Networks Chapter Notes | Computer Science for Grade 12 PDF Download
Structure of a Network
Revision Notes
Types of Networks
(a) LAN (Local Area Network) : A network spanning inside a small area generally a building is termed as Local Area Network. It usually covers an organization’s office, schools, colleges or universities. It may consist up to few hundred systems. In LAN, sharing of resources between end users becomes easy. It operates on private IP address. It uses Ethernet as Token – Ring technology. LAN can be wired, wireless or in both forms at once.
(b) WAN (Wide Area Network) : It covers a wide area that may span across many cities and even a whole country. Telecommunication networks are example of WAN. WAN uses expensive equipment as they are equipped with high speed backbone.
New Technologies
Internet : It is network of networks inter connected to each other like web. It connects all WANs and may have connection to LANs. It uses TCP/IP protocol suites and IP as its addressing protocol. Internet enables, its users to share and access information world wide using WWW, FTP and other services. Like e-mail, fund transfer etc.
(a) Cloud : Refers to a shared pool of configurable computing resources like networks, servers, network storage, application and services that can be provisioned. Some basic types of cloud delivery models are available as given below.,
(i) Public Cloud : Such clouds offer their services to anyone in general public and maintain large data centres and computing hardware.
(ii) Private cloud : Such clouds are set up by an organization exclusively for their internal use, sometime because of security reasons and some times because of various regulations. For this, organization may set up cloud at their own data centres or use a hosted private cloud services. In a hosted private cloud service, the vendor sets aside certain computing resources that can be used by only one customer.
(iii) Hybrid cloud : The infra-structure designed with the combination of public, private or community is called hybrid cloud.
(b) IoT (Internet of Things) : It is a network of things (computing devices, mechanical devices and digital machines, any object of our daily life, an animal and a person). All these are provided with UIDs (Unique Identifiers) and the ability to transfer data over a network without requiring human to – human or human – to – computer interaction.
(c) Wired Networks : It refers to a setup where physical cables are used to transfer data between devices and computer systems. e.g. Ethernet, Arpanet, Internet, Extranet.
(d) Wireless Networks : It refers to the use of infrared or radio frequency signals to share information and resources between devices. e.g. bluetooth, wifi, wi Max, VSAT etc.
(e) Client, Server Model : It is a concept where the computer tasks are distributed or divided amongst the clients, who request for a service and a server, who fulfills the requests. Both client and server use different hardware. e.g. Airlines and Railway reservation systems.
Network Devices
Network devices are used to connect various electronic devices and computer hardwares to a network so that data can be transmitted in a fast, secured and correct way from different networks.
(a) Router : It transmits data between two same protocol supporting LANs but only after strengthening the signal. It connects at least two LANs and an ISP(Internet Service Provider). It is a network layer hardware device and receives data in the form of packets.
(b) Modem : A MODEM (MOdulator DEModulator) is an electronic device that enables a computer to transmit data over telephone lines. There are two types of modems namely, internal modem and external modem.
(c) RJ45 Connector : The RJ-45 (Registered Jack) connectors are the plug-in devices used in the networking and telecommunication applications. They are used primarily for connecting LANs, particularly Ethernet.
(d) Ethernet Card : It is a hardware device that helps in connection of nodes within a network. Ethernet cards are sometimes known as Network Interface Cards (NICs).
(e) Hub : It is a hardware device used to connect several computers together. Hubs can be either active or passive. Hubs usually can support 8, 12 or 24 RJ45 parts.
(f) Switch : A switch (switching hub) is a network device which is used to interconnect computers or devices in a network. It filters and forwards data packets across a network. The main difference between a hub and a switch is that hub replicates what it received on one port to all the other ports while switch replicates what it received on one port to specified port.
(g) Gateway : A gateway is a device that connects dissimilar networks.
(h) Repeater : A repeater is a network device that amplifies and restores signals for long distance transmission.
(i) Access Point : Access Point is a station that receives and transmits data in the network.
Network Stack
It is a layered set of protocols which work together to provide a set of network functions. It is also known as Protocol stack.
