Computer Science: CUET Mock Test - 7 - Humanities/Arts MCQ
30 Questions MCQ Test - Computer Science: CUET Mock Test - 7
The Programming language Python is named after:
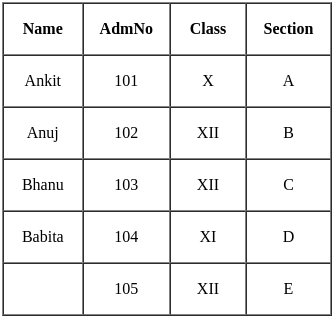
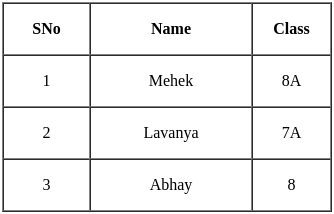
Identify primary key in the given table student:
If a table has 5 tuples and 7 attributes, then what will be the degree and cardinality of the table?
Find the output:
s = "CuEt #2022"
f = open("new.Txt", "w+")
f.write(s)
f.seek(0)
c = f.read(9)
for i in c:
if i.isupper():
print(i.lower(), end="#")
elif i.islower():
print(i.upper(), end="#")
elif int(i).isdigit():
print(int(i)+1, end="#")
else:
print("$", end="#")
f.close()
Consider the table given below.

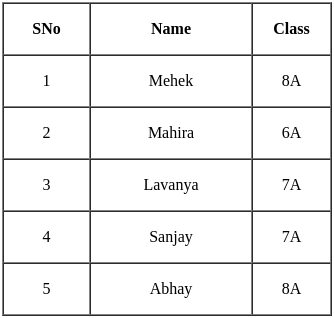
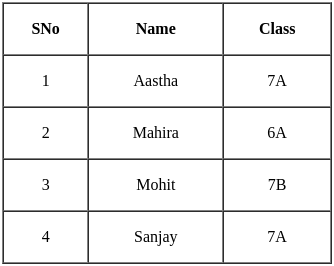
Identify the operation applied to the given tables to get the given output
Consider the given text file 'pledge.txt'

f=open('pledge.txt', 'r') #Statement 1
ine = f.readlines() #Statement 2
print(len(line)) #Statement 3
f.close() #Statement 4
Identify the correct output, will be given by statement 3.
Consider the following statements related to stacks and queues and choose the option that correctly identifies their validity.
- In a stack, the operation to remove an item is called "enqueue," while in a queue, it is called "dequeue."
- A queue follows the FIFO (First In, First Out) principle, allowing elements to be added at one end and removed from the other.
- The "push" operation is utilized in both stacks and queues for adding elements.
What is the output produced by following output code
def test():
try:
return 0
except:
print('error')
finally:
return 2
obj=test()
print(obj)
A relational database, which is in 3NF, may have undesirable data redundancy because there may exist
____ constraints apply only to individual column.
Which of the following options is not correct?
Study the following program:
x = 1
while true:
if x % 5 = = 0:
break
print(x)
x + = 1
What will be the output of this code?
A perfect hash function maps every input key to a unique index in the hash table. If the hash function is perfect, collisions will______.
Where would you look for errors from the database engine?
Which of the following are true about handling text and binary files in Python?
(A) A text file stores data in human-readable format, while a binary file stores data in machine-readable format.
(B) The pickle module is used to store and retrieve Python objects in text files.
(C) The open() function is used to open files, and it requires at least one argument: the filename.
(D) The "wb" mode is used to write data to a binary file.
Choose the correct answer from the options given below:
What will be the output of the following Python code?
def f1(a,b=[]):
b.append(a)
return b
print (f1(2,[3,4]))
Match List-I with List-II:
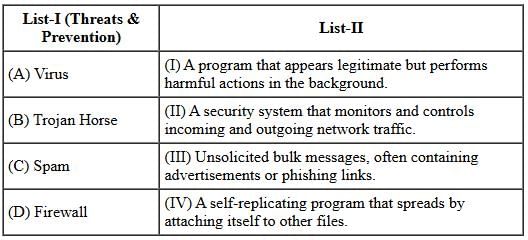
Choose the correct answer from the options given below:
Syntax of seek function in Python is myfile.seek(offset, reference_point) where myfile is the file object. What is the default value of reference_point?
