Information and Communication Technology Skills Chapter Notes | Artificial Intelligence for Class 10 PDF Download
| Table of contents |

|
| Session 1: Basic Computer Operations |

|
| Session 2: Performing Basic File Operations |

|
| Session 3: Computer Care and Maintenance |

|
| Session 4: Computer Security and Privacy |

|
Session 1: Basic Computer Operations
What is ICT?
ICT stands for Information and Communication Technology. ICT refers to all the methods, tools, concepts related to storing, recording and sending digital information.
Computer Hardware and Software

A computer system consists of two main parts — the hardware and the software. The physical parts that we can see, and touch are called hardware. Another important part is known as software which we can see but we cannot touch it.
What is Operating System?
The most important software in any computer is the Operating System (OS). When we start computer the first software display on the desktop is operating system. Some of the most commonly used operating systems for laptops and desktop are Ubuntu, Microsoft Windows and Mac OS.
How to start and shutdown the computer?
To start a computer, click on Power button on the CPU. This will start the operating system of your computer and display main screen of the monitor.
a. Basic Functions performed when a computer starts
When you start a computer, automatically computer will run a basic program called BIOS (Basic Input/Output System). The BIOS first does a self-test. If the self-test shows that the system is fine, the BIOS will load the Operating System.
b. Login and Logout
Login and Logout is used to protect your computer from unauthorised person. To make sure your computer is locked, you have login-IDs and passwords.
c. Shutting Down a computer
When you click Shut down button, the Operating System will safely close all the applications and turn off the computer.
Using the Keyboard
A keyboard is an input device used to type text, numbers and commands into the computer.
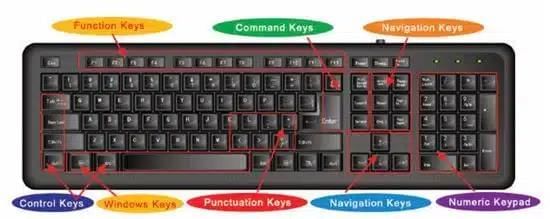
Some of the important keys of Keyboard are –
- Function Keys: Keys from F1 to F12 is known as function key which perform specific functions.
- Control keys: Keys, such as Control (CTRL), SHIFT, SPACEBAR, ALT, CAPS LOCK and TAB, are special control keys that perform special functions.
- Enter key: The key can be either ENTER or RETURN, you use the ENTER or the RETURN key to move the cursor to the beginning of a new line.
- Punctuation keys: Punctuation keys include keys for punctuation marks, such as colon (:), semicolon (;), question mark (?), single quotation marks (‘ ’), and double quotation marks (“ ”).
- Navigation keys: Keys, such as the arrow keys, HOME, END, PAGE UP, and PAGE DOWN are navigation keys. These are used to move up and down, right and left in a document. The HOME and END keys move the cursor to the left/right end of a line of text, respectively.
- Command keys: Keys, such as INSERT (INS), DELETE (DEL), and BACKSPACE are command keys. When the INSERT key is turned ON, it helps you overwrite characters to the right of the cursor. The DELETE key and the BACKSPACE key are used to remove typed text.
- Windows key: Pressing this key opens the Start menu.
Using a Mouse
The mouse is small device that you can use to move, select and open items on your computer screen.
- Roll Over or Hover
- Point and Click
- Drag and Drop
- Double-click
Session 2: Performing Basic File Operations
Creating and managing files and folders
- Files: In computer, information are stored in files, every file having a file name and extension. The file name and file name extension are separated by a period or a ‘dot’. for example, if you store information in Notepad and file name is school then notepad extension will be .txt and it will look like “school.txt”.
- Folder: A folder is a location where a group of files can be stored.
Session 3: Computer Care and Maintenance
Importance of Care and Maintenance of Computers
When we take good care of computer on a regular basis, we can use them for a longer time. This will help us save money as we do not need to buy new devices too often.
Basic Tips for Taking Care of Devices
Here are some simple ways that you can follow to take care of your computer.
Keeping a Device Clean
- You can clean a keyboard with a soft brush and remove crumbs and dust particles.
- You can wipe the screen with a soft cloth to remove any finger marks.
- Be careful with food and drinks and avoid eating and keeping glasses of water or cups of coffee near a computer
- Handle devices carefully and avoid dropping or banging it against a hard surface.
- Keep the computer, mobile device cool and avoid leaving a device in the sun.
- Do not overcharge your battery
- Always plug in devices carefully
- Do not run too many programs at a time
Prepare a Maintenance Schedule
We need a plan or a schedule for maintenance of the computer –
(a) Daily Maintenance
- Clean up your e-mail inbox
- Download e-mail attachments and save in proper folders
(b) Weekly Maintenance
