to their jobs.
- Implementation Cost: The implementation of automated processes may be an expensive proposition in terms of acquisition/development cost of automated systems and special skills required to operate and maintain these systems.
BPA Implementation
Business needs a reason to go for any new system. Benefits outlined in Table 1.3.1 are good indicators why any business shall go for automation for business process.
Of all good reasons discussed above, one factor needs additional consideration that is global competition. Today the connected world has opened huge opportunities as well as brought new threats to any business. The increased availability of choice to customers about products/services makes it very important for businesses to keep themselves updated to new technology and delivery mechanisms. All these factors are forcing businesses to adopt BPA.
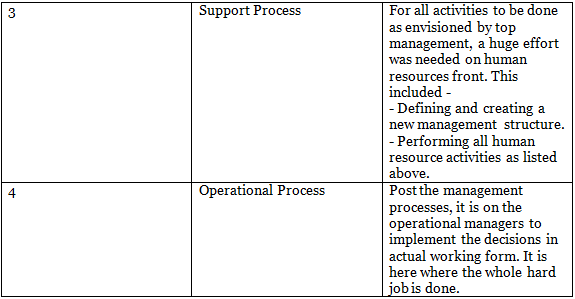
The steps to go about implementing Business Process Automation are depicted in Table 1.3.2. One important point to remember is that not all processes can be automated at a time. The best way to go about automation is to first understand the criticality of the business process to the enterprise. Let us discuss the key steps in detail.
(i) Step 1: Define why we plan to implement a BPA?
The primary purpose for which an enterprise implements automation may vary from enterprise to enterprise. A list of generic reasons for going for BPA may include any or combination of the following:
- Errors in manual processes leading to higher costs.
- Payment processes not streamlined, due to duplicate or late payments, missing early pay discounts, and losing revenue.
- Paying for goods and services not received.
- Poor debtor management leading to high invoice aging and poor cash flow.
- Not being able to find documents quickly during an audit or lawsuit or not being able to find all documents.
- Lengthy or incomplete new employee or new account on-boarding.
- Unable to recruit and train new employees, but where employees are urgently required.
- Lack of management understanding of business processes.
- Poor customer service.
(ii) Step 2: Understand the rules / regulation under which enterprise needs to comply with?
One of the most important steps in automating any business process is to understand the rules of engagement which include following the rules, adhering to regulations and following document retention requirements. This governance is established by a combination of internal corporate policies, external industry regulations and local, state, and central laws. Regardless of the source, it is important to be aware of their existence and how they affect the documents that drive the processes. It is important to understand that laws may require documents to be retained for specified number of years and in a specified format. Entity needs to ensure that any BPA adheres to the requirements of law.
(iii) Step 3: Document the process, we wish to automate
At this step, all the documents that are currently being used need to be documented. The following aspects need to be kept in mind while documenting the present process:
- What documents need to be captured?
- Where do they come from?
- What format are they in: Paper, FAX, email, PDF etc.?
- Who is involved in processing of the documents?
- What is the impact of regulations on processing of these documents?
- Can there be a better way to do the same job?
- How are exceptions in the process handled?
The benefit of the above process for user and entity being:
- It provides clarity on the process.
- It helps to determine the sources of inefficiency, bottlenecks, and problems.
- It allows designing the process to focus on the desired result with workflow automation.
An easy way to do this is to sketch the processes on a piece of paper, possibly in a flowchart format. Visio or even Word can be used to create flowcharts easily.
It is important to understand that no automation shall benefit the entity, if the process being automated is error-prone. Investment in hardware, workflow software and professional services, would get wasted if the processes being automated are not made error-free. Use of technology needs to be made to realize the goal of accurate, complete and timely processing of data so as to provide right information to the right people safely and securely at optimum cost.
