Cyber Ethics Chapter Notes | Computer Application: Class 10 PDF Download
Introduction to Cyber Ethics
Cyber ethics is a set of guidelines that promote responsible and respectful behavior when using computers and the internet. It focuses on maintaining good conduct online, ensuring users act politely and responsibly to create a safe and positive digital environment. Cyber ethics helps protect individuals' moral, financial, and social well-being by encouraging safe and sensible use of technology.
Netiquettes
- Netiquettes are guidelines for polite and respectful online behavior to ensure effective and harmonious digital communication.
- Following netiquettes fosters a positive online environment and enhances communication for everyone.
Be Respectful and Courteous
- Treat others kindly and respectfully, just as you would in person.
Example: Use polite language and avoid offensive remarks, even during disagreements. - Avoid using all capital letters, as it may seem like shouting.
Example: Write “This is important” instead of “THIS IS IMPORTANT.”
Be Clear and Concise
- Keep messages relevant to the topic to avoid confusion.
Example: Stick to project updates in a discussion instead of sharing unrelated stories. - Use proper grammar and spelling for clear and professional communication.
Example: Proofread emails to fix typos or errors before sending.
Respect Privacy and Confidentiality
- Do not share personal or sensitive information about yourself or others.
Example: Avoid posting your address or phone number on public platforms. - Ask for permission before sharing someone else’s content.
Example: Get a friend’s consent before sharing their photo online.
Be Mindful of Tone
- Ensure your tone is clear to avoid misinterpretation, as online messages lack vocal cues.
Example: Use emojis or polite words, like “I’m excited to work on this! ” instead of just “I’m excited.”
Respect Others’ Time
- Avoid sending repetitive or unnecessary messages to prevent spamming.
Example: Don’t send multiple follow-ups if a question has already been answered. - Reply to messages promptly to show respect for others’ time.
Example: Respond to important emails within 24 hours.
Avoid Plagiarism
- Always give credit to the original source when using someone else’s work or ideas.
Example: Cite articles or references when quoting in your work.
Handle Conflicts Calmly
- Resolve disagreements privately through direct messages rather than public platforms.
Example: Discuss a disagreement with a team member via email instead of a public chat. - Offer constructive feedback or solutions instead of just criticizing.
Example: Suggest “Let’s try this approach” instead of saying “This won’t work.”
Use Appropriate Usernames and Avatars
- Choose usernames that are professional and suitable for the context.
Example: Use “JaneDoe” instead of “SuperStarJane” for professional platforms. - Select avatars or profile pictures appropriate for the platform’s purpose.
Example: Use a professional photo for LinkedIn and a casual one for personal social media.
Software Licenses and the Open Source Software Movement
Software licenses and the open source software movement are key to how software is created, shared, and utilized. Knowing them helps you make informed choices about the software you use and contribute to. Here’s an overview:
Software Licenses
- Software licenses are legal agreements that outline how software can be used, modified, and shared.
Proprietary Licenses
- Restrict how software can be used, modified, or shared, keeping the source code private.
Example: Microsoft Windows or Adobe Photoshop. - Users must pay for the software.
- Usage is limited to terms set by the license.
Open Source Licenses
- Allow users to view, modify, and share the software’s source code.
Examples: MIT License (allows broad use and modification), GNU General Public License (GPL requires modified versions to remain open source). - Source code is publicly accessible.
- License terms may require derivative works to also be open source.
The Open Source Software Movement
- Promotes freely available software source code, encouraging collaboration and transparency.
Principles of Open Source
- Transparency: Users can see and improve the software’s code.
- Collaboration: Developers worldwide can contribute to improve the software.
- Freedom: Users can use, modify, and share the software freely.
Benefits of Open Source
- Cost: Often free, reducing expenses.
- Security: Community scrutiny helps identify and fix vulnerabilities quickly.
- Flexibility: Software can be customized to meet specific needs.
Examples of Open Source Software
- Linux: A widely used open source operating system for servers and desktops.
- Mozilla Firefox: A customizable open source web browser.
- Apache HTTP Server: A popular open source web server software.
Challenges and Considerations
- Support: May lack professional support compared to proprietary software.
- Compatibility: May not work well with some proprietary systems.
