Previous Year Questions: Data Link Layer | Computer Networks - Computer Science Engineering (CSE) PDF Download
Q1: Consider an Ethernet segment with a transmission speed of 1 0 8 bits/sec and a maximum segment length of 500 meters. If the speed of propagation of the signal in the medium is 2 × 1 0 8 meters/sec, then the minimum frame size (in bits) required for collision detection is _________ (2024 SET 2)
(a) 400
(b) 450
(c) 500
(d) 550
Ans: (c)
Sol: Data Transfer Rate: 108 bit/sec.
Distance = 500 m
Signal Speed = 2 * 108 m/sec.
Frame Size = n bits.
Transmission Time = Frame Length / Data Transfer Rate
= n bits / 108 bits/sec
= n/108 sec.
Propagation Time = 500 m/ 2 * 108 m/sec
= 500/2 * 108 sec.
For collision detection,
Transmission time >= 2 * Propagation Time
n/108 >= 2 * (500/2* 108)
n >= 500.
Hence, the correct answer is 500 Bits.
Q2: Consider a network path P − Q − R between nodes P and R via router Q . Node P P sends a file of size 1 0 6 bytes to R via this path by splitting the file into chunks of 1 0 3 bytes each. Node P P sends these chunks one after the other without any wait time between the successive chunk transmissions. Assume that the size of extra headers added to these chunks is negligible, and that the chunk size is less than the MTU. (2024 SET 1)
Each of the links P − Q and Q − R has a bandwidth of 1 0 6 b i t s / s e c , and negligible propagation latency. Router Q immediately transmits every packet it receives from P P to R R, with negligible processing and queueing delays. Router Q can simultaneously receive on link P − Q and transmit on link Q − R link.
Assume P starts transmitting the chunks at time t = 0. Which one of the following options gives the time (in seconds, rounded off to 3 decimal places) at which R receives all the chunks of the file?
(a) 8
(b) 8.008
(c) 15.992
(d) 16
Ans: (b)
Sol: The network has three nodes P,Q,R connected as P-Q-R. P sends 1000 packets each of size 1000 bytes.
The transmission time of one packet between two nodes is packet size / Bandwidth.
we are given bandwitdth is 1 mega bits per second.
hence we have 8000 / 106 = 8 milliseconds.
The total transmission time = ( Number of packets + n ) * Tt | here n is the number of nodes on the path in between source and destination.
Hence total time taken = (1000+1)* 8ms = 8008ms = 8.008s
Q3: Suppose two hosts are connected by a point-to-point link and they are configured to use Stop-and-Wait protocol for reliable data transfer. Identify in which one of the following scenarios, the utilization of the link is the lowest. (2023)
(a) Longer link length and lower transmission rate
(b) Longer link length and higher transmission rate
(c) Shorter link length and lower transmission rate
(d) Shorter link length and higher transmission rate
Ans: (b)
Sol: Utilization of Link = Efficiency
Efficiency of Stop and wait protocol is η = 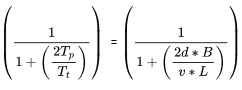
where d = link length (distance) , v = speed , B = bandwidth (Transmission Rate) and L = packet Length
As Efficiency η is inversely proportional to distance d , So Longer Distance means lower efficiency.
As Efficiency η is also inversely proportional to Bandwidth B , So Higher Bandwidth means lower efficiency.
Hence option B is correct.