(a) Amplitude modulation : The amplitude of the carrier wave is varied in proportion to that of the message signal being transmitted. It is used to transmit information over a radio carrier wave.
(b) Frequency modulation : In frequency modulation, frequency of the radio carrier is changed in line with the amplitude of the incoming signal.
(c) Collision in wireless networks : In wireless networking, hidden node problem or hidden terminal problem occurs when a node is visible to a wireless access point (AP) but not to other nodes communicating with that AP.
RTS/CTS handshaking : Collision can not be detected in hidden node problems thus CSMA/CD (Carrier Sense Multiple Access with Collision Detection) does not work here. Hence RTS/CTS handshaking (IEEE 802.11 RTS/CTS) is implemented in addition to CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) scheme.
MA/CA (Multiple Access with Collision Avoidance). In open node problem, this algorithm is implemented where in the sender and receiver exchange frames with each other before transmitting data. Thus all nearby nodes are informed about the transmission that is about to begin.
(d) Error Checking : Data – link layer uses some error control mechanism to ensure that frames are transmitted with certain level of accuracy.
Types of Errors :
(i) Single bit Error : In a frame, only one bit is corrupt.
(ii) Multiple bit Error : More than one bits in a frame is corrupted.
(iii) Burst Error : More than 1 consecutive bits is corrupted.
Error Detection : Few extra bits are sent with actual data to confirm that bits received at other end are same as they were sent.
(i) Parity Check : One extra bit is sent along with original bits to make numbers of 1's even in even parity, or odd in case of odd parity.
(ii) CRC (Cyclic Redundancy Check) : The sender transmits data bits as codewords. Codewords is generated by adding remainder of binary division of actual data bits to the actual data bits.
(iii) LRC (Longitudinal Redundancy Check) : It is a bit by bit parity computation, as we calculate the parity of each column individually.
(iv) Check Sum : They are similar to parity bits except, the number of bits in the sum is larger than parity and result is always constrained to be zero.
Error Correction : It is the ability to restore data in which errors have been found to its original state.
(i) Backward Error Correction : The receiver requests the retransmission of the data on detecting an error.
(ii) Forward Error Correction : In case of some kinds of errors, receiver executes error correcting code to auto – recover the corrupted data.
(e) MAC address : It is a unique identification for an Ethernet or network adapter over a network. It occurs in the Media Access Control Protocol sub – layer in OSI model. It is used in most IEEE 802 networks. It is also known as physical address.
(f) MAC address notion : These are assigned by manufacturer of every NIC. They are permanent and created according to IEEE specifications
Each MAC address consists of a 12-digit hexadecimal notation. It includes manufacturer’s organizationally Unique Identification followed by six digits of serialized or random unique identifier.
The three notions given by IEEE are as below
(i) Addresses are printed as six groups of two hexadecimal digits separated by hyphens in transmission order. Used for EUI 48 and EUI 64 e.g. 10-32-54-76-98-BA.
(ii) Addresses are printed as six groups of two hexadecimal digits separated by colon (:). e.g. 10:32:54:76:98:BA
(iii) Addresses are printed as three groups of four hexadecimal digits separated by dots(.) eg. 1032.5476.98BA.
Standard notation or canonical format for MAC addresses is written in transmission order with the least significant bit of each byte transmitted first.
Bit reversed notation or non-canonical format is written in standard transmission order but in mostsignificant bit first order.
(g) Routing Concepts:
(i) Routing is the process to provide path information to reach the destination so that routed protocol can carry the data packet to destination. Router fulfills this requirement.
(ii) Routing Table : Routers maintain a routing table and by default all routers has capability to keep their directly connected network information in their routing table – New or not directly connected Route information in routing table can be injected in two ways
(a) Static (b) Dynamic
IP Addresses :
IP (Internet Protocol) : The Network Layer Protocol in the TCP/IP stack offering a connectionless internetwork service. IP provides features for addressing type of service.
