All Exams >
Class 10 >
CBSE Sample Papers For Class 10 >
All Questions
All questions of CBSE Sample Question Papers for 2021-22 for Class 10 Exam
Which one of the following software comes under Open-Source Software category?- a)Photoshop
- b)Ms-Paint
- c)Linux
- d)Windows
Correct answer is option 'C'. Can you explain this answer?
Which one of the following software comes under Open-Source Software category?
a)
Photoshop
b)
Ms-Paint
c)
Linux
d)
Windows
|
|
Vivek Rana answered |
Linux is an open source software. Open source software (OSS) is a software that is distributed with its source code, making it available for use, modification and distribution with its original rights.
Which attribute is NOT valid for the <body> tag?- a)background
- b)color
- c)vlink
- d)bgcolor
Correct answer is option 'B'. Can you explain this answer?
Which attribute is NOT valid for the <body> tag?
a)
background
b)
color
c)
vlink
d)
bgcolor
|
|
Anita Menon answered |
Color is not a valid attribute for the <body> tag background attribute is used to specify a background image for a document. vlink attribute is used to specify the colour of a visited link in a document. bgcolor attribute is used to specify the background color of a document.
________ is a software for which exclusive rights of modification in the source code remain with the owner.- a)Free Open-Source Software
- b)Freeware
- c)Open-Source Software
- d)Proprietary Software
Correct answer is option 'D'. Can you explain this answer?
________ is a software for which exclusive rights of modification in the source code remain with the owner.
a)
Free Open-Source Software
b)
Freeware
c)
Open-Source Software
d)
Proprietary Software
|
|
Ritu Saxena answered |
Proprietary software is a software for which exclusive rights of modification in the source code remain with the owner. Examples of proprietary software include Microsoft Windows, Adobe Flash Player, Adobe Photoshop, Google Earth etc.
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.Q. Secure data transmission means- a)Data can be accessed by any unauthorized person during transmission
- b)Data can be accessed by only authorized person
- c)Transmission of data
- d)None of the above
Correct answer is option 'B'. Can you explain this answer?
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
Q. Secure data transmission means
a)
Data can be accessed by any unauthorized person during transmission
b)
Data can be accessed by only authorized person
c)
Transmission of data
d)
None of the above
|
|
Urvashi dasgupta answered |
Understanding Secure Data Transmission
Secure data transmission is crucial in protecting sensitive information during transfer. This method ensures that only authorized individuals can access the data, safeguarding it from unauthorized access and potential breaches.
Why the Correct Answer is Option 'B'
The correct answer is option 'B' because:
Conclusion
In summary, secure data transmission ensures that data is accessible only to authorized individuals, thus protecting it from unauthorized access and potential breaches. This fundamental principle is essential for maintaining privacy and security in our increasingly digital world.
Secure data transmission is crucial in protecting sensitive information during transfer. This method ensures that only authorized individuals can access the data, safeguarding it from unauthorized access and potential breaches.
Why the Correct Answer is Option 'B'
The correct answer is option 'B' because:
- Protection Against Unauthorized Access: Secure data transmission methods are designed to ensure that only the intended recipient can access the data being sent. This is achieved through various encryption techniques that prevent unauthorized individuals from intercepting and reading the information.
- Encryption Technologies: Techniques like email encryption utilize public-key cryptography, which ensures that even if data is intercepted during transmission, it remains unreadable to anyone without the appropriate decryption key.
- Confidentiality Assurance: By employing methods such as secure file transfer protocols and encrypted email services, organizations can guarantee the confidentiality of the information being shared, thereby reducing the risk of privacy breaches.
- Importance in Personal and Professional Contexts: Whether in personal or professional settings, secure transmission is vital for maintaining trust and integrity in communication. It protects sensitive data from being accessed by unauthorized entities, which could lead to embarrassment or loss of sensitive information.
Conclusion
In summary, secure data transmission ensures that data is accessible only to authorized individuals, thus protecting it from unauthorized access and potential breaches. This fundamental principle is essential for maintaining privacy and security in our increasingly digital world.
Sunil wants to insert an image “e-learning.jpg” into a web page. Identify the name of tag he should use.- a)<IMAGE>
- b)<IMG>
- c)<IM>
- d)<I>
Correct answer is option 'B'. Can you explain this answer?
Sunil wants to insert an image “e-learning.jpg” into a web page. Identify the name of tag he should use.
a)
<IMAGE>
b)
<IMG>
c)
<IM>
d)
<I>
|
|
Kiran Mehta answered |
<IMG> tag is used to insert an image. It is an inline element, that means text and other elements can wrap around it.
Raman is an employer of ABC company. He wants a software for which he paid what type of software is raman using?- a)Freeware software
- b)Proprietary software
- c)Shareware software
- d)Open source software
Correct answer is option 'B'. Can you explain this answer?
Raman is an employer of ABC company. He wants a software for which he paid what type of software is raman using?
a)
Freeware software
b)
Proprietary software
c)
Shareware software
d)
Open source software