- Maintenance: Relies on community contributions, which may be inconsistent.
Intellectual Property Rights, Plagiarism, and Digital Property Rights
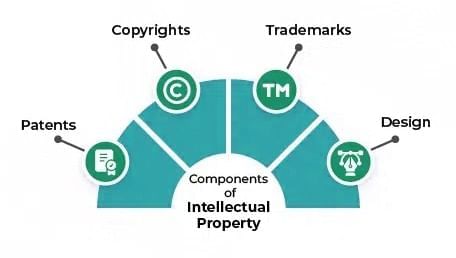
Intellectual Property Rights
- Legal protections for creators to control and profit from their inventions, designs, or artistic works.
Types of Intellectual Property Rights
- Copyright: Protects original works like books, music, films, and software, giving creators exclusive rights to reproduce and distribute.
Example: J.K. Rowling’s rights over Harry Potter books. - Patent: Protects inventions, granting exclusive rights to make, use, or sell them for a period.
Example: Alexander Graham Bell’s patent for the telephone. - Trademark: Protects symbols, names, or logos that identify goods or services.
Example: Nike’s “swoosh” logo. - Trade Secret: Protects confidential business information that gives a competitive advantage.
Example: Coca-Cola’s recipe.
Plagiarism
- Using someone else’s work or ideas without giving credit, considered unethical with serious consequences.
Types of Plagiarism
- Direct Plagiarism: Copying text word-for-word without citing the source.
Example: Copying a website paragraph into an essay without quotes or citation. - Self-Plagiarism: Reusing your own previous work without acknowledgment.
Example: Submitting the same paper for multiple classes without permission. - Mosaic Plagiarism: Mixing phrases or ideas from various sources without citation.
Example: Combining sentences from different sources in an essay without citing. - Accidental Plagiarism: Failing to cite sources due to ignorance or oversight.
Example: Forgetting to cite a paraphrased idea.
Preventing Plagiarism
- Cite Sources: Always credit quotes, ideas, or data to their original source.
- Paraphrase Correctly: Rewrite information in your own words and cite the source.
- Use Plagiarism Checkers: Tools like Turnitin or Grammarly help detect potential plagiarism.
Digital Property Rights
- Rights related to digital content and assets, covering ownership and distribution.
Key Aspects of Digital Property Rights
- Digital Copyright: Extends copyright protection to digital formats like e-books or online articles.
Example: Rights to a digital photograph shared online. - Digital Rights Management (DRM): Technologies to control the use and distribution of digital content.
Example: Encryption on digital music to prevent unauthorized sharing. - Terms of Service Agreements: Rules governing how users interact with digital platforms.
Example: Facebook’s terms outline how user data is used and shared.
Challenges in Digital Property Rights
- Piracy: Unauthorized copying or distribution of digital content.
Example: Downloading movies or software from illegal sources. - Data Privacy: Protecting personal data collected online from misuse.
Example: Companies managing user data responsibly. - Enforcement: Difficulty enforcing rights due to the internet’s global nature.
Example: Legal action against websites distributing pirated content.
Freedom of Information and the Digital Divide
Freedom of Information
- The right to access information held by public authorities, promoting transparency and accountability.
Key Aspects
- Transparency: Allows public scrutiny of government actions and decisions.
Example: Requesting records on public fund usage. - Access to Public Records: Individuals can request documents or emails from government agencies.
Example: Accessing city council meeting minutes. - Limitations: Exceptions protect sensitive information like national security or personal privacy.
Example: Withholding ongoing investigation details or medical records.
Benefits of Freedom of Information
- Promotes Accountability: Ensures officials are responsible for their actions.
- Encourages Participation: Helps citizens make informed decisions and engage in civic life.
- Prevents Corruption: Transparency reduces opportunities for corrupt practices.
Challenges
- Information Overload: Large data volumes can be hard to process.
- Access Issues: Not everyone has the means or knowledge to request information.
- Potential Misuse: Information may be misinterpreted or misused.
The Digital Divide
- The gap between those with access to technology and those without, affecting internet, devices, and digital skills.
Key Aspects
- Access to Technology: Differences in access to devices and high-speed internet.
Example: Rural areas often have less reliable internet than urban areas. - Digital Skills: Varying abilities to use technology effectively.
