Computer Knowledge - 10 - SSC CGL MCQ
20 Questions MCQ Test - Computer Knowledge - 10
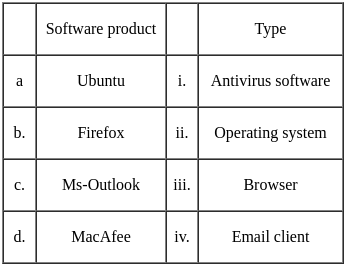
Unwanted or unlawful email messages are frequently referred to as___ .
What does MS-DOS operating system use for interacting with the end users?
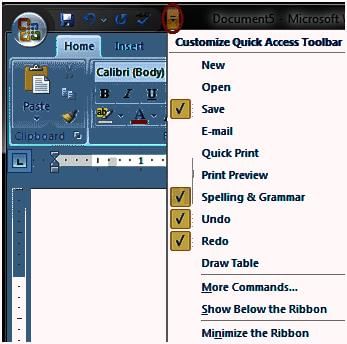
Which of the following buttons are present in the Quick Access Toolbar by default in MS-Word 2010?
_______ refers to a cell or a range of cells on a spreadsheet and can be used to find the values or data that the user wants a formula to calculate.
Which of the following translates internet domain and host names to IP address?
Which of the following is the most important/powerful computer in a typical network?
What is the shortcut for using ‘Thesaurus’ tool in MS-Word?
In the context of computers, what is the full form of Virus?
Which of the following function key opens a chart area to draw a specific chart in MS-Excel?
In the context of computers, what does T stands for in FTP?
Which is a standard connector used for computer video output?
In MS Excel 2007, the outlined cell (the one with the dark borders) within the worksheet is referred to as the________.
The quickest way to create a MS-PowerPoint presentation is to use the _________.
How do colours contribute to effective presentation and documents in MS PowerPoint?
Identify whether the given statements are true or false.
i. The storage unit of the computer holds only instructions and no data.
ii. Primary memory is temporary in nature.
iii. The secondary memory is slower and cheaper than the primary memory.