Computer Knowledge - 4 - SSC CGL MCQ
20 Questions MCQ Test SSC CGL Tier II Mock Test Series 2025 - Computer Knowledge - 4
In terms of computers, the set of ways in which an adversary can enter a system and can potentially cause damage is called:
Which of the following symbols is used to make the absolute address of a cell in MS-Excel?
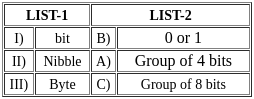
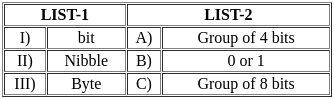
Select the option that correctly matches the elements of the below lists.
Which of the following font effects is not available in the MS-Word 2010 font dialog box?
Which one of the following memories is extremely fast and acts as a high-speed buffer between the CPU and the main memory?
In case of MS-access, the rows of table corresponds to ______________ .
Which of the following is both a system as well as application software?
Which of the following extension is used to save a spreadsheet created by MS-Excel?
Which of the following is another name for a monitor of computer?
Which of the following key has two or more attributes that allow you to uniquely recognize a specific record in DBMS?
Which of the following is the biggest board in a computer chassis?
Which field should be used when you want to send a copy of an email to someone else without the original recipient knowing?
|
66 docs|139 tests
|