Computer Science Engineering (CSE) Exam > Computer Science Engineering (CSE) Questions > A hash table of length 10 uses open addressin...
Start Learning for Free
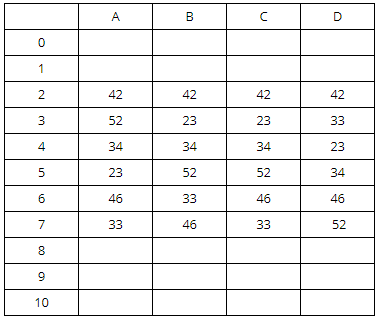
A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.
Q. Which one of the following choices gives a possible order in which the key values could have been inserted in the table?
- a)46, 42, 34, 52, 23, 33
- b)34, 42, 23, 52, 33, 46
- c)46, 34, 42, 23, 52, 33
- d)42, 46, 33, 23, 34, 52
Correct answer is option 'C'. Can you explain this answer?
Verified Answer
A hash table of length 10 uses open addressing with hash function h(k)...
Linear Probing: The location where the key value should be stored in the table is determined by the hash function.
● Here hash function is k mod 10. For e.g., if we need to store 42 then find 42 mod 10, then we get the value 2, that means the key value 42 should be stored in the table index 2.
● When there is a collision, linearly come down to locate next empty location and store the value in that location.
For the above question, only option (d) will give you the above hash table. Hash table for all options are given below:
Most Upvoted Answer
A hash table of length 10 uses open addressing with hash function h(k)...
The sequence (A) doesn’t create the hash table as the element 52 appears before 23 in this sequence.
The sequence (B) doesn’t create the hash table as the element 33 appears before 46 in this sequence.
The sequence (C) creates the hash table as 42, 23 and 34 appear before 52 and 33, and 46 appears before 33.
The sequence (D) doesn’t create the hash table as the element 33 appears before 23 in this sequence.
The sequence (B) doesn’t create the hash table as the element 33 appears before 46 in this sequence.
The sequence (C) creates the hash table as 42, 23 and 34 appear before 52 and 33, and 46 appears before 33.
The sequence (D) doesn’t create the hash table as the element 33 appears before 23 in this sequence.

|
Explore Courses for Computer Science Engineering (CSE) exam
|

|
Similar Computer Science Engineering (CSE) Doubts
A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer?
Question Description
A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? for Computer Science Engineering (CSE) 2025 is part of Computer Science Engineering (CSE) preparation. The Question and answers have been prepared according to the Computer Science Engineering (CSE) exam syllabus. Information about A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? covers all topics & solutions for Computer Science Engineering (CSE) 2025 Exam. Find important definitions, questions, meanings, examples, exercises and tests below for A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer?.
A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? for Computer Science Engineering (CSE) 2025 is part of Computer Science Engineering (CSE) preparation. The Question and answers have been prepared according to the Computer Science Engineering (CSE) exam syllabus. Information about A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? covers all topics & solutions for Computer Science Engineering (CSE) 2025 Exam. Find important definitions, questions, meanings, examples, exercises and tests below for A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer?.
Solutions for A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? in English & in Hindi are available as part of our courses for Computer Science Engineering (CSE).
Download more important topics, notes, lectures and mock test series for Computer Science Engineering (CSE) Exam by signing up for free.
Here you can find the meaning of A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? defined & explained in the simplest way possible. Besides giving the explanation of
A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer?, a detailed solution for A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? has been provided alongside types of A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? theory, EduRev gives you an
ample number of questions to practice A hash table of length 10 uses open addressing with hash function h(k)=k mod 10, and linear probing. After inserting 6 values into an empty hash table, the table is as shown below.Q.Which one of the following choices gives a possible order in which the key values could have been inserted in the table?a)46, 42, 34, 52, 23, 33b)34, 42, 23, 52, 33, 46c)46, 34, 42, 23, 52, 33d)42, 46, 33, 23, 34, 52Correct answer is option 'C'. Can you explain this answer? tests, examples and also practice Computer Science Engineering (CSE) tests.

|
Explore Courses for Computer Science Engineering (CSE) exam
|

|
Signup for Free!
Signup to see your scores go up within 7 days! Learn & Practice with 1000+ FREE Notes, Videos & Tests.
