IP is responsible for moving packet of data from node to node. IP forwards each packet based on a four byte destination address (the IP number). The Internet authorities assign ranges of numbers to different organizations. The organizations assign groups of their numbers to departments. IP operates on gateway machines that moves data from department to organization, then to region and then around the world.
IP addresses are a scheme for computers to communicate over a network. It currently has two versions IPv4 and IPv6
(i) IPv4 is the fourth revision of IP. It uses a 32 bit address scheme.
(ii) IPv6 is upgrade to IPv4 also known as IPng (Internet Protocol next generation). It uses a 128 bit address scheme. It is written in hexadecimal and separated by colons.
(a) DNS or Domain Name System is a system to translate domain names into IP addresses.
Domain names are used to identify one or more IP addresses. Every domain name has a suffix that indicates which top level domain (TLD) it belongs to. e.g.
gov – government organizations
edu – educational institutions etc.
(b) Web URL’s - Uniform Resource Locator is the address as well as a way of finding a resource on the World Wide Web. URL consists of three parts :
- Network protocol
- Host name or address
- File or resource location

Network Protocol
- A protocol means the rules and regulation that are applicable for controlling, monitoring and regulating a network. It defines the standardised format for data packets, techniques for detecting and correcting errors and so on.
- A protocol is a formal description of message formats and the rules that two or more machines must follow to exchange those messages. e.g., using library books.
Types of protocols are following :
(a) HTTP → To browse web pages of the web site.
(b) FTP → To send and receive text files and documents.
(c) TCP/IP → To send UDP packet over wired network.
(d) SMTP → To send receive e-mail over internet.
(e) POP3 → To read and write e-mails contents.
(a) Hypertext Transfer Protocol (HTTP) is a communication protocol for the transfer of information on the internet and the World Wide Web. HTTP is a request/response standard between a client and a server. A client is the end-user while, the server is the web site.
(b) FTP (File Transfer Protocol) is the simplest and most secured way to exchange files over the Internet. The objectives of FTP are :
- To promote sharing of Files (computer programs and/or data)
- To encourage indirect or implicit use of remote computers.
- To shield a user from variations in file storage systems among different hosts.
- To transfer data reliably and efficiently.
(c) TCP/IP (Transmission Control Protocol/Internet Protocol)
TCP is responsible for verifying the correct delivery of data from client to server. Data can’t be lost in the intermediate network. TCP adds support to detect errors or lost data and to trigger retransmission until the data is correctly and completely received.
(d) SMTP : (Simple Mail Transfer Protocol) is a standard protocol for email services on TCP/IP network that provides ability to send and receive email.
(e) POP3 : (Post Office Protocol version 3) is a message access protocol which allows client to fetch an e-mail from remote mail server.
IP is responsible for moving packet of data from source to destination. It handles the address part of each packet so that is reaches to the right destination.
(a) 1G (First Generation-1G) networks (NMT, C-Nets, AMPS, TACS) are considered to be the first analog cellular systems, which started in decade of 1980s. There were radio telephone systems even before that. 1G networks were conceived and designed purely for voice calls with almost no consideration of data services (with the possible exception of built-in modems in some headsets). The “G” in wireless networks refers to the “generation” of the underlying wireless network technology.
(b) 2G (Second Generation-2G) networks (GSM, CDMAOne, D-AMPS) are the first digital cellular systems launched in the decade of 1990, offering improved sound quality, better security and higher total capacity. GSM supports circuit-switched data (CSD), allowing users to place dial-up data calls digitally, so that the network’s switching station receives actual ones and zeroes rather than the screech of an analog modem.
(c) 3G (Third Generation-3G) networks (UMTS FDD and TDD, CDMA2000 1x EVDO, CDMA2000 3x, TDSCDMA, Arib WCDMA, EDGE, IMT-2000 DECT) are newer cellular networks that have data rates of 384kbit/s and more. The UN’s International Telecommunications Union IMT-2000 standard requires stationary speeds of 2Mbps and mobile speeds of 384kbps for a “true” 3G.
(d) 4G (Fourth Generation-4G) technology refers to the fourth generation of mobile phone communication standards. LTE and WiMAX are marketed as parts of this generation, even though they fall short of the actual standard.
