Previous Year Questions: Network Layer Protocol | Computer Networks - Computer Science Engineering (CSE) PDF Download
Q1: Which one of the following CIDR prefixes exactly represents the range of IP addresses 10.12.2.0 to 10.12.3.255? (2024 SET 2)
(a) 10.12.2.0/23
(b) 10.12.2.0/24
(c) 10.12.0.0/22
(d) 10.12.2.0/22
Ans: (a)
Sol: As per the given data,
Range of IP Address = 10.12.2.0 to 10.12.3.255
Expanding the last two octets of these IP Addresses:
10.12.0000001 0.00000000
10.12.0000001 1.11111111
As you can see above, the 23-bit common prefix and the last 9 bits are all zeros to all ones.
10.12.2.0/23
Hence, the correct option is A.
Q2: Which of the following fields of an IP header is/are always modified by any router before it forwards the IP packet? (2024 SET 2)
(a) Source IP Address
(b) Protocol
(c) Time to Live (TTL)
(d) Header Checksum
Ans: (c, d)
Sol:
A) Source IP address remains unchanged as it identifies the original sender and is used for sending acknowledgement by destination or an ICMP message by router/destination.
B) Protocol indicates the type of data carried (e.g., TCP, UDP) and isn't altered by routers.
C) Time to Live(TTL) value is decremented by 1 by each router that forwards the packet.
D) As TTL value of IP header is changed by every router, corresponding Header Checksum is recalculated based on the new value of TTL.
So, correct options are C, D.
Q3: Node X has a TCP connection open to node Y. The packets from X to Y go through an intermediate IP router R. Ethernet switch S is the first switch on the network path between X and R. Consider a packet sent from X to Y over this connection. (2024 SET 2)
Which of the following statements is/are TRUE about the destination IP and MAC addresses on this packet at the time it leaves X?
(a) The destination IP address is the IP address of R
(b) The destination IP address is the IP address of Y
(c) The destination MAC address is the MAC address of S
(d) The destination MAC address is the MAC address of Y
Ans: (b)
Sol: Source IP address (public IP) and Destination IP address always remain unchanged throughout the journey of Packet from Node X to Node Y. The destination IP address is always that of Node Y.
(At destination, public destination IP address will be changed to private IP of receiving node due to NAT)
When the receiving node is outside the source node's local network, the source node sends packets to the default gateway (usually a router). In this case, the destination MAC address will be that of the router. The switch in the network simply forwards the packets along the path without altering their content.
Correct Answer: B
Q4: Consider sending an IP datagram of size 1420 bytes (including 20 bytes of IP header) from a sender to a receiver over a path of two links with a router between them. The first link (sender to router) has an MTU (Maximum Transmission Unit) size of 542 bytes, while the second link (router to receiver) has an MTU size of 360 bytes. The number of fragments that would be delivered at the receiver is _____ (2024 SET 1)
(a) 5
(b) 6
(c) 7
(d) 8
Ans: (b)
Sol: To determine the number of fragments that will be delivered to the receiver, we need to perform IP fragmentation based on the MTU sizes of the links. The IP datagram has a total size of 1420 bytes, including a 20-byte IP header, leaving us with a data payload of 1400 bytes.
The first link has an MTU of 542 bytes. Since the IP header is 20 bytes, the maximum data size that can be sent in one fragment is:
542 - 20 = 522 bytes
We need to calculate how many fragments are needed for the first link:
[1400 / 522] = [2.68]= 3 fragments
However, the payload size of 522 bytes must be a multiple of 8 (the fragment offset field is measured in units of 8 bytes). Adjusting the payload size:
522 / 8 = 65.25 ⇒ 65 x 8 = 520 bytes
So, each fragment data payload on the first link would be 520 bytes. Let's outline the fragmentation process for the first link:
First fragment:
20 bytes of IP header
520 bytes of data
Second fragment:
20 bytes of IP header
520 bytes of data
Third fragment:
20 bytes of IP header
remaining 360 bytes of data.
