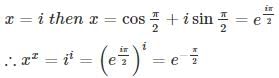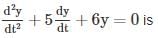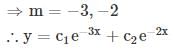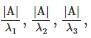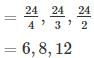Full Test 2 - EKT CSE - AFCAT MCQ
30 Questions MCQ Test - Full Test 2 - EKT CSE
Two trains 120 m and 80 m in length are running in opposite directions with velocities 42 kmph and 30 kmph. In what time they will cross each other?
What should be the velocity of a sound source moving towards a stationary observer so that apparent frequency is double the actual frequency (Velocity of sound is v)
| 1 Crore+ students have signed up on EduRev. Have you? Download the App |
A man can see clearly upto a distance of 2 m and not more than that. What will be the power of lens he should use for clear vision?
Wavelength and frequency are related as: (c = speed of light)
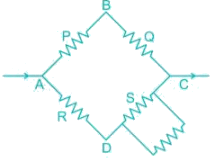
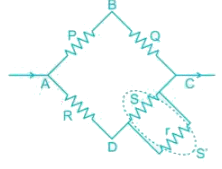
In Wheatstone's bridge P = 9 ohm, Q = 11 ohm, R = 4 ohm and S = 6 ohm. How much resistance must be put in parallel to the resistance S to balance the bridge
In an iso-thermal process, the internal energy of gas molecules ________.
Which of the following has same representation for +0 and -0 ?
What is the output of the following code fragment ?
#include
int main()
{
char ch;
printf(“%d”, sizeof(ch));
return 0;
}
A list of a finite number of homogeneous data elements is known as?
Which layer of international standard organization’s OSI model is responsible for creating and recognizing frame boundaries?
Electronic mail, Electronic messaging and Browsing the World Wide Web are functionality of which of the following layers?
What is the output of the following program ?
#include <stdio.h>
main()
{
int a , b;
a = 10;
printf(“%d”,(a == 1) ? 20: 30 );
printf(“%d”,(a == 10) ? 20: 30 );
}
For the function f(x) = x2e-x, where x ∈ [0,2]; the maximum value occurs when x is equal to
If 4,3,24,3,2 are the Eigen values of AA. Then find the Eigen values of Adj(A)Adj(A) if detA=24



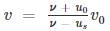
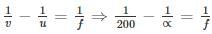
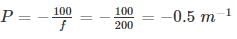
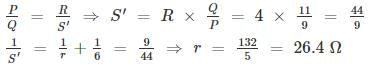
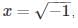 then the value of xx is
then the value of xx is