Table 1.3.2: Steps involved in Implementing Business Process Automation
(iv) Step 4: Define the objectives/goals to be achieved by implementing BPA
Once the above steps have been completed, entity needs to determine the key objectives of the process improvement activities. When determining goals, remember that goals need to be SMART:
- Specific: Clearly defined,
- Measurable: Easily quantifiable in monetary terms,
- Attainable: Achievable through best efforts,
- Relevant: Entity must be in need of these, and
- Timely: Achieved within a given time frame.
Example 4: Consider for the following cases
Case 1: For vendor’s offering early payment discounts, entity needs to consider:
- How much could be saved if they were taken advantage of, and if the entity has got the cash flow to do so?
- Vendor priority can be created based on above calculations, for which gets paid sooner rather than later.
Case 2: To determine the average invoice aging per customer. Entity can decide to reduce the average from 75 days to 60 days. This alone can dramatically improve cash flow.
(v) Step 5: Engage the business process consultant
This is again a critical step to achieve BPA. To decide as to which company/ consultant to partner with, depends upon the following:
- Objectivity of consultant in understanding/evaluating entity situation.
- Does the consultant have the experience with entity business process?
- Is the consultant experienced in resolving critical business issues?
- Whether the consultant can recommend and implement a combination of hardware, software and services as appropriate to meeting enterprise BPA requirements?
- Does the consultant haves the required expertise to clearly articulate the business value of every aspect of the proposed solution?
(vi) Step 6: Calculate the RoI for project
The right stakeholders need to be engaged and involved to ensure that the benefits of BPA are clearly communicated, and implementation becomes successful. Hence, the required business process owners have to be convinced so as to justify the benefits of BPA and get approval from senior management. A lot of meticulous effort would be required to convince the senior management about need to implement the right solution for BPA. The right business case must be made covering technical and financial feasibility so as to justify and get approval for implementing the BPA. The best way to convince would be to generate a proposition that communicates to the stakeholders that BPA shall lead to not only cost savings for the enterprise but also improves efficiency and effectiveness of service offerings.
Some of the methods for justification of a BPA proposal may include:
- Cost Savings, being clearly computed and demonstrated.
- How BPA could lead to reduction in required manpower leading to no new recruits need to be hired and how existing employees can be re-deployed or used for further expansion.
- Savings in employee salary by not having to replace those due to attrition.
- The cost of space regained from paper, file cabinets, etc. is reduced.
- Eliminating fines to be paid by entity due to delays being avoided.
- Reducing the cost of audits and lawsuits.
- Taking advantage of early payment discounts and eliminating duplicate payments.
- Ensuring complete documentation for all new accounts.
- New revenue generation opportunities.
- Collecting accounts receivable faster and improving cash flow.
- Building business reputation by providing superior levels of customer service.
- Instant access to records (e.g. public information, student transcripts, medical records).
The above can be very well presented to justify the proposal and convince management to go ahead with the project of BPA implementation as required for the enterprise.
(vii) Step 7: Developing the BPA
Once the requirements have been document, RoI have been computed and top management approval to go ahead has been received, the consultant develops the requisite BPA. The developed BPA needs to meet the objectives for which the same is being developed.
(viii) Step 8: Testing the BPA
Once developed, it is important to test the new process to determine how well it works and identify where additional “exception processing” steps need to be included. The process of testing is an iterative process, the objective being to remove all problems during this phase.
Testing allows room for improvements prior to the official launch of the new process, increases user adoption and decreases resistance to change. Documenting the final version of the process will help to capture all of this hard work, thinking and experience which can be used to train new people.
Case studies on Business Processes Automation
Case 1: Automation of purchase order generation process in a manufacturing entity Various steps of automation are given as follows:
Step 1: Define why we plan to go for a BPA?
The entity has been facing the problem of non-availability of critical raw material items which is leading to production stoppages and delay in delivery. Delay in delivery has already cost company in terms of losing customer and sales.
Step 2: Understand the rules / regulation under which needs to comply with?
The item is not covered by regulation, regarding quantity to be ordered or stored. To keep cost at minimum, entity has calculated economic order quantity for which orders are placed.
Step 3: Document the process, we wish to automate.
The present process is manual where the orders are received by purchase department from stores department. Stores department generates the order based on manual stock register, based on item’s re-order levels. The levels were decided five years back and stores records are not updated timely.
Step 4: Define the objectives/goals to be achieved by implementing BPA.
The objective behind the present exercise is to ensure that there are no production losses due to non-availability of critical items of inventory. This shall automatically ensure timely delivery of goods to customer.
Step 5: Engage the business process consultant.
ABC Limited, a consultant of repute, has been engaged for the same. The consultant has prior experience and knowledge about entity’s business.
Step 6: Calculate the ROI for project.
The opportunity loss for the project comes to around ₹ 100/- lakhs per year. The cost of implementing the whole BPA shall be around ₹ 50/- lakhs. It is expected that the opportunity loss after BPA shall reduce to ₹ 50 lakhs in year one, ₹ 25/- lakhs in later years for the next five years.
Step 7: Developing the BPA.
Once the top management says ‘Yes’, the consultant develops the necessary BPA. The BPA is to generate purchase orders as soon as an item of inventory reaches its re-order level. To ensure accuracy, all data in the new system need to be checked and validated before being put the same into system:
- Item’s inventory was physically counted before uploading to new system.
- Item’s re-order levels were recalculated.
- All items issued for consumption were timely updated in system.
- All Purchase orders automatically generated are made available to Purchase manager at the end of day for authorizations.
Step 8: Testing the BPA.
Before making the process live, it should be thoroughly tested.
Case 2: Automation of Employee Attendance
Various steps of automation are given as follows:
Step 1: Define why we plan to go for a BPA?
The system of recording of attendance being followed is not generating confidence in employees about the accuracy. There have been complaints that salary pay-outs are not as per actual attendance. It has also created friction and differences between employees, as some may feel that other employees have been paid more for their salary has not been deducted for being absent.
Step 2: Understand the rules/regulation under which needs to comply with?
Numbers of regulations are applicable to employee attendance including Factories Act 1948, Payment of Wages Act 1936, State laws, etc. This is a compliance requirement and hence, any BPA needs to cater to these requirements.
Step 3: Document the process, we wish to automate.
The present system includes an attendance register and a register at the security gate. Employees are expected to put their signatures in attendance registers. The register at the gate is maintained by security staff, to mark when an employee has entered. There is always a dispute regarding the time when an employee has entered and what has been marked in the security register. The company policy specifies that an employee coming late by 30 minutes for two days in a month shall have a ½ day salary deduction. There is over-writing in attendance register, leading to heated arguments between human resource department staff and employees.
As the time taken to arrive at the correct attendance is large, there is a delay in preparation of salary. The same has already led to penal action against company by labor department of the state.
Step 4: Define the objectives/goals to be achieved implementing BPA.
The objective for implementing BPA is to have:
- Correct recording of attendance.
- Timely compilation of monthly attendance so that salary can be calculated and distributed on a timely basis.
- To ensure compliance with statutes.
Step 5: Engage the business process consultant.
XYZ Limited a consultant of repute has been engaged for the same. The consultant has prior experience and knowledge about entity’s business.
Step 6: Calculate the RoI for project.
The BPA may provide tangible benefits in the form of reduced penalties and intangible benefits which may include:
- Better employee motivation and morale,
- Reduced differences between employees,
- More focus on work rather than salary, and
- Improved productivity.
Step 7: Developing the BPA.
Implementing BPA includes would result in the following:
- All employees would be given electronic identity cards.
- The cards would contain details about employees.
- The attendance system would work in the following manner:
(i) Software with card reading machine would be installed at the entry gate.
(ii) Whenever an employee enters or leaves the company, he/she needs to put the card in front of machine.
(iii) The card reading machine would be linked to the software which would record the attendance of the employee.
(iv) At the end of month, the software would print attendance reports employee-wise. These reports would also point out how many days an employee has reported late in the month.
(v) Based on this report, monthly attendance is put in the system to generate the monthly salary.
Step 8: Testing the BPA.
Before making the process live, it should be thoroughly tested.
The above illustrations are of entities which have gone for business process automation. There are thousands of processes across the world for which entities have gone for BPA and reaped numerous benefits. These include:
- Tracking movement of goods,
- Sales order processing,
- Customer services departments,
- Inventory management,
- Employee Management System, and
- Asset tracking systems.
Risks and Its Management
Risk is any event that may result in a significant deviation from a planned objective resulting in an unwanted negative consequence. The planned objective could be any aspect of an enterprise’s strategic, financial, regulatory and operational processes, products or services. The degree of risk associated with an event is determined by the likelihood (uncertainty, probability) of the event occurring, the consequences (impact) if the event were to occur and it’s timing.
Sources of Risk
When an enterprise adopts automation to support its critical business processes, it exposes itself to several risks, such as downtime due to failure of technology. The most important step in risk management process is to identify the sources of risk, the areas from where risks can occur. This will give information about the possible threats, vulnerabilities and accordingly appropriate risk mitigation strategy can be adapted. Some of the common sources of risk are Commercial and Legal Relationships, Economic Circumstances, Human Behavior, Natural Events, Political Circumstances, Technology and Technical Issues, Management Activities and Controls, and Individual Activities.
Broadly, risk has the following characteristics:
- Potential loss that exists as the result of threat/vulnerability process. Threats have the potential to cause damage or loss. A risk is an expectation that a threat may succeed and the potential damage can occur.
- Uncertainty of loss expressed in terms of probability of such loss. The extent of loss includes not only the immediate direct financial loss but also the loss due to its impact in the long run. Loss in the long run includes losses such as loss of business, loss of reputation, etc.
- The probability / likelihood that a threat agent may mount a specific attack against a particular system. The assessment of both the likelihood/probability of occurrence and the consequences of risk is a high probability event.
Types of Risks
The risks can be broadly categorized as follows:
A. Business Risks: Business risk is a broad category which applies to any event or circumstances related to business goals. Businesses face all kinds of risks ranging from serious loss of profits to even bankruptcy and are discussed below:
- Strategic Risks: These are the risks that would prevent an organization from accomplishing its objectives (meeting its goals). Examples include risks related to strategy, political, economic relationship issues with suppliers and global market conditions; also, could include reputation risk, leadership risk, brand risk, and changing customer needs.
- Financial Risks: Financial risks are those risks that could result in a negative financial impact to the organization (waste or loss of assets). Examples include risks from volatility in foreign currencies, interest rates, and commodities; credit risk, liquidity risk, and market risk.
- Regulatory (Compliance) Risks: This includes risks that could expose the organization to fines and penalties from a regulatory agency due to noncompliance with laws and regulations. Examples include Violation of laws or regulations governing areas such as environmental, employee health and safety, lack of due diligence, protection of personal data in accordance with global data protection requirements and local tax or statutory laws. New and emerging regulations can have a wide-ranging impact on management’s strategic direction, business model and compliance system. It is, therefore, important to consider regulatory requirements while evaluating business risks.
- Operational Risks: Operational risks include those risks that could prevent the organization from operating in the most effective and efficient manner or be disruptive to other operations due to inefficiencies or breakdown in internal processes, people and systems. Examples include risk of loss resulting from inadequate or failed internal processes, fraud or any criminal activity by an employee, business continuity, channel effectiveness, customer satisfaction and product/service failure, efficiency, capacity, and change integration.
- Hazard Risks: Hazard risks include risks that are insurable, such as natural disasters; various insurable liabilities; impairment of physical assets; terrorism etc.
- Residual Risks: This includes any risk remaining even after the counter measures are analyzed and implemented. An organization’s management of risk should consider these two areas: Acceptance of residual risk and Selection of safeguards. Even when safeguards are applied, there is probably going to be some residual risk. The risk can be minimized, but it can seldom be eliminated. Residual risk must be kept at a minimal, acceptable level. As long as it is kept at an acceptable level, (i.e. the likelihood of the event occurring or the severity of the consequence is sufficiently reduced) the risk can be managed.
B. Technology Risks: Automated processes are technology driven. The dependence on technology in BPA for most of the key business processes has led to various challenges. All risks related to the technology equally apply to BPA. As technology is taking new forms and transforming as well, the business processes and standards adapted by enterprises should consider these new set of IT risks and challenges:
(i) Downtime due to technology failure: Information system facilities may become unavailable due to technical problems or equipment failure. A common example of this type failure is non-availability of system due to server failure.
(ii) Frequent changes or obsolescence of technology: Technology keeps on evolving and changing constantly and becomes obsolete very quickly. Hence, there is always a challenge that the investment in technology solutions unless properly planned may result in loss to the organization due to risk of obsolescence.
(iii) Multiplicity and complexity of systems: The technology architecture used for services could include multiple digital platforms and is quite complex. Hence, this requires the personnel to have knowledge about requisite technology skills or the management of the technology could be outsourced to a company having the relevant skill set.
(iv) Different types of controls for different types of technologies/systems: Deployment of technology often gives rise to new types of risks. These risks need to be mitigated by relevant controls as applicable to the technology/information systems deployed.
(v) Proper alignment with business objectives and legal/regulatory requirements: Organizations must ensure that the systems implemented cater to all the business objectives and needs, in addition to the legal/regulatory requirements envisaged. (vi) Dependence on vendors due to outsourcing of IT services: In a systems environment, the organization requires staff with specialized domain skills to manage IT deployed. Hence, these services could be outsourced to vendors and there is heavy dependency on vendors and gives rise to vendor risks which should be managed by proper contracts, controls and monitoring.
(vii) Vendor related concentration risks: There may not be one but multiple vendors providing different services. For example, network, hardware, system software and application software services may be provided by different vendors or these services may be provided by a single vendor. Both these situations result in higher risks due to heavy dependence on vendors.
(viii) Segregation of Duties (SoD): Organizations may have a highly-defined organization structure with clearly defined roles, authority and responsibility. The Segregation of Duties as per organization structure should be clearly mapped. This is a high-risk area since any SoD conflicts can be a potential vulnerability for fraudulent activities. For example, if a single employee can initiate, authorize and disburse a loan, the possibility of misuse cannot be ignored.
(ix) External threats leading to cyber frauds/ crime: The system environment provides access to customers anytime, anywhere using internet. Hence, information system which was earlier accessible only within and to the employees is now exposed as it is open to be accessed by anyone from anywhere. Making the information available is business imperative but this is also fraught with risks of increased threats from hackers and others who could access the software to commit frauds/crime.
(x) Higher impact due to intentional or unintentional acts of internal employees: Employees in a technology environment are the weakest link in an enterprise. Employees are expected to be trusted individuals that are granted extended privileges, which can easily be abused.
(xi) New social engineering techniques employed to acquire confidential credentials: Fraudsters use new social engineering techniques such as socializing with employees and extracting information which is used to commit frauds. For example: extracting information about passwords from staff acting as genuine customer and using it to commit frauds.
(xii) Need for governance processes to adequately manage technology and information security: Controls in system should be implemented from macro and business perspective and not just from function and technology perspective. With BPA, technology becomes the key enabler for the organization and is implemented across the organization. The senior management should be involved in directing how technology is deployed in and approve appropriate policies. This requires governance process to implement security as required.
(xiii) Need to ensure continuity of business processes in the event of major exigencies: The high dependence on technology makes it imperative to ensure resilience to ensure that failure does not impact the organization’s services. Hence, a documented business continuity plan with adequate technology and information systems should be planned, implemented and monitored.
C. Data related risks: The primary concern of any organization should be its data, because it is often a unique resource. All data and applications are susceptible to disruption, damage and theft.
Risk Management and Related Terms
Various terminologies relating to risk management are given as follows:
Risk Management: Risk Management is the process of assessing risk, taking steps to reduce risk to an acceptable level and maintaining that level of risk. Risk management involves identifying, measuring, and minimizing uncertain events affecting resources.
Asset: Asset can be defined as something of value to the organization e.g., information in electronic or physical form, software systems, employees. Irrespective the nature of the assets themselves, they all have one or more of the following characteristics:
- They are recognized to be of value to the organization.
- They are not easily replaceable without cost, skill, time, resources or a combination.
- They form a part of the organization’s corporate identity, without which, the organization may be threatened.
- Their data classification would normally be Proprietary, Highly confidential or even Top Secret.
It is the purpose of Information Security Personnel to identify the threats against the risks and the associated potential damage to, and the safeguarding of Information Assets.
Vulnerability: Vulnerability is the weakness in the system safeguards that exposes the system to threats. It may be a weakness in information system/s, cryptographic system (security systems), or other components (e.g. system security procedures, hardware design, internal controls) that could be exploited by a threat. Vulnerabilities potentially “allow” a threat to harm or exploit the system. For example - vulnerability could be a poor access control method allowing dishonest employees (the threat) to exploit the system to adjust their own records. Some examples of vulnerabilities are as follows:
- Leaving the front door unlocked makes the house vulnerable to unwanted visitors.
- Short passwords (less than 6 characters) make the automated information system vulnerable to password cracking or guessing routines.
Missing safeguards often determine the level of vulnerability. Determining vulnerabilities involves a security evaluation of the system including inspection of safeguards, testing, and penetration analysis.
Normally, vulnerability is a state in a computing system (or set of systems), which must have at least one condition, out of the following:
- ‘Allows an attacker to execute commands as another user’ or
- ‘Allows an attacker to access data that is contrary to the specified access restrictions for that data’ or
- ‘Allows an attacker to pose as another entity’ or
- ‘Allows an attacker to conduct a denial of service’.
Threat: Any entity, circumstance, or event with the potential to harm the software system or component through its unauthorized access, destruction, modification, and/or denial of service is called a Threat. It is an action, event or condition where there is a compromise in the system, its quality and ability to inflict harm to the organization. Threat has capability to attack on a system with intent to harm. It is often to start threat modeling with a list of known threats and vulnerabilities found in similar systems. Every system has a data, which is considered as a fuel to drive a system, data is nothing but assets. Assets and threats are closely correlated. A threat cannot exist without a target asset. Threats are typically prevented by applying some sort of protection to assets.
Exposure: An exposure is the extent of loss the enterprise has to face when a risk materializes. It is not just the immediate impact, but the real harm that occurs in the long run. For example: loss of business, failure to perform the system’s mission, loss of reputation, violation of privacy and loss of resources etc.
Likelihood: Likelihood of the threat occurring is the estimation of the probability that the threat will succeed in achieving an undesirable event. The presence, tenacity and strengths of threats, as well as the effectiveness of safeguards must be considered while assessing the likelihood of the threat occurring.
Attack: An attack is an attempt to gain unauthorized access to the system’s services or to compromise the system’s dependability. In software terms, an attack is a malicious intentional fault, usually an external fault that has the intent of exploiting vulnerability in the targeted software or system.
Basically, it is a set of actions designed to compromise CIA (Confidentiality, Integrity or Availability) or any other desired feature of an information system. Simply, it is the act of trying to defeat Information Systems (IS) safeguards. The type of attack and its degree of success determines the consequence of the attack.
Example 5: Fig. 1.4.1 depicts the risk and its related terms.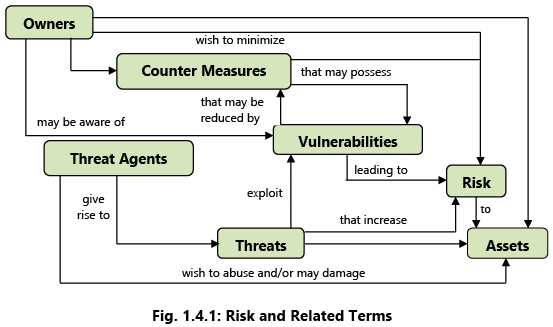 Counter Measure: An action, device, procedure, technique or other measure that reduces the vulnerability of a component or system is referred as Counter Measure. For example, well known threat ‘spoofing the user identity’, has two countermeasures:
Counter Measure: An action, device, procedure, technique or other measure that reduces the vulnerability of a component or system is referred as Counter Measure. For example, well known threat ‘spoofing the user identity’, has two countermeasures:
- Strong authentication protocols to validate users; and
- Passwords should not be stored in configuration files instead some secure mechanism should be used.
Similarly, for other vulnerabilities, different countermeasures may be used.
The relationship and different activities among these terms may be understood by Fig. 1.4.1. To conclude, Risk can be defined as the potential harm caused if a threat exploits a particular vulnerability to cause damage to an asset, and Risk Analysis is defined as the process of identifying security risks and determining their magnitude and impact on an organization.
Risk Assessment includes the following:
- Identification of threats and vulnerabilities in the system;
- Potential impact or magnitude of harm that a loss of CIA, would have on enterprise operations or enterprise assets, should an identified vulnerability be exploited by a threat; and
New technology provides the potential for dramatically enhanced business performance, improved and demonstrated information risk reduction and security measures. Technology can also add real value to the organization by contributing to interactions with the trading partners, closer customer relations, improved competitive advantage and protected reputation.
Risk Management Strategies
Effective risk management begins with a clear understanding of an enterprise’s risk appetite and identifying high-level risk exposures. The unacceptable high levels of risks can be controlled by designing and implementing adequate proactive controls. But it is not always appropriate to counter risks by implementing controls because controls involve cost. After defining risk appetite and identified risk exposure, strategies for managing risk can be set and responsibilities clarified. Based on the type of risk, project and its significance to the business; Board and Senior Management may choose to take up any of the following risk management strategy in isolation or combination as required:
- Tolerate/Accept the risk: One of the primary functions of management is managing risk. Some risks may be considered minor because their impact and probability of occurrence is low. In this case, consciously accepting the risk as a cost of doing business is appropriate. The risks should be reviewed periodically to ensure that their impact remains low.
- Terminate/Eliminate the risk: It is possible for a risk to be associated with the use of a technology, supplier, or vendor. The risk can be eliminated by replacing the technology with more robust products and by seeking more capable suppliers and vendors.
- Transfer/Share the risk: Risk mitigation approaches can be shared with trading partners and suppliers. A good example is outsourcing infrastructure management. In such a case, the supplier mitigates the risks associated with managing the IT infrastructure by being more capable and having access to more highly skilled staff than the primary organization. Risk also may be mitigated by transferring the cost of realized risk to an insurance provider.
- Treat/Mitigate the risk: Where other options have been eliminated, suitable controls must be devised and implemented to prevent the risk from manifesting itself or to minimize its effects.
- Turn back: Where the probability or impact of the risk is very low, then management may decide to ignore the risk.
FAQs on Automated Business Processes: Notes (Part - 1) - Financial Management & Strategic Management for CA Intermediate
| 1. What are enterprise business processes? |  |
| 2. How can automated business processes benefit an organization? |  |
| 3. What are the risks associated with automated business processes? |  |
| 4. How can organizations manage the risks associated with automated business processes? |  |
| 5. What are some examples of automated business processes? |  |

 Introduction
Introduction