Class 10 Computer Application: CBSE Sample Question Paper- Term I (2021-22) - 3 | CBSE Sample Papers For Class 10 PDF Download
| Table of contents |

|
| Class-X |

|
| Time: 90 |

|
| Minutes |

|
| M.M: 25 |

|
| Section - A |

|
| Section - B |

|
| Section - C |

|
Class-X
Time: 90
Minutes
M.M: 25
General Instructions :
Read the following instructions very carefully and strictly follow them:
- The Question Paper contains three sections A, B and C.
- Section A has 20 questions. Attempt any 16 questions.
- Section B has 20 questions. Attempt any 16 questions.
- Section C has 10 questions. Attempt any 8 questions.
- All questions carry equal marks.
- There is no negative marking.
Section - A
Q.1: An example of a _______ transaction would be a person buying a pair of shoes from a retailer.
(a) B2B
(b) B2C
(c) C2B
(d) 2C2
Correct Answer is Option (b)
B2C (Business to Consumer) describes activites of business serving and consumers with products and services. Common B2C E-Business models include E-Ships and E-mails. An example of a B2C transaction would be a person buying a pair of shoes from a retailer.
Q.2: Which of the following is/are type(s) of plagiarism?
(a) Complete plagiarism
(b) Self plagiarism
(c) Concealing sources
(d) All of these
Correct Answer is Option (d)
Plagiarism is the wrongful appropriation and stealing the publication of another author’s language, thoughts, ideas as one’s own original work. Types of plagiarism are complete plagiarism, self plagiarism, partial plagiarism, concealing sources, word switch, inadvertently, copying and parting etc.
Q.3: ______ is the special power of monopoly granted by the law.
(a) Copyright
(b) Patent
(c) Trademark
(d) All of these
Correct Answer is Option (b)
Patent is the special power of monopoly granted by the law. The work cannot be used or reproduced without obtaining a license from patent holder.
Q.4: <IMG> log is an empty element, which means it has
(a) no opening tag
(b) no closing tag
(c) both tags
(d) None of these
Correct Answer is Option (b)
<IMG> tag is used to insert an image in a web page. <IMG> tag is an empty element, which means it has no closing tag.
Q.5: The value for ALT attribute is a text string of upto _______ characters including spaces and punctuations
(a) 256
(b) 512
(c) 786
(d) 1024
Correct Answer is Option (d)
ALT attribute of <IMG> tag is used to provide alternate text when an image on a web page cannot be displayed. The value for ALT attribute is a text string of upto 1024 characters including spaces and punctuations.
Q.6: To prevent hacking, which point is to be used?
(a) Create complex passwords
(b) Lack of enforcement
(c) Give your password to anyone
(d) Don’t logout of accounts
Correct Answer is Option (a)
Hacking means stealing of required information by seeking and exploiting weakness in a computer or computer network. To prevent hacking, create complex passwords.
Q.7: Which of the following provide services titled “Webtrust” and “Systrust”?
(a) TRUSTE
(b) BBB Online
(c) PrivacyBoat.com
(d) CPA Webtrust
Correct Answer is Option (d)
CPA webtrust provide services titled “WebTrust” and “SysTrust”. It promises an audit of technology, security and business practices.
Q.8: Use the ________ container tag to create multiline, scribble, text entry boxes.
(a) <TEXTAREA>
(b) <SELECT>
(c) <TEXT>
(d) <OPTION>
Correct Answer is Option (a)
Use the <TEXTAREA> container tag to create muttiline, scrollable, text entry boxes. Whatever is between the <TEXTAREA> and </TEXTAREA> tags will be the initial contents of the entry box, so put them right next to each others, if you do not want initial contents.
Q.9: Which of the following is/are attributes(s) of <OPTION> tag?
(a) label
(b) value
(c) Selected
(d) All of these
Correct Answer is Option (d)
<OUTPUT> tag occurs only within the <SELECT> element and is used to represent each choice of the select. These are various attributes of <OPTION> tag as label, value, selected.
Q.10: ______ is the protection against the denial of order or denial of payment.
(a) TRUSTE
(b) Privacy
(c) Non-reputability
(d) Copyright
Correct Answer is Option (c)
Non-reputability is true protection against the denial of order or denial of payment. Once a sender sends a of order or denial of payment. The sender should not be able to deny sending the message. Similarly, the recipient of message should not be able of deny the receipt.
Q.11: Which of the following is the back end of your website?
(a) Content management system
(b) Site Hasting
(c) Social media pages
(d) Domain name
Correct Answer is Option (a)
Content management system is the back end of your website check who has access to this section of your website and make sure they don’t have unrestricted access to the site.
Q.12: Which tag defines text entity fields, check boxes, radio buttons or push buttons?
(a) <SELECT>
(b) <INPUT>
(c) <OPTION>
(d) <TEXTAREA>
Correct Answer is Option (b)
<INPUT> tag defines text entry fields, check boxes, radio buttons or push buttons. It is an empty element specified by <INPUT> tag. It defines an object on the form which can receive user input.
Q.13: Which of the following attribute, that is the HTTP method used to submit the form data?
(a) name
(b) action
(c) method
(d) none of these
Correct Answer is Option (c)
HTML forms are very effective because they can easily collect data from the internet and utilize that information in other webpage. A method attribute, which is the HTTP method used to sumbit the form data.
Q.14: HTML is what type of language?
(a) Scripting language
(b) Markup language
(c) Programming language
(d) Network protocol
Correct Answer is Option (b)
HTML is a markup language used to build web pages and web applications.
Q.15: Which of the following is the attribute of <FORM> tag?
(a) GET
(b) POST
(c) form
(d) action
Correct Answer is Option (d)
Action is the attribute of <FORM> tag. Action provides the URL of the program (in the server) that receives the information from the form and processes it.
Q.16: Common B2C e-Business models include
(a) e-ships
(b) e-mails
(c) (A) and (B)
(d) None of these
Correct Answer is Option (c)
Business to Consumer (B2C) describes activates of business serving and consumer with products and services. Common B2C E-Business models include E-Ship’s and E-mails. The transactions that led to the shoes being available for purchase, which is the purchase of the leather, laces, rubber etc.
Q.17: Apart from <b> tag, what other tag makes text bold?
(a) <fat>
(b) <strong>
(c) <black>
(d) <emp>
Correct Answer is Option (b)
The HTML <strong> tag gives text a strong emphasis which traditionally means that the text is displayed as bold by the browser. This tag is also commonly referred to as the <strong> element.
Q.18: How is a tag enclosed?
(a) ()
(b) <>
(c) []
(d) {}
Correct Answer is Option (b)
A tag is an HTML code that defines every structure on an HTML page. They also define the placement of test image, links in an HTML document
HTML tags begins with “less-than” symbol (<) and end with “greater-than” symbol (>). These symbols are also called angular brackets. A start tag marks the beginning of a tag and its syntax is:
<TAGNAME>
An end tag marks the end of a tag and its syntax is: </TAGNAME>.
Q.19: ____ method is used to sent form data as HTTP Post.
(a) Get
(b) Set
(c) POST
(d) None of these
Correct Answer is Option (c)
Some feature of POST requests are:
POST requests are never cached.
POST requests do not remain in the browser history.
Q.20: To display (x + y)2, correct HTML code is:
(a) <SUB> (X + Y)2</SUB>
(b) X + Y<SUP>2</SUP>
(c) (X + Y)<SUP>2</SUP>
(d) <SUP>(X + Y)2</SUP>
Correct Answer is Option (c)
The <SUP> tag is used to display the test as superscript. The superscript text will appear half a character height above the other characters.
Section - B
Q.21: Arun clicks on a link received in a message on his phone which promises him a complimentary trip to a destination of his choice. He forwarded this message to his friend, Panshul and asked him to do the same. But Panshul refuses and tells Arun that his personal and private information, such as online account names, login information and passwords can be stolen and he should be careful of such .................... attacks.
(a) Phishing
(b) Spamming
(c) Scamming
(d) Plagiarism
Correct Answer is Option (a)
A phishing attack happens when someone tries to trick you into sharing personal information online. For example, someone who is phishing might send you an email that looks like it is from your bank so that you will give them information about your bank account.
Q.22: Consider the following HTML code:
<ol type='i'>
<li>First</li>
<li>Second</li>
<li>Third</li>
<li>Fourth</li>
</ol>
Choose the correct output that would be shown upon execution of the above code , from the choices given below:
(a)
I. First
II. Second
III. Third
IV. Fourth
(b)
i. First
ii. Second
iii. Third
iv. Fourth
(c)
I. First
II. Second
III. Third
IV. Fourth
(d)
i. First
ii. Second
iii. Third
iv. Fourth
Correct Answer is Option (b)
<ol> tag defines the ordered list and type attribute of that list defines the type of list.