These three fragments will be examined by the router. Now, let’s consider the second link with an MTU of 360 bytes. After adding the IP header (20 bytes), the maximum data payload is:
360 - 20 =340bytes
To see how the first fragment (520 bytes) will be further fragmented:
[520 / 340] = [1. 53] =2 fragments
Fragment 1:
20 bytes of IP header
340 bytes of data
Fragment 2:
20 bytes of IP header
remaining 180 bytes of data
The second fragment (520 bytes) will be split in the same manner:
Fragment 3:
20 bytes of IP header
340 bytes of data
Fragment 4:
20 bytes of IP header
remaining 180 bytes of data
Finally, the third fragment's 360 bytes of data will be sent as one fragment:
Fragment 5:
20 bytes of IP header
340 bytes of data
Fragment 6:
20 bytes of IP header
20 bytes of data
Summarizing, the total number of fragments delivered at the receiver is the sum of all fragments processed through the router for the second link, which is 6 fragments.
Q5: Consider the entries shown below in the forwarding table of an P router. Each entry consists of an IP prefix and the corresponding next hop router for packets whose destination IP address matches the prefix. The notation "/N" in a prefix indicates a subnet mask with the most significant N bits set to 1. (2024 SET 1)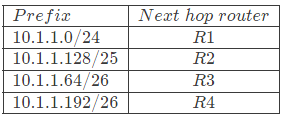
This router forwards 20 packets each to 5 hosts. The IP addresses of the hosts are 10.1.1.16, 10.1.1.72, 10.1.1.132, 10.1.1.191, and 10.1.1.205. The number of packets forwarded via the next hop router R2 is
(a) 40
(b) 20
(c) 10
(d) 5
Ans: (a)
Sol: In order to find how many packets are forwarded via the next hop router R 2 , first we need to check that how many hosts are passing through the subnet 10.1 .1 .128 / 25 .
In order to do that we need to do following steps:
- Find out the total range of all networks.
- Check in which range does the given host lie.
- If more than one networks are matching then select the network with longest prefix length i.e value of / N .
Range of all subnets in forwarding table is:
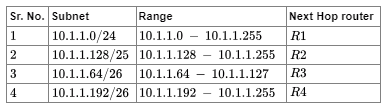 For host 10.1 .1 .16 , it lies in the range of subnet numbered 1 . So it will pass through router R 1 .
For host 10.1 .1 .16 , it lies in the range of subnet numbered 1 . So it will pass through router R 1 .
For host 10.1 .1 .72 , it lies in the range of subnets numbered 1 , 3 . But since prefix length of subnet 3 ( 26 ) is greater than subnet 1 ( 24 ) , the host ip address will pass through router R 3 .
For host 10.1 .1 .132 , it lies in the range of subnets numbered 1 , 2 . But since prefix length of subnet 2 ( 25 ) is greater than subnet 1 ( 24 ) , the host ip address will pass through router R 2 .
Similarly for host 10.1 .1 .191 , it will pass through router R 2 and for host 10.1 .1 .205 , it will pass through router R 4 .
In total 2 hosts have their next hop router as R 2 . So total number of packets transmitted through R 2 will be 40 .
Q6: Which of the following fields is/are modified in the IP header of a packet going out of a network address translation (NAT) device from an internal network to an external network? (2024 SET 1)
(a) Source IP
(b) Destination IP
(c) Header Checksum
(d) Total Length
Ans: (a, c)
Sol: NAT device takes the outgoing packet and replaces the source IP address from private address pool to a IP address from its public address pool.
Since the source IP address is changed, the header checksum will also be recalculated so that the router does not get error while checking the header checksum.
Answer: A, C
Q7: The forwarding table of a router is shown below. (2023)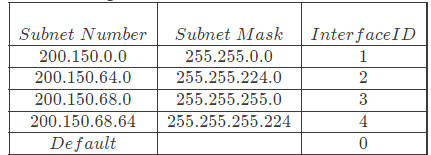
A packet addressed to a destination address 200.150.68.118 arrives at the router. It will be forwarded to the interface with ID _____.