- Clean your keyboard
- Clean your monitor
- Dust CPU and printer
- Backup your data to an external drive
(c) Monthly Maintenance
- Transfer photographs to computer and delete from drive
- Organise photos into folders or albums
- Clean up ‘Download’ folder
- Uninstall unused programs and apps
- Run disk-cleaner software
- Run full system virus scan
Backup Your Data
Backup means to save the data present on your computer on another device, such as CD/DVD
drives or hard disk. This data can recover using backup when the computer stops working.
Scanning and Cleaning Viruses
Computer virus can affect the computer system performance and data; to protect the computer we can install anti-virus software.
Increasing Computer Performance
When we are using computer for a long time then lot of unnecessary files and data stored in computer automatically, this unnecessary file is called temporary files which decrease the performance of computer. Try to keep clean this type of temporary files using disk cleaner software or deleting temporary file directly from the “temporary folder”.
Removing SPAM from your Computer
Sometimes we get unwanted emails from companies who are advertising a product or trying to attract you to their website. Such mails are called SPAM. Set email filters in the settings to prevent SPAM from entering our mailbox.
Session 4: Computer Security and Privacy
We are keeping our personal information in our computer, so, it is essential to keep computers secure and our data safe. If any of this information gets lost or leaked and falls into the wrong hands, it can cause a lot of harm to the people.
Computer Security Deals with Protecting Computers
Protecting Computer against Viruses
Computer security and privacy deals with the measures used to prevent loss of data.
Reasons for Security Break – Security break is leakage of information, personal information can be lost or leaked in two ways:
- We are not careful in giving out personal information over the Internet. For example, we share our account details and password on unsecure sites.
- A person gets unauthorised access to our computer. This can happen in the office if we leave are computer without logging out.
Threats to Computer
Threats are the ways in which personal information can be leaked from a computer without our knowing.
(a) Theft: Theft means stealing of information or hardware. These maybe of three types:
- Physical: Where a person may steal your desktop computer or laptop.
- Identity: Where a hacker steals your personal information and using this information as a false identity.
- Software Piracy: This is stealing of software and includes using or distributing unlicensed and unauthorised copies of a computer program or software.
(b) Virus: Viruses are computer programs that can damage the data and software programs or steal the information stored on a computer. Major types of viruses are Worms and Trojan Horse.
- Worms: These are viruses that replicate themselves and spread to all files is known as Worms virus. This type of virus is very difficult to remove from computer.
- Trojan Horse: A Trojan Horse appears as a useful software program, but once it reaches a computer it starts behaving like a virus and destroying data or transferring data from one computer to another computer.
- Online Predator: Online predators are people who trap you into inappropriate relationships. This type of online predator can do bullying you into doing illegal activities.
- Internet Scams: Sometimes you are receiving offers in email or in WhatsApp, they are offering attractive prizes or saying you won a huge money in a lottery, these types of offers are known as Internet Scams.
Protecting your Data
To protect our data from theft and viruses we can take the following measures –
- Use passwords to login to your computer: Use passwords that are difficult to guess. for example, using small letter, capital letters, numbers and special characters in the password.
- Install Anti-virus and Firewall: Anti-viruses and firewalls helps to monitor the data and prevent your computer from viruses and from hackers.
- Encrypt Data: Banks and Companies encrypt their data using Windows (BitLocker) or using any other data encrypt software and preventing their data from unauthored usage using password.
- Secure sites: Always try to check https:// and lock symbol in browser when every you are purchasing or transfer your money on the Internet using Credit Card or Debit Card. HTTPS helps to transfer the data in secure manner.
|
22 videos|68 docs|11 tests
|
FAQs on Information and Communication Technology Skills Chapter Notes - Artificial Intelligence for Class 10
| 1. What are the basic operations that can be performed on a computer? |  |
| 2. How can I perform basic file operations on my computer? |  |
| 3. What are some essential practices for computer care and maintenance? |  |
| 4. How can I ensure my computer's security and privacy? |  |
| 5. Why is understanding Information and Communication Technology (ICT) skills important? |  |