<li> tag defines the list item
In given code, type=i so the correct output is
i. First ii. Second iii. Third iv. Fourth
Q.23: Charlene is an artist. She displays her artwork on the Internet using her website to attract buyers. One day while browsing the Internet she discovers that another artist has displayed her painting portraying it as his own. Which right of Charlene was infringed?
(a) Digital Privacy right
(b) Intellectual Property right
(c) Digital Property right
(d) Intellectual Privacy right
Correct Answer is Option (b)
The right of charlene was infringed as Intellectual Property Right.
Intellectual Property Rights are the rights given to persons over the creations of their minds.
Q.24: Which of the following will result in the largest text size?
(a) <H3>
(b) <H6>
(c) <H2>
(d) <H4>
Correct Answer is Option (c)
From given options, the largest text size will be <H2>.
The heading tag is used in HTML to define by, <Hn>, with “n” being a number 1 and 6. The largest heading tag is <h1> but from options <h3>, <h6>, <h2> and <h4>, <h2> will be largest.
Q.25: We can create a numbered list using the tag.
(a) <UL>
(b) <list>
(c) <OL>
(d) <DL>
Correct Answer is Option (c)
<OL> tag defines the ordered or numbered or numbered list. While <UL> tag defines the unordered or bulleted list and <DL> tag defines the definition list.
Q.26: Which of these is NOT an example of Cyber bullying?
(a) Copying a classmate’s personal photo against his/her permission from his social media account and sending it to other friends on their emails
(b) Bullying a classmate in the school corridor.
(c) Threatening someone on whatsapp.
(d) Posting mean messages about someone on their social media.
Correct Answer is Option (b)
Cyberbullying is the use of technology to harass, threaten, embarrass or target another person. Bullying a classmate in the school corridor is not an example of Cyberbullying.
Q.27: Identify which of the following type of list will create a bulleted list.
(a) Unordered
(b) Ordered
(c) Definition
(d) Numbered
Correct Answer is Option (a)
Unordered type of list will create a bulleted list. This list is defined by <UL> tag.
Q.28: Which sequence of HTML tags is correct?
(a) <html><head><title></title></head><body></body></html>
(b) <html><head><title><body></title></head></body></html>
(c) <html><head><title</head><body></body>></title></</html>
(d) <html><head><title><body></body ></title></head ></html>
Correct Answer is Option (a)
The HTML code structure
Q.29: Pratham is excited to use a new software which is freely available to download but he cannot modify or change the source code. Pratham is using
(a) Freeware
(b) Open-Source Software
(c) Both (A) and (B)
(d) None of the above
Correct Answer is Option (a)
Pratham is using freeware. Freeware is a software that may be freely downloaded, installed, used and shared. But used cannot modify or change its source code.
Q.30: Priyanshu has written the following code snippet as part pf an HTML program.
<B> Mystery Moon </B>
Predict the output of the above from the following:
(a) Mystery Moon
(b) Mystery Moon
(c) Mystery Moon
(d) Mystery Moon
Correct Answer is Option (b)
<B> tag is used to specify the bold text without any extra importance.
The correct output of given code is Mystery Moon.
Q.31: Consider the following code:
<img src="https://cn.edurev.in/omputers.jpg" width=" _________ " height=" ________”>
Fill in the blanks to set the image size to be 250 pixels wide and 400 pixels tall.
(a) 250, 400
(b) 400, 250
(c) <250><400>
(d) <400><250>
Correct Answer is Option (a)
<img src = “computers. jpg” width=“250” height=”400”> because 250 pixels is given for width and 400 pixels is given for height of an image.
Q.32: Tag (s) required to create Description lists in HTML:
(a) <DL>
(b) <DT>
(c) <DD>
(d) All of the above
Correct Answer is Option (d)
To create description list in HTML , three tags as <DL>, <DT>, <DD> are used.
Here, <DL> stands for Definition list, <DT> defines a term in a definition list and <DD> provide the description.
Q.33: Which of the following is NOT a reason for the digital divide in different demographic regions?
(a) Cost of Technology
(b) Lack of information
(c) Lack of access to high performance computers
(d) Lack of access to the disabled.
Correct Answer is Option (b)
The digital divide refers to the gap between demographics and regions that have access to modern information and communications technology and those that don’t have access.
Lack of access to high performance computers is not a reason for the digital divide in different demographic regions.