Q4: Consider a 100 Mbps link between an earth station (sender) and a satellite (receiver) at an altitude of 2100 km. The signal propagates at a speed of 3 × 1 0 8 m/s. The time taken (in milliseconds, rounded off to two decimal places) for the receiver to completely receive a packet of 1000 bytes transmitted by the sender is (2022)
(a) 15.06
(b) 54.25
(c) 7.08
(d) 4.25
Ans: (c)
Sol: Given,
Bandwidth (Bw) = 100 Mbps
distance (d) = 2100 Km = 2100 × 10 3 m
velocity (v) = 3 × 10 8 m/s
packet size (L) = 1000 bytes = 8000 bits
Here, sender is station and receiver is satellite
Here, sender is station and receiver is satellite
So, Total time = Transmission time + Propagation time
Transmission time = L / Bw = 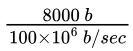 = 0.08 ms
= 0.08 ms
Propagation time = d / v 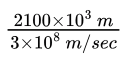 = 7ms
= 7ms
∴ Total time = 0.08 + 7 = 7.08 ms
Q5: Consider a network using the pure ALOHA medium access control protocol, where each frame is of length 1,000 bits. The channel transmission rate is 1 Mbps (= 1 0 6 bits per second). The aggregate number of transmissions across all the nodes (including new frame transmissions and retransmitted frames due to collisions) is modelled as a Poisson process with a rate of 1,000 frames per second. Throughput is defined as the average number of frames successfully transmitted per second. The throughput of the network (rounded to the nearest integer) is ______________ (2021 SET 2)
(a) 180
(b) 160
(c) 135
(d)115
Ans: (c)
Sol: Frame Transmission Time Tfr = L / B= 1000/106 = 1ms
System generates 1000frames in 1 second.
Now, G is defined as average no of frames generated by the system in one frame transmission time.
- 1 second → 1000 frames
- ∴ 1ms →1 frame
Therefore, G = 1
Average number of successful transmissions, S = G * e -2G = 1* e -2 = 0.13534
Throughput is defined in question as the average number of frames
successfully transmitted per second.
∴ Throughput = 0.13534 * 1000 = 135 .34 ≈ 135.
Q6: Consider the cyclic redundancy check (CRC) based error detecting scheme having the generator polynomial X 3 + X + 1. Suppose the message m 4 m 3 m 2 m 1 m 0 = 11000 is to be transmitted. Check bits c 2 c 1 c 0 are appended at the end of the message by the transmitter using the above CRC scheme. The transmitted bit string is denoted by m 4 m 3 m 2 m 1 m 0 c 2 c 1 c 0. The value of the check bit sequence c 2 c 1 c 0 is (2021 SET 2)
(a) 101
(b) 110
(c) 100
(d) 111
Ans: (c)
Sol: The given polynomial x 3 + x + 1 is written as 1011, which consists of 4 bits so, append 3 bits of 0s to the message.
M = 11000000
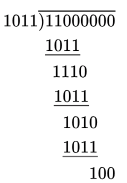 There the check bits sequence is: 100.
There the check bits sequence is: 100.
Correct Option: C
Q7: Consider the sliding window flow-control protocol operating between a sender and a receiver over a full-duplex error-free link. Assume the following: (2021 SET 1)
The time taken for processing the data frame by the receiver is negligible.
The time taken for processing the acknowledgement frame by the sender is negligible.
The sender has infinite number of frames available for transmission.
The size of the data frame is 2,000 bits and the size of the acknowledgement frame is 10 bits.
The link data rate in each direction is 1 Mbps ( = 10 6 bits per second).
One way propagation delay of the link is 100 milliseconds. The minimum value of the sender's window size in terms of the number of frames, (rounded to the nearest integer) needed to achieve a link utilization of 50% is _____________
(a) 82
(b) 51
(c) 44
(d) 65
Ans: (b)
Sol: Let the sender window size be N.
One way propagation delay = 100 ms = 0.1 s
Transmission delay packet = Size of data frame / Link bit rate = 2000 / 106 = 0.002 s
Transmission delay ACK = Size of ACK frame / Link bit rate = 10 / 106 = 0.00001 s
Link Utilization (η) = Useful Data Transfer time / Total time Link
⇒ η = 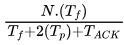
⇒N = 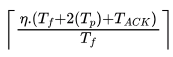 =
= 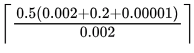 = [ 50. 5025] = 51
= [ 50. 5025] = 51
Correct Answer: 51
Q8: Assume that a 12-bit Hamming codeword consisting of 8-bit data and 4 check bits is d 8 d 7 d 6 d 5 c 8 d 4 d 4 d 3 d 2 c 4 d 1 c 2 c 1 d , where the data bits and the check bits are given in the following tables: (2021 S3ET 1)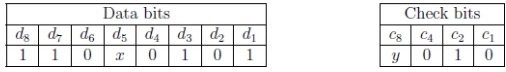
Which one of the following choices gives the correct values of x and y?
(a) x is 0 and y is 0
(b) x is 0 and y is 1
(c) x is 1 and y is 0
(d) x is 1 and y is 1
Ans: (a)
Sol: First I wanna point out a mistake here, it says hamming codeword is 12-bit long, but given codeword sequence is of 13-bit due to repetition of d4 twice (I believe this is a typing error, either they should have write a 13-bit codeword, or d4 occurs only once in this codeword), also 13-bit codeword is very unlikely as it is given in this question, reason: we put check bits at 2 i ∀ i ∈ N ,
But in the given codeword c8 is at 9th position taken from RHS)
Case 1: assume it’s a 12-bit codeword and d4 is repeated twice by mistake,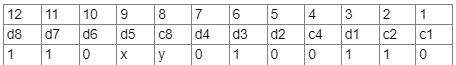 (1) c1 + d1 + d2 + d4 + d5 + d7 should be of even parity
(1) c1 + d1 + d2 + d4 + d5 + d7 should be of even parity
= 0 + 1 + 0 + 0 + x + 1 = x + 2,
x must be 0 for even parity.
(2) c2 + d1 + d3 + d4 + d6 + d7 should be even
= 1 + 1 + 1 + 0 + 0 + 1 = 4 (yes)
(3) c4 + d2 + d3 + d4 + d8 should be even
= 0 + 0 + 1 + 0 + 1 = 2 (yes even)
(4) c8 + d5 + d6 + d7 + d8 should be even
= y + x + 0 + 1 + 1 = y + 2 (taking x=0) , for even parity, y should be 0
Hence if code work is of 12-bit, both x and y are 0.
A is correct here
Case 2: It’s a 13-bit codeword, (I don’t think this will be the case, because c8 should be at position 8), but lets try anyway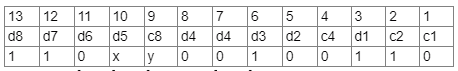 (1) c1 + d1 + d2 + d4 + c8 + d6 + d8 = 0 + 1 + 0 + 0 + y + 0 + 1 = y+2, y will be 0.
(1) c1 + d1 + d2 + d4 + c8 + d6 + d8 = 0 + 1 + 0 + 0 + y + 0 + 1 = y+2, y will be 0.
(2) c2 + d1 + d3 + d4 + d5 + d6 = 1 + 1 + 1 + 0 + x + 0 = x + 3, x will be 1
We may conclude C is correct in this case. but i just wanna check it further for other parity bits whether
they holds good or not
(3) c 4 + d 2 + d 3 + d 4 + d 7 + d 8 = 0 + 0 + 1 + 0 + 1 + 1 = 3 (odd parity) , c 4 should be 1 for this to be
true, which it isn’t)
This case fails, so C is definitely not the answer.
Q9: Consider the following two statements. (2021 SET 1)
S1: Destination MAC address of an ARP reply is a broadcast address.
S2: Destination MAC address of an ARP request is a broadcast address.
Which one of the following choices is correct?
(a) Both S1 and S2 are true
(b) S1 is true and S2 is false
(c) S1 is false and S2 is true
(d) Both S1 and S2 are false
Ans: (c)
Sol: In ARP, source broadcasts an ARP request to all devices in local subnet.
The destination which has the matching IP address then sends an ARP response which includes the MAC address of the source and hence is a unicast message.
Option (C) S1 is false and S2 is true
Q10: Consider that 15 machines need to be connected in a LAN using 8-port Ethernet switches. Assume that these switches do not have any separate up link ports. The minimum number of switches needed is ___________. (2019)
(a) 2
(b) 3
(c) 4
(d) 5
Ans: (b)
Sol: Using 3 switches we can connect maximum 20 machines together.