Example: Older adults may find new technology harder to use than younger people. - Economic Factors: Cost of technology can be a barrier for low-income families.
Example: Families may struggle to afford internet or modern devices.
Impacts of the Digital Divide
- Educational Disparities: Students without technology struggle with online learning.
- Employment Opportunities: Lack of digital skills limits job prospects.
- Social Exclusion: No internet access can exclude people from online communities and services.
Bridging the Digital Divide
- Community Programs: Offer affordable or free technology and internet access.
Example: Libraries providing free internet and computer use. - Educational Training: Programs to teach digital skills and online safety.
Example: Workshops on basic computer use or internet safety. - Policy and Infrastructure: Government efforts to improve internet access and affordability.
Example: Subsidies for internet providers to expand rural coverage.
E-Commerce: Privacy, Fraud, and Secure Data Transmission
Privacy
- Protecting users’ personal and financial information to build trust and comply with laws.
Key Aspects
- Personal Data Protection: Safeguarding details like names, addresses, and payment information.
Example: Retailers not sharing email or credit card details without consent. - Privacy Policies: Websites must clearly state how they collect, use, and protect data.
Example: A policy stating data is used only for orders and marketing, not sold to others. - Regulations: Laws like GDPR or CCPA require user consent and data deletion options.
Example: GDPR mandates explicit consent for data collection.
Challenges
- Data Breaches: Hackers accessing personal data due to weak security.
- User Awareness: Many users don’t understand or read privacy policies.
Fraud
- Deceptive practices exploiting vulnerabilities in online transactions or data.
Types of Fraud
- Credit Card Fraud: Using stolen card details for unauthorized purchases.
Example: Making purchases with stolen credit card information from phishing emails. - Phishing Scams: Tricking users into sharing sensitive information via fake communications.
Example: Fake bank emails asking for login details through a link. - Identity Theft: Using stolen personal information for fraudulent accounts or purchases.
Example: Opening accounts or loans using someone else’s details.
Preventing Fraud
- Secure Payment Gateways: Use processors with fraud detection features.
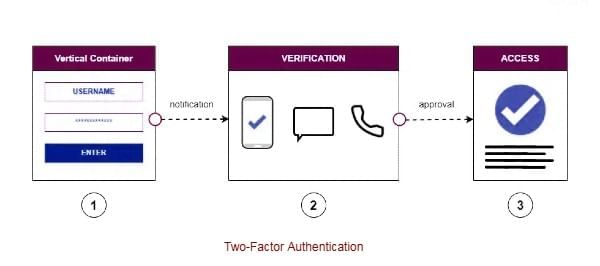
Example: PayPal or Stripe detecting suspicious transactions. - Two-Factor Authentication (2FA): Requires a second verification step beyond passwords.
Example: Entering a code sent to your phone along with your password. - Regular Monitoring: Checking transactions for suspicious activity.
Example: Flagging large purchases from new accounts as potential fraud.
Secure Data Transmission
- Protecting data exchanged online from interception or tampering.
Key Techniques
- Encryption: Scrambles data so only authorized parties can read it.
Example: HTTPS encrypts data between your browser and an e-commerce site. - SSL/TLS Certificates: Secure protocols for encrypting internet connections.
Example: A padlock icon in the browser indicates SSL/TLS security. - Secure Sockets Layer (SSL) Certificates: Ensures data between a server and browser is encrypted.
Example: Websites with “https” URLs use SSL for secure connections.
Challenges
- Phishing Sites: Fake websites mimicking legitimate ones to steal data.
Example: Checking for “https” and padlock icons to avoid fake sites. - Outdated Protocols: Using old security protocols increases data risks.
Example: Regularly updating security systems to maintain protection.
|
10 videos|97 docs|18 tests
|
FAQs on Cyber Ethics Chapter Notes - Computer Application: Class 10
| 1. What is cyber ethics and why is it important? |  |
| 2. How can individuals protect their privacy and personal information online? |  |
| 3. What are the potential risks and challenges associated with cyber ethics? |  |
| 4. How can parents and educators promote cyber ethics among children and students? |  |
| 5. What are the legal consequences of unethical online behavior? |  |

