|
Bibek Goyal answered |
Proprietary software
Proprietary software refers to software that is owned by a specific company or individual and is protected by copyright law. This type of software is not freely distributed and usually requires the user to pay a license fee or purchase it.
Explanation:
What is proprietary software?
Proprietary software is a type of software that is developed and owned by a specific company or individual. It is protected by intellectual property rights, such as copyright, and its use is restricted by a license agreement. The company or individual that owns the software has exclusive control over its distribution, modification, and licensing terms.
Characteristics of proprietary software:
1. Ownership: Proprietary software is owned by a specific company or individual, who has full control over its development, distribution, and licensing.
2. License agreement: Users must agree to the terms and conditions of a license agreement to use the software. This agreement outlines the rights and restrictions imposed on the user.
3. Limited distribution: Proprietary software is not freely distributed. It is typically sold or licensed to users, who then have the right to use it within the terms of the license agreement.
4. Support and updates: The company or individual that owns the software is responsible for providing support, updates, and bug fixes. Users may need to pay for these services separately.
5. Closed source: Proprietary software is often closed source, meaning that the source code is not freely available to the public. This restricts users from modifying or redistributing the software.
Why is Raman using proprietary software?
Raman is using proprietary software because he paid for it. This indicates that the software he is using is not freely available and requires a license fee or purchase. Since Raman is an employer of ABC company, it is likely that the software he is using is specifically developed for business purposes and may have features tailored to meet the company's needs. By using proprietary software, Raman can benefit from the support, updates, and services provided by the company or individual that owns the software.
Conclusion:
Based on the given information, Raman is using proprietary software because he paid for it. Proprietary software is owned by a specific company or individual, is protected by copyright, and requires users to agree to a license agreement. It is not freely distributed and provides the company or individual with control over its development, distribution, and licensing terms.
Proprietary software refers to software that is owned by a specific company or individual and is protected by copyright law. This type of software is not freely distributed and usually requires the user to pay a license fee or purchase it.
Explanation:
What is proprietary software?
Proprietary software is a type of software that is developed and owned by a specific company or individual. It is protected by intellectual property rights, such as copyright, and its use is restricted by a license agreement. The company or individual that owns the software has exclusive control over its distribution, modification, and licensing terms.
Characteristics of proprietary software:
1. Ownership: Proprietary software is owned by a specific company or individual, who has full control over its development, distribution, and licensing.
2. License agreement: Users must agree to the terms and conditions of a license agreement to use the software. This agreement outlines the rights and restrictions imposed on the user.
3. Limited distribution: Proprietary software is not freely distributed. It is typically sold or licensed to users, who then have the right to use it within the terms of the license agreement.
4. Support and updates: The company or individual that owns the software is responsible for providing support, updates, and bug fixes. Users may need to pay for these services separately.
5. Closed source: Proprietary software is often closed source, meaning that the source code is not freely available to the public. This restricts users from modifying or redistributing the software.
Why is Raman using proprietary software?
Raman is using proprietary software because he paid for it. This indicates that the software he is using is not freely available and requires a license fee or purchase. Since Raman is an employer of ABC company, it is likely that the software he is using is specifically developed for business purposes and may have features tailored to meet the company's needs. By using proprietary software, Raman can benefit from the support, updates, and services provided by the company or individual that owns the software.
Conclusion:
Based on the given information, Raman is using proprietary software because he paid for it. Proprietary software is owned by a specific company or individual, is protected by copyright, and requires users to agree to a license agreement. It is not freely distributed and provides the company or individual with control over its development, distribution, and licensing terms.
Which HTML tags cause browsers to render text as italics?- a)<text style = “italics”></text>
- b)<ital.></ital.>
- c)<i></i>
- d)<b></b>
Correct answer is option 'C'. Can you explain this answer?
Which HTML tags cause browsers to render text as italics?
a)
<text style = “italics”></text>
b)
<ital.></ital.>
c)
<i></i>
d)
<b></b>
|
|
Ishan Choudhury answered |
<i> </i> tags are used to render text as italics. It represents a change in mood or quality of text.
The correct HTML code to display(P+Q)2 is:- a)<SUB>(P+) 2</SUB>
- b)P+Q <SUP> 2 </SUP>
- c)(P + Q)<SUP> 2 </SUP>
- d)<SUP> (P+Q) 2</SUP>
Correct answer is option 'C'. Can you explain this answer?
The correct HTML code to display(P+Q)2 is:
a)
<SUB>(P+) 2</SUB>
b)
P+Q <SUP> 2 </SUP>
c)
(P + Q)<SUP> 2 </SUP>
d)
<SUP> (P+Q) 2</SUP>
|
|
Kiran Mehta answered |
<SUP> tag defines superscript text in an HTML document. In (P+Q)2, 2 is the superscript text. So, the HTML code of (P+Q)2 is (P+Q)<SUP>2</SUP>.
Which term is used for copying of data or computer software without the owner ’s permission?- a)Software privacy
- b)Software license
- c)Open software
- d)Software piracy
Correct answer is option 'D'. Can you explain this answer?
Which term is used for copying of data or computer software without the owner ’s permission?
a)
Software privacy
b)
Software license
c)
Open software
d)
Software piracy
|
|
Avinash Patel answered |
Software piracy means copying of data or computer software without the owner’s permission. However, most people are aware about piracy and know that it is illegal, yet the piracy is uncontrollable. This is simply the notation of intellectual property rights and right to privacy.
Secure data transmission means- a)Data is accessible by any unauthorized person during transmission.
- b)Data can not be accessed by any unauthorized person during transmission.
- c)Transmission of data happens easily
- d)No one can access it
Correct answer is option 'B'. Can you explain this answer?
Secure data transmission means
a)
Data is accessible by any unauthorized person during transmission.
b)
Data can not be accessed by any unauthorized person during transmission.
c)
Transmission of data happens easily
d)
No one can access it
|
|
Avinash Patel answered |
Secure data transmission means data cannot be accessed by any unauthorized person during transmission. Secure means CANI i.e., confidentiality, authenticity, nonrepudiation and integrity.
Which of the following tag is required when the user has to give some input/data?- a)INPUT
- b)OUTPUT
- c)OPTION
- d)SELECT
Correct answer is option 'A'. Can you explain this answer?
Which of the following tag is required when the user has to give some input/data?
a)
INPUT
b)
OUTPUT
c)
OPTION
d)
SELECT
|
|
Naina Sharma answered |
The <INPUT> tag is requied when the user has to give some input/data. This tag is always used within the FORM tag. Thus, INPUT tag defines a FORM element which can receive user input. The Type attribute determines the specific sort of FORM element to be created i.e., this attribute specifies the type of input we want from the user.
It can be used to create the following type of interface elements:
(a) BUTTON
(b) CHECKBOX
(c) RADIO
(d) TEXT
(e) SUBMIT and RESET
(f) IMAGE
(g) FILE
<INPUT TYPE = “BUTTON”>: This will place a button on an HTML form.
It can be used to create the following type of interface elements:
(a) BUTTON
(b) CHECKBOX
(c) RADIO
(d) TEXT
(e) SUBMIT and RESET
(f) IMAGE
(g) FILE
<INPUT TYPE = “BUTTON”>: This will place a button on an HTML form.
The default alignment of images, that are inserted in Web page, is:- a)left
- b)right
- c)inline with text
- d)middle
Correct answer is option 'C'. Can you explain this answer?
The default alignment of images, that are inserted in Web page, is:
a)
left
b)
right
c)
inline with text
d)
middle
|
|
Radha Iyer answered |
The default alignment of images that are inserted in web page is inline with text.
Which of these is NOT an attribute of the font tag?- a)color
- b)face
- c)type
- d)size
Correct answer is option 'C'. Can you explain this answer?
Which of these is NOT an attribute of the font tag?
a)
color
b)
face
c)
type
d)
size
|
|
Niyati nayar answered |
Explanation:
The font tag was used in the earlier versions of HTML to specify the font style, size, and color of the text. However, it is no longer recommended to use the font tag as it has been deprecated in HTML5. Instead, CSS (Cascading Style Sheets) is used to style the text.
The font tag has the following attributes:
a) color: Specifies the color of the text.
b) face: Specifies the font family or typeface of the text.
c) size: Specifies the size of the text.
HTML bullet points:
- The color attribute of the font tag is used to specify the color of the text. It can take various values such as color names (e.g., red, green, blue), hexadecimal color codes (e.g., #FF0000 for red), or RGB values (e.g., rgb(255, 0, 0) for red).
- The face attribute of the font tag is used to specify the font family or typeface of the text. It can take the name of a specific font or a list of fonts separated by commas. The browser will use the first available font in the list.
- The size attribute of the font tag is used to specify the size of the text. It can take various values such as a number representing the size in pixels (e.g., size="12" for 12 pixels), or relative size values (e.g., size="+1" for a size one increment larger than the default).
Therefore, the correct answer is option 'C' because the type attribute is not an attribute of the font tag. The type attribute is used for specifying the type of an input element (e.g., text, password, checkbox) in HTML forms, but it is not applicable to the font tag.
The font tag was used in the earlier versions of HTML to specify the font style, size, and color of the text. However, it is no longer recommended to use the font tag as it has been deprecated in HTML5. Instead, CSS (Cascading Style Sheets) is used to style the text.
The font tag has the following attributes:
a) color: Specifies the color of the text.
b) face: Specifies the font family or typeface of the text.
c) size: Specifies the size of the text.
HTML bullet points:
- The color attribute of the font tag is used to specify the color of the text. It can take various values such as color names (e.g., red, green, blue), hexadecimal color codes (e.g., #FF0000 for red), or RGB values (e.g., rgb(255, 0, 0) for red).
- The face attribute of the font tag is used to specify the font family or typeface of the text. It can take the name of a specific font or a list of fonts separated by commas. The browser will use the first available font in the list.
- The size attribute of the font tag is used to specify the size of the text. It can take various values such as a number representing the size in pixels (e.g., size="12" for 12 pixels), or relative size values (e.g., size="+1" for a size one increment larger than the default).
Therefore, the correct answer is option 'C' because the type attribute is not an attribute of the font tag. The type attribute is used for specifying the type of an input element (e.g., text, password, checkbox) in HTML forms, but it is not applicable to the font tag.
Which of the following is not a cybercrime?- a)Plagiarism
- b)Phishing
- c)using licensed software
- d)hacking
Correct answer is option 'C'. Can you explain this answer?
Which of the following is not a cybercrime?
a)
Plagiarism
b)
Phishing
c)
using licensed software
d)
hacking
|
|
Ritu Saxena answered |
Cybercrime is criminal activity that either targets or uses a computer, a computer network or an networked device. Plagiarism, Phishing and hacking are cuber crime.
Using licensed software is not a cybercrime.
Using licensed software is not a cybercrime.
Preeti needs to send a very confidential message to her colleague in office over a secure channel. She uses a technique wherein an actual message (which is in readable form) can be converted into an unreadable message. This concept is known as________- a)Encryption
- b)Decryption
- c)Plagiarism
- d)Data Security
Correct answer is option 'A'. Can you explain this answer?
Preeti needs to send a very confidential message to her colleague in office over a secure channel. She uses a technique wherein an actual message (which is in readable form) can be converted into an unreadable message. This concept is known as________
a)
Encryption
b)
Decryption
c)
Plagiarism
d)
Data Security
|
|
Pratibha chauhan answered |
Answer:
Encryption is the process of converting a readable message into an unreadable form, also known as ciphertext, using a cryptographic algorithm. It is a technique used to ensure the confidentiality of data being transmitted over a network or stored on a device. In this case, Preeti is using encryption to protect the confidentiality of her message.
Encryption Process:
1. Readable Message: Preeti starts with a readable message that she wants to send to her colleague.
2. Encryption Algorithm: She uses an encryption algorithm, such as Advanced Encryption Standard (AES) or RSA, to convert the message into ciphertext.
3. Ciphertext: The encryption algorithm transforms the readable message into an unreadable form, which is known as ciphertext. This ciphertext can only be decrypted back into the original message using a decryption key.
Benefits of Encryption:
- Data Confidentiality: Encryption ensures that only authorized recipients can access and understand the message. It protects sensitive information from unauthorized access.
- Data Integrity: Encryption can also provide data integrity by detecting any unauthorized modifications or tampering with the encrypted message. If any changes are made to the ciphertext, the decryption process will fail, indicating that the message has been compromised.
- Secure Communication: By using encryption over a secure channel, Preeti can securely send confidential information without the fear of interception or eavesdropping by attackers.
Other Options:
- Decryption: Decryption is the reverse process of encryption. It involves converting the unreadable ciphertext back into the original readable message using a decryption key. While decryption is essential for the intended recipient to read the message, the question specifically asks for the technique to convert a readable message into an unreadable message, which is encryption.
- Plagiarism: Plagiarism refers to the act of copying someone else's work or ideas without giving proper credit. It is unrelated to the concept of encryption.
- Data Security: Data security is a broader term that encompasses various techniques and measures, including encryption, to protect data from unauthorized access, modification, or destruction. While encryption is a crucial aspect of data security, it is only one component of a comprehensive data security strategy.
Encryption is the process of converting a readable message into an unreadable form, also known as ciphertext, using a cryptographic algorithm. It is a technique used to ensure the confidentiality of data being transmitted over a network or stored on a device. In this case, Preeti is using encryption to protect the confidentiality of her message.
Encryption Process:
1. Readable Message: Preeti starts with a readable message that she wants to send to her colleague.
2. Encryption Algorithm: She uses an encryption algorithm, such as Advanced Encryption Standard (AES) or RSA, to convert the message into ciphertext.
3. Ciphertext: The encryption algorithm transforms the readable message into an unreadable form, which is known as ciphertext. This ciphertext can only be decrypted back into the original message using a decryption key.
Benefits of Encryption:
- Data Confidentiality: Encryption ensures that only authorized recipients can access and understand the message. It protects sensitive information from unauthorized access.
- Data Integrity: Encryption can also provide data integrity by detecting any unauthorized modifications or tampering with the encrypted message. If any changes are made to the ciphertext, the decryption process will fail, indicating that the message has been compromised.
- Secure Communication: By using encryption over a secure channel, Preeti can securely send confidential information without the fear of interception or eavesdropping by attackers.
Other Options:
- Decryption: Decryption is the reverse process of encryption. It involves converting the unreadable ciphertext back into the original readable message using a decryption key. While decryption is essential for the intended recipient to read the message, the question specifically asks for the technique to convert a readable message into an unreadable message, which is encryption.
- Plagiarism: Plagiarism refers to the act of copying someone else's work or ideas without giving proper credit. It is unrelated to the concept of encryption.
- Data Security: Data security is a broader term that encompasses various techniques and measures, including encryption, to protect data from unauthorized access, modification, or destruction. While encryption is a crucial aspect of data security, it is only one component of a comprehensive data security strategy.
Which of the following techniques can be used for security of data?- a)Authentication
- b)Authorisation
- c)Encryption
- d)All of the these
Correct answer is option 'D'. Can you explain this answer?
Which of the following techniques can be used for security of data?
a)
Authentication
b)
Authorisation
c)
Encryption
d)
All of the these
|
|
Naina Sharma answered |
There are various techniques used for security of data as Authentication, Authorization and Encryption. Authentication is the process of determining whether someone or something is, in fact, who or what it declares itself to be.
Authorization is the process of giving someone permission to do or have something.
Encryption is the method by which information is converted into secret code that hides the information’s true meaning.
Authorization is the process of giving someone permission to do or have something.
Encryption is the method by which information is converted into secret code that hides the information’s true meaning.
The correct HTML code for inserting an image is :- a)<img href=”image.gif ”>
- b)<img> image.gif</gif>
- c)<image src = “image.gif ”>
- d)<img src = “image.gif ”>
Correct answer is option 'D'. Can you explain this answer?
The correct HTML code for inserting an image is :
a)
<img href=”image.gif ”>
b)
<img> image.gif</gif>
c)
<image src = “image.gif ”>
d)
<img src = “image.gif ”>
|
|
Ritu Saxena answered |
<img src = “image.gif ”> code is used for inserting an image and image’s name is ‘image’ with gif format.
The < __________ > tag displays text in subscript form.- a)sub
- b)sup
- c)sups
- d)subs
Correct answer is option 'A'. Can you explain this answer?
The < __________ > tag displays text in subscript form.
a)
sub
b)
sup
c)
sups
d)
subs
|
|
Radha Iyer answered |
<sub> tag displays text is subscript form for example, in the chemical formula CO2, the number 2 is rendered as subscript which has a smaller font and appears with a lowered baseline.
Identify the HTML tag used to include numbered list in HTML web page.- a)<UL> tag
- b)<OL> tag
- c)<NL> tag
- d)<DL> tag
Correct answer is option 'B'. Can you explain this answer?
Identify the HTML tag used to include numbered list in HTML web page.
a)
<UL> tag
b)
<OL> tag
c)
<NL> tag
d)
<DL> tag
|
|
Ishan Choudhury answered |
<OL> tag defines an ordered list. An ordered list can be numerical or alphabetical. The <LI> tag is used to define each list item.
While creating a Web document, which unit is used to express an image’s height and width?- a)Centimeters
- b)Pixels
- c)Dots per inch
- d)Inches
Correct answer is option 'B'. Can you explain this answer?
While creating a Web document, which unit is used to express an image’s height and width?
a)
Centimeters
b)
Pixels
c)
Dots per inch
d)
Inches
|
|
Ishan Choudhury answered |
height and width attribute of <img> tag are used to define the height and width of the image. Values of these attributes are considered as pixel.
Which of the following is NOT an example of Intellectual Property rights?- a)Patent
- b)Trademark
- c)Password
- d)Industrial Design
Correct answer is option 'C'. Can you explain this answer?
Which of the following is NOT an example of Intellectual Property rights?
a)
Patent
b)
Trademark
c)
Password
d)
Industrial Design
|
|
Aditya Shah answered |
Intellectual property rights are the rights given to persons over the creations of their minds. Patent, Trademark, Industrial design are examples of intellectual property rights.
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.Q. Which method is mostly web-based?- a)FTP
- b)Email encryption
- c)Cloud services
- d)P2P
Correct answer is option 'B'. Can you explain this answer?
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
Q. Which method is mostly web-based?
a)
FTP
b)
Email encryption
c)
Cloud services
d)
P2P
|
|
Anita Menon answered |
Email encryption is encryption of email messages to protect the content from being ready by entities other than the intended recipients.
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:
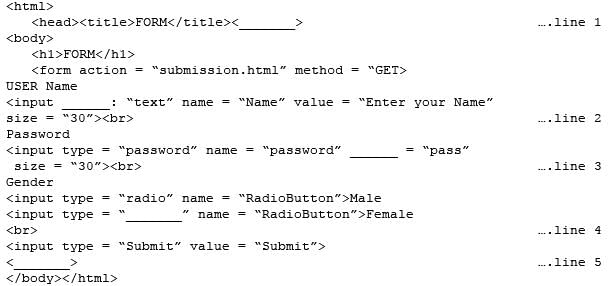 Q. Choose the correct option from the following to fill up in line 3.
Q. Choose the correct option from the following to fill up in line 3.- a)value
- b)size
- c)type
- d)name
Correct answer is option 'A'. Can you explain this answer?
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:

Consider the following code created by developer for a webpage:

Q. Choose the correct option from the following to fill up in line 3.
a)
value
b)
size
c)
type
d)
name
|
|
Rohit Sharma answered |
Value is used to fill up in line 3. It is input tag attribute which is used to fill the value of content.
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:
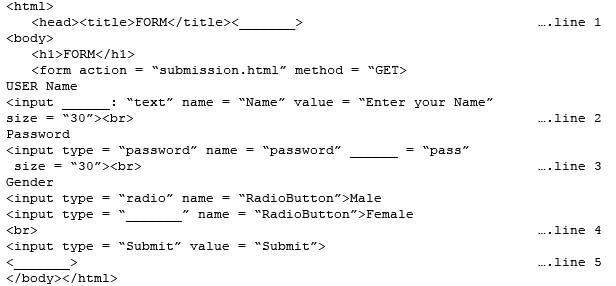 Q. Choose the correct option from the following to fill up in line 2?
Q. Choose the correct option from the following to fill up in line 2?- a)value
- b)size
- c)type
- d)name
Correct answer is option 'C'. Can you explain this answer?
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:

Consider the following code created by developer for a webpage:

Q. Choose the correct option from the following to fill up in line 2?
a)
value
b)
size
c)
type
d)
name
|
|
Ishan Choudhury answered |
Type is used to fill up in line 2.
“text” is the value of type attribute which create the text box in document.
“text” is the value of type attribute which create the text box in document.
FOIA stands for- a)Freedom of Information Act
- b)Freedom of Information Action
- c)Freeware of Information Act
- d)Freeware of Information Action
Correct answer is option 'A'. Can you explain this answer?
FOIA stands for
a)
Freedom of Information Act
b)
Freedom of Information Action
c)
Freeware of Information Act
d)
Freeware of Information Action
|
|
Ritu Saxena answered |
FOIA stands for Freedom of Information Act. It is a federal law that generally provider that any person has a right to obtain access to federal agency records. FOIA is intended to increase transparency. It does not provide access to all government documents.
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.Q. Email-Encryption can rely on which function?- a)Security
- b)Cryptography
- c)Plain-text
- d)None of these
Correct answer is option 'B'. Can you explain this answer?
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
Q. Email-Encryption can rely on which function?
a)
Security
b)
Cryptography
c)
Plain-text
d)
None of these
|
|
Avinash Patel answered |
Email encryption is an amazing innovation in cybersecurity. It uses the technology of cryptography, which has been around for milleria, and adapts it to protect communications in the digital age.
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:
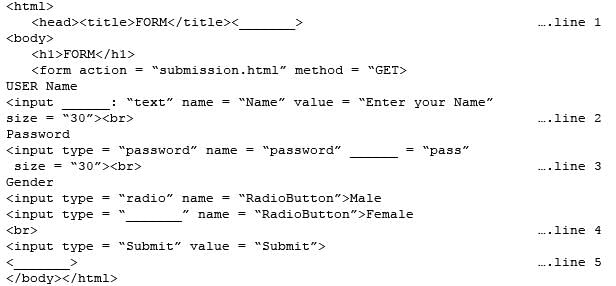 Q. Choose the correct option from the following to fill up in line 1.
Q. Choose the correct option from the following to fill up in line 1.- a)</html>
- b)</head>
- c)</body>
- d)</form>
Correct answer is option 'B'. Can you explain this answer?
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:

Consider the following code created by developer for a webpage:

Q. Choose the correct option from the following to fill up in line 1.
a)
</html>
b)
</head>
c)
</body>
d)
</form>
|
|
Anita Menon answered |
</head> is used to fill up in line 1. It is the closing tag of <head>. The <head> tag contains other head elements such as <title>.
Attribute is used to specify the location of an image file.- a)alt
- b)src
- c)align
- d)name
Correct answer is option 'B'. Can you explain this answer?
Attribute is used to specify the location of an image file.
a)
alt
b)
src
c)
align
d)
name
|
|
Kiran Mehta answered |
SRC attribute is required and contains the path to the image you want to embed. This attribute is used in <img> tag.
A is the right given by the government to an inventor to protect his/ her invention from being used/ copied for a fixed period of time.- a)Copyright
- b)Intellectual Property
- c)Patent
- d)Trademark
Correct answer is option 'C'. Can you explain this answer?
A is the right given by the government to an inventor to protect his/ her invention from being used/ copied for a fixed period of time.
a)
Copyright
b)
Intellectual Property
c)
Patent
d)
Trademark
|
|
Naina Sharma answered |
A patent is the copy right given by the government to an inventor to protect his/her invention from being used/copied for a fixed period of time.
A _______ is defined as an exclusive right granted for an invention.- a)Patent
- b)Copyright
- c)Trademark protection
- d)Design protection
Correct answer is option 'A'. Can you explain this answer?
A _______ is defined as an exclusive right granted for an invention.
a)
Patent
b)
Copyright
c)
Trademark protection
d)
Design protection
|
|
Naina Sharma answered |
Patent provides protection for novel technical solutions to problems. A patent provides patent owners with protection for their inventions. Patent applications are published after 18 months. A patent applies for a maximum of 20 years.
Which attribute of <OPTION> tag is used to specify a shorter label for an option?- a)selected
- b)value
- c)label
- d)name
Correct answer is option 'C'. Can you explain this answer?
Which attribute of <OPTION> tag is used to specify a shorter label for an option?
a)
selected
b)
value
c)
label
d)
name
|
|
Aditya Shah answered |
Label attribute of <OPTION> tag is used to specify a shorter label for an option.
Syntax
<OPTION label = “text”>
Syntax
<OPTION label = “text”>
The attribute of <img> tag specifies an alternate text for an image, if the image cannot be displayed due to any reason.- a)alt
- b)alternate
- c)tooltip
- d)text
Correct answer is option 'A'. Can you explain this answer?
The attribute of <img> tag specifies an alternate text for an image, if the image cannot be displayed due to any reason.
a)
alt
b)
alternate
c)
tooltip
d)
text
|
|
Ritu Saxena answered |
alt attribute of <img> tag specifies an alternate text for an image, if the image cannot be displayed due to any reason.
_____ is a technology which keeps the message secret from unauthorized access.- a)Encryption
- b)Decryption
- c)Anthorisation
- d)Authentication
Correct answer is option 'A'. Can you explain this answer?
_____ is a technology which keeps the message secret from unauthorized access.
a)
Encryption
b)
Decryption
c)
Anthorisation
d)
Authentication
|
|
Kiran Mehta answered |
Encryption is the method by which information is converted into secret code that hides the information’s true meaning.
What colours do #000000 denote?- a)white
- b)black
- c)blue
- d)red
Correct answer is option 'B'. Can you explain this answer?
What colours do #000000 denote?
a)
white
b)
black
c)
blue
d)
red
|
|
Rohit Sharma answered |
The colour which denotes #000000 is black. It is a hexadecimal code.
Raj has written the following code to display an image in the background of HTML document:
<BODY BgGround = “Colours.jpeg”>
But he is not getting the desired output. Help him identifying correct code from the following.- a)<BODY Bg = “Colours.jpeg”
- b)<BODY BACK = “Colours.jpeg”>
- c)<BODY BGIMAGE = “Colours.jpeg”>
- d)<BODY BACKGROUND = “Colours.jpeg”>
Correct answer is option 'D'. Can you explain this answer?
Raj has written the following code to display an image in the background of HTML document:
<BODY BgGround = “Colours.jpeg”>
But he is not getting the desired output. Help him identifying correct code from the following.
<BODY BgGround = “Colours.jpeg”>
But he is not getting the desired output. Help him identifying correct code from the following.
a)
<BODY Bg = “Colours.jpeg”
b)
<BODY BACK = “Colours.jpeg”>
c)
<BODY BGIMAGE = “Colours.jpeg”>
d)
<BODY BACKGROUND = “Colours.jpeg”>
|
|
Radha Iyer answered |
To display the image in the background of HTML document, BACKGROUND attribute is used which take image’s name with its format as value.
So, the correct code is
<BODY BACKGROUND = “Colours. jpeg”>
So, the correct code is
<BODY BACKGROUND = “Colours. jpeg”>
Which is the correct way to comment out something in HTML?- a)Using ## and #
- b)Using <!-- and -->
- c)Using </-- and -/->
- d)Using <!-- and -!>
Correct answer is option 'B'. Can you explain this answer?
Which is the correct way to comment out something in HTML?
a)
Using ## and #
b)
Using <!-- and -->
c)
Using </-- and -/->
d)
Using <!-- and -!>
|
|
Meera Rana answered |
The HTML comment tag is used to add text to an HTML document without including that text in the web page. Comment tag is shown with <! - - and - ->
Which of the following is the correct way to create a list using the uppercase letters?- a)<ol alpha = “A”>
- b)<ol type = “A”>
- c)<ol letter = “A”>
- d)None of the above
Correct answer is option 'B'. Can you explain this answer?
Which of the following is the correct way to create a list using the uppercase letters?
a)
<ol alpha = “A”>
b)
<ol type = “A”>
c)
<ol letter = “A”>
d)
None of the above
|
|
Ritu Saxena answered |
<OL> tag is used to define the ordered or numbered list in HTML document. Type attribute of <OL> tag defines the type of ordered list. To create a list using the uppercase letters, the correct code is
<OL type = “A”>
<OL type = “A”>
In HTML, the tag <HTML> is same as:- a)<html>
- b)<HTML>
- c)<Html>
- d)All of these
Correct answer is option 'D'. Can you explain this answer?
In HTML, the tag <HTML> is same as:
a)
<html>
b)
<HTML>
c)
<Html>
d)
All of these
|
|
Meera Rana answered |
Case sensitive means both uppercase and lowercase letters are treated as same. Thus, in HTML, tag and attributes are not case-sensitive.
An unordered list of items are marked with- a)bullet
- b)digit
- c)alphabet
- d)number
Correct answer is option 'A'. Can you explain this answer?
An unordered list of items are marked with
a)
bullet
b)
digit
c)
alphabet
d)
number
|
|
Vivek Rana answered |
An unordered list is a bulleted list of items. The tags for an unordered list are <UL> and <UL>. It is used to create unordered list or bulleted list like to represent the list in the form of disc, square and circle. The data is defined under the <UL> tag, by using <LI> tag.
Syntax <UL>…</UL>
Syntax <UL>…</UL>
Which of the following is a system for insuring the security of financial transactions on the intersect?- a)SSL
- b)URL
- c)SET
- d)None of these
Correct answer is option 'C'. Can you explain this answer?
Which of the following is a system for insuring the security of financial transactions on the intersect?
a)
SSL
b)
URL
c)
SET
d)
None of these
|
|
Aditya Shah answered |
SET(Secure Electronic Transaction) is a system for ensuring the security of financial transactions on the internet. It was supported initially by master card, visa, Microsoft, Netscape and others. SET is not some system that enables payment but it is a security protocol applied on those payments. It prevents merchants from seeing the customer payment information.
Tag to create textarea filed in HTML document:- a)<textarea>
- b)<input>
- c)<text>
- d)<area>
Correct answer is option 'A'. Can you explain this answer?
Tag to create textarea filed in HTML document:
a)
<textarea>
b)
<input>
c)
<text>
d)
<area>
|
|
Meera Rana answered |
Tag to create textarea field in HTML document is <TEXTAREA>.
Consider the following HTML code:
<input type = “radio” name = “gender” value = “male” checked>Male.
<input type = “radio” name = “gender” value = “Female” checked>Female.
<input type = “radio” name = “gender” value = “Others” checked>Others.
Choose the correct output that would be shown upon execution of the above code, from the choice given below:

- a)A
- b)B
- c)C
- d)D
Correct answer is option 'B'. Can you explain this answer?
Consider the following HTML code:
<input type = “radio” name = “gender” value = “male” checked>Male.
<input type = “radio” name = “gender” value = “Female” checked>Female.
<input type = “radio” name = “gender” value = “Others” checked>Others.
Choose the correct output that would be shown upon execution of the above code, from the choice given below:

<input type = “radio” name = “gender” value = “male” checked>Male.
<input type = “radio” name = “gender” value = “Female” checked>Female.
<input type = “radio” name = “gender” value = “Others” checked>Others.
Choose the correct output that would be shown upon execution of the above code, from the choice given below:

a)
A
b)
B
c)
C
d)
D
|
|
Radha Iyer answered |
To create a radio button, <INPUT> tag is used in which type attribute includes radio as its value that defines the radio button.
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.Q. Which of the following method can be used for security of data?- a)Authentication
- b)Authorisation
- c)Encryption
- d)All of the above
Correct answer is option 'C'. Can you explain this answer?
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
Q. Which of the following method can be used for security of data?
a)
Authentication
b)
Authorisation
c)
Encryption
d)
All of the above
|
|
Anita Menon answered |
Encryption is a means of securing digital data using one or more mathematical techniques, along with a password or “key” used to decrypt the information.
The default colour of a hyperlink on a webpage is- a)Black
- b)Pink
- c)Blue
- d)Grey
Correct answer is option 'C'. Can you explain this answer?
The default colour of a hyperlink on a webpage is
a)
Black
b)
Pink
c)
Blue
d)
Grey
|
|
Kiran Mehta answered |
The default colour of a hyperlink on a web page is blue.
Riya wants to buy and sell goods online, which term is used to describe this process?- a)e-Commerce
- b)m-Commerce
- c)e-Business
- d)e-Trade
Correct answer is option 'A'. Can you explain this answer?
Riya wants to buy and sell goods online, which term is used to describe this process?
a)
e-Commerce
b)
m-Commerce
c)
e-Business
d)
e-Trade
|
|
Meera Rana answered |
Riya is used to describe the e-commerce process. E-commerce is the buying and selling of goods or services via the internet, and the transfer of money and data to complete the sales.
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.Q. Some encrypted email providers has increased significantly. Out of the following which is not notable provider- a)Hushmail
- b)Mailfence
- c)Blackhat
- d)Tutanota
Correct answer is option 'C'. Can you explain this answer?
Read the following text and answer the following questions on the basis of the same:
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
In computer science, secure transmission refers to the transfer of data such as confidential or proprietary information over a secure channel. It is related to our personal or professional lives. But if the information shared is not securely transferred to receiver, it can cause breach of privacy or embarrassment.
There are some top secure data transmission methods – Email Encryption, Website Encryption, FTP(File Transfer Protocol), Cloud services, Peer to Peer (P2P) communication, etc. Email encryption → This method is mostly web-based and works by sending the recipient a link, who then logs into a secure email-server after clicking it. Email-encryption can rely on public-key cryptography. Since 2000, the number of available encrypted email providers has increased significantly. Notable providers include: Hushmail, Mailfence, Proton Mail, Tutanota.
Q. Some encrypted email providers has increased significantly. Out of the following which is not notable provider
a)
Hushmail
b)
Mailfence
c)
Blackhat
d)
Tutanota
|
|
Vivek Rana answered |
Email encryption have various notable providers, these are – Hushmail, Mailfence, Proton Mail, Tutanota, So, out of the giving options blackhat is not the notable provider.
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:
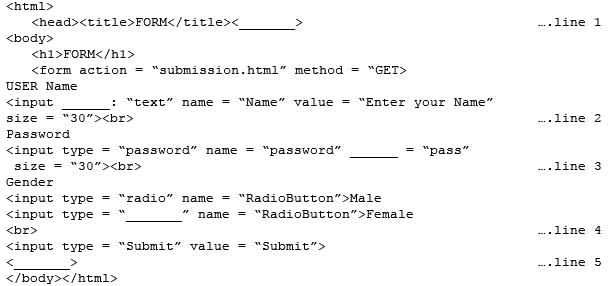 Q. Choose the correct option from the following to fill up in line 4.
Q. Choose the correct option from the following to fill up in line 4.- a)radio
- b)checkbox
- c)dropdown
- d)none
Correct answer is option 'A'. Can you explain this answer?
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:

Consider the following code created by developer for a webpage:

Q. Choose the correct option from the following to fill up in line 4.
a)
radio
b)
checkbox
c)
dropdown
d)
none
|
|
Kiran Mehta answered |
Radio is used to fill up in line 4. In input tag this is used as type attribute value, so that radio button is created on document.
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:
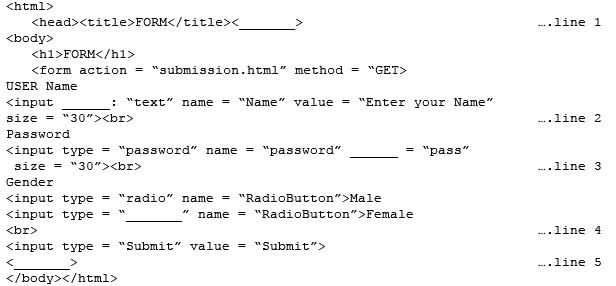 Q. Choose the correct option from the following to fill up in line 5..
Q. Choose the correct option from the following to fill up in line 5..- a)</input>
- b)</form>
- c)</body>
- d)</html>
Correct answer is option 'B'. Can you explain this answer?
Read the following text and answer the following question on the basis of the same:
Consider the following code created by developer for a webpage:

Consider the following code created by developer for a webpage:

Q. Choose the correct option from the following to fill up in line 5..
a)
</input>
b)
</form>
c)
</body>
d)
</html>
|
|
Meera Rana answered |
</form> is used to fill up in line 5. This is the <form> closing tag. The form tag is used to create an HTML form for user input.
Chapter doubts & questions for CBSE Sample Question Papers for 2021-22 - CBSE Sample Papers For Class 10 2025 is part of Class 10 exam preparation. The chapters have been prepared according to the Class 10 exam syllabus. The Chapter doubts & questions, notes, tests & MCQs are made for Class 10 2025 Exam. Find important definitions, questions, notes, meanings, examples, exercises, MCQs and online tests here.
Chapter doubts & questions of CBSE Sample Question Papers for 2021-22 - CBSE Sample Papers For Class 10 in English & Hindi are available as part of Class 10 exam.
Download more important topics, notes, lectures and mock test series for Class 10 Exam by signing up for free.

Contact Support
Our team is online on weekdays between 10 AM - 7 PM
Typical reply within 3 hours
|
Free Exam Preparation
at your Fingertips!
Access Free Study Material - Test Series, Structured Courses, Free Videos & Study Notes and Prepare for Your Exam With Ease

 Join the 10M+ students on EduRev
Join the 10M+ students on EduRev
|

|
Create your account for free
OR
Forgot Password
OR
Signup on EduRev and stay on top of your study goals
10M+ students crushing their study goals daily