∴ We require at least 3switches to connect 15 machines.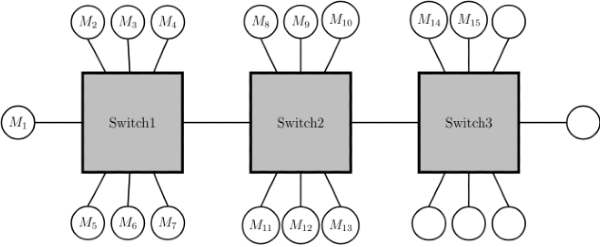
Q11: Suppose that in an IP-over-Ethernet network, a machine X wishes to find the MAC address of another machine Y in its subnet. Which one of the following techniques can be used for this? (2019)
(a) X sends an ARP request packet to the local gateway's IP address which then finds the MAC address of Y and sends to X
(b) X sends an ARP request packet to the local gateway's MAC address which then finds the MAC address of Y and sends to X
(c) X sends an ARP request packet with broadcast MAC address in its local subnet
(d) X sends an ARP request packet with broadcast IP address in its local subnet
Ans: (c)
Sol: Steps in ARP Operation :
- The sender (X) knows its own IP address and MAC address. X also knows the IP address of the target (Y) . It needs to find MAC address of Y
- IP asks ARP to create an ARP request message, filling in X's IP and MAC address and Y's IP address. The destination MAC address is set to all 0s.
- The message is passed to Data Link layer where it is encapsulated in a frame using MAC address of X as the source address and physical broadcast address (all 1s) as the destination address.
- Every host in subnet receives the request message because we have used broadcast MAC address in the destination address. All machines except Y (we have specified Y's IP address in our ARP request message) drop the ARP request message.
- Y replies with an ARP reply message that contains its MAC address.
- When X receives this message, it gets to know the MAC address of Y.
Please note that, a host uses its own IP address and network mask to decide if target IP address is in
its own network or not.
If it is in its network, it uses ARP to resolve the MAC address.
If target IP address is not in its network, it takes the help of default gateway to resolve MAC address using ARP.
Since in question it is clearly mentioned that X (source) and Y (destination) both are in the same subnet, we need not send ARP request message targeted at gateway and then expect it to give the MAC address of Y to X.
So the correct answer is option C.
Q12: Consider a simple communication system where multiple nodes are connected by a shared broadcast medium (like Ethernet or wireless). The nodes in the system use the following carrier-sense based medium access protocol. A node that receives a packet to transmit will carrier-sense the medium for 5 units of time. If the node does not detect any other transmission in this duration, it starts transmitting its packet in the next time unit. If the node detects another transmission, it waits until this other transmission finishes, and then begins to carrier-sense for 5 time units again. Once they start to transmit, nodes do not perform any collision detection and continue transmission even if a collision occurs. All transmissions last for 20 units of time. Assume that the transmission signal travels at the speed of 10 meters per unit time in the medium.
Assume that the system has two nodes P and Q, located at a distance d meters from each other. P starts transmitting a packet at time t=0 after successfully completing its carrier-sense phase. Node Q has a packet to transmit at time t=0 and begins to carrier-sense the medium.
The maximum distance d (in meters, rounded to the closest integer) that allows Q to successfully avoid a collision between its proposed transmission and P's ongoing transmission is _____. (2018)
(a) 25
(b) 50
(c) 75
(d) 100
Ans: (b)
Sol: P starts transmission at t = 0 . If P's first bit reaches Q within Q's sensing window, then Q won't transmit and there shall be no collision.
Q senses carrier till t = 5 . At t = 6 it starts its transmission.
If the first bit of P reaches Q by t = 5 , collision can be averted. Since signal speed is 10 m/time (given), we can conclude that max distance between P and Q can be 50 meters.