Q.34: One of the most popular method of encrypting data is Ceaser cipher where original data is replaced by a key character like if key is –2 than ‘a’ will be replaced by ‘y’, ‘b’ is replaced by ‘z’ and so on.
If the key is 2 i.e. Every letter is replaced by its next to next letter means the letter 'A' will be replaced by 'C', the letter 'B' is replaced by 'D', and so on then what will be the replacement of the word 'CoMpUtEr'.
(a) Eqorwvgt
(b) eQOrwVtG
(c) eqroWVTG
(d) EqOrWvGt
Correct Answer is Option (d)
If the key is 2 i.e. every letter is replaced by its next to next letter
So, the replacement of the word ‘CoMpUtEr’ is EqOrWvGt.
Q.35: Consider the following form control in a HTML form: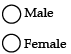
Now choose the correct line of code for the above :
(a) <input type = “radio” name= “Gender ” value= “male”>Male<br>
<input type = “radio” name= “Gender” value= “female”>Female<br>
(b) <input type = “radiobutton” name= “Gender ” value= “male”>Male<br>
<input type = “radiobutton” name= “Gender” value= “female”>Female<br>
(c) <input type = “radio”, name= “Gender ”>< value= “male”>Male
<input type = “radio”, name= “Gender”>< value= “female”>Female
(d) <input type = “radio” name= “Gender ” value= “male”><br>
<input type = “radio” name= “Gender” value= “female”><br>
Correct Answer is Option (a)
Here is two radio buttons which has values Male and Female
So, the correct doe is
<input type = “radio” name = “Gender” value = “male”> Male <br> <input type = “ratio” name = “Gender” value = “female”> Female <br>
Q.36: Gagandeep has written the following code to display an image in the background of HTML document:
<BODY BgGround= “Animals.jpeg”>
but he is not getting the desired output. Help him in identifying correct code from the following:
(a) <BODY Bg= “Animals.jpeg”>
(b) <BODY BACK= “Animals.jpeg”>
(c) <BODY BGIMAGE= “Animals.jpeg”>
(d) <BODY BACKGROUND= “Animals.jpeg”>
Correct Answer is Option (d)
To display the image in the background of HTML document, BACKGROUND attribute is used which take image’s name with its format as value.
So, the correct code is
<BODY BACKGROUND = “Animals. jpeg”>
Q.37: Which of the following is a way to avoid Plagiarism when using material from the Internet?
(i) Citing
(ii) Paraphrasing
(iii) Referencing
(iv) embedding
Choose the correct option:
(a) (i) and (ii) only
(b) Only (i)
(c) (i), (ii) and (iii) only
(d) (ii) and (iv) only
Correct Answer is Option (c)
Plagiarism refers to using some other person’s ideas and information without acknowledging that specific person as the source.
There are certain ways to avoid plagiarism when using material from the Internet as
- Citing
- Paragraphing
- Referencing
Q.38: Tag to create password field in HTML document:
(a) <password>
(b) <input>
(c) <pwd>
(d) <pword>
Correct Answer is Option (b)
<input> element of type “password” provide a way for the user to securely enter password.
Syntax
<input type = “password”>
Q.39: Which of the following tag is used to define options in a drop-down selection list?
(a) <select>
(b) <list>
(c) <dropdown>
(d) <option>
Correct Answer is Option (d)
To include an option in a drop down list, use the <option> tag in HTML. This is a container tag which has opening tag as well as closing tag.
Q.40: Which of the following is the correct way to create a list using the lowercase letters?
(a) <ol alpha = "a" >
(b) <ol type = "a">
(c) <ol letter = "a">
(d) None of the above
Correct Answer is Option (b)
<ol> tag is used to define the ordered or numbered list in HTML document type attribute of <ol> tag defines the type of ordered.
To create a list using the lowercase letters, the correct code is
<ol type = “a”>
Section - C
I. Read the following text and answer the following questions on the basis of the same:
HTML can be used to insert image in the following formats:
GIF (Graphics Interchange Format)
XBM(X Bitmap)
JPG or JPEG (Joint Photographic Experts Group)
PNG(Portable Network Graphics)
The <IMG> tag is used to insert an image in a web page. It is very important to know that images are not technical part of the web page file, they are separate tiles which are inserted into the web page, when it is viewed by a browser.
So, a simple web page with one image is actually two files. When an HTML file is displayed in a browser it request the image file and places it on the web page where the tag appears.
Based on the given information, answer the Questions No. 41-45.
