Previous Year Questions: Transport Layer Protocol | Computer Networks - Computer Science Engineering (CSE) PDF Download
Q1: Consider a TCP connection operating at a point of time with the congestion window of size 12 MSS (Maximum Segment Size), when a timeout occurs due to packet loss. Assuming that all the segments transmitted in the next two RTTs (Round Trip Time) are acknowledged correctly, the congestion window size (in MSS) during the third RTT will be _________ (2024 SET 2)
(a) 2
(b) 4
(c) 8
(d) 16
Ans: (b)
Sol: As per the given information, Congestion Window ( CWND ) = 12 MSS
Threshold = CWND/2 = 6 MSS
CWND = 1 MSS
Whenever TCP Congestion Control enters into a slow start phase (i.e. Congestion Window is less than the Threshold ), In case, when the segment is acknowledged, CWND increases by one, and CWND gets doubled at the end of all RTTs.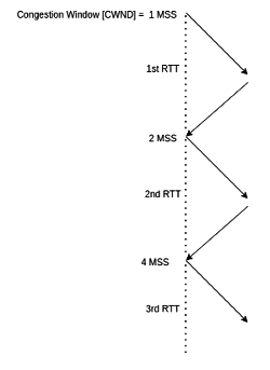
Hence, during the third RTT, the congestion window size will be 4.
Therefore, the correct answer is B.
Q2: Which of the following statements about IPv4 fragmentation is/are TRUE? (2024 SET 2)
(a) The fragmentation of an IP datagram is performed only at the source of the datagram
(b) The fragmentation of an IP datagram is performed at any IP router which finds that the size of the datagram to be transmitted exceeds the MTU
(c) The reassembly of fragments is performed only at the destination of the datagram
(d) The reassembly of fragments is performed at all intermediate routers along the path from the source to the destination
Ans: (b, c)
Sol: A. False.
Statement: The fragmentation of an IP datagram is performed only at the source of the datagram.
Fragmentation can occur at routers also.
B. False.
Statement: The fragmentation of an IP datagram is performed at any IP router which finds that the size of the datagram to be transmitted exceeds the MTU.
Fragmentation can indeed occur at any router along the path if the packet size exceeds the MTU, but it depends on whether the "Don't Fragment" flag is set in the IP header. If this flag is set, the router will not fragment the packet and will instead drop it, sending an ICMP "Fragmentation Needed" message back to the source.
C. True.
Statement: The reassembly of fragments is performed only at the destination of the datagram
Reassembly of fragments is typically performed only at the destination of the datagram. The destination is responsible for putting the fragments back together to reconstruct the original packet.
D. False.
Statement: The reassembly of fragments is performed at all intermediate routers along the path from the source to the destination.
Reassembly of fragments is not performed at intermediate routers along the path. Routers forward individual fragments based on their headers and do not reassemble them.
Q3: TCP client P successfully establishes a connection to TCP server Q. Let N P denote the sequence number in the SYN sent from P to Q. Let N Q denote the acknowledgement number in the SYN ACK from Q to P. Which of the following statements is/are CORRECT? (2024 SET 1)
(a) The sequence number N P is chosen randomly by P
(b) The sequence number N P is always 0 for a new connection
(c) The acknowledgement number N Q is equal to N P
(d) The acknowledgement number N Q is equal to N P + 1
Ans: (a, d)
Sol: In the context of a TCP connection establishment, understanding the roles of sequence and acknowledgment numbers is crucial. Let's analyze each option:
Option A: The sequence number NP is chosen randomly by P
This statement is correct. The sequence number N P in the SYN packet sent by client P is not fixed to any value but is chosen randomly. This randomness helps in ensuring security and reliability in the communication.
Option B: The sequence number NP is always 0 for a new connection
This statement is incorrect. The sequence number NP is not fixed at 0 for a new connection. As mentioned in Option A, it is chosen randomly.
Option C: The acknowledgement number NQ is equal to NP
This statement is incorrect. The acknowledgment number NQ in the SYN-ACK packet from server Q to client P is not equal to the sequence number NP . Instead, it acknowledges the receipt of the SYN packet from P.