Q13: Consider two hosts X and Y, connected by a single direct link of rate 10 6 bits/sec . The distance between the two hosts is 10,000 km and the propagation speed along the link is 2x 1 0 8 m/sec . Host X sends a file of 50,000 bytes as one large message to host Y continuously. Let the transmission and propagation delays be p milliseconds and q milliseconds, respectively . Then the values of p and q are (2017 SET 2)
(a) p = 50 and q = 100
(b) p = 50 and q = 400
(c) p = 100 and q = 50
(d) p = 400 and q = 50
Ans: (d)
Sol: Tt Length / Bandwidth
= (50000 x 8 / 10 6
= 40/100 = 0.4s = 400 ms
Tp = Distance / Velocity
= 10000 x 10 3 / 2 x 10 8
= 1/20 = 0.05s = 50 ms
Hence, answer (D) p = 400, q = 50.
Q14: Consider a binary code that consists of only four valid code words as given below:
00000,01011,10101,11110
Let the minimum Hamming distance of the code be p and the maximum number of erroneous bits that can be corrected by the code be q. Then the values of p and q are (2017 SET 2)
(a) p = 3 and q = 1
(b) p = 3 and q = 2
(c) p = 4 and q = 2
(d) p = 4 and q = 1
Ans: (a)
Sol: 00000 (code1), 01011 (code2), 10101 (code3), 11110 (code4)
Haming distance = min of all hamming distances.
Which is 3 b/w (code1) and (code2) so, p = 3
Now to correct d bit error we need hamming distance = 2 d + 1
So, 2 d + 1 = 3 will gives d = 1 .
A is answer.
Q15: The values of parameters for the Stop-and-Wait ARQ protocol are as given below: (2017 SET 1)
Bit rate of the transmission channel = 1Mbps
Propagation delay from sender to receiver = 0.75 ms
Time to process a frame = 0.25ms
Number of bytes in the information frame =1980
Number of bytes in the acknowledge frame = 20
Number of overhead bytes in the information frame = 20
Assume that there are no transmission errors. Then the transmission efficiency ( expressed in percentage) of the Stop-and - Wait ARQ protocol for the above parameters is _________( correct to 2 decimal places)
(a) 68.3
(b) 79.8
(c) 89.33
(d) 92.66
Ans: (c)
Sol:
Q16: A computer network uses polynomials over GF(2) for error checking with 8 bits as information bits and uses x 3 + x + 1as the generator polynomial to generate the check bits. In this network, the message 01011011 is transmitted as (2017 SET 1)
(a) 01011011010
(b) 01011011011
(c) 01011011101
(d) 01011011100
Ans: (c)
Sol: The generator polynomial has degree 3. So, we append 3 zeroes to the original message.
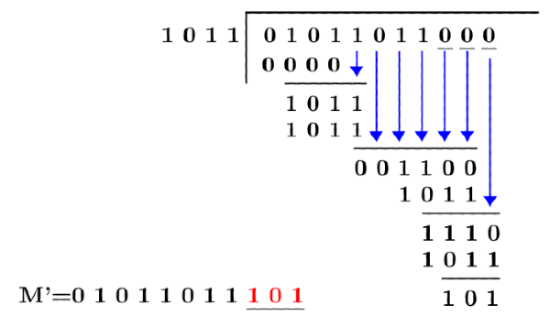
Correct Answer: C
Q17: Consider a 128 × 1 0 3 bits/second satellite communication link with one way propagation delay of 150 milliseconds. Selective retransmission(repeat) protocol is used on this link to send data with a frame size of 1 kilobyte. Neglect the transmission time of acknowledgement. The minimum number of bits required for the sequence number field to achieve 100% utilization is ________. (2016 SET 2)
(a) 3
(b) 4
(c) 5
(d) 6
Ans: (b)
Sol: Answer is 4 bits.
As we want 100 % efficiency (μ) , w s ≥ 1 + 2 a
α = propagation time / transmission time
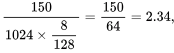
⇒ w s ≥ 1 + 2a = [5.6875] = 6
Available seq numbers ≥ w s + w r
In Selective Repeat,
w s = w r (let it be n)
2xn=2×6=12
avail seq numbers > 12
So, minimum seq numbers are 12.
Number of bits for that is [log 2 12] = 4.
Q18: For the IEEE802.11 MAC protocol for wireless communication, which of the following statements is/are TRUE?