Q.41: Web browsers display images in the following format
(a) XBM
(b) JPEG
(c) GIF
(d) All of these
Correct Answer is Option (d)
HTML supports various formats of the images, like Graphics Interchange Format(GIF), Joint Photographi Experts Group(JPEG), etc. GIF is limited to an 8-bit palette or 256 colors.
This makes the GIF format suitable for storing graphics with relatively few colors such as simple diagrams, shapes, logos and cartoon style images whereas JPEG is the best format for photographers. It contains 1 million colors.
Q.42: Which tag is used to insert an image in web page?
(a) <A>
(b) <TABLE>
(c) <IMG>
(d) <P>
Correct Answer is Option (c)
Images can enhance the appearance and the design of a web page. In HTML, the <IMG> tag is used to define images. The <IMG> tag at a minimum, takes two attributes. ALT and SRC.
Q.43: The correct HTML code for inserting an image is:
(a) <IMG hred = “image.gif”>
(b) <IMG> image.gif</gif>
(c) <IMG src = “image.gif”>
(d) <IMAGE src = “image.gif ”>
Correct Answer is Option (c)
The syntax of inserting an image in a web page is:
<IMG SRC = “URL”>
The URL points to the location where the image is stored. The browser puts the image where the image tag occurs in the document.
Q.44: src attribute used with <IMG> tag stands for :
(a) screen
(b) screen resolution count
(c) source
(d) structure
Correct Answer is Option (c)
The SRC attribute is used to specify the URL of the image. The SRC attribute is mandatory to insert an image.
Q.45: ________ attribute is used to specify the location of an image file.
(a) alt
(b) src
(c) align
(d) name
Correct Answer is Option (b)
The SRC attribute is used to give URL of an image. It is compulsory to use this attribute to insert an image.
Read the following text and answer the following questions on the basis of the same:
Digital divide: The digital divide or the digital split is a social issue of referring to the differing amount of information between those who have access the internet and these who do not have access. The term became popular among concerned parties such as scholars policy makers and advocacy group, in the late 1990s.
Brodly speaking, the difference is not necessarily determined by the access to ICT (Information and communication technology) and to the media that the different segment of society can use with regard to the internet, the access is only one aspect, others factors such as the quality of connection and related services should be considered. Today, the most discussed issue is the availability of the access at an affordable cost and quality.
Based on the given information, answer the questions NO. 46-50.
Q.46: What is the another name for digital divide?
(a) Plagiarism
(b) Digital split
(c) Digital advance
(d) Digital core
Correct Answer is Option (b)
Digital divide is also known as digital split. It is a term that describes the uneven distribution of information and communication technology (ICT). It differences between rural and urban internet access.
Q.47: Which of the following is not the effects of digital divide?
(a) Economic inequality
(b) Effect on education
(c) Attitudinal factors
(d) Democracy
Correct Answer is Option (c)
There are various effects of digital divide as economic inequality, effect on education, economic growth, democracy and social mobility. Attitudinal factors is not the effect of digital divide.
Q.48: Which of the following is/are challenges and barriers to the digital divide?
(a) High cost
(b) Language barriers
(c) Technology barrier
(d) All of these
Correct Answer is Option (d)
There are various challenges and barriers to the digital divide as high cost, language barriers, technology barrier and Internet connectivity barrier.
Q.49: Which of the following is a term that describes the uneven distribution of information and communication technology (ICT) ?
(a) Digital divide
(b) e-Commerce
(c) Privacy
(d) Piracy
Correct Answer is Option (a)
Digital divide is a term that describes the uneven distribution of information and communication technology. It differences between rural and urban internet access.
Q.50: It differences between developed, developing and emerging nations in terms of the availability of Internet.
(a) Refund fraud
(b) Digital divide
(c) BBB online
(d) Privacy
Correct Answer is Option (b)
Digital divide differences between developed, developing and emerging nations in terms of the availability of internet.
|
363 docs|7 tests
|
FAQs on Class 10 Computer Application: CBSE Sample Question Paper- Term I (2021-22) - 3 - CBSE Sample Papers For Class 10
| 1. What is the structure of the Class 10 Computer Application exam according to the CBSE Sample Question Paper? |  |
| 2. How can students prepare effectively for the Class 10 Computer Application exam? |  |
| 3. What are some important topics covered in the Class 10 Computer Application syllabus? |  |
| 4. Are there any specific resources recommended for studying Computer Application for Class 10? |  |
| 5. What is the importance of practical exams in Class 10 Computer Application? |  |

