(e) Wi – Fi (Wireless Fidelity): This technology enables us to connect to the high – speed Internet or other wireless networks. It is a trademark phrase that means IEEE 802.11x
Data Communication Terminologies
- Concept of Channel : A data channel is the medium used to carry information or data from one point to another.
- Baud : It is the unit to measure the data transmission speed. It is equivalent to bps (bits per second).
- Bandwidth : The maximum volume of data that can be transferred over any communication channel at a given point of time is known as the bandwidth. In analog systems, it is measured in hertz (Hz) and in digital systems, it is measured in bits per second (bps).
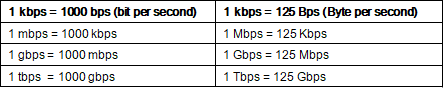
- Data Transfer Rate : The amount of data transferred per second by the communication channel from one point to another is known as the data transfer rate. It is measured in bits per second (bps) and bytes per second (Bps).
- Congestion : Traffic in excess of network capacity
- FRR (Fast Retransmit and Recovery) is a congestion cantrol algorithm that make it possible to quickly recover last data packets.
Basic Network tools
Revision Notes
- Traceroute/Tracert : Determines the path taken to a destination by sending Internet Control Message Protocol (ICMP) echo request messages to the destination with incrementally increasing Time to Live (TTL) field values.
Syntax :
tracert [-d] [-h maximum_hops] [-j host-list] [-w timeout] target_name Ping : It is a TCP/IP command used to trouble shoot connectivity, reachability and name resolution. Ping calculate the round trip time of the data packets route from its source to the destination and back and determines whether any packet were lost during the trip.
syntax: ping [hostname]ipconfig(Internet Protocol configuration) : It displays all current TCP/IP network configuration values and refreshes DHCP and DNS settings.
syntax :
ipconfig [/all][/renew [Adapter]][/release [adapter]]
[/Plushdns][/displaydns][/registerdns]
[/showclassid [Adapter]][/setclassid Adapter [class ID]]nslookup (Name Server Lookup) : It is a UNIX shell command to query Internet domain name servers. In addition to looking up server information, nslookup can be used to test IP connections.
whois : This is used to find out who owns the domain. It can also be used to find out whether a domain name is available or has already been taken.
Speed test : Network speed test measures your network delay, download speed and upload speed.
Application layer
Revision Notes
- HTTP – Hyper Text Transfer Protocol (HTTP) is an application layer protocol for hypermedia systems. It is World Wide Web’s data communication foundation. It has following features,
(a) HTTP is connectionless i.e. the client and server know each other only during the current request. Further requests are made on new connection.
(b) HTTP is media independent i.e. any type of data can be sent by HTTP as long as both the client and the server know how to handle the data contents.
(c) HTTP is stateless i.e. neither client nor the server can retain the information between different requests across the web pages. - Email : Electronic mail (E-mail) most commonly referred to as E-mail, is a method of exchanging digital message from sender to one or more recipient. E-mail system consists of three parts.
(a) Mailer or mail application or mail client is an application that helps us to massage, read and compare e-mail.
(b) Mail Server receives, stores and delivers the e-mail.
(c) Mailbox is a folder that contains emails and information about them.
Working – It works on client server model. It sends, compares a message using mailer and clicks send. The email text and attachments are uploaded to the SMTP to receiver’s mail server. The POP server of the receiver check for and received mail. Received mail is forwarded and stored in receiver’s device. - Secure Communication : It refers to communication between two parties without any third party knowing about it.
- Encryption : It is the process of translating readable data into something that appears random and has no meaning unless you know how to decrypt.
- Digital certificate are issued to individuals on making payment. These are used by organizatios to verify the identities of people and organization.
- SSL or Secured Socket Layer is the way a website creates a secure connection with a web browser.
- SSL Certificate : The web server must have an SSL certificate to create an SSL connection.
- HTTPS : Hypertext Transfer Protocol Secure combines HTTP with SSL to ensure security.