(a) 1
(b) 2
(c) 3
(d) 4
Ans: (c)
Sol: As we know that when data packets arrived at the internal router, it will perform the following steps:
Find the first address/subnet id between the destination IP address and subnet mask using bitwise and operation.
after finding the first address 3 cases can be there:
If FA is matched with one subnet address then data is forwarded to the matched subnet address.
If FA is matched with more than one subnet address then data is forwarded to the interface corresponding to the largest subnet mask (maximum number of 1’s)
If FA is not matched with anyone then the data packet is forwarded to the default interface.
let’s check one by one:
(A): 200.150.68.118 ∧ 255.255.0.0
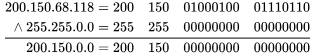
∴ subnet id= 200.150 .0 .0 ,matched
(B) 200.150.68.118 ∧ 255.255.224. 0
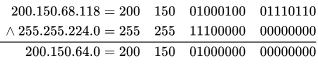 ∴ subnet id= 200.150 .64 .0 ,matched.
∴ subnet id= 200.150 .64 .0 ,matched.
(C) 200.150.68.118 ∧ 255.255.255.0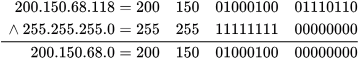 ∴ subnet id= 200.150 .64 .0 ,matched.
∴ subnet id= 200.150 .64 .0 ,matched.
(D) 200.150.68.118 ∧ 255.255.255.244
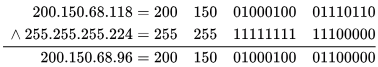
∴ subnet id= 200.150 .64 .96 ,not matched.
Since more than one subnet address is matched the data packet is forwarded to the interface corresponding to the largest subnet mask (a subnet mask having the maximum number of 1’s).
Here 255.255 .255 .0 has the maximum number of 1’s in binary representation among A, B, and C so the data packet is forwarded to the interface id 3 .
the correct answer is 3
Q8: Which of the following statements is/are INCORRECT about the OSPF (Open Shortest Path First) routing protocol used in the Internet? (2023)
(a) OSPF implements Bellman-Ford algorithm to find shortest paths.
(b) OSPF uses Dijkstra's shortest path algorithm to implement least-cost path routing
(c) OSPF is used as an inter-domain routing protocol
(d) OSPF implements hierarchical routing.
Ans: (a, c)
Sol: You need to know certain points about OSPF if you are GATE aspirant
- OSPF is an open standard, not related to any particular vendor.
- OSPF is hierarchical routing protocol, using area 0 (Autonomous System) at the top of the hierarchy.
- OSPF uses Link State Algorithm, and an OSPF network diameter can be much larger than that of RIP.
- OSPF supports Variable Length Subnet Masks (LSM)V, resulting in efficient use of networking resources.
- OSPF uses multicasting within areas.
- After initialization, OSPF only sends updates on routing table sections which have changed, it does not send the entire routing table, which in turn conserves network bandwidth.
- Using areas, OSPF networks can be logically segmented to improve administration, and decrease the size of routing tables.
Q9: Consider a network with three routers P, Q, R shown in the figure below. All the links have cost of unity. (2022)
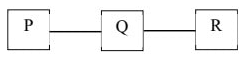
The routers exchange distance vector routing information and have converged on the routing tables, after which the link Q-R fails. Assume that P and Q send out routing updates at random times, each at the same average rate. The probability of a routing loop formation (rounded off to one decimal place) between P and Q, leading to count-to-infinity problem, is ____ (2022)
(a) 0.25
(b) 0.33
(c) 0.50
(d) 0.75
Ans: (c)
Sol: Answer : 0.5
Once Q-R fails then Q will immediately update its distance to R to ∞ . But P will still be having some finite value (which is 2).
Now it depends on P and Q, who is sending distance vector first.
if Q sends then system becomes stable immediately but if P sends first then it will be count to infinity. Please understand that count to infinity is not some wrong thing, it is just it takes some time to stable.
Since it is given in question that both have same average rate hence probability is also 1 / 2 that P sends first than Q. Hence the answer.
But we can calculate answer more mathematically considering that time is continuous variable.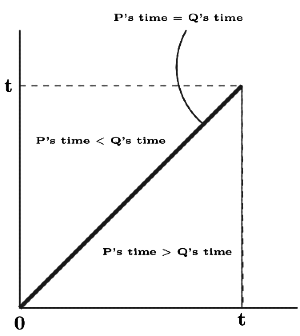
We are interested in probability represented by the shaded area,
which will be = Area of Tringle / Area of Square = 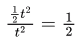
Method 2 OPTIONAL
Let X and Y be uniform random variables in [ 0 , t ] representing time for P and Q respectively.
We need to find P (X < Y ) = ?
P (X < Y ) = P (X ≤ Y) = P ( X ≤ k) ( Let Y = k)
P (X < Y ) =Can you continue from here ?.
Also refer Forouzan snapshot of count to infinity
Q10: Consider routing table of an organization's router shown below: (2022)
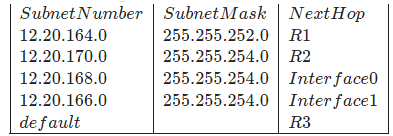
Which of the following prefixes in CIDR notation can be collectively used to correctly aggregate all of the subnets in the routing table?
[MSQ]
(a) 12.20.164.0/20
(b) 12.20.164.0/22
(c) 12.20.164.0/21
(d) 12.20.168.0/22
Ans: (b, d)
Sol: Given Routing Tables :
1. | 12.20.164.0 | 255.255.252.0 |
| 12.20.10100100.00000000 |
2. | 12.20.170.0 | 255.255.254.0 |
| 12.20.10101010.00000000 |
3. | 12.20.168.0 | 255.255.254.0 |
| 12.20.10101000.00000000 |
4. | 12.20.166.0 | 255.255.254.0 |
| 12.20.10101110.00000000 |
Subnet (2) and subnet (3) can be aggregated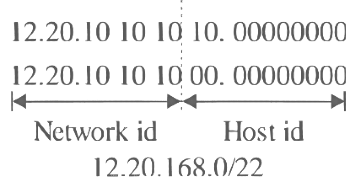 Subnet (1) and subnet (4) can be aggregated
Subnet (1) and subnet (4) can be aggregated 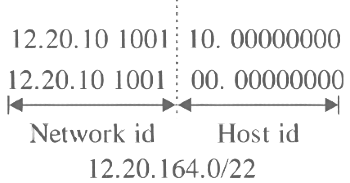
Hence the correct option is (B) and (D).
Q11: Consider an enterprise network with two Ethernet segments, a web server and a firewall, connected via three routers as shown below. (2022)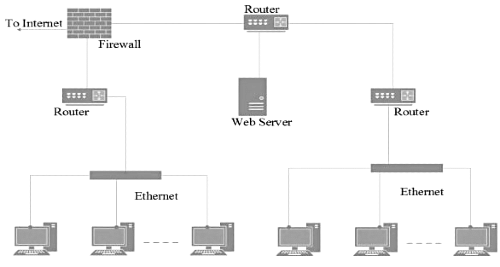
What is the number of subnets inside the enterprise network?
(a) 3
(b) 12
(c) 6
(d) 8
Ans: (c)
Sol: The correct answer is Option C: 6. Here's why:
To determine the number of subnets, we need to analyze the network addresses and subnet masks assigned to each segment. Let's break down the network configuration:
Segment 1:
Network Address: 192.168.1.0
Subnet Mask: 255.255.255.192
Segment 2:
Network Address: 192.168.2.0
Subnet Mask: 255.255.255.192
Segment 3 (Web Server):
Network Address: 192.168.3.0
Subnet Mask: 255.255.255.192
Subnet Calculation:
The subnet mask 255.255.255.192 provides a subnet mask of 232 -26 = 64 addresses.