Option D: The acknowledgement number NP is equal to NP + 1
This statement is correct. When server Q sends the SYN-ACK packet, it sets the acknowledgment number NQ to NP + 1 indicate that it has received the SYN packet from P and expects the next byte to be NP + 1 . This is a part of the TCP three-way handshake protocol.
Therefore, the correct statements are:
Option A: The sequence number NP is chosen randomly by P
Option D: The acknowledgement number NQ is equal to NP + 1
Q4: Suppose you are asked to design a new reliable byte-stream transport protocol like TCP. This protocol, named myTCP, runs over a 100 Mbps network with Round Trip Time of 150 milliseconds and the maximum segment lifetime of 2 minutes. (2023)
Which of the following is/are valid lengths of the Sequence Number field in the myTCP header?
(a) 30 bits
(b) 32 bits
(c) 34 bits
(d) 36 bits
Ans: (b, c, d)
Sol: The calculation of the sequence number field size is based on the maximum amount of data that can be in flight in the network. Since the maximum segment lifetime is 2 minutes (or 120 seconds), we need to calculate how much data can be sent over the network in this time.
Given the bandwidth of 100 Mbps, 1 second translates to 100*10^6 bits, or 125 * 10^5 bytes. Hence, in 120 seconds, we can send 15000 * 10^5 bytes.
The sequence number field needs to be large enough to assign a unique number to each byte that could be in flight. This means we need a field size that can represent up to 15000 * 10^5 bytes. Taking the base-2 logarithm of this number (to get the number of bits required to represent this many distinct values) and rounding up to the nearest integer (since we can't have a fraction of a bit), we find that we need at least 31 bits.
Therefore, the valid lengths for the sequence number field in the myTCP header are 32 bits, 34 bits, and 36 bits, corresponding to options B, C, and D
Q5: Consider the data transfer using TCP over a 1 Gbps link. Assuming that the maximum segment lifetime (MSL) is set to 60 seconds, the minimum number of bits required for the sequence number field of the TCP header, to prevent the sequence number space from wrapping around during the MSL is (2022)
(a) 31
(b)32
(c) 33
(d) 34
Ans: (c)
Sol: The given data,
Bandwidth = 1 Gbps =230/8 = bytes sec
Maximum segment lifetime (MSL) = 60 seconds.
Wrap around time = Total sequence number / Bandwidth.
Wrap around time > Maximum segment lifetime
Total sequence number / Bandwidth > Maximum segment life time.
Suppose, minimum number of bits required for the sequence number field = x.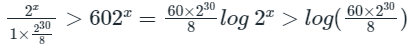 x> log 60 + log 230 - log 8
x> log 60 + log 230 - log 8
Minimum value of x = 30 + 5.9 - 3
Minimum value of x = 33.
Hence the correct answer is 33.
Q6: Consider the three-way handshake mechanism followed during TCP connection establishment between hosts P and Q. Let X and Y be two random 32-bit starting sequence numbers chosen by P and Q respectively. Suppose P sends a TCP connection request message to Q with a TCP segment having SYN bit =1, SEQ number =X, and ACK bit =0. Suppose Q accepts the connection request. Which one of the following choices represents the information present in the TCP segment header that is sent by Q to P? (2021 SET 2)
(a) SYN bit =1, SEQ number =X+1, ACK bit =0, ACK number =Y, FIN bit =0
(b) SYN bit =0, SEQ number =X+1, ACK bit =0, ACK number =Y, FIN bit =1
(c) SYN bit =1, SEQ number =Y, ACK bit =1, ACK number =X+1, FIN bit =0
(d) SYN bit =1, SEQ number =Y, ACK bit =1, ACK number =X, FIN bit =0
Ans: (c)
Sol: Host P sends the first SYN packet with S E Q number = X , S Y N flag = 1 and A C K flag = 0 as it’s a connection request.
Host Q will reply back with a SYN packet and acknowledging the arrival of P ′ s SYN packet.
Host Q will send a packet with SYN flag =1 , SEQ number = Y , to synchronize and establish the connection,
and ACK flag = 1 to acknowledge the P ′ s SYN packet, with ACK number = X+1 because ACK number denotes the sequence number of next expecting Byte.