I. At least three non-overlapping channels are available for transmissions.
II. The RTS-CTS mechan is misused for collision detection.
III. Unicast frames are ACKed. (2016 SE6T 2)
(a) All I,II,andIII
(b) I andIIIonly
(c) II andIIIonly
(d) II only
Ans: (b)
Sol: 802.11
MAC = Wifi
I. This is true, maximum 3 overlapping channels are possible in Wifi !
II. This is false. Collision detection is not really possible in Wireless, because signal strength of sending & receiving signal need not be same ! So Wifi uses collision Avoidance instead ! In this RTS-CTS are used to announce to all nodes, that for which node wireless channel is reserved for communication. So this is collision avoidance, not detection
III. This is true. Every frame in Wifi is acked, because Wifi station do not use collision detection, in Ethernet we use collision detection, in which it is possible for us to listen channel for collision & use exponential back off in case of collision detection. As in case of wifi, due to more error rate and not using collision detection strategy , we instead use ACK frame, in case of not getting ACK Host will retransmit after Random back off period
Answer is (B).
Q19: A network has a data transmission bandwidth of 20 × 10 6 bits per second. It uses CSMA/CD in the MAClayer. The maximum signal propagation time from one node to another node is 40 microseconds. The minimum size of a frame in the network is ______ bytes. (2016 SET 2)
(a) 200
(b) 400
(c)100
(d) 600
Ans: (a)
Sol: Since, CSMA/CD
Transmission Delay = RTT
Hence,
LB X RTT
⇒L= B x 2 x Tpropagation delay
⇒ L = (20×10 6) × 2 × 40 ×10-6
= 20 x 2 x 40
= 1600 bits
= 200 bytes
Hence, 200 Bytes is the answer.
Q20: In an Ethernet local area network, which one of the following statements is TRUE? (2016 SET 2)
(a) A station stops to sense the channel once it starts transmitting a frame.
(b) The purpose of the jamming signal is to pad the frames that are smaller than the minimum framesize.
(c) A station continues to transmit the packet even after the collision is detected.
(d) The exponential backoff mechanism reduces the probability of collisionon retransmissions.
Ans: (d)
Sol: On Ethernet:
A. This is false because station need not stop to listen to stuff !
B. No, this is not purpose of jamming signal.
C. No, stations sends jamming signal if collision is detected. This is reason why (B) is false.
So, answer is (D).
Q21: A sender uses the Stop-and Wait ARQ protocol for reliable transmission of frames. Frames are of size 1000bytes and the transmission rate at the sender is 80Kbps(1Kbps=1000 bits/second). Size of acknowledgement is 100bytes and the transmission rate at the receiver is 8Kbps. The one-way propagation delay is 100milliseconds. (2016 SET 1)
Assuming no frame is lost, the sender throughput is _____bytes/second.
(a) 1000
(b) 1500
(c) 2500
(d) 3000
Ans: (c)
Sol: Answer is 2500 bytes per second.
Throughput is number of bytes we are able to send per second.
Calculate the transmission time of sender Tt ( Send ) , calculate one way propagation delay Tp , Calculate the transmission time of receiver Tt (Recv) We get Tt ( Send ) here as 1 /10 seconds,
Tp as 1 /10 seconds( given in question as 100 ms )
Tt (Recv) as 1 / 10 seconds.
So , total time taken to send a frame from sender to destination,
= Tt ( Send ) + 2 × T p + Tt (Recv) = 4 / 10 seconds
So, we can send 1000 bytes (frame size) in 4 / 10 seconds.
in 1 second , we can send 2500 bytes . So throughput is 2500 bytes per second.
Q22: Two hosts are connected via a packet switch with 10 7bits per second links. Each link has a propagation delay of 20 microseconds. The switch begins forwarding a packet 35 microseconds after it receives the same. If 10000 bits of data are to be transmitted between the two hosts using a packet size of 5000 bits, the time elapsed between the transmission of the first bit of data and the reception of the last bit of the data in microseconds is____________. (2015 SET 3)
(a) 1215
(b) 745
(c) 1650
(d) 1575
Ans: (d)
Sol: No. of packets sent = 10000 / 5000 = 2 .
Time for the first packet to reach switch =Transmission time + Propagation delay
= 5000 / 107) x 106 μs + 20μs
= 520 μs
( Another 520 μ s is required for the same packet to reach the destination from the switch and in between there is a forwarding delay of 35 μ s . So, first packet is received at destination at 2 × 520 + 35 = 1075 μ s . )
After 520 μ s , the switch can start receiving the second packet and at 520 + 500 = 1020 μ s , second frame is completely received by the switch ( we don't need to add propagation time here as packet 2 can just follow packet 1 ).
So, at 1055 μ s from the start the switch starts sending the second packet and this will be received at destination after another 520 μ s = 1575 μ s . Since we added transmission time, this ensures that the last bit of data is received at the sender.
EDIT:-
(Alternate solution)
We can think the same question in terms of last packet, argument here is: The moment last packet reaches to destination, all other packets are already reached.
Total time =Transmission time of all packets + Propagation time for first link
+ Switch Delay + Transmission time of last packet for Switch
propagation time for 2nd link.
= (104/ 107 sec = 1 ms = =1000μs) 1000 +20 + 35+500 + 20 = 1575με.
Q23: Consider a network connecting two systems located 8000 kilometers apart. The bandwidth of the network is 500x10 6bits per second. The propagation speed of the media is 4x10 6meters per second. It is needed to design a Go-Back-N sliding window protocol for this network. The average packet size is 10 7bits. The network is to be used to its full capacity. Assume that processing delays at nodes are negligible. Then, the minimum size in bits of the sequence number field has to be ___________. (2015 set 3)
(a) 9
(b) 6
(c) 7
(d) 8
Ans: (d)
Sol: In order to achieve full utilization, sender has to keep on sending frames till
the acknowledgement arrives for the first frame.
Time taken for acknowledgement to arrive is 2times propagation delay + transmission time for a frame.
One way propagation delay = 8000 x 103 / (4 x 106 )= 2s
Time taken to transmit one frame = 107(500 x 106 = 0.02 s
So, RTT =2 × 2 + 0.02 = 4.02s
No. of frames that can be transmitted in 4.02 secs = 4.02 / 0.02 =201
Being Go-Back-N protocol this means W S = 201 and W R = 1. So, total number of sequence numbers required = 201 + 1 = 202.
Hence, minimum number of bits required for sequence numbers till 202 is [ log 2 202 ] = 8.
Q24: Consider a CSMA/CD network that transmits data at a rate of 100 Mbps (10 8bits per second) over a 1 km (kilometer) cable with no repeaters. If the minimum frame size required for this network is 1250 bytes, what is the signal speed (km/sec) in the cable? (2015 SET 3)
(a) 8000
(b) 10000
(c) 16000
(d) 20000
Ans: (d)
Sol: For collision to be detected, the frame size should be such that the transmission time of the frame should be greater than twice the propagation delay (So, before the frame is completely sent, any possible collision will be discovered).
So. 1250 x 8 / 108 ≥ 2 x 1 / x
⇒ x =2 × 10 4 = 20000
Correct Answer: D
Q25: A link has a transmission speed of 10 6bits/sec. It uses data packets of size 1000 bytes each. Assume that the acknowledgment has negligible transmission delay, and that its propagation delay is the same as the data propagation delay. Also assume that the processing delays at nodes are negligible. The efficiency of the stop-and-wait protocol in this setup is exactly 25%. The value of the one-way propagation delay (in milliseconds) is ________. (2015 SET 2)
(a) 12
(b) 18
(c) 25
(d) 8
Ans: (a)
Sol: In stop and wait, a frame is sent and next frame will be sent only after ACK is received.
Efficiency = Amount of data sent / Amount of data that could be sent
Amount of data sent / RTT x 106
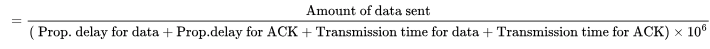
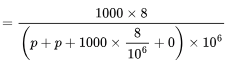 = 8 / 2 p + 8 ms (where p is the prop. delay in milli seconds)
= 8 / 2 p + 8 ms (where p is the prop. delay in milli seconds)
= 4 / p + 4 = 0.25 (given in question)
So, p + 4 = 16 , p = 12 ms .
Q26: Consider a LAN with four nodes S1 , S2 , S3 a n d S4 . Time is divided into fixed-size slots, and a node can begin its transmission only at the beginning of a slot. A collision is said to have occurred if more than one node transmit in the same slot. The probabilities of generation of a frame in a time slot by s S1 , S2 , S3 a n d S4 are 0.1, 0.2, 0.3 and 0.4, respectively. The probability of sending a frame in the first slot without any collision by any of these four stations is _____________. (2015 SET 1)
(a) 0.2
(b) 0.4
(c) 0.6
(d) 0.8
Ans: (b)
Sol: P = P(S1) P(¬S2)P(¬S3)P(¬S4)
+P(¬S1)P(S2)P(¬S3)P(¬S4)
+P(¬S1)P(¬S2)P(S3)P(¬S4)
+P(¬S1)P(¬S2)P(¬S3)P(S4)
0.1 * 0.8 * 0.7 * 0.6 + 0.9 * 0.2 * 0.7 * 0.6 + 0.9 * 0.8 * 0.3 * 0.6 + 0.9 * 0.8 * 0.7 * 0.4
= 0.4404
Q27: Suppose that the stop-and-wait protocol is used on a link with a bit rate of 64 kilobits per second and 20 milliseconds propagation delay. Assume that the transmission time for the acknowledgement and the processing time at nodes are negligible. Then the minimum frame size in bytes to achieve a link utilization of at least 50% is______________. (2015 SET 1)
(a) 220
(b) 180
(c) 320
(d) 120
Ans: (c)
Sol: Link Utilization = Amount of data sent / Max. amount of data that could be sent
Let x be the frame size in bits.
In stop-and-wait protocol, once a frame is sent, next frame won't be sent until ACK is received.
Time for this,
RTT = Propagation delay for frame + Transmission time for frame
+ Propagation delay for ACK + Transmission time for ACK
= 20 ms + x / 64 ms + 20 ms (+ 0 (as given in question)
= (40 + x / 64 ) ms.
Amount of data sent during RTT = x
Max. amount of data that could be sent = (40 + x / 64 ) x 64 = 2560 + x bites.
So, link utilization, 0. 5 = x (2560 + x)
x = 2560 bits = 320 bytes.
Alternative Approach ,
Link utilization or efficiency of stop and wait protocol is ,
efficiency = 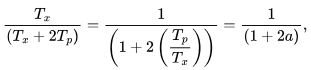
where , Transmission time = T x = packet size / bandwidth d = L / B
Propagation time = T p = distance / speed = d / v , and
a = Propagation time / Transmission time = T p / T x ,
Now for 50 % efficiency ,
efficiency = 1 / (1 + 2a)
50% = 1/(1 + 2a)
1/2 = 1/(1 + 2a)
2 = (1 + 2a)
2 - 1 = 2a
1 = 2(Tp / t x )
Tx = 2 x Tp
L / B = 2 x 20ms
L = 2 x 20ms x B = 2 x 20 x 10 - 3 x 64k bits
= 2 x 20 x 10- 3 x 64 x 10 3 bits
L = 40 x 64 bits = 40 x 64 / 8 bytes = 40 × 8 bytes = 320 bytes (answer)
|
21 videos|143 docs|66 tests
|
FAQs on Previous Year Questions: Data Link Layer - Computer Networks - Computer Science Engineering (CSE)
| 1. What is the purpose of the Data Link Layer in computer networking? |  |
| 2. What are some common protocols used in the Data Link Layer? |  |
| 3. How does the Data Link Layer handle addressing in a network? |  |
| 4. What is the difference between a Data Link Layer switch and a router? |  |
| 5. How does the Data Link Layer ensure data integrity during transmission? |  |
