- Network applications are the applications that either run on a network or use data stored on a network or both. These use client server architecture.
- Remote Desktop allows a user to access an operating computer’s desktop using internet or another network.
- Remote Login (Login is a UNIX command) that allows an authorized user to login other UNIX machines on a network.
- FTP transfers files from one computer to another. It involves two processes.
- Downloading : To obtain files from a server to a client’s workstation.
- Downloading : To obtain files from a server to a client’s workstation.
- TELNET allows workstation to access the server for an application program. The workstation then acts as a dumb terminal.
- SSH (Secure Socket Shell) is a cryptographic protocol and interface. It enables two remotely connected computers to perform network communication over unsecured network.
- POP : It is a protocol that is used to retrieve e-mail from a mail server.
- IMAP : Internet Message Access Protocol is a protocol used for accessing and storing mail on a mail server.
- Difference between POP and IMAP is that POP works with only one client connected to a mail server while IMAP can work for multiple clients of the same mail box.
- VoIP : Voice over Internet Protocol is a category of hardware and software using which telephone calls can be done. Here internet is the transmission medium and voice data is sent in packets using IP.
- NFC : Near Field Communication is a communication protocol that enables two devices to communicate wirelessly when kept in near proximity line about 4 cm near to each other. This does not require Internet.
- SCP : Secure Copy Protocol
Know the Terms
- ARPANET : Advanced Research Projects Agency Network. Landmark packet-switching network established in 1969. ARPANET was developed in the 1970s by BBN and founded by ARPA and later DARPA. It eventually evolved into the Internet. The term ARPANET was officially retired in 1990.
- Backbone : Referring to the internet, a central network that provides a pathway for other networks to communicate.
- Bridge : A Data Link Layer device that limits traffic between two network segments by filtering the data between them based on hardware addresses.
- Broadband : A transmission system capable of carrying many channels of communication simultaneously by modulating them on one of several carrier frequencies.
- Bus Topology : Linear LAN architecture in which transmissions from network stations propagate the length of the medium and are received by all other stations.
- Congestion : Traffic in excess of network capacity may cause traffic jamming.
- Data Link : The physical connection between two devices such as Ethernet, Local Talk or Token Ring that is capable of carrying information in the service or networking protocols such as AppleTalk, TCP/IP orXNS.
- Destination Address : Address of a network device that is receiving data.
- Dot Address : Refers to the common notation for IP addresses in the form of <n.n.n.n> where each number n represents, in decimal, 1 byte of the 4-byte IP address. Also called dotted notation or four-part dotted notation.
- Optical Fibre Cable : Physical medium capable of conducting modulated light transmission. Compared with other transmission optical fibre cable is more expensive, but is not susceptible to electromagnetic interference and is capable of higher data rates called as optical fibre.
- Firewall : A piece of security software or hardware designed to protect web servers. They are typically used to protect sites from hacker attacks/unauthorized accesses.
- Gbps : Gigabits per second. · GHz : Gigahertz.
- KBPS : A unit of measure used to describe the rate of data transmission equal to 1000 bits per second.
- MBPS : A unit of measure used to describe the rate of data transmission equal to one millions bits per second.
- Packet : A discrete chunk of communication in a predefined format.
- Server : A device that is shared by several users of a network.
- Session : An on-going relationship between two computing devices involving the allocation of resources and sustained data flow.
- Hybrid Cloud : The cloud service that utilizes both private and public cloud.
- SaaS : Software as a Service is a software development method that provides access to software and its function remotely as a Web-based service.
- PaaS : Platform as a Service is computing platform being delivered as a service.
- IaaS (Infrastructure as a Service) : Computer infrastructure, such as servers, storage and network delivered as a service.
- OSI (Open System Interconnection ) model service is a standard template describing a network protocol stack.
- RTS : Request to send.
- CTS : Clear to send.
- DHCP : Dynamic Host Configuration Protocol.
- DNS : Domain Name System.
- Node : Any system or device connected to a network.
|
1 videos|23 docs|18 tests
|
















