MEDIUM ACCESS CONTROL
This algorithm is commonly called the Ethernet‟s media access control (MAC). It is typically implemented in hardware on the network adaptor.
FRAME FORMAT:
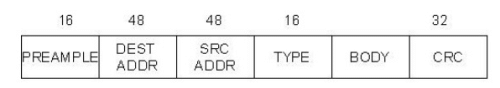
Preamble allows the receiver to synchronize with the signal. Both the source and destination hosts are identified with a 48-bit address. Each frame contains up to 1,500 bytes of data. A frame must contain at least 46 bytes of data, even if this means the host has to pad the frame before transmitting it. Each frame includes a 32-bit CRC.
ADDRESSES:
It is usually burned into ROM. Ethernet addresses are typically printed in a form humans can read as a sequence of six numbers separated by colons.
Each number corresponds to 1 byte of the 6-byte address and is given by a pair of hexadecimal digits, one for each of the 4-bit nibbles in the byte; leading 0s are dropped.
To ensure that every adaptor gets a unique address, each manufacturer of Ethernet devices is allocated a different prefix that must be prep-ended to the address on every adaptor they build.
UNICAST
MULTICAST
BROADCAST
TRANSMITTER ALGORITHM:
The receiver side of the Ethernet protocol is simple; the real smarts are implemented at the sender‟s side. The transmitter algorithm is defined as follows:
When the adaptor has a frame to send and the line is busy, it waits for the line to go idle and then transmits immediately.
The Ethernet is said to be a 1-persistent protocol because an adaptor with a frame to send transmits with probability 0<=p<=1 after a line becomes idle, and defers with probability q=1-p. Because there is no centralized control it is possible for two (or more) adaptors to begin transmitting at the same time, either because both found the line to be idle or because both had been waiting for a busy line to become idle.
When this happens, the two (or more) frames are said to collide on the network. Each sender, because the Ethernet supports collision detection, is able to determine that a collision is in progress. At the moment an adaptor detects that is frame is colliding with another, it first makes sure to transmit a sure to transmit a 32-bit jamming sequence and then stops the transmission.
Thus, a transmitter will minimally send 96 bits in the case of a collision: 64-bit preamble plus 32-bit jamming sequence. One way that an adaptor will send only 96-bits which is sometimes called a runt frame is if the two hosts are close to each other. Had the two hosts been farther apart, they would have had to transmit longer, and thus send more bits, before detecting the collision.
In fact, the worst-case scenario happens when the two hosts are at opposite ends of the Ethernet. To know for sure that the frame it just sent did not collide with another frame, the transmitter may need to send as many as 512 bits.
Not coincidentally, every Ethernet frame must be at least 512 bits (64 bytes)long: 14 bytes of header plus 46 bytes of data plus 4 bytes of CRC.
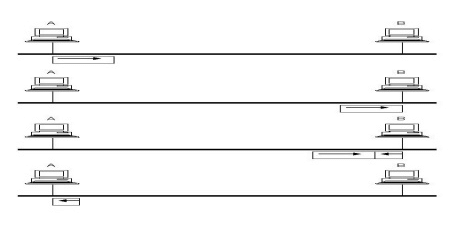
Where hosts A and B are at opposite ends of the network. Suppose host A begins transmitting a frame at time t, as shown in (a). it takes it one link latency (let‟s denote the latency as d) for the frame to reach host B.
Thus, the first bit of A‟s frame arrives at B at time t+d, as shown in (b). Suppose an instant before host A‟s frame arrives (i.e., B still sees and idle line), host B begins to transmit its own frame.
B‟s frame will immediately collide with A‟s frame, and this collision will be detected by host B(c). host B will send the 32-bit jamming sequence, as described above.(B‟s frame will be a runt).
Unfortunately, host A will not know that the collision occurred until B‟s frame reaches it, which will happen one link latency later, at time t+2xd, as shown in (d). Host A must continue to transmit until this time in order to detect the collision. In other words, host A must transmit for 2xd should be sure that it detects all possible collisions.
Considering that a maximally configured Ethernet is 2,500 m long, and that there may be up to four repeaters between any two hosts, the round-trip delay has been determined to be 51.2 microseconds, which on a 10-Mbps Ethernet corresponds to 512 bits.
The other way to look at this situation is that we need to limit the Ethernet‟s maximum latency to a fairly small value (e.g., 512micro seconds) for the access algorithm to work; hence, an Ethernet‟s maximum length must be something on the order of 2,500m.
Once an adaptor has detected a collision and stopped its transmission, it waits certain amount of time and tries again. Each time it tries to transmit but fails, the adaptor doubles the amount of time it waits before trying again.
This strategy of doubling the delay interval between each retransmission attempt is a general technique known as exponential back off. More precisely, the adaptor first delays either 0 or 51.2 microseconds, selected at random. If this effort fails, it then waits 0, 51.2, 102.4, or 153.6 microseconds (selected randomly) before trying again; this is kx51.2 for k=0...2^3-1, again selected at random.
In general, the algorithm randomly selects a k between 0 and 2^n-1 and waits kx51.2 microseconds, where n is the number of collisions experienced so far. The adaptor gives up after a given number of tries and reports a transmit error to the host. Adaptor typically retry up to 16 times, although the back off algorithm caps n in the above formula at 10.