Then P will reply back with an A C K packet to complete the three-way handshake. (not asked here)
F I N flag is used to terminate the connection, and will not be used here, FIN flag = 0 .
Hence C is correct.
Q7: Consider two hosts P and Q connected through a router R. The maximum transfer unit (MTU) value of the link between P and R is 1500 bytes, and between R and Q is 820 bytes. (2021 SET 1)
A TCP segment of size 1400 bytes was transferred from P to Q through R, with IP identification value as 0x1234. Assume that the IP header size is 20 bytes. Further, the packet is allowed to be fragmented, i.e., Don't Fragment (DF) flag in the IP header is not set by P.
Which of the following statements is/are correct?
[MSQ]
(a) Two fragments are created at R and the IP datagram size carrying the second fragment is 620 bytes.
(b) If the second fragment is lost, R will resend the fragment with the IP identification value 0x1234.
(c) If the second fragment is lost, P is required to resend the whole TCP segment.
(d) TCP destination port can be determined by analysing only the second fragment.
Ans: (a, c)
Sol: A is correct as you can follow the process of IPv4 fragmentation and you will get 620B fragments as described in the statement.
C is correct as fragmentation happened at the router and the sender has no way of knowing what kind of fragmentation occurred, so it will resend the whole TCP segment.
For B to be true, the original sender must retransmit the packet data in a datagram with the same IPv4 ID field as before, i.e.
0 X 1234. Take a look at RFC 1122 to see what they say about retransmitting with the same ID field (text below).
First of all, it says that retaining the ID field is optional. Secondly, it says that due to certain constraints, this is not practical, and therefore not believed to be useful (so it does not really happen in practice).
B’s statement implies that the router will definitely resend a fragment with
0 X 1234 ID, which can only happen if the sender resends the whole segment with the same ID number, but there is no such guarantee. Therefore B is false.
When sending an identical copy of an earlier datagram, a
host MAY optionally retain the same Identification field in
the copy.
Some Internet protocol experts have maintained that
when a host sends an identical copy of an earlier
datagram, the new copy should contain the same
Identification value as the original. There are two
suggested advantages: (1) if the datagrams are
fragmented and some of the fragments are lost, the
receiver may be able to reconstruct a complete datagram
from fragments of the original and the copies; (2) a
congested gateway might use the IP Identification field
(and Fragment Offset) to discard duplicate datagrams
from the queue.
However, the observed patterns of datagram loss in the
Internet do not favor the probability of retransmitted
fragments filling reassembly gaps, while other
mechanisms (e.g., TCP repacketizing upon
retransmission) tend to prevent retransmission of an
identical datagram [IP:9]. Therefore, we believe that
retransmitting the same Identification field is not
useful.
Q8: A TCP server application is programmed to listen on port number P on host S. A TCP client is connected to the TCP server over the network.
Consider that while the TCP connection was active, the server machine S crashed and rebooted. Assume that the client does not use the TCP keepalive timer. Which of the following behaviors is/are possible? (2021 SET 1)
[MSQ]
(a) If the client was waiting to receive a packet, it may wait indefinitely.
(b) The TCP server application on S can listen on P after reboot.
(c) If the client sends a packet after the server reboot, it will receive a RST segment.
(d) If the client sends a packet after the server reboot, it will receive a FIN segment
Ans: (a, b, c)
Sol: Option A is correct, because client doesn’t have a keepalive timer, and the server after a reboot forgets any connection with the client existed.
As for option C and D, option D is wrong because there is no reason for a FIN segment to be sent because there is no established connection which can be closed according to the recently rebooted server.
As for option C, scroll down to read the paragraph from page 35*** of the documentation, which proves that it is in fact correct.
Now, for option B, during the exam i reasoned that there is a distinction between a server machine being rebooted, and a tcp application/process being restarted.
For instance, whenever your computer crashes and reboots when you were browsing on google chrome (this was the case atleast a few years ago), did your computer automatically also restart the google chrome application? Obviously not.