Each of the three segments uses this subnet mask. Therefore, there are 6 subnets:
192.168.1.0/26
192.168.1.64/26
192.168.1.128/26
192.168.2.0/26
192.168.2.64/26
192.168.3.0/26
Q12: Consider a computer network using the distance vector routing algorithm in its network layer. The partial topology of the network is shown below. (2021 SET 2)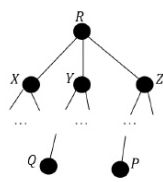
The objective is to find the shortest-cost path from the router R to routers P and Q. Assume that R does not initially know the shortest routes to P and Q. Assume that R has three neighboring routers denoted as X, Y and Z. During one iteration, R measures its distance to its neighbors X, Y, and Z as 3, 2 and 5, respectively. Router R gets routing vectors from its neighbors that indicate that the distance to router P from routers X, Y and Z are 7, 6 and 5, respectively. The routing vector also indicates that the distance to router Q from routers X, Y and Z are 4, 6 and 8 respectively. Which of the following statement(s) is/are correct with respect to the new routing table o R, after updation during this iteration?
[MSQ]
(a) The distance from R to P will be stored as 10
(b) The distance from R to Q will be stored as 7
(c) The next hop router for a packet from R to P is Y
(d) The next hop router for a packet from R to Q is Z
Ans: (b, c )
Sol: 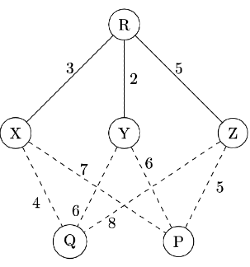
As per Distance Vector Routing Algorithm,
R to P = min { R − X − P , R − Y − P , R − Z − P } = min { 10 , 8 , 10 } = 8 through Y.
R to Q = min { R − X − Q , R − Y − Q , R − Z − Q } = min { 7 , 8 , 13 } = 7 through X .
Hence Options (B) and (C) are correct
Q13: An organization requires a range of IP address to assign one to each of its 1500 computers. The organization has approached an Internet Service Provider (ISP) for this task. The ISP uses CIDR and serves the requests from the available IP address space 202.61.0.0/17. The ISP wants to assign an address space to the organization which will minimize the number of routing entries in the ISP?s router using route aggregation. Which of the following address spaces are potential candidates from which the ISP can allot any one of the organization? (2020 )
I. 202.61.84.0/21
II. 202.61.104.0/21
III. 202.61.64.0/21
IV. 202.61.144.0/21
(a) I and II only
(b) II and III only
(c) III and IV only
(d) I and IV only
Ans: (b)
Sol: (B) II and III only
Given IP address space: 202.61 .0 .0 / 17 , 17 bits are in network ID bits(NID) and rest will be host ID bits(HID).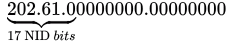
In order to assign 1500 hosts we need minimum 11 bits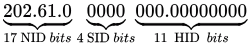 We have 4 subnet bits, eligible networks are those which belongs among possible 16 subnets.
We have 4 subnet bits, eligible networks are those which belongs among possible 16 subnets.
If we expand the given Network bits we can see:
- 202.61 . 84 .0 / 21 = 202.61 .0 1010 100.0
Not possible as all Host Bits should be zero - 202.61.104.0/21=202.61.01101000.0
Possible - 202.61.64.0/21=202.61.01000000.0
Possible - 202.61 . 144 .0 / 21 = 202.61 .1 0010 000.0
Not possible as 16 th bit from right (part of NID is 0 and not
Q14: Consider the following statements about the functionality of an IP based router. (2020)
I. A router does not modify the IP packets during forwarding.
II. It is not necessary for a router to implement any routing protocol.
III. A router should reassemble IP fragments if the MTU of the outgoing link is larger than the size of the incoming IP packet.
Which of the above statements is/are TRUE?
(a) I and II only
(b) I only
(c) II and III only
(d) II only
Ans: (d)
Sol: Taking the given statements one by one:
I. (FALSE) Router needs to fragment the incoming IP packets if the connecting line has smaller MTU (Maximum Transmission Unit) than size of incoming packets.