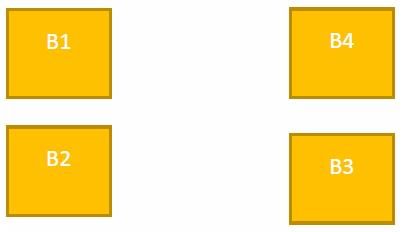
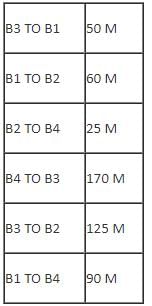
A company ABC Enterprises has four blocks of buildings as shown in the figure:
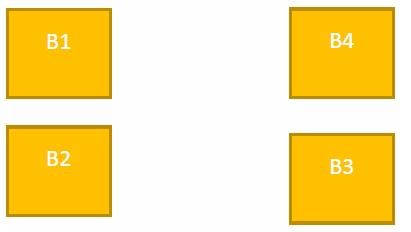
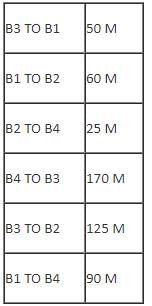
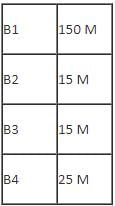
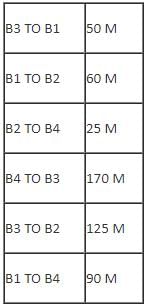
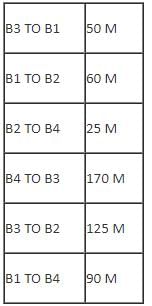
Center to center distance between various blocks:
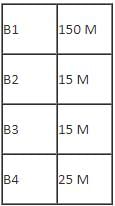
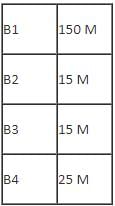
Number of computers in each block:
Computers in each block are networked but blocks are not networked. The company has now decided to connect the blocks also.
Q. Suggest the most appropriate topology for the connections between the blocks.
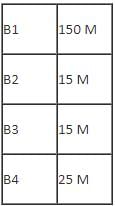
A company ABC Enterprises has four blocks of buildings as shown in the figure:
Center to center distance between various blocks:
Number of computers in each block:
Computers in each block are networked but blocks are not networked. The company has now decided to connect the blocks also.
Q. Which one of the following devices will you suggest for connecting all the computers with in each of their blocks?
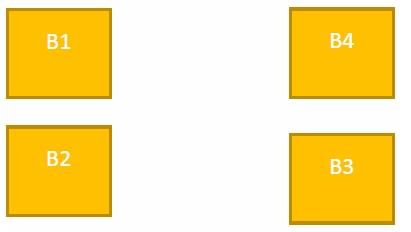
A company ABC Enterprises has four blocks of buildings as shown in the figure:
Center to center distance between various blocks:
Number of computers in each block:
Computers in each block are networked but blocks are not networked. The company has now decided to connect the blocks also.
Q. Suggest the most appropriate location of the server, to get the best connectivity for maximum number of computers.
A company ABC Enterprises has four blocks of buildings as shown in the figure:
Center to center distance between various blocks:
Number of computers in each block:
Computers in each block are networked but blocks are not networked. The company has now decided to connect the blocks also.
Q. The company wants internet accessibility in all the blocks. The suitable and cost-effective technology for that would be:
A company ABC Enterprises has four blocks of buildings as shown in the figure:
Center to center distance between various blocks:
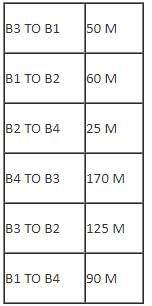
Number of computers in each block:
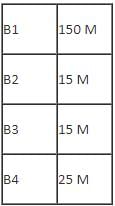
Computers in each block are networked but blocks are not networked. The company has now decided to connect the blocks also.
Q. The company is planning to link its head office situated in New Delhi with the offices in hilly areas. Suggest a way to connect it economically:
Match List-I with List-II:
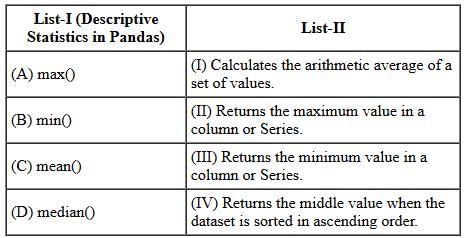
Choose the correct answer from the options given below: