All Exams >
Class 6 >
National Cyber Olympiad Class 6 >
All Questions
All questions of HOTS (High Order Thinking Skills) for Class 6 Exam
What is a primary function of a firewall in computer networks?
(1) Blocking unauthorized access to a network.
(2) Speeding up the internet connection.
(3) Monitoring network traffic.- a)Only (1)
- b)Both (1) and (2)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
(1) Blocking unauthorized access to a network.
(2) Speeding up the internet connection.
(3) Monitoring network traffic.
a)
Only (1)
b)
Both (1) and (2)
c)
Both (1) and (3)
d)
(1), (2), and (3)
|
|
Harshad Goyal answered |
Understanding Firewall Functions
Firewalls are essential components of computer networks, serving multiple critical functions.
1. Blocking Unauthorized Access
- The primary function of a firewall is to act as a barrier between a trusted internal network and untrusted external networks, such as the internet.
- It monitors incoming and outgoing traffic and blocks any unauthorized access attempts, protecting sensitive data from potential threats.
2. Monitoring Network Traffic
- Firewalls continuously monitor network traffic to identify any suspicious activity.
- By analyzing data packets, they can detect and alert administrators to potential security breaches or attacks, ensuring a safe network environment.
3. Speeding Up Internet Connection
- While firewalls do not inherently speed up internet connections, they can help optimize network performance by managing traffic.
- By controlling data flow and preventing unwanted or malicious traffic, firewalls can indirectly lead to improved speeds for legitimate users.
Conclusion
The correct answer is option 'C' because firewalls primarily focus on blocking unauthorized access (1) and monitoring network traffic (3). While they can contribute to network performance, speeding up the internet connection is not their main function (2). Therefore, the combination of blocking unauthorized access and monitoring traffic outlines the core responsibilities of a firewall.
Firewalls are essential components of computer networks, serving multiple critical functions.
1. Blocking Unauthorized Access
- The primary function of a firewall is to act as a barrier between a trusted internal network and untrusted external networks, such as the internet.
- It monitors incoming and outgoing traffic and blocks any unauthorized access attempts, protecting sensitive data from potential threats.
2. Monitoring Network Traffic
- Firewalls continuously monitor network traffic to identify any suspicious activity.
- By analyzing data packets, they can detect and alert administrators to potential security breaches or attacks, ensuring a safe network environment.
3. Speeding Up Internet Connection
- While firewalls do not inherently speed up internet connections, they can help optimize network performance by managing traffic.
- By controlling data flow and preventing unwanted or malicious traffic, firewalls can indirectly lead to improved speeds for legitimate users.
Conclusion
The correct answer is option 'C' because firewalls primarily focus on blocking unauthorized access (1) and monitoring network traffic (3). While they can contribute to network performance, speeding up the internet connection is not their main function (2). Therefore, the combination of blocking unauthorized access and monitoring traffic outlines the core responsibilities of a firewall.
Which of the following statement is correct about the operating system such as windows 7, windows 8, etc?- a)It is a numeric – analysis tool that allows you to create a kind of computerized ledger.
- b)It is an entertainment software that allows a computer to be used as an entertainment tool only.
- c)It is a personal assistance software.
- d)It takes care of effective and efficient utilization of all hardware and software components of a computer system.
Correct answer is option 'D'. Can you explain this answer?
Which of the following statement is correct about the operating system such as windows 7, windows 8, etc?
a)
It is a numeric – analysis tool that allows you to create a kind of computerized ledger.
b)
It is an entertainment software that allows a computer to be used as an entertainment tool only.
c)
It is a personal assistance software.
d)
It takes care of effective and efficient utilization of all hardware and software components of a computer system.
|
|
Mihir Menon answered |
A) It is a numeric operating system
What should you do if you receive a suspicious email from an unknown sender?(1) Open any attachments to see what they are.(2) Click on any links provided to verify their authenticity.(3) Delete the email without opening it.- a)Only (1)
- b)Only (3)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'B'. Can you explain this answer?
What should you do if you receive a suspicious email from an unknown sender?
(1) Open any attachments to see what they are.
(2) Click on any links provided to verify their authenticity.
(3) Delete the email without opening it.
a)
Only (1)
b)
Only (3)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
Shiksha Academy answered |
The safest action is to delete the suspicious email without opening it (3). Opening attachments or clicking on links could result in malware infection.
Which of the following is NOT a common use of a database?- a)Storing large amounts of structured data
- b)Running complex calculations on data
- c)Maintaining records of transactions
- d)Managing user information
Correct answer is option 'B'. Can you explain this answer?
Which of the following is NOT a common use of a database?
a)
Storing large amounts of structured data
b)
Running complex calculations on data
c)
Maintaining records of transactions
d)
Managing user information

|
EduRev Class 6 answered |
Databases are primarily used to store and manage large amounts of structured data, maintain records of transactions, and manage user information. Running complex calculations on data is more typically done using specialized software or programming languages.
Which of the following can be considered a type of malware?
(1) Virus
(2) Worm
(3) Firewall- a)Only (1)
- b)Only (2)
- c)Both (1) and (2)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
Which of the following can be considered a type of malware?
(1) Virus
(2) Worm
(3) Firewall
(1) Virus
(2) Worm
(3) Firewall
a)
Only (1)
b)
Only (2)
c)
Both (1) and (2)
d)
(1), (2), and (3)

|
Coachify answered |
Both viruses and worms are types of malware, but a firewall is a security system designed to protect against unauthorized access.
Which of the following practices can help protect your online privacy?
(1) Using strong, unique passwords for each account.
(2) Sharing personal information on social media.
(3) Enabling two-factor authentication.- a)Only (1)
- b)Only (3)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
Which of the following practices can help protect your online privacy?
(1) Using strong, unique passwords for each account.
(2) Sharing personal information on social media.
(3) Enabling two-factor authentication.
(1) Using strong, unique passwords for each account.
(2) Sharing personal information on social media.
(3) Enabling two-factor authentication.
a)
Only (1)
b)
Only (3)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
Dr Manju Sen answered |
Using strong, unique passwords (1) and enabling two-factor authentication (3) help protect online privacy. Sharing personal information on social media (2) can compromise privacy.
Identify the correct statement about firewalls.- a)Firewalls can only be hardware-based.
- b)Firewalls prevent unauthorized access to or from a private network.
- c)Firewalls are not necessary for home networks.
- d)Firewalls can detect and remove viruses.
Correct answer is option 'B'. Can you explain this answer?
Identify the correct statement about firewalls.
a)
Firewalls can only be hardware-based.
b)
Firewalls prevent unauthorized access to or from a private network.
c)
Firewalls are not necessary for home networks.
d)
Firewalls can detect and remove viruses.

|
Coachify answered |
Firewalls are security systems that monitor and control incoming and outgoing network traffic based on predetermined security rules, thus preventing unauthorized access to or from a private network.
Which of the following is an example of a web browser?- a)Google Chrome
- b)Microsoft Excel
- c)Mozilla Firefox
- d)Both (A) and (C)
Correct answer is option 'D'. Can you explain this answer?
Which of the following is an example of a web browser?
a)
Google Chrome
b)
Microsoft Excel
c)
Mozilla Firefox
d)
Both (A) and (C)

|
EduRev Class 6 answered |
Google Chrome and Mozilla Firefox are web browsers used to access the internet, while Microsoft Excel is a spreadsheet application.
Which of the following is NOT a characteristic of a strong password?- a)It includes uppercase and lowercase letters.
- b)It contains numbers and special characters.
- c)It is easy to remember and short.
- d)It is at least 8 characters long.
Correct answer is option 'C'. Can you explain this answer?
Which of the following is NOT a characteristic of a strong password?
a)
It includes uppercase and lowercase letters.
b)
It contains numbers and special characters.
c)
It is easy to remember and short.
d)
It is at least 8 characters long.

|
Dr Manju Sen answered |
A strong password should be difficult to guess, typically containing a mix of uppercase and lowercase letters, numbers, special characters, and be at least 8 characters long. An easy-to-remember and short password does not meet these criteria.
Identify the correct definition of a firewall:- a)A software that ensures data backup.
- b)A system designed to prevent unauthorized access to or from a private network.
- c)A tool used for word processing.
- d)A device to amplify sound.
Correct answer is option 'B'. Can you explain this answer?
a)
A software that ensures data backup.
b)
A system designed to prevent unauthorized access to or from a private network.
c)
A tool used for word processing.
d)
A device to amplify sound.

|
Shiksha Academy answered |
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules, preventing unauthorized access.
Which of the following describes phishing?
(1) Sending fake emails to trick people into giving personal information.
(2) Encrypting files to demand a ransom.
(3) Installing malicious software without user consent.- a)Only (1)
- b)Both (1) and (2)
- c)Both (2) and (3)
- d)(1), (2), and (3)
Correct answer is option 'A'. Can you explain this answer?
Which of the following describes phishing?
(1) Sending fake emails to trick people into giving personal information.
(2) Encrypting files to demand a ransom.
(3) Installing malicious software without user consent.
(1) Sending fake emails to trick people into giving personal information.
(2) Encrypting files to demand a ransom.
(3) Installing malicious software without user consent.
a)
Only (1)
b)
Both (1) and (2)
c)
Both (2) and (3)
d)
(1), (2), and (3)

|
Shiksha Academy answered |
Phishing involves sending fake emails (1) to trick people into giving personal information. Encrypting files for ransom (2) is ransomware, and installing malicious software (3) is typically referred to as malware.
What is the only restriction that computers have while messaging via e-mail?- a)Data should not be in.rtf format.
- b)Data should not be in. odt format.
- c)Data should not be in. docx format.
- d)Data should be in readable format.
Correct answer is option 'D'. Can you explain this answer?
What is the only restriction that computers have while messaging via e-mail?
a)
Data should not be in.rtf format.
b)
Data should not be in. odt format.
c)
Data should not be in. docx format.
d)
Data should be in readable format.
|
|
Adya Garg answered |
Readable Format Emails are a form of communication that require the content to be understandable to the recipient. This means that: - Text Clarity: The data should be in a format that can be easily read and interpreted by the recipient. Common formats include plain text and widely-used document formats. - Compatibility: Various email clients support specific formats. If the data is in a format that is not recognized or supported, it may not display correctly or at all, rendering it unreadable. - User Accessibility: Recipients may use different devices or applications to access emails. Therefore, ensuring that the content is in a universally readable format enhances accessibility. Other Format Restrictions While the question mentions specific formats like .rtf, .odt, and .docx, these do not inherently restrict email communication. Instead, they may present challenges in terms of compatibility or usability. - Common Formats: Formats like .docx or .pdf are often used, but they should be accompanied by proper software to view them. If the software is not available, the data may not be readable. - Focus on Readability: The essence of email communication lies in conveying information clearly. Therefore, ensuring that the content is in a readable format is crucial to effective communication. In summary, the only real restriction for messaging via email is that the data must be in a readable format, ensuring clarity and accessibility for all recipients.
What does 'HTTP' stand for?- a)HyperText Transfer Protocol
- b)High Tech Transfer Protocol
- c)HyperText Transmission Protocol
- d)High Tech Transmission Protocol
Correct answer is option 'A'. Can you explain this answer?
What does 'HTTP' stand for?
a)
HyperText Transfer Protocol
b)
High Tech Transfer Protocol
c)
HyperText Transmission Protocol
d)
High Tech Transmission Protocol

|
Vp Classes answered |
HTTP stands for HyperText Transfer Protocol, which is used for transmitting web pages on the internet.
What is a strong password characteristic?- a)Contains at least eight characters.
- b)Includes a mix of uppercase and lowercase letters, numbers, and special symbols.
- c)Uses common words or phrases.
- d)(1) and (2)
Correct answer is option 'C'. Can you explain this answer?
What is a strong password characteristic?
a)
Contains at least eight characters.
b)
Includes a mix of uppercase and lowercase letters, numbers, and special symbols.
c)
Uses common words or phrases.
d)
(1) and (2)

|
Vp Classes answered |
A strong password should have a minimum length of eight characters and a combination of different types of characters. Common words or phrases should be avoided as they are easier to guess.
What is the purpose of a firewall in a computer network?
(1) To prevent unauthorized access.
(2) To monitor and control incoming and outgoing network traffic.
(3) To increase the speed of the network.- a)Only (1)
- b)Only (2)
- c)Both (1) and (2)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
What is the purpose of a firewall in a computer network?
(1) To prevent unauthorized access.
(2) To monitor and control incoming and outgoing network traffic.
(3) To increase the speed of the network.
(1) To prevent unauthorized access.
(2) To monitor and control incoming and outgoing network traffic.
(3) To increase the speed of the network.
a)
Only (1)
b)
Only (2)
c)
Both (1) and (2)
d)
(1), (2), and (3)

|
Coachify answered |
Firewalls are used to protect networks by controlling the flow of traffic based on predetermined security rules and preventing unauthorized access. They do not increase network speed.
Which device is used to connect multiple computers to form a network?- a)Monitor
- b)Keyboard
- c)Switch
- d)Printer
Correct answer is option 'C'. Can you explain this answer?
Which device is used to connect multiple computers to form a network?
a)
Monitor
b)
Keyboard
c)
Switch
d)
Printer

|
Vp Classes answered |
A switch is a networking device that connects multiple computers within a local area network (LAN), enabling them to communicate with each other.
Which one of these is an example of an input device?- a)Monitor
- b)Printer
- c)Mouse
- d)Speaker
Correct answer is option 'C'. Can you explain this answer?
a)
Monitor
b)
Printer
c)
Mouse
d)
Speaker

|
Dr Manju Sen answered |
A mouse is an input device that allows the user to interact with the computer by moving the cursor on the screen and selecting objects.
Which of the following statements is incorrect about fourth generation computers?- a)They had larger primary and secondary storage capacity as compared to third generation computers.
- b)They were general purpose machines.
- c)Their manufacturing process required manual assembly of individual components into electronic circuits.
- d)They consumed less power than third generation computers.
Correct answer is option 'C'. Can you explain this answer?
Which of the following statements is incorrect about fourth generation computers?
a)
They had larger primary and secondary storage capacity as compared to third generation computers.
b)
They were general purpose machines.
c)
Their manufacturing process required manual assembly of individual components into electronic circuits.
d)
They consumed less power than third generation computers.
|
|
Palak Nambiar answered |
Incorrect Statement about Fourth Generation Computers: c) Their manufacturing process required manual assembly of individual components into electronic circuits.
Explanation:
The fourth generation of computers was developed in the late 1970s and continued into the early 1990s. These computers were a significant advancement over the previous generations in terms of size, performance, and capabilities. They introduced several new features and technologies that made them more powerful and efficient.
Larger Primary and Secondary Storage Capacity:
- The statement in option a) is correct. Fourth generation computers had larger primary and secondary storage capacity compared to third generation computers.
- This was made possible by the development of smaller and more efficient integrated circuits (ICs) and semiconductor memory technologies such as dynamic random-access memory (DRAM).
- These advancements allowed for increased memory capacity, which in turn enabled more complex and resource-intensive applications to be run on these computers.
General Purpose Machines:
- The statement in option b) is correct. Fourth generation computers were general-purpose machines, meaning they were designed to perform a wide range of tasks and applications.
- They were capable of executing various software programs and could be used for tasks such as word processing, data analysis, graphics, and gaming.
- This versatility made them suitable for both personal and business use.
Less Power Consumption:
- The statement in option d) is correct. Fourth generation computers consumed less power than their third generation counterparts.
- This was primarily due to advancements in semiconductor technology, which allowed for the development of more energy-efficient microprocessors and electronic components.
- The reduced power consumption not only made these computers more environmentally friendly but also helped in reducing electricity costs.
Automated Manufacturing Process:
- The statement in option c) is incorrect. The manufacturing process of fourth generation computers did not require manual assembly of individual components into electronic circuits.
- Instead, the development of integrated circuits (ICs) and printed circuit boards (PCBs) enabled the automated production of electronic circuits.
- ICs integrated multiple electronic components onto a single chip, reducing the need for manual assembly.
- PCBs provided a platform for connecting and interconnecting these ICs and other electronic components, further streamlining the manufacturing process.
In conclusion, the incorrect statement about fourth generation computers is c) Their manufacturing process required manual assembly of individual components into electronic circuits. The manufacturing process of fourth generation computers was automated, thanks to the advancements in integrated circuit technology and printed circuit board manufacturing.
Explanation:
The fourth generation of computers was developed in the late 1970s and continued into the early 1990s. These computers were a significant advancement over the previous generations in terms of size, performance, and capabilities. They introduced several new features and technologies that made them more powerful and efficient.
Larger Primary and Secondary Storage Capacity:
- The statement in option a) is correct. Fourth generation computers had larger primary and secondary storage capacity compared to third generation computers.
- This was made possible by the development of smaller and more efficient integrated circuits (ICs) and semiconductor memory technologies such as dynamic random-access memory (DRAM).
- These advancements allowed for increased memory capacity, which in turn enabled more complex and resource-intensive applications to be run on these computers.
General Purpose Machines:
- The statement in option b) is correct. Fourth generation computers were general-purpose machines, meaning they were designed to perform a wide range of tasks and applications.
- They were capable of executing various software programs and could be used for tasks such as word processing, data analysis, graphics, and gaming.
- This versatility made them suitable for both personal and business use.
Less Power Consumption:
- The statement in option d) is correct. Fourth generation computers consumed less power than their third generation counterparts.
- This was primarily due to advancements in semiconductor technology, which allowed for the development of more energy-efficient microprocessors and electronic components.
- The reduced power consumption not only made these computers more environmentally friendly but also helped in reducing electricity costs.
Automated Manufacturing Process:
- The statement in option c) is incorrect. The manufacturing process of fourth generation computers did not require manual assembly of individual components into electronic circuits.
- Instead, the development of integrated circuits (ICs) and printed circuit boards (PCBs) enabled the automated production of electronic circuits.
- ICs integrated multiple electronic components onto a single chip, reducing the need for manual assembly.
- PCBs provided a platform for connecting and interconnecting these ICs and other electronic components, further streamlining the manufacturing process.
In conclusion, the incorrect statement about fourth generation computers is c) Their manufacturing process required manual assembly of individual components into electronic circuits. The manufacturing process of fourth generation computers was automated, thanks to the advancements in integrated circuit technology and printed circuit board manufacturing.
Which of the following statements is correct about the given logo?

- a)It is a family of mobile systems on a chip by Qualcomm.
- b)It is the latest video game.
- c)It is an I/O interface.
- d)It is an app developed by Apple Inc.
Correct answer is option 'A'. Can you explain this answer?
Which of the following statements is correct about the given logo?


a)
It is a family of mobile systems on a chip by Qualcomm.
b)
It is the latest video game.
c)
It is an I/O interface.
d)
It is an app developed by Apple Inc.
|
|
Rajdeep Mandal answered |
The correct answer is “Option A” because Snapdragon is a family of mobile systems on a chip by Qualcomm.
In MS Word 2010, by switching to Print Layout view and then pressing Ctrl + Alt and the plus (+) sign on the numeric pad and press enter, customize keyboard dialog box is displayed as shown in the figure. What does this command box display?
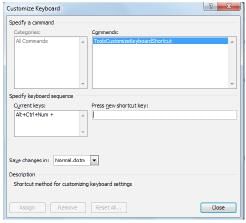
- a)Actual command’s name
- b)Font size of the text
- c)Reveal text formatting
- d)Limited formatting to permitted styles
Correct answer is option 'A'. Can you explain this answer?
In MS Word 2010, by switching to Print Layout view and then pressing Ctrl + Alt and the plus (+) sign on the numeric pad and press enter, customize keyboard dialog box is displayed as shown in the figure. What does this command box display?


a)
Actual command’s name
b)
Font size of the text
c)
Reveal text formatting
d)
Limited formatting to permitted styles

|
Ali Tariq answered |
C
Which of the following is a benefit of using cloud storage?(1) Accessing your files from any internet-connected device.(2) Keeping your files safe from local hardware failures.(3) Increasing your computer's processing speed.- a)Only (1)
- b)Only (3)
- c)Both (1) and (2)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
Which of the following is a benefit of using cloud storage?
(1) Accessing your files from any internet-connected device.
(2) Keeping your files safe from local hardware failures.
(3) Increasing your computer's processing speed.
a)
Only (1)
b)
Only (3)
c)
Both (1) and (2)
d)
(1), (2), and (3)

|
EduRev Class 6 answered |
Cloud storage allows access from any device (1) and protects against local hardware failures (2). It does not increase your computer's processing speed (3).
Which of the following statements about computer viruses is INCORRECT?- a)A virus can replicate itself and spread to other programs or files.
- b)A virus can corrupt or delete data on your computer.
- c)A virus always displays a warning message when it infects a computer.
- d)A virus can slow down the performance of your computer.
Correct answer is option 'C'. Can you explain this answer?
Which of the following statements about computer viruses is INCORRECT?
a)
A virus can replicate itself and spread to other programs or files.
b)
A virus can corrupt or delete data on your computer.
c)
A virus always displays a warning message when it infects a computer.
d)
A virus can slow down the performance of your computer.

|
Dr Manju Sen answered |
Computer viruses often operate without the user's knowledge, and do not necessarily display a warning message when they infect a computer. They can replicate, spread, corrupt data, and degrade computer performance.
Which of the following statements is true about phishing?- a)Phishing is a method of directly hacking into computers.
- b)Phishing involves tricking people into giving out personal information.
- c)Phishing requires physical access to the victim's computer.
- d)Phishing can only occur through emails.
Correct answer is option 'B'. Can you explain this answer?
Which of the following statements is true about phishing?
a)
Phishing is a method of directly hacking into computers.
b)
Phishing involves tricking people into giving out personal information.
c)
Phishing requires physical access to the victim's computer.
d)
Phishing can only occur through emails.

|
EduRev Class 6 answered |
Phishing is a form of social engineering where attackers deceive individuals into providing sensitive information, such as passwords and credit card numbers, often through fake emails or websites.
Which of the following describes phishing?
(1) Sending fake emails to trick people into giving personal information.
(2) Encrypting files to demand a ransom.
(3) Installing malicious software without user consent.- a)Only (1)
- b)Both (1) and (2)
- c)Both (2) and (3)
- d)(1), (2), and (3)
Correct answer is option 'A'. Can you explain this answer?
(1) Sending fake emails to trick people into giving personal information.
(2) Encrypting files to demand a ransom.
(3) Installing malicious software without user consent.
a)
Only (1)
b)
Both (1) and (2)
c)
Both (2) and (3)
d)
(1), (2), and (3)

|
EduRev Class 6 answered |
Phishing involves sending fake emails (1) to trick people into giving personal information. Encrypting files for ransom (2) is ransomware, and installing malicious software (3) is typically referred to as malware.
What is the purpose of encryption in cybersecurity?
(1) To protect data from unauthorized access.
(2) To make data transmission faster.
(3) To ensure data integrity.- a)Only (1)
- b)Only (2)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
(1) To protect data from unauthorized access.
(2) To make data transmission faster.
(3) To ensure data integrity.
a)
Only (1)
b)
Only (2)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
EduRev Class 6 answered |
Encryption is used to protect data from unauthorized access (1) and ensure data integrity (3). It does not make data transmission faster (2).
Which of the following are considered cyber threats?- a)Phishing
- b)Social engineering
- c)Antivirus software
- d)(1) and (2)
Correct answer is option 'C'. Can you explain this answer?
Which of the following are considered cyber threats?
a)
Phishing
b)
Social engineering
c)
Antivirus software
d)
(1) and (2)

|
Vp Classes answered |
Phishing and social engineering are methods used by attackers to trick individuals into providing sensitive information. Antivirus software is a defense mechanism against such threats.
Identify the following:
It is a malicious software designed to cause damage to a computer or network. It often spreads through email attachments or malicious websites.- a)Virus
- b)Firewall
- c)Router
- d)Operating System
Correct answer is option 'A'. Can you explain this answer?
It is a malicious software designed to cause damage to a computer or network. It often spreads through email attachments or malicious websites.
a)
Virus
b)
Firewall
c)
Router
d)
Operating System

|
EduRev Class 6 answered |
A virus is a type of malicious software (malware) that, when executed, replicates by inserting copies of itself into other computer programs, data files, or the boot sector of the hard drive.
Which of the following statements about the internet is true?- a)The internet is a single, centralized network.
- b)The internet can only be accessed via computers.
- c)The internet consists of a vast number of interconnected networks.
- d)The internet was created in the 1990s.
Correct answer is option 'C'. Can you explain this answer?
Which of the following statements about the internet is true?
a)
The internet is a single, centralized network.
b)
The internet can only be accessed via computers.
c)
The internet consists of a vast number of interconnected networks.
d)
The internet was created in the 1990s.

|
Coachify answered |
The internet is a global system of interconnected networks that use the Internet Protocol Suite (TCP/IP) to communicate between networks and devices. It is decentralized and can be accessed via various devices, not just computers. The development of the internet began in the 1960s.
What does the term "encryption" refer to?- a)Compressing files to save storage space.
- b)Scanning files for viruses.
- c)Converting data into a coded form to prevent unauthorized access.
- d)Deleting unwanted files permanently.
Correct answer is option 'C'. Can you explain this answer?
What does the term "encryption" refer to?
a)
Compressing files to save storage space.
b)
Scanning files for viruses.
c)
Converting data into a coded form to prevent unauthorized access.
d)
Deleting unwanted files permanently.

|
Dr Manju Sen answered |
Encryption is the process of converting data into a coded form to prevent unauthorized access, ensuring that only authorized parties can read it.
What is the primary purpose of a web browser?- a)To store files on the internet.
- b)To provide access to email services.
- c)To navigate and view web pages on the internet.
- d)To develop websites.
Correct answer is option 'C'. Can you explain this answer?
What is the primary purpose of a web browser?
a)
To store files on the internet.
b)
To provide access to email services.
c)
To navigate and view web pages on the internet.
d)
To develop websites.

|
EduRev Class 6 answered |
A web browser is a software application used to access and view websites on the internet, allowing users to navigate between pages and interact with online content.
Which of the following is a benefit of using cloud computing?
(1) Access to files from anywhere with an internet connection.
(2) Requires powerful local hardware.
(3) Automatic software updates.- a)Only (1)
- b)Only (2)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
Which of the following is a benefit of using cloud computing?
(1) Access to files from anywhere with an internet connection.
(2) Requires powerful local hardware.
(3) Automatic software updates.
(1) Access to files from anywhere with an internet connection.
(2) Requires powerful local hardware.
(3) Automatic software updates.
a)
Only (1)
b)
Only (2)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
Vp Classes answered |
Cloud computing allows users to access files from anywhere with an internet connection and benefits from automatic software updates. It does not require powerful local hardware, making it accessible on less powerful devices.
______ is a high-end 4G touch screen, smartphone developed by Black Berry and was released on September 18, 2013.- a)BlackBerry Z10
- b)BlackBerry Z30
- c)BlackBerry Z20
- d)BlackBerry 230
Correct answer is option 'B'. Can you explain this answer?
______ is a high-end 4G touch screen, smartphone developed by Black Berry and was released on September 18, 2013.
a)
BlackBerry Z10
b)
BlackBerry Z30
c)
BlackBerry Z20
d)
BlackBerry 230

|
My Creations answered |
Collect different kinds of maps and study them. if you have any doubts clarify them with your teacher. AS
Which of the following statements is correct?- a)File server provides a central storage facility to store files of several users on a network.
- b)Name the server that translates name into network addresses.
- c)Database server manages a centralized database, and enables several users on a network to have shared access to same database.
- d)All of these
Correct answer is option 'D'. Can you explain this answer?
Which of the following statements is correct?
a)
File server provides a central storage facility to store files of several users on a network.
b)
Name the server that translates name into network addresses.
c)
Database server manages a centralized database, and enables several users on a network to have shared access to same database.
d)
All of these

|
Nyanzobe Magambo answered |
C
Which of the following best describes a 'phishing' attack?- a)A method to improve computer performance.
- b)A technique to steal personal information by pretending to be a trustworthy entity.
- c)A process to backup data regularly.
- d)A software used to remove viruses.
Correct answer is option 'B'. Can you explain this answer?
a)
A method to improve computer performance.
b)
A technique to steal personal information by pretending to be a trustworthy entity.
c)
A process to backup data regularly.
d)
A software used to remove viruses.

|
Coachify answered |
Phishing is a type of social engineering attack where attackers attempt to steal sensitive information by pretending to be a trustworthy entity, often through email.
Suppose, a webpage owner updated his webpage, then which of the following would find those changes and update its index?- a)HotBot
- b)Spider
- c)Lycos
- d)Inference find
Correct answer is option 'B'. Can you explain this answer?
Suppose, a webpage owner updated his webpage, then which of the following would find those changes and update its index?
a)
HotBot
b)
Spider
c)
Lycos
d)
Inference find
|
|
Charvi Chauhan answered |
The correct answer is option 'B' which is "Spider". A spider, also known as a crawler or a bot, is an automated program that systematically browses the web to collect data from websites. Here is a detailed explanation of how spiders work and update their index:
How Spiders Work:
- Spiders start by visiting a website's homepage and following links to other pages on the site.
- They collect information about the pages they visit, including the content, links, and metadata.
- The data is then stored in a search engine's index, which is a database of all the information collected by the spider.
- When a user enters a search query, the search engine uses its index to find relevant pages.
How Spiders Update their Index:
- When a webpage owner updates their webpage, the changes will be reflected on the live site.
- The spider will revisit the site on a regular basis to check for changes and update its index accordingly.
- The frequency of spider visits can vary depending on the website's popularity and the search engine's algorithm.
- Generally, popular sites are visited more frequently, while less popular sites may take longer to be re-crawled.
In conclusion, spiders are automated programs that systematically browse the web to collect data from websites. They update their index by revisiting sites on a regular basis and checking for changes. This allows search engines to provide up-to-date and relevant search results for users.
How Spiders Work:
- Spiders start by visiting a website's homepage and following links to other pages on the site.
- They collect information about the pages they visit, including the content, links, and metadata.
- The data is then stored in a search engine's index, which is a database of all the information collected by the spider.
- When a user enters a search query, the search engine uses its index to find relevant pages.
How Spiders Update their Index:
- When a webpage owner updates their webpage, the changes will be reflected on the live site.
- The spider will revisit the site on a regular basis to check for changes and update its index accordingly.
- The frequency of spider visits can vary depending on the website's popularity and the search engine's algorithm.
- Generally, popular sites are visited more frequently, while less popular sites may take longer to be re-crawled.
In conclusion, spiders are automated programs that systematically browse the web to collect data from websites. They update their index by revisiting sites on a regular basis and checking for changes. This allows search engines to provide up-to-date and relevant search results for users.
Which of the following statements about strong passwords are true?
(1) They include a mix of letters, numbers, and symbols.
(2) They are easy to guess.
(3) They are at least 8 characters long.- a)Only (1)
- b)Only (3)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
Which of the following statements about strong passwords are true?
(1) They include a mix of letters, numbers, and symbols.
(2) They are easy to guess.
(3) They are at least 8 characters long.
(1) They include a mix of letters, numbers, and symbols.
(2) They are easy to guess.
(3) They are at least 8 characters long.
a)
Only (1)
b)
Only (3)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
Coachify answered |
A strong password should be a combination of letters, numbers, and symbols (1), and it should be at least 8 characters long (3). It should not be easy to guess.
What is the purpose of encryption in cybersecurity?
(1) To protect data from unauthorized access.
(2) To make data transmission faster.
(3) To ensure data integrity.- a)Only (1)
- b)Only (2)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
What is the purpose of encryption in cybersecurity?
(1) To protect data from unauthorized access.
(2) To make data transmission faster.
(3) To ensure data integrity.
(1) To protect data from unauthorized access.
(2) To make data transmission faster.
(3) To ensure data integrity.
a)
Only (1)
b)
Only (2)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
Vp Classes answered |
Encryption is used to protect data from unauthorized access (1) and ensure data integrity (3). It does not make data transmission faster (2).
Which of the following actions can help you stay safe online?
(1) Using strong, unique passwords for each account.
(2) Clicking on suspicious links to check if they are safe.
(3) Keeping your software and apps updated.- a)Only (1)
- b)Only (2)
- c)Both (1) and (3)
- d)(1), (2), and (3)
Correct answer is option 'C'. Can you explain this answer?
(1) Using strong, unique passwords for each account.
(2) Clicking on suspicious links to check if they are safe.
(3) Keeping your software and apps updated.
a)
Only (1)
b)
Only (2)
c)
Both (1) and (3)
d)
(1), (2), and (3)

|
Dr Manju Sen answered |
Using strong, unique passwords (1) and keeping your software updated (3) are both important steps for staying safe online. Clicking on suspicious links (2) is unsafe and should be avoided.
Chapter doubts & questions for HOTS (High Order Thinking Skills) - National Cyber Olympiad Class 6 2025 is part of Class 6 exam preparation. The chapters have been prepared according to the Class 6 exam syllabus. The Chapter doubts & questions, notes, tests & MCQs are made for Class 6 2025 Exam. Find important definitions, questions, notes, meanings, examples, exercises, MCQs and online tests here.
Chapter doubts & questions of HOTS (High Order Thinking Skills) - National Cyber Olympiad Class 6 in English & Hindi are available as part of Class 6 exam.
Download more important topics, notes, lectures and mock test series for Class 6 Exam by signing up for free.
National Cyber Olympiad Class 6
12 videos|25 docs|53 tests
|

Contact Support
Our team is online on weekdays between 10 AM - 7 PM
Typical reply within 3 hours
|
Free Exam Preparation
at your Fingertips!
Access Free Study Material - Test Series, Structured Courses, Free Videos & Study Notes and Prepare for Your Exam With Ease

 Join the 10M+ students on EduRev
Join the 10M+ students on EduRev
|

|
Create your account for free
OR
Forgot Password
OR
Signup to see your scores
go up within 7 days!
Access 1000+ FREE Docs, Videos and Tests
Takes less than 10 seconds to signup