II. (TRUE) That's the case of static routing where forward paths are pre-loaded/downloaded to routers.
III. (FALSE) This is not possible in case of cut-through-switching where IP packet is forwarded as it arrives.
Q15: Consider three machines M, N and P with IP addresses 100.10.5.2, 100.10.5.5 and 100.10.5.6 respectively. The subnet mask is set to 255.255.255.252 for all the three machines. Which one of the following is true? (2019)
(a) M, N and P all belong to the same subnet
(b) Only M and N belong to the same subnet
(c) Only N and P belong to the same subnet
(d) M, N, and P belong to three different subnets
Ans: (c)
Sol: First derive the network address of those machines, then we can decide !
Finding network address for a M/C :- Perform Bitwise AND between m/c address and given subnet mask.
Subnet Mask: keep 1's in Network part + subnet part and keep 0's in Host part.
255.255 .255 .252 = 11111111.11111111 .11111111 .11111100
⟹ 24 ( from first 3 octets ) + 6 ( in last octet )
= 30 bits in Network+ subnet portion and last 2 bits represent the Host part .
Subnet Mask = 255.255 .255 .252 and M = 100.10 .5 .2 but keep all zero's in HOST part !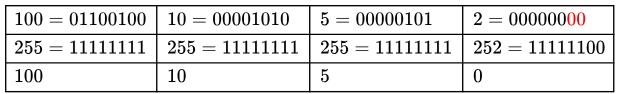 Subnet Mask = 255.255 .255 .252 and N = 100.10 .5 .5 but keep all zero's in HOST part !
Subnet Mask = 255.255 .255 .252 and N = 100.10 .5 .5 but keep all zero's in HOST part !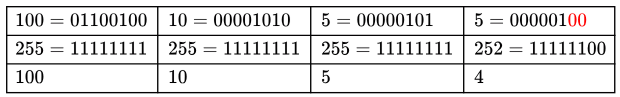 Subnet Mask = 255.255 .255 .252 and P = 100.10 .5 .6but keep all zero's in HOST part !
Subnet Mask = 255.255 .255 .252 and P = 100.10 .5 .6but keep all zero's in HOST part !
 ∴ only N and P are belong to same network (100.10.5.,4 / 30)
∴ only N and P are belong to same network (100.10.5.,4 / 30)
Q16: Consider an IP packet with a length of 4,500 bytes that includes a 20-byte IPv4 header and a 40-byte TCP header. The packet is forwarded to an IPv4 router that supports a Maximum Transmission Unit (MTU) of 600 bytes. Assume that the length of the IP header in all the outgoing fragments of this packet is 20 bytes. Assume that the fragmentation offset value stored in the first fragment is 0.
The fragmentation offset value stored in the third fragment is _______. (2018)
(a) 120
(b) 144
(c) 210
(d) 175
Ans: (b)
Sol: Packet Length = 4500 B
IP Payload =4500 - 20 = 4488 B
MTU = 600B
MTU Payload = 600B − 20 B = 580B
But payload should be multiple of 8 so number nearest to 580and multiple of 8 is 576, so MTU
payload = 576 B
IP Packet size = 576B + 20 B = 596 B
Size of Offset = 576 / 8 = 72
- 1 st fragment offset = 0
- 2 nd fragment offset = 72
- 3 rd fragment offset= 144
Q17: The maximum number of IPv4 router addresses that can be listed in the record route (RR) option field of an IPv4 header is _________. (2017 SET 2)
(a) 10
(b) 12
(c) 9
(d) none of above
Ans: (c)
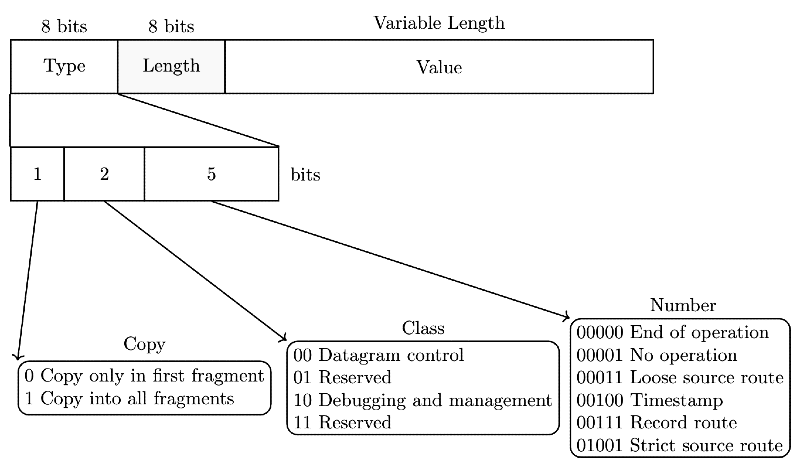
Sol: A record-route (RR) option is used to record the Internet routers that handle the datagram. It is listed in OPTIONS of IPv4.