There are some processes which the computer automatically starts on boot, but those are the exceptions and not the norm.
A client or server won’t simply restart its previous processes after a crash and reboot, unless it has been configured to do so, and nowhere in the question do i see that the server was a dedicated server running only the said tcp application.
The question asks what behaviour is possible on reboot. When such wording is used, it is natural to assume that it means what happens after the reboot without any external interference, human or otherwise. Because if we don’t assume this to be true, then a whole lot of things are possible after a system restarts.
An established connection is said to be "half-open" if one of the
TCPs has closed or aborted the connection at its end without the
knowledge of the other, or if the two ends of the connection have
become desynchronized owing to a crash that resulted in loss of
memory. Such connections will automatically become reset if an
attempt is made to send data in either direction. However, half-open
connections are expected to be unusual, and the recovery procedure is
mildly involved.
If at site A the connection no longer exists, then an attempt by the
user at site B to send any data on it will result in the site B TCP
receiving a reset control message. Such a message indicates to the
site B TCP that something is wrong, and it is expected to abort the
connection.
Assume that two user processes A and B are communicating with one
another when a crash occurs causing loss of memory to A's TCP.
Depending on the operating system supporting A's TCP, it is likely
that some error recovery mechanism exists. When the TCP is up again,
A is likely to start again from the beginning or from a recovery
point. As a result, A will probably try to OPEN the connection again
or try to SEND on the connection it believes open. In the latter
case, it receives the error message "connection not open" from the
local (A's) TCP. In an attempt to establish the connection, A's TCP
will send a segment containing SYN. This scenario leads to the
example shown in figure 10.
The highlighted words indicate that it isn’t always necessary that the tcp process will restart after a crash, and that it is dependent upon the operating system.
Given that we don’t know what the TCP process is exactly, it could as well be an unimportant process on a non well-known port, which was used for a private connection between the client and the server, which has no specific reason to restart after the server reboots.
And until and unless the process restarts, it won’t start listening on its configured port number.
Q10: Consider a TCP connection between a client and a server with the following specifications; the round trip time is 6 ms, the size of the receiver advertised window is 50 KB, slow-start threshold at the client is 32 KB, and the maximum segment size is 2 KB. The connection is established at time t=0. Assume that there are no timeouts and errors during transmission. Then the size of the congestion window (in KB) at time t+ 60 ms after all acknowledgements are processed is _______ (2020)
(a) 22
(b) 44
(c) 18
(d) 36
Ans: (b)
Sol: In Case of AIMD(Additive Increase/ Multiplicative Decrease): -
- Start with given MSS (Min Sequence Size)
- Increase the window size in multiples of MSS till the slow start threshold occurs
- Once the threshold reached, increase the window size by 1 MSS till the timeout occurs
- Once the timeout occurs, reduce threshold to half of current window size and again start from given start MSS.
t = 0
1 MSS = 2 KB
W threshold = 32 KB
|→ denotes 1RTT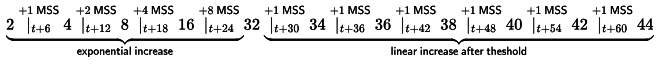
∴ The size of the congestion window(in KB) at time t + 60 ms after all acknowledgments are processed is 44 KB
Q11:Consider the following statements regarding the slow start phase of the TCP congestion control algorithm. Note that
cwnd stands for the TCP congestion window and MSS denotes the Maximum Segment Size. (2018)
(i) The cwnd increases by 2 MSS on every successful acknowledgment.
(ii) The cwnd approximately doubles on every successful acknowledgement.
(iii) The cwnd increases by 1 MSS every round trip time.
(iv) The cwnd approximately doubles every round trip time.
Which one of the following is correct?
(a)Only (ii) and (iii) are true
(b) Only (i) and (iii) are true
(c) Only (iv) is true
(d) Only (i) and (iv) are true
Ans: (c)
Sol: Each time an A C K is received by the sender, the congestion window is increased by 1 segment:
C W N D = C W N D + 1 .
C W N D increases exponentially on every R T T .
Hence, correct answer is C.
Q12: Match the following: (2018)

(a) P-III, Q-IV, R-II, S-I
(b) P-II, Q-I, R-IV, S-III
(c) P-IV, Q-I, R-II, S-III
(d) P-IV, Q-I, R-III, S-II
Ans: (c)
Sol: UDP header - 16 bits
MAC address: 48 bits
IPv6 next header: 8 bits
TCP Sequence No.: 32 bits
Answer: (C) P:IV, Q:I, R:II, S:III
Q13: Consider socket API on a Linux machine that supports connected UDP sockets. A connected UDP socket is a UDP socket on which connect function has already been called. Which of the following statements is/are CORRECT ? (2017 SET 2)
I. A connected UDP socket can be used to communicate with multiple peers simultaneously.
II. A process can successfully call connect function again for an already connected UDP socket.
(a) I only
(b) II only
(c) Both I and II
(d) Neither I nor II
Ans: (b)
Sol: Calling connect Multiple Times for a UDP Socket
A process with a connected UDP socket can call connect again for that socket for one of two reasons:
- To specify a new IP address and port
- To un connect the socket
The first case specifying a new peer for a connected UDP socket differs from the use of connect with a TCP socket. Connect can be called only one time for a TCP socket. To un connect a UDP socket. we call Connect but set the family member of the socket address structure to AT_UNSPEC .
Also, a UDP client or server can call Connect only if that process uses the UDP socket to communicate with exactly one peer.
So, option B should be the answer
Q14: Consider a TCP client and a TCP server running on two different machines. After completing data transfer, the TCP client calls close to terminate the connectional and a FIN segment is sent to the TCP server. Server-side TCP responds by sending an ACK which is received by the client-side TCP. As per the TCP connections state diagram (RFC 793), in which state does the client-side TCP connection wait for the FIN from the sever-side TCP? (2017 SET 1)
(a) LAST-ACK
(b) TIME-WAIT
(c) FIN-WAIT-1
(d) FIN-WAIT-2
Ans: (d)
Sol: After completing the data transfer, the TCP client executes a close primitive, and a FIN segment is sent to the TCP server by the client and wait for the corresponding ACK from the server. After this, two cases will happen:
1) When the ACK arrives from the server, a transition is made to state FIN-WAIT 2 by the client and then one direction of the connection will be closed. When other side closes too, a FIN comes in which is acknowledged and both sides will be closed.
2) In second case, instead of getting ACK from server till the time-out, TCP client received FIN from server. Client will acknowledge this FIN and then it will move to the close state. TCP client will wait for the ACK for its own FIN from server. After receiving ACK, TCP client will move to the TIME-WAIT state.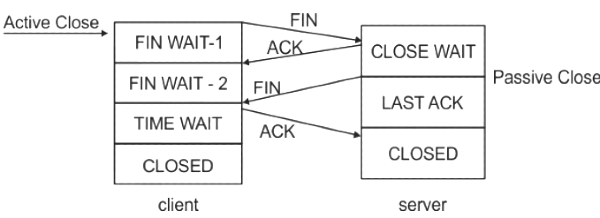
Q15: For a host machine that uses the token bucket algorithm for congestion control, the token bucket has a capacity of 1 megabyte and the maximum output rate is 20 megabytes per second. Tokens arrive at a rate to sustain output at a rate of 10megabytes per second. The token bucket is currently full and the machine needs to send 12megabytes of data. The minimum time required to transmit the data is _____seconds (2016 SET 1)
(a) 0.6
(b) 1.1
(c) 2.5
(d) 2.9
Ans: (b)
Sol: Initially token bucket is full.
Rate at which it is emptying is ( 20 − 10 ) MBps.
Time taken to empty token bucket of 1 MB is 1/ 10 i.e 0.1 sec.
Data send in this time is 0.1 ∗ 20 = 2 MB (rate at which bucket is emptying is different from rate at which data is send) .
Data left to send is 12 − 2 = 10 MB .
Now bucket is empty and rate of token arriving is less than that of going out so effective data speed will be 10 MBps.
Time to send remaining 10 MB will be 1 sec. So total time is 1 + 0.1 = 1.1 sec
Q16: Consider the following statements. (2015 SET 3)
I. TCP connections are full duplex
II. TCP has no option for selective acknowledgement
III. TCP connections are message streams
(a) Only I is correct
(b) Only I and III are correct
(c) Only II and III are correct
(d) All of I, II and III are correct
Ans: (a)
Sol: Transmission Control Protocol (TCP):
- TCP is a reliable connection-oriented protocol that can be used in any application where reliability is important.
- TCP explicitly defines to provide a connection establishment, data transfer, and connection teardown phases to provide a connection-oriented service.
- TCP connections are full-duplex
- TCP uses GBN and SR protocols to attain reliability. Therefore it has selective acknowledgment.
- It provides end-to-end communication due to the port number of source and destination.
- TCP connections are byte streams.
Hence statement I is correct
Q17: Assume that the bandwidth for a TCP connection is 1048560 bits/sec. Let α α be the value of RTT in milliseconds (rounded off to the nearest integer) after which the TCP window scale option is needed. Let β be the maximum possible window size with window scale option. Then the values of α and β are (2015 SET 2)
(a) 63 milliseconds, 65535 x 2 14
(b) 63 milliseconds, 65535 x 2 16
(c) 500 milliseconds, 65535 x 2 14
(d) 500 milliseconds, 65535 x 2 16
Ans: (c)
Sol: In TCP when the bandwidth-delay product increases beyond 64K receiver window scaling is needed.
The bandwidth-delay product is the maximum amount of data on the network circuit at any time and is measured as RTT * Bandwidth. This is not the time for sending data rather just the time for sending data without acknowledgement.
So, here, we have bandwidth delay product = (1048560 / 8) B * a = 64K
a = (64 k * 8 ) / 1048560 = 0.5 s = 500 milliseconds
Q18: Host A sends a UDP datagram containing 8880 bytes of user data to host B over an Ethernet LAN. Ethernet frames may carry data up to 1500 bytes (i.e. MTU=1500 bytes). Size of UDP header is 8 bytes and size of IP header is 20 bytes. There is no option field in IP header. How many total number of IP fragments will be transmitted and what will be the contents of offset field in the last fragment? (2015 SET 2)
(a) 6 and 925
(b) 6 and 7400
(c) 7 and 1110
(d) 7 and 8880
Ans: (c)
Sol: Number of fragments = [8888 / 1480 ] = 7
Offset of last fragment = (1500 - 20) x 6 / 8 = 1110
So, here, we have bandwidth delay product(scaling factor of 8 is used in offset field).
TCP or UDP header will be added to the DataUnit received from Transport Layer to Network Layer. And fragmentation happens at Network Layer. So no need to add TCP or UDP header into each fragment.
Q19: Suppose two hosts use a TCP connection to transfer a large file. Which of the following statements is/are FALSE with respect to the TCP connection? (2015 SET 1)
I. If the sequence number of a segment is m, then the sequence number of the subsequent segment is always m+1.
II. If the estimated round trip time at any given point of time is t sec, the value of the retransmission timeout is always set to greater than or equal to t sec.
III. The size of the advertised window never changes during the course of the TCP connection.
IV. The number of unacknowledged bytes at the sender is always less than or equal to the advertised window.
(a) III only
(b) I and III only
(c) I and IV only
(d) II and IV only
Ans: (b)
Sol: III. False. It is the size of the receiver's buffer that's never changed. RcvWindow is the part of the receiver's buffer that's changing all the time depending on the processing capability at the receiver's side and the network traffic.
Powered by Froala Editor
|
21 videos|145 docs|66 tests
|
FAQs on Previous Year Questions: Transport Layer Protocol - Computer Networks - Computer Science Engineering (CSE)
| 1. What is the purpose of a transport layer protocol? |  |
| 2. What are some examples of transport layer protocols commonly used in networking? |  |
| 3. How does TCP ensure reliable data transmission? |  |
| 4. What is the difference between TCP and UDP? |  |
| 5. Why is the transport layer important in networking? |  |





