According to RFC 791 , there are two cases for the format of an option:
- Case 1 : A single octet of option-type.
- Case 2 : An option-type octet, an option-length octet, and the actual option-data octets.
In both the cases, first 16 bits of OPTIONS field is used. Therefore, out off 40 Bytes only 38 Bytes
are remaining for storing IPv4 addresses. In 38 Bytes we can store 9 IPv4 addresses as each IPv4
address is of 4 Bytes.
∴ 9 should be answer.
Q19: Consider the following statements about the routing protocols, Routing Information Protocol (RIP) and Open Shortest Path First (OSPF) in an IPv4 network. (2017 SET 2)
I. RIP uses distance vector routing
II. RIP packets are sent using UDP
III. OSPF packets are sent using TCP
IV. OSPF operation is based on link-state routing
Which of the statements above are CORRECT?
(a) I and IV only
(b) I, II and III only
(c) I, II and IV only
(d) II, III and IV only
Ans: (c)
Sol: Statement 1 is CORRECT because RIP is one of the Oldest DVR(Distance Vector Routing) Protocols which employ the hop count as a routing metric.
Statement 2 is CORRECT because RIP uses the UDP as its transport protocol with port no 520.
Statement 3 is INCORRECT because OSPF does not use a transport protocol such as UDP or TCP but encapsulates its data directly into IP Packets.
Statement 4 is CORRECT because OSPF is a routing protocol which uses Link State Routing(LSR) and works within a single Autonomous System.
PS:
OSPF needs to perform reliable multicasting because it needs to talk to multiple possible neighbors on the same network segment. Now, TCP does not support multicast and UDP is not reliable Therefore, OSPF implements its own transport mechanism that allows both for reliability (acknowledgements and retransmissions of lost segments) and multicasting, bypassing both TCP and UDP.
Hence, Option C is CORRECT.
Q20: An IP datagram of size 1000 bytes arrives at a router. The router has to forward this packet on a link whose MTU (maximum transmission unit)is 100bytes. Assume that the size of the IP header is 20bytes.
The number of fragments that the IP datagram will be divided into for transmission is _________. (2016 SET 1)
(a) 10
(b) 13
(c) 14
(d) 12
Ans: (b)
Sol: IP Datagram size = 1000 B
MTU = 100 B
IP header size = 20 B
So, each packet will have 20 B header + 80 B payload.
Therefore, 80 × 12 = 960
now remaining 20 B data could be sent in next fragment.
So, total 12 + 1 = 13 fragments.
Q21: Which one of the following protocols is NOT used to resolve one form of address to another one? (2016 SET 1)
(a) DNS
(b) ARP
(c) DHCP
(d) RARP
Ans: (c)
Sol:
A) DNS - host name to IP address
B) ARP - IP to MAC
D) RARP - MAC to IP
So ANSWER is C
Q22: In the network 200.10.11.144/27, the fourth octet (in decimal) of the last IP address of the network which can be assigned to a host is ____________. (2015 SET 3)
(a) 176
(b) 175
(c) 159
(d) 158
Ans: (d)
Sol: Answer = 158
144 in binary = 10010000
out of this 3 bits in left are subnet bits. ( 27 bits are used for subnet, which means top 3 bytes and leftmost 3 bits from the last byte)
So, the 4 th octet in the last IP address of the network which can be assigned to a host is 100 11110 . (its not 100 11111 because its network broadcast address)
So, 10011110 is 158 in decimal.
Q23: Consider the following routing table at an IP router: (2015 SET 2)
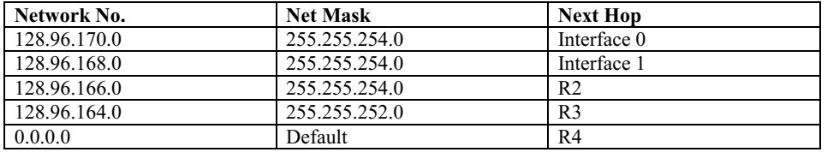
For each IP address in Group I identify the correct choice of the next hop from Group II using the entries from the routing table above.
(a) i-a, ii-c, iii-e, iv-d
(b) i-a, ii-d, iii-b, iv-e
(c) i-b, ii-c, iii-d, iv-e
(d) i-b, ii-c, iii-e, iv-d
Ans: (a)
Sol: Bitwise AND between 128.96 .171 .92 and 255.255 .254 .0 we get the subnet ID as follows: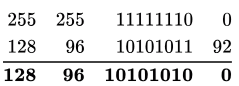
∴ Subnet ID = 128.96.170.0
∴ 128.96.171.92 will forward to interface 0
Taking the 2nd IP Address: 128.96.167.151
Bitwise AND between 128.96 .167.151 and 255.255 .254 .0 we get the subnet ID as follows: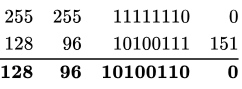
∴ Subnet ID = 128.96.166.0
∴ 128.96.167.151 will forward to interface R2
Taking the 3rd IP Address: 128.96.163.151
Bitwise AND between 128.96 .163.151 and 255.255 .254 .0 we get the subnet ID as follows: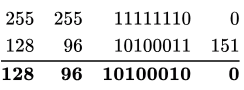
∴ Subnet ID = 128.96.162.0 (Doesn’t match with any given interface)
Bitwise AND between 128.96 .167.151 and 255.255 .254 .0 we get the subnet ID as follows: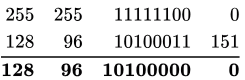
∴ Subnet ID = 128.96.160.0 (Doesn’t match with any given interface)
∴ 128.96.163.151 will forward to default interface R4
Taking the last IP Address: 128.96.164.121
Bitwise AND between 128.96 .164.121 and 255.255 .254 .0 we get the subnet ID as follows: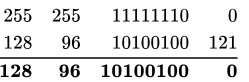
∴ Subnet ID = 128.96.164.0
∴ 128.96.167.151 will forward to interface R3
∴ Option (A) is the correct answer.
Q24: Which one of the following fields of an IP header is NOT modified by a typical IP router? (2051 SET 1)
(a) Checksum
(b) Source address
(c) Time to Live (TTL)
(d) Length
Ans: (b)
Sol: A router will not change the source address of the packet, rest of the given fields can be changed at the router.
Checksum: Checksum field changes at every router in correspondence with the change in values of other fields.
TTL (Time to Live): After every hop, the TTL field is reduced by one. Hence this field changes at every router.
Length: If fragment - apian is required length field will certainly change.
|
21 videos|145 docs|66 tests
|
FAQs on Previous Year Questions: Network Layer Protocol - Computer Networks - Computer Science Engineering (CSE)
| 1. What are the main functions of a network layer protocol? |  |
| 2. How does a network layer protocol differ from other layers in the OSI model? |  |
| 3. What are some examples of network layer protocols commonly used in computer networks? |  |
| 4. How does a network layer protocol handle fragmentation of data packets? |  |
| 5. What is the significance of the network layer protocol in ensuring end-to-end communication in a network? |  